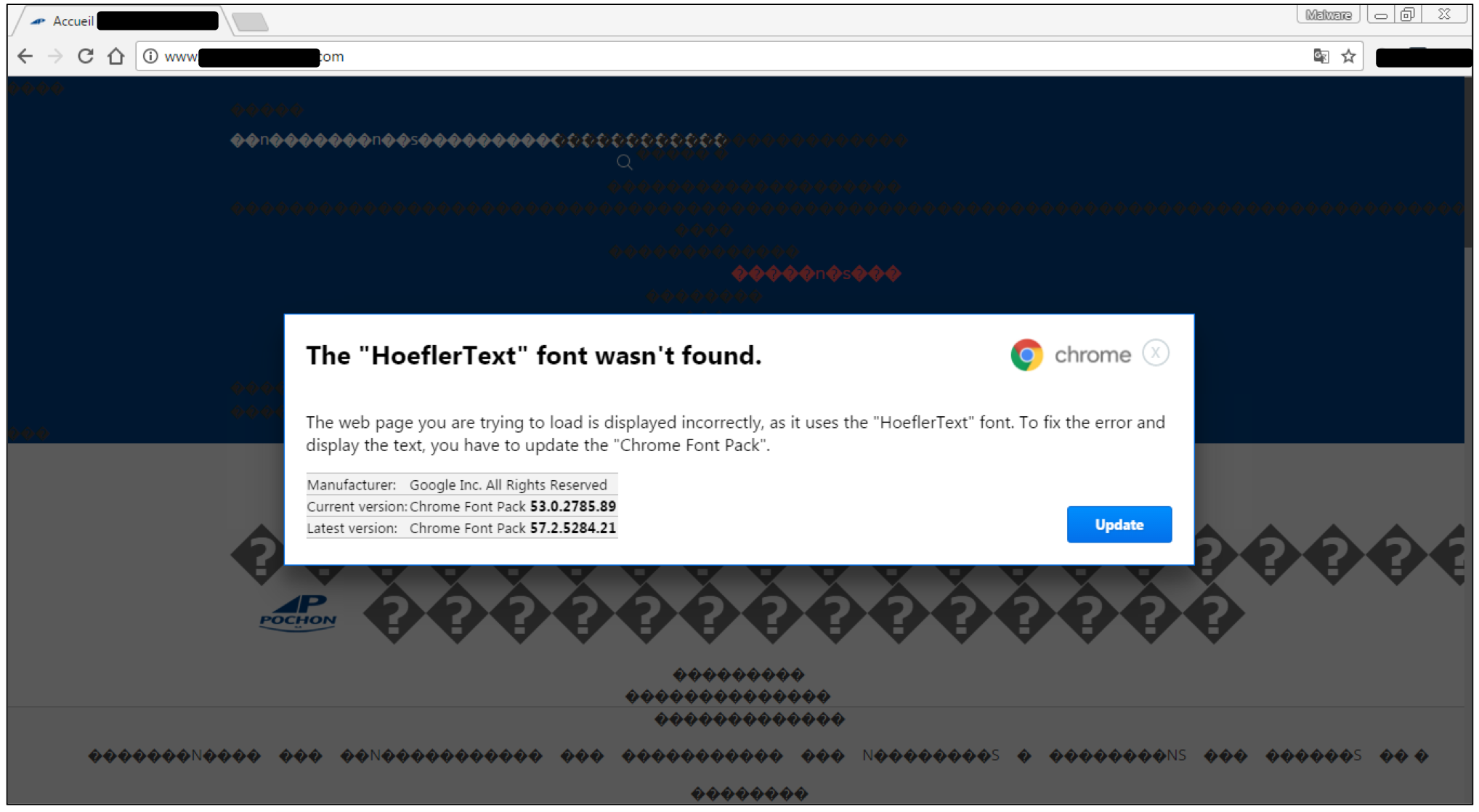
One of the most common malware campaigns from compromised websites is known as EITest and has traditionally been redirecting victims towards exploit kits. But it also has an alternate payload for browsers other than Internet Explorer, specifically for Google Chrome, where it tricks users into downloading a fake font file.
The technique first exposed by Proofpoint, is simple and yet so clever because it truly creates an illusion that there is a problem with the site being viewed. In addition, the prompt to download the ‘Chrome Font Pack’ looks sleek and professional:
The downloaded file is not a font of course, but malware. The perpetrators have used the standard name “Chrome font.exe” and a few other variations, but they have been playing with character encoding as well. This alters the file name enough (perhaps to break simple signature detection?) but still looks almost identical to the naked eye.
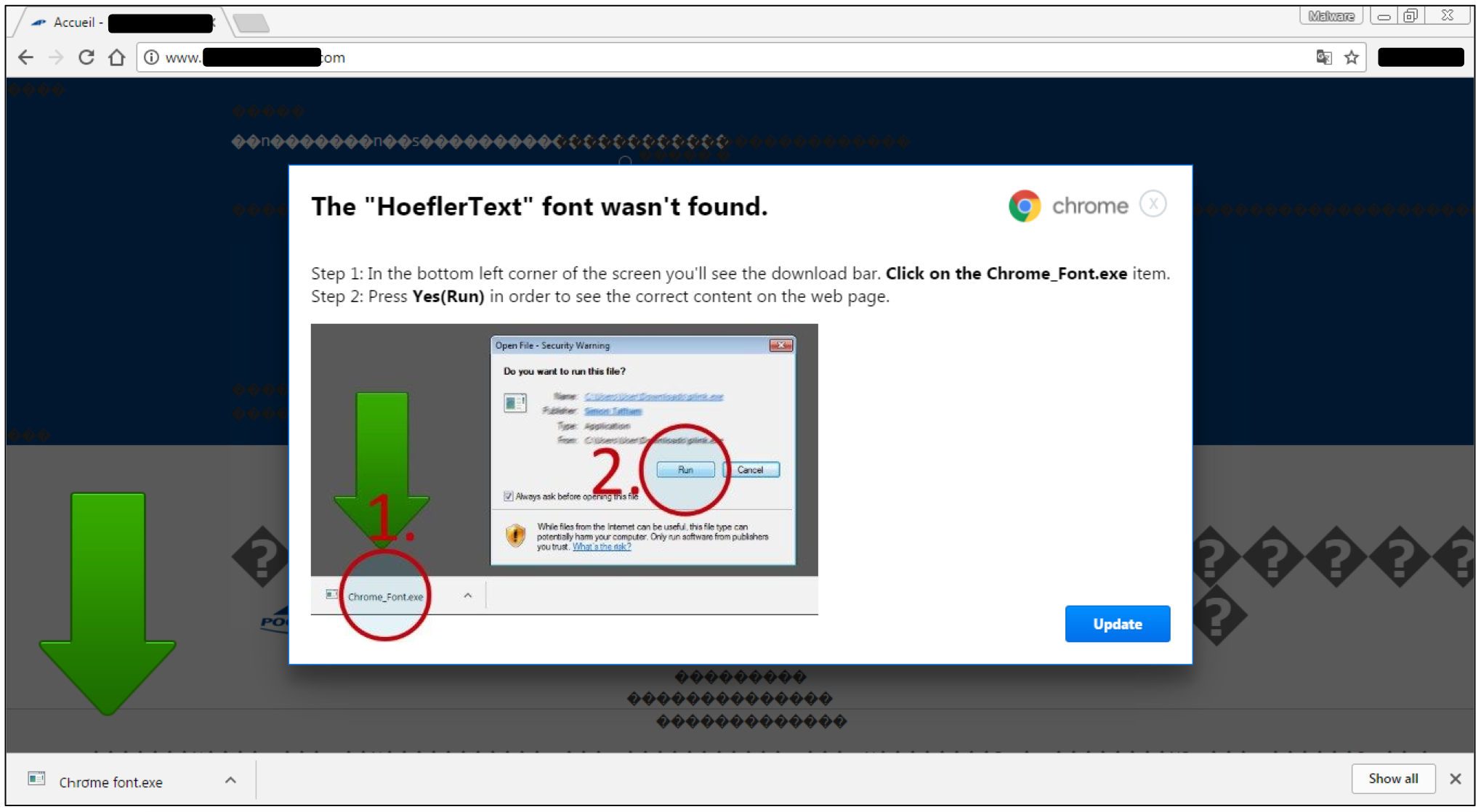
This is how the file looks, side by side with the classic UTF encoding:
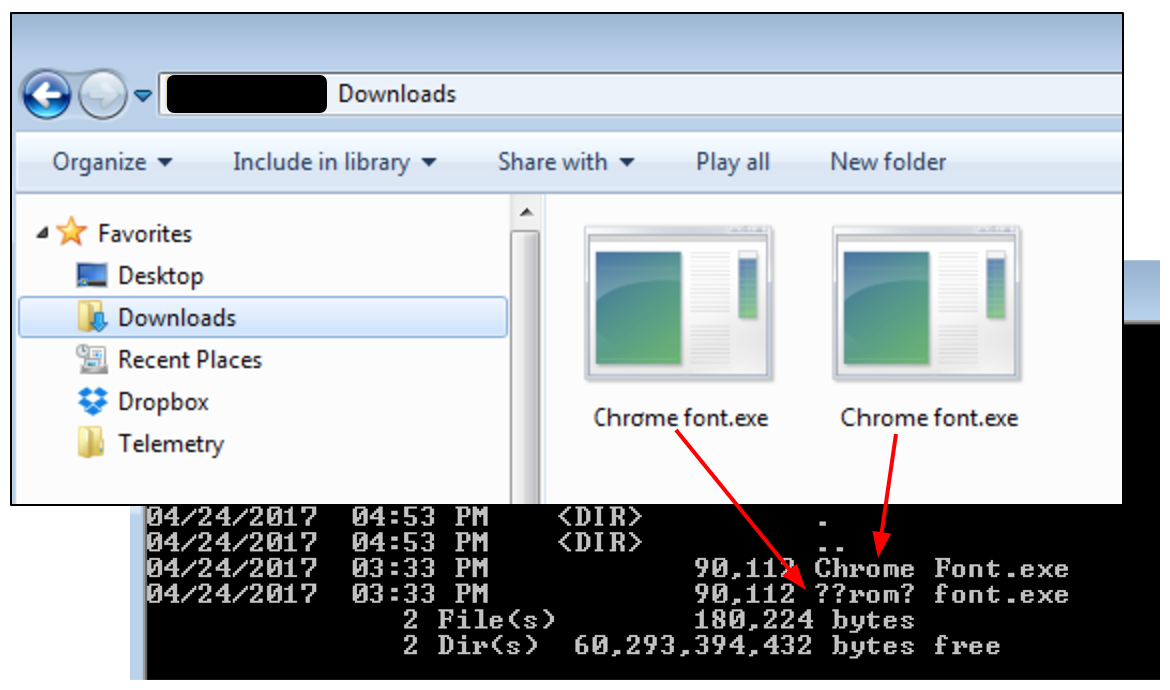
When Windows doesn’t recognize the character set, it will display ‘?’ instead. Here’s a quick view of this encoding (courtesy of Unicode Analyzer).

Users that proceed and install the so-called font are immediately infected with the Spora ransomware:
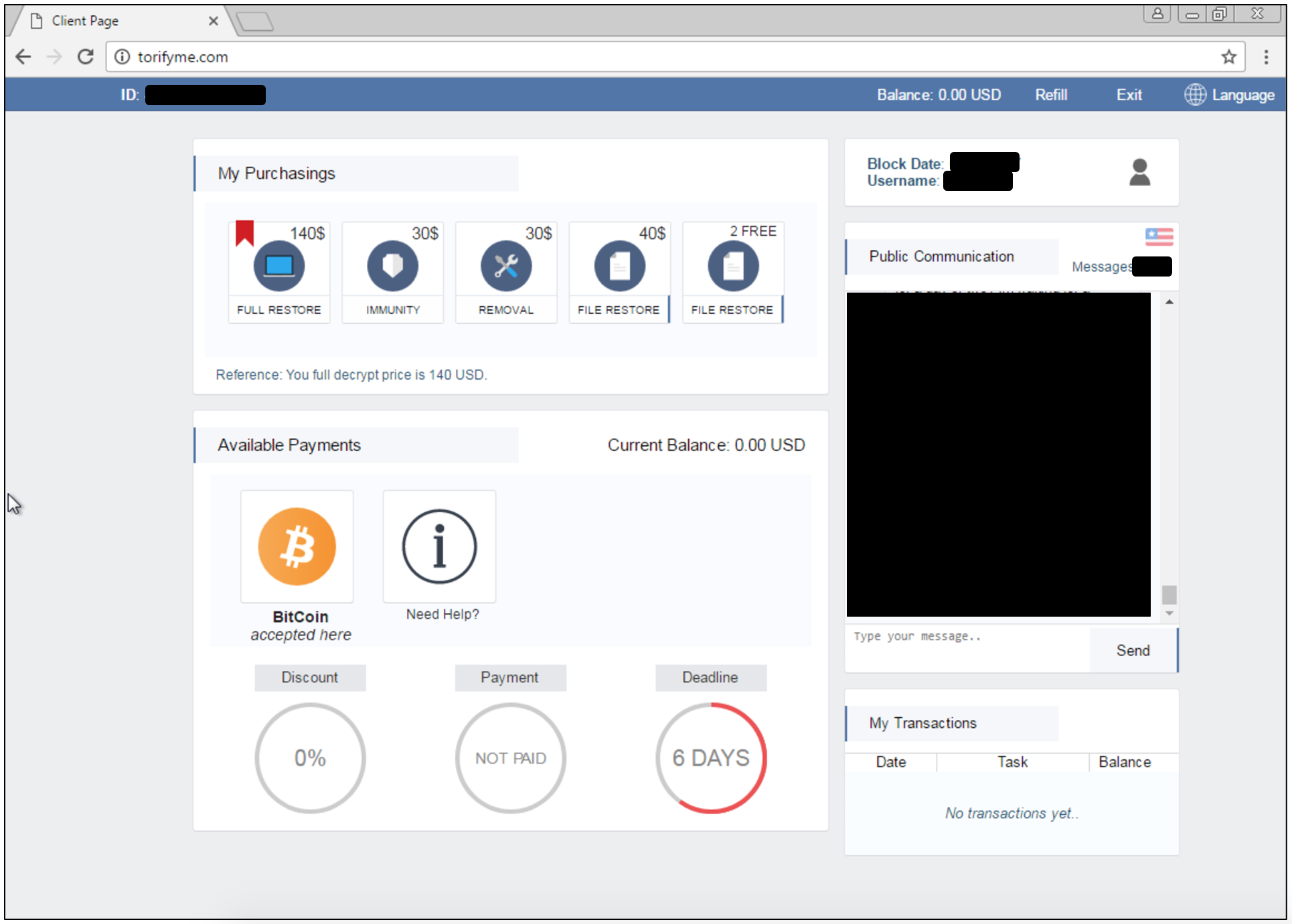
Malwarebytes already protects you against Spora thanks to its behaviour-based ransomware detection engine.










