In this series of posts, we will be using the flowchart below to follow the process of determining which adware we are dealing with. Our objective is to give you an idea of how many different types of adware are around for Windows systems. Though most are classified as PUPs, you will also see the occasional Trojan or rootkit, especially for the types that are more difficult to detect and remove.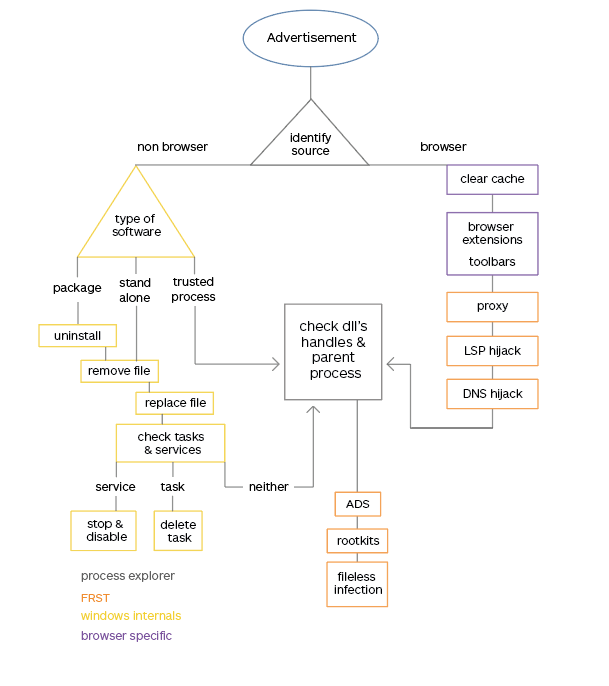
In this part of the series, we will be focusing on cases where the process we found as the one that was showing the advertisement was not the actual culprit. We will demonstrate how to use Process Explorer to see which handles, DLL’s and parent processes are involved. Which is a relatively easy way to figure out what a process is doing.
Process Explorer
As mentioned before the tool we will be using for this episode is Sysinternal’s Process Explorer. At the moment I was writing this post the current version of Process Explorer was v16.21. To view DLLs and handles you will need to enable the Lower Pane view and set it to DLLs or Handles respectively.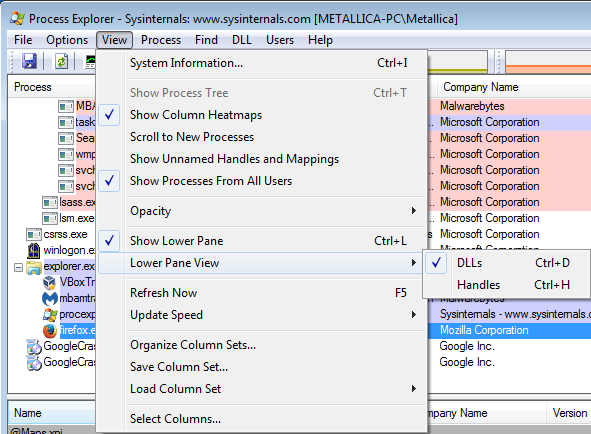
To enable the Lower Pane View, click View > and put a check-mark in front of Lower Pane View. Then if you hover over the Lower Pane View option you can either select DLLs or Handles.
Parent process
But let’s have a look at the parent process first. When you toggle the header of the Process column you will notice one configuration (like in the screenshot above), where the processes are shown in a tree-like fashion. The other configurations are alphabetical and reversed alphabetical. The tree-like representation allows you to see which process started the one(s) listed under it. Example: the processes listed under “explorer.exe” have explorer.exe as the parent process. Which in the case of explorer.exe often means that the user double-clicked the executable or a shortcut to that executable. But in cases where a browser window is showing you an advertisement, it can be interesting to see which process is the parent process of the browser process, because that could be the one you are after.
DLLs
Dynamic Load Libraries (DLLs) are files that can be used by other executable files. They often contain functions or other pieces of code, that can be called by name or entry point. In this way, the code in the library can be executed as part of the running process. To see all the DLLs that are in use by one process, you can look at the Lower Pane. Tip: if you want to present this list to someone to get a second opinion, you can select the process in the top window, then click
Tip: if you want to present this list to someone to get a second opinion, you can select the process in the top window, then click File > Save As and save the resulting text file.
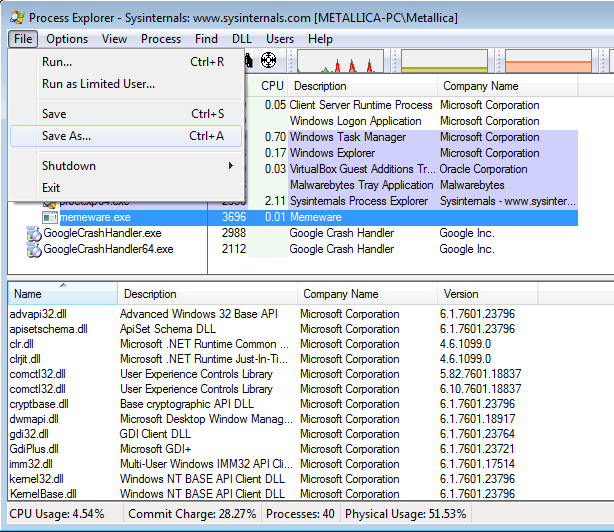
Tip: sort the Lower Pane by Company Name so you can easily skip all the Microsoft Corporation files. This will usually limit the number of DLLs you need to look at to a few.
Handles
Handles are a good way of looking whether a process is using certain resources like ports, sockets, and files. And the beauty of Process Explorer is, that if you know which handle you are looking for, you can search for that handle. For example, if you want to look at which processes have a handle on the counters.dat file, which is often shared among many internet connected processes, you can click Find > Find Handle or DLL… and then type the name of the resource in the prompt to get a list of processes that have a handle on it.
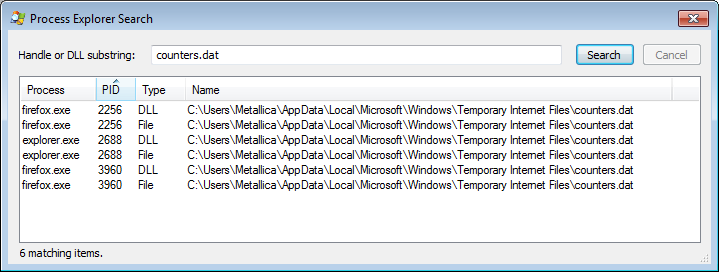
When in doubt, you can enable the Virustotal lookup of handles by clicking Options > VirusTotal.com > Check VirusTotal.com. This will send the hashes to Virustotal, a free service that analyzes suspicious files and URLs. With a bit of luck, you will notice a detection in the list that you would have missed if you had only checked the list of processes against Virustotal.
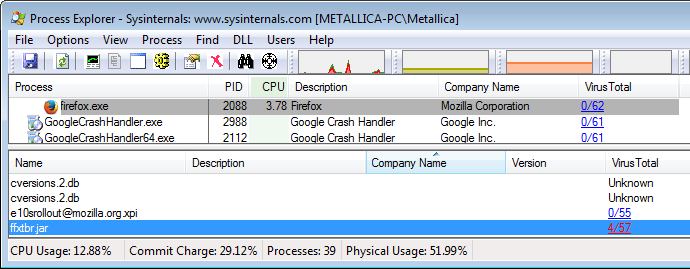
When you right-click a Handle, you will see the option to Close Handle. Releasing these handles can sometimes help when you encounter files that are undeletable because they are in use. By closing all the handles these files will become deletable as they will be no longer in use.
Example
Let’s use some adware, as an example, that uses your default browser to open advertisements. On this system, Firefox is the default browser. Every time I open Firefox I will get a new tab with a different advertisement (all redirects in this case).
It is obvious that the process is firefox.exe and a quick examination tells me there are no extensions at play and no active proxy is present. A little deeper investigation showed no LSP or DNS hijacks.
So I looked at my list of installed programs and saw something unknown, which was also suspicious because it has no Publisher and no Version, and the install date happens to match the date the advertisements started.
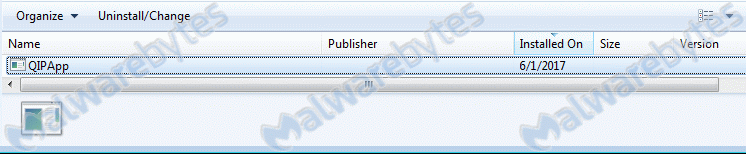
So I performed a search for DLLs and Handles with Process Explorer and found the QIPApp in quite a lot of processes and it even has a process with the same name.
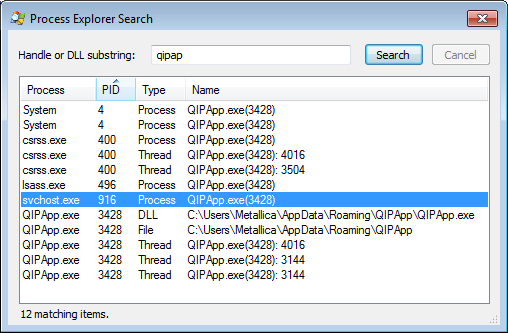
In this case, the uninstall worked and the adware was gone after a reboot, so we didn’t have to remove it manually. We also could have used Malwarebytes to remove it, but I used it as an example to demonstrate the method of investigation.
See you next time when we will tackle the ones that are a lot harder to find and remove.
Index
- Identify the process
- Clear browser caches
- Remove browser extensions
- Proxies
- Winsock hijackers
- DNS hijackers
- Type of software
- Uninstall
- Remove file
- Replace file
- Scheduled tasks
- Services
Part 5
- DLL’s
- Handles
- Parent process
Up next, part 6
- ADS
- Rootkits
- Fileless infections











