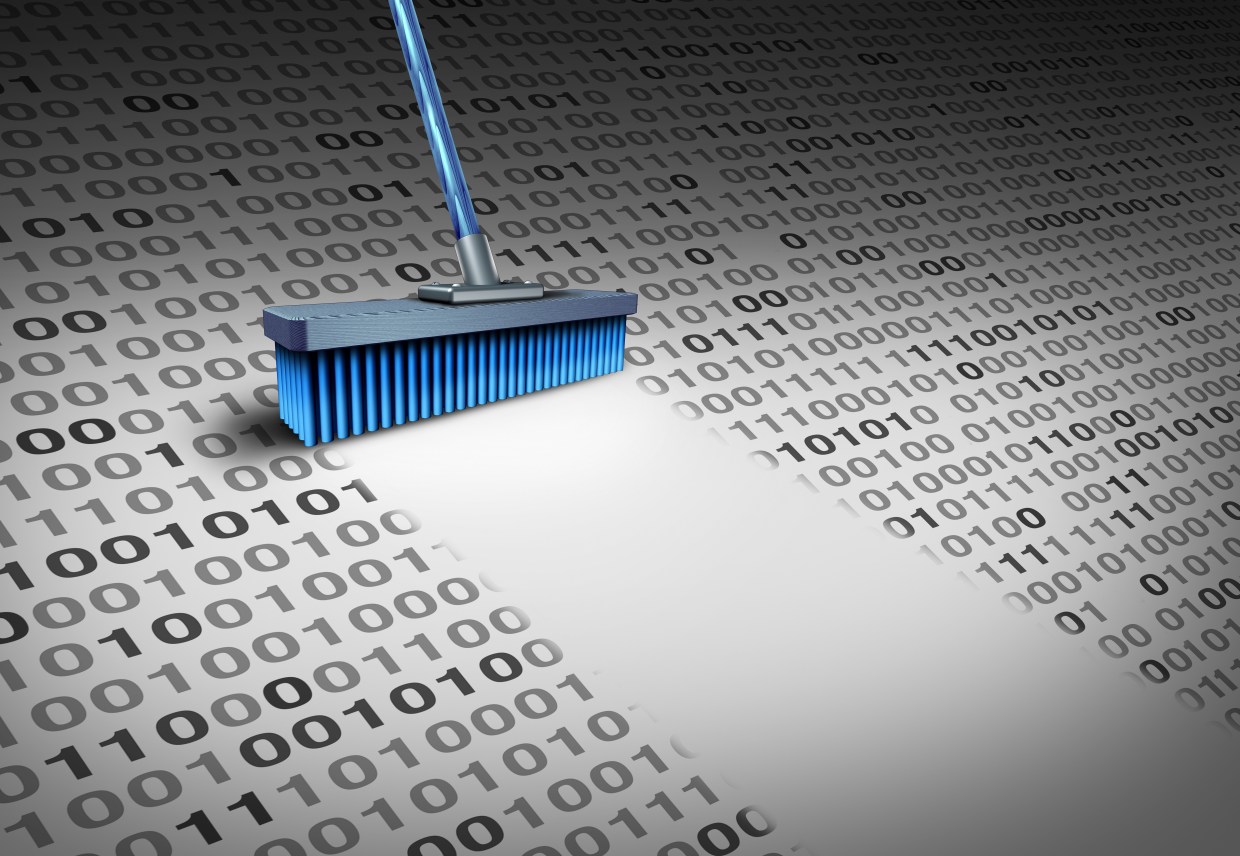
In this series, we will be using the flowchart below to follow the process of determining which adware we are dealing with. Our objective is to give you an idea of how many different types of adware are around for Windows systems. Though most adware will be classified as PUPs, you will also see the occasional Trojan or rootkit, especially in the types of adware that are harder to detect and remove.
Advertisements
It all starts with advertising.To give you an idea how much money goes around in this industry, the US online ad spending for 2016 was estimated at $ 62 Billion. Anyone that is able to grab a chunk of that will be very happy to do so, even if the methods are considered iffy. Some will not shy away from criminal behavior when that kind of money is involved. Two of the fraudulent methods to grab some of that money are called ad fraud and adware. If you want to learn the difference between these two please read my blog post, Adware vs Ad fraud. In this post, we will concentrate on adware, which basically boils down to some program on your computer showing you advertisements that do not come from the websites you are visiting.
Identify the source
We will use Process Explorer to identify the process that is behind an advertisement. Usually, this will be a browser and you will recognize it as such. But sometimes, these advertisements pop up as windows without title bars. In cases like these, you can use the cross-hairs in the Process Explorer menu, as shown below:
Drag and drop the cross-hairs on the window you are curious about and in the Process Explorer list of running processes the process responsible for the window will be selected (showing in blue).
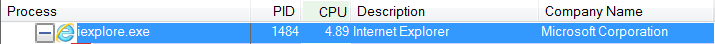
You now have the name of the process and, in case there are more instances of that process, the Process Identification (PID) associated with it.
Check where the process is connecting to
This is optional since it almost never provides any information that is useful in the removal process. Extra research, however, could tell us what family the adware belongs to and what characteristics you may expect as a result.
So, if you like, you can use the Windows built-in (after XP) tool Resource Monitor (resmon). To start Resource Monitor, you can use Windows Key + “R”, type “resmon” in the “Run” box and click OK.
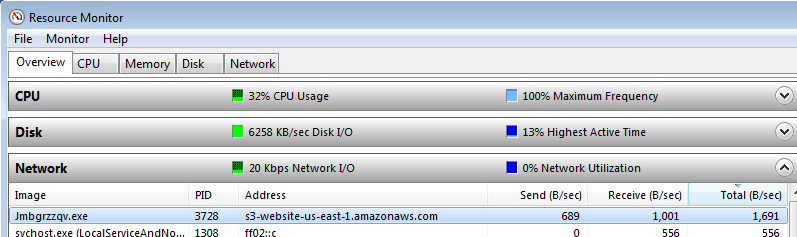
Under the Network tab > Network activity, you will find the most specific information for any connected process.
If one process has several open connections you can click the “Image” column header to sort the processes alphabetically, which provides a better overview of what a given process might be doing. Also, check if the PID listed in Process Explorer matches the one in Resource Monitor. This should be done to make sure that you are looking at the process that is showing the advertisement.
Browsers first
As this will be the most common case, let’s deal with it first. The window showing the advertisement is a window or new tab of your default browser. Some adware authors find it easier or more effective to open the Microsoft browser that came with the OS, so they will open Edge for Windows 10 and Internet Explorer (IE) for earlier versions.
Clear your browser’s cache
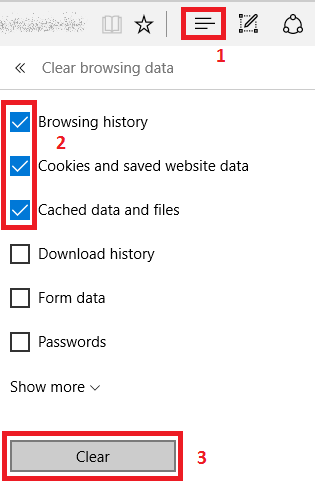
In Edge, the procedure is:
- Click the Hub icon, click “Clear History”
- Select the appropriate options. Note that clearing the “Cookies and saved website data” will result in you having to login at every site again.
- Click the “Clear” button.
For Internet Explorer:
- Click the gearbox icon
- Select Internet Options
- On the General tab click on the Delete button under Browsing history
- Select the appropriate categories. Note that clearing the “Cookies and website data” will result in you having to login at every site again.
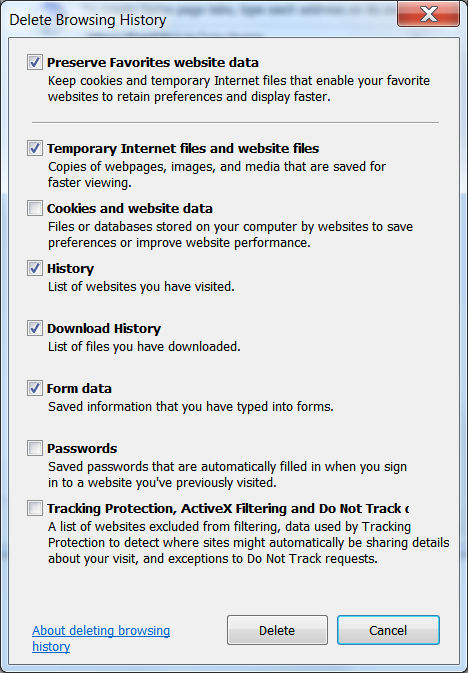
- Click the Delete button if you are happy with your choices.
For Firefox:
- Click the menu button and choose Options.
- Select the Advanced panel.
- Click on the Network tab.
- In the Cached Web Content section, click Clear Now.
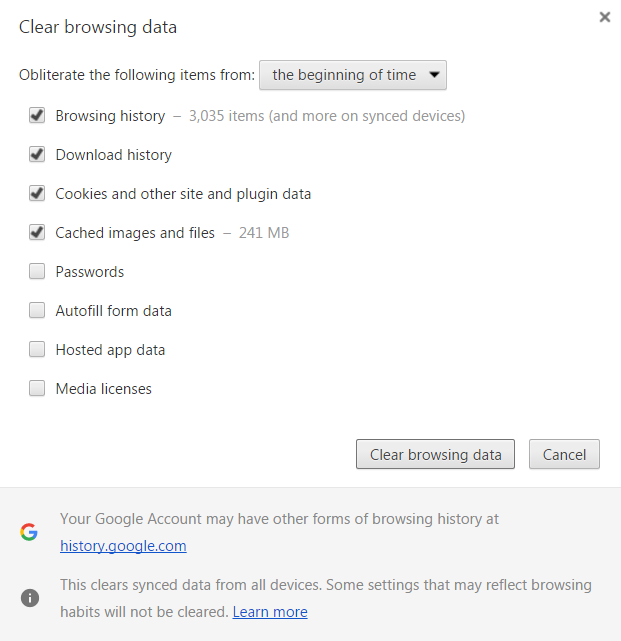
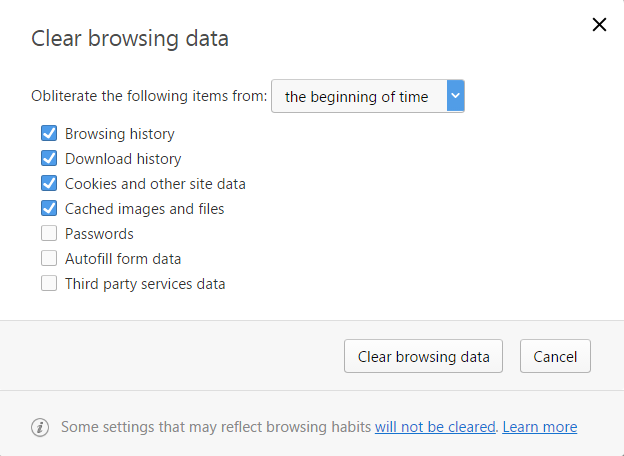
For Chrome:
- On your browser toolbar, click More (3 dots)
- Point to More tools, and then click Clear browsing data.
- Select the items that you want to clear.
- Click the Clear browsing data button.
For Opera:
- In the Opera Menu choose Settings
- Select Privacy and Security
- Under Privacy click the Clear browsing data… button
- Delete the items you wish to delete
- And click on the Clear browsing data button
Removing extensions and toolbars
Extensions and toolbars are so closely related that removing the extension will usually take the toolbar out as well.
Internet Explorer: Tools (gear icon) > Manage add-ons > Toolbars and Extensions > Select the one(s) you don’t trust one by one and click “Disable”
Firefox: Menu (horizontal stripes) > Add-ons > click on “Disable” behind the ones you don’t trust or don’t recall installing.
Chrome: Menu (horizontal stripes) > Settings > Extensions > Uncheck “Enabled” behind the ones you don’t trust or don’t recall installing.
Opera: click the Opera icon > Extensions > Extension Manager > click on Disable below the ones you don’t trust or don’t recall installing.
Index
Part 1:
- Identify the process
- Clear browser caches
- Remove browser extensions and toolbars
- Proxies
- Winsock hijackers
- DNS hijackers
Pieter Arntz