The latest wave of ransomware following the WannaCry outbreak has kept everyone very busy and been the topic of many conversations. In the meantime, other threat actors have been quite active and perhaps even enjoyed this complimentary diversion. This is certainly true for the most prolific malvertising gang of the moment, dubbed AdGholas.
Exposed a few times this year by ProofPoint and TrendMicro, AdGholas is playing a whack-a-mole game with the ad industry to distribute malware onto unsuspecting users with the help of the Astrum exploit kit.
A master of disguise, AdGholas has been flying right under the nose of several top ad networks while benefiting from the ‘first to move’ effect. Indeed, the malvertising operators are able to quickly roll out and activate a fake advertising infrastructure for a few days before getting banned.
On June 28 (which is about ten days after it was last publicly reported), we started seeing a new wave of drive-by download attacks distributed globally pushing the Astrum exploit kit. Sure enough, it was associated with AdGholas activity via a decoy website. Behind the fake ad banners for ‘expert essays’ designed to trick ad agencies, laid code to exploit and infect users who simply happened to visit popular websites.
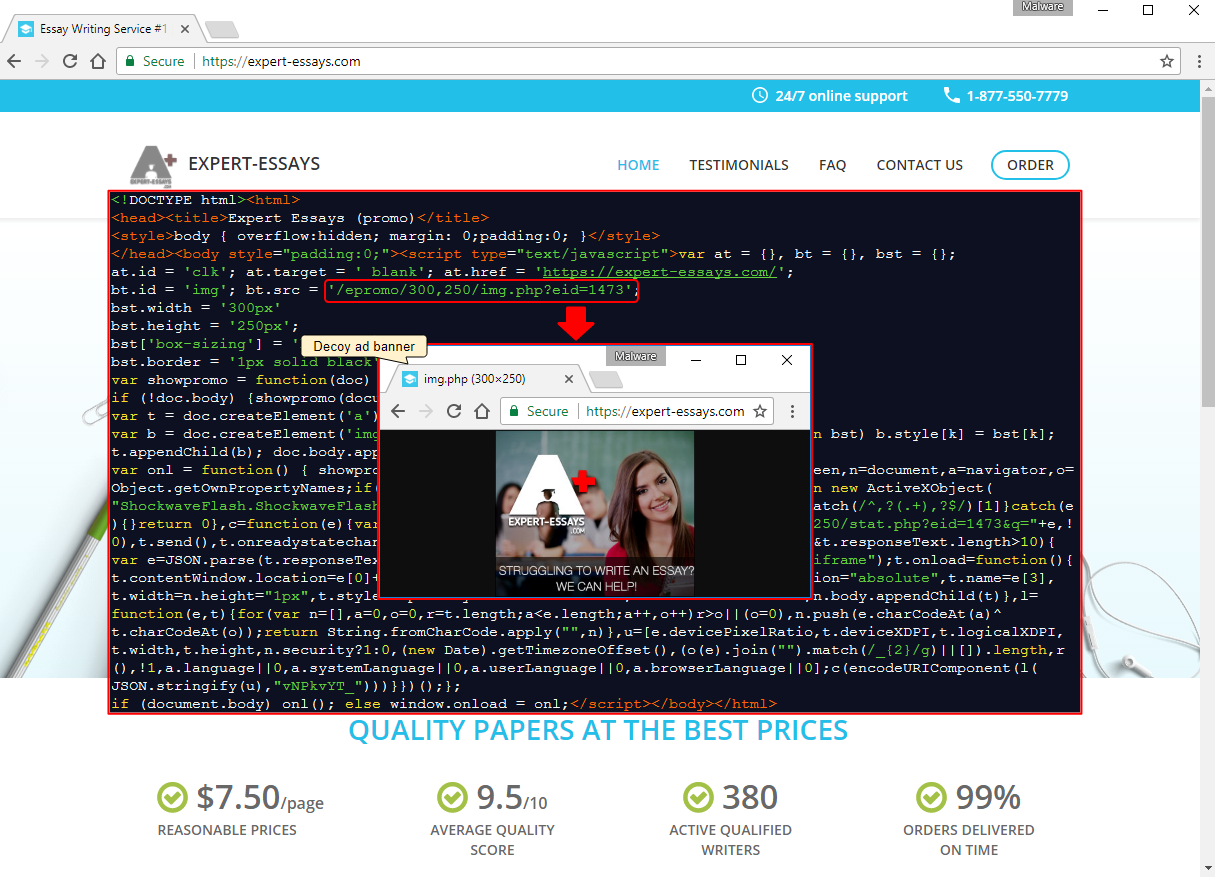
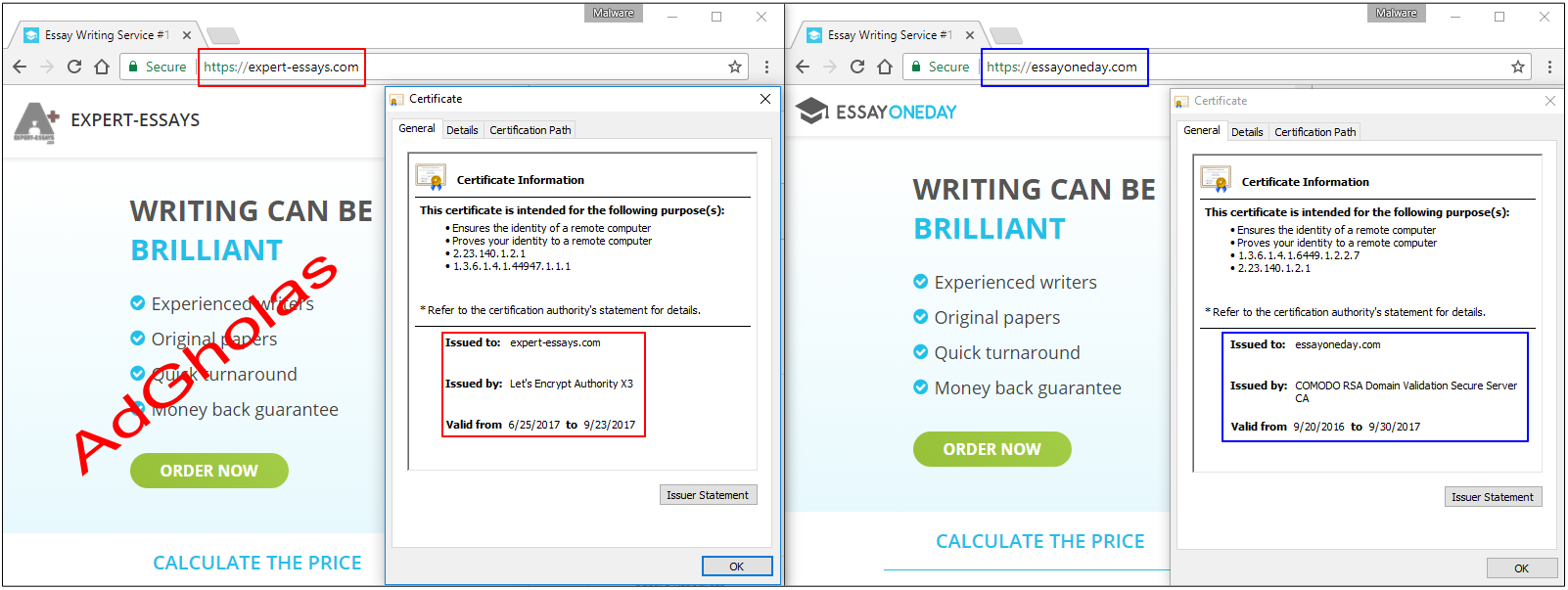
The fraudulent website expert-essays[.]com, which was registered June 22, is using a certificate from Let’s Encrypt, and is a replica from essayoneday.com. There are only a few minor visual differences between the two, and a cursory review would reveal the copycat. However, it is easier said than done in an industry dominated by automation and volume.
After getting caught, AdGholas came back up again on July 1st and 2nd – perhaps a long holiday week-end in the US may have seemed like the right timing – via a new decoy site, jet-travels[.]com, with the same modus operandi:

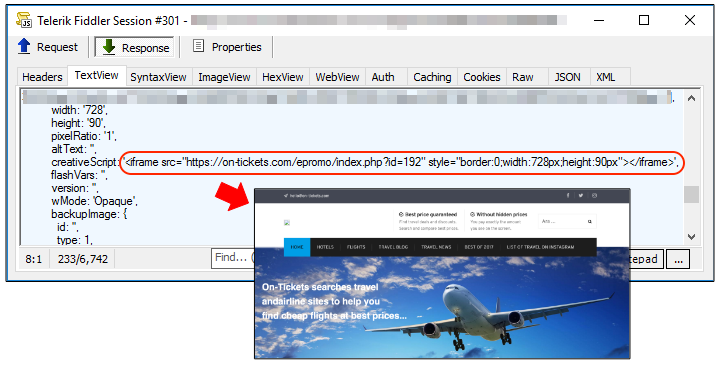
On July 6th, AdGholas struck again via on-tickets[.]com with the same delivery chain we had observed before. We’ve added the new IOCs at the bottom of this blog.
From AdGholas to Astrum EK
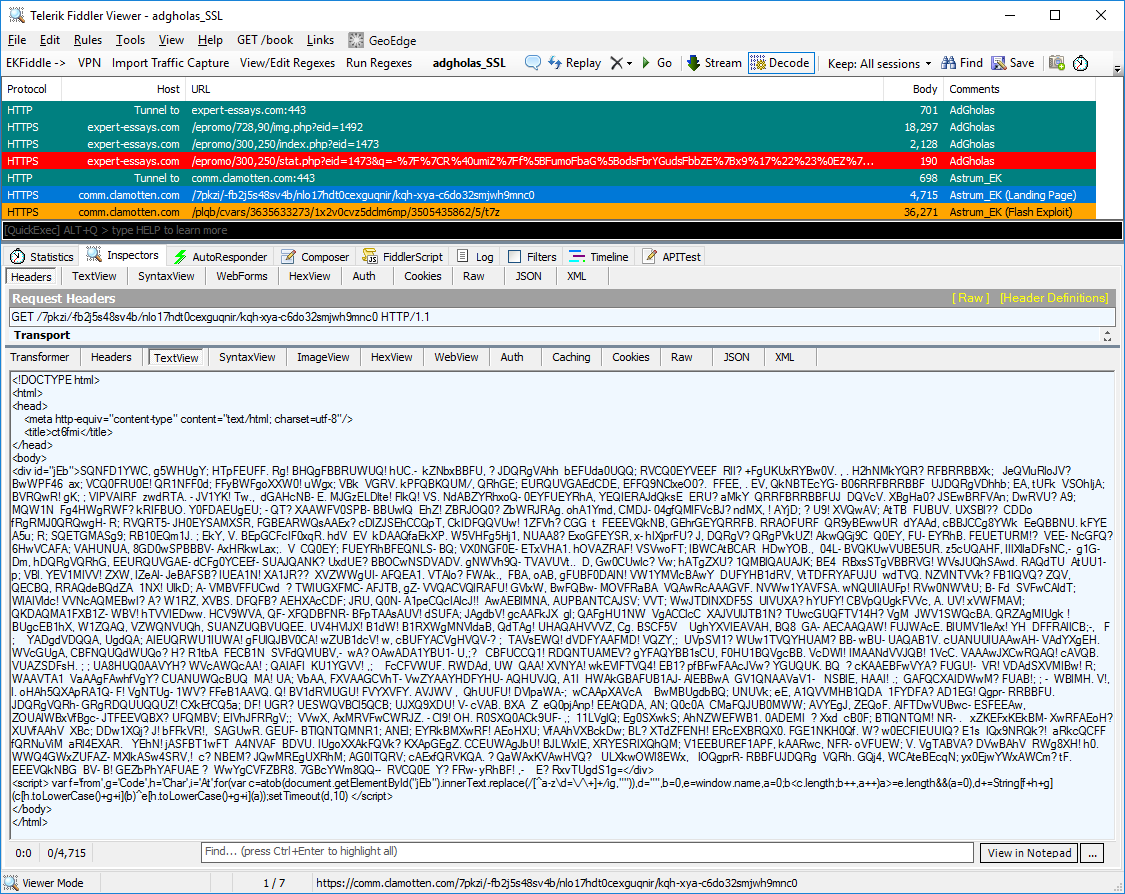
We collected artifacts that show us the redirection between the AdGholas group and the Astrum exploit kit. This kind of redirect is highly conditional in order to evade the majority of ad scanners. While many malvertising actors do not care about cloaking, it is very important to others such as AdGholas because stealthiness is a strength that contributes to its longevity.
The redirect tag hosted on expert-essays[.]com loads a landing page for the Astrum exploit kit with:
[“javascript:%27%27″,”https://comm.clamotten.com/7pkzi/-fb2j5s48sv4b/nlo17hdt0cexguqnir/kqh-xya-c6do32smjwh9mnc0″,”ae0a5bca85a8f0e1″]
The group behind Astrum EK is also very sneaky, making good use of SSL, domain shadowing and other server side tricks that render traffic collection and replay a challenge. In the current exploit kit landscape, domain shadowing has been slowed down and the popular RIG EK is mainly resorting (other than for a few exceptions) to IP addresses, in lieu of shadowed domains. As far as serving the content, plain HTTP is the norm, setting Astrum EK apart from the rest.
For a long time banking Trojans were the payload of choice for Astrum EK. This seemed to fit in with the elusive and muffled nature of the exploit kit. However, according to ProofPoint, new AdGholas/Astrum infection chains have recently been dropping ransomware. Although it’s a change from those threat actors’ style, cashing in on the ransomware frenzy makes sense.
Containment and protection
Malvertising continues to affect users on a large scale and is a relied upon infection vector for threat actors. The recent and renewed activity from sophisticated groups like AdGholas is something to watch out for in a drive-by landscape dominated by malvertising-borne attacks more so than from compromised sites.
Ad-blockers are one of several layers end users can rely on, but it is worth noting that even ad-blockers can be bypassed and do not fix the most common underlying issue which is outdated software. In other words, patching machines regularly immediately raises the difficulty level for an attacker to compromise your system. However, knowing that threat actors like AdGholas and Astrum EK are advanced and have employed zero-days, it is also important to use a signature-less and proactive defense to handle those cases.
We’re happy to report that Malwarebytes users were protected against these malvertising campaigns already.
Indicators of compromise (IOCs)
AdGholas:
expert-essays[.]com jet-travels[.]com on-tickets[.]com 5.34.180.73 162.255.119.165 185.82.218.52
Astrum Exploit Kit:
uniy[.]clamotten[.]com comm[.]clamotten[.]com comp[.]computer-tutor[.]info lexy[.]computer-tutor[.]info sior[.]ccnacertification[.]info kvely[.]our-health[.]us nuent[.]mughalplastic[.]com mtive[.]linksaffpixel[.]com cons[.]pathpixel[.]com sumer[.]pathlinkaff[.]com nsruc[.]ah7xb[.]com ction[.]ah7xb[.]com nstru[.]onlytechtalks[.]com const[.]linksaffpixel[.]com quely[.]onlytechtalks[.]com coneq[.]modweave[.]com inct[.]boundbywaves[.]com saly[.]bellportbranding[.]com dist[.]bellportbranding[.]com dist[.]slacx[.]com 94.156.174.11 94.156.174.115 SWF: 4ad7556a7ef85be260a8c10cfbc855234f0e9b8880db2be17ad0ad1d6e52909e










