Everyone knows about phishing. We’ve all heard that the solution to phishing is to educate the user as, after all, it must be the user’s fault for stupidly clicking on the thing. But what about when perverse incentives make clicking the phish seem logical? What about the enterprise pseudophish—when design-by-committee language, lack of attribution, and over broad requests for personal information make something look like a phish?
Users will frequently be inundated with corporate requests for information; requests they are often required to comply with. When companies that don’t think these things through end up with something that apes the style of a phish, they can be training their users to click on actual phishes that come their way. Let’s check out a recent example pertinent to the Anthem breach settlement a few months back.
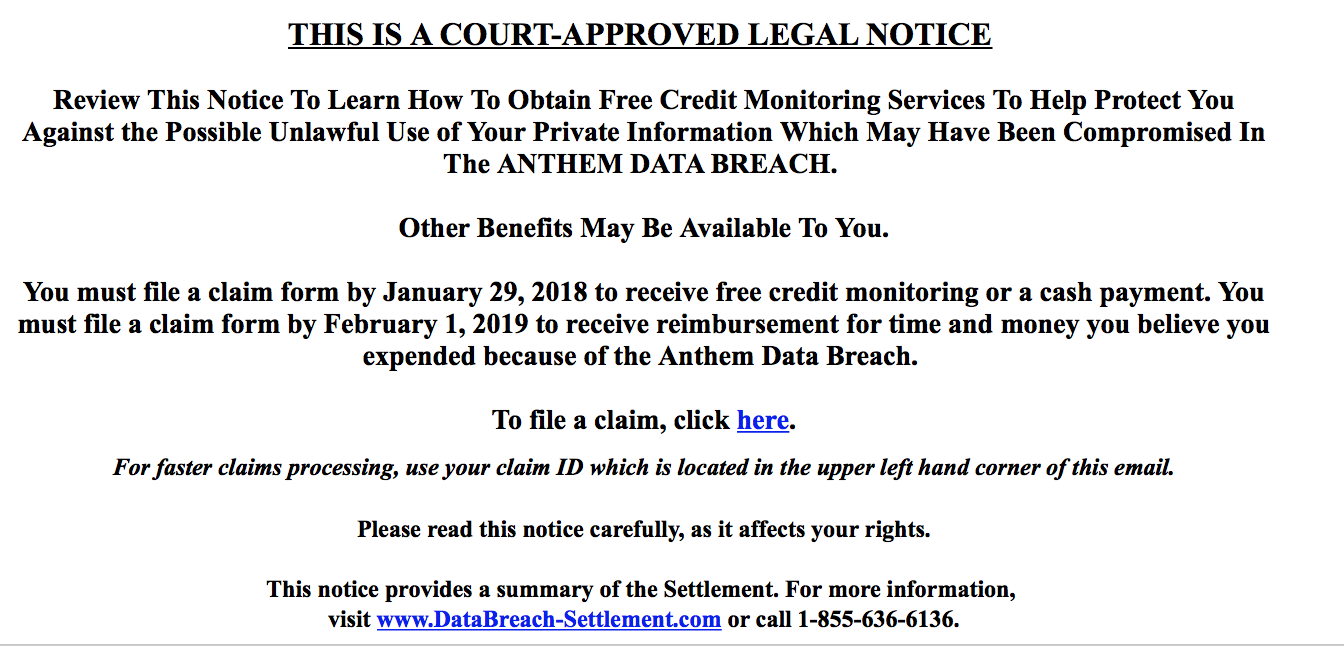
This legitimate email relies fairly heavily on the style and tone favored by phishes for decades. First of all, the email includes a lengthy “Claim ID” string without explaining what that means to the user. Next is the all-caps appeal to authority of a “court-approved legal notice.” The sender then includes an urgent call to action bounded with a deadline to induce anxiety. Lastly, they provide links with no indication of content and no direct connection to Anthem that the user is expected to click on.
Stylistically, the whole thing is a mess of odd margins and shifting formatting for no particular reason. Most concerning is that nowhere in the email does it address who the sender is, how they got your email, or what their connection to Anthem is.
Are there other ways to verify the legitimacy of the email, like examining headers, running the URL provided in a test VM first, or searching on the provided number? Of course. But can we realistically expect the user to do that for every ill-thought out communication?
User education
The presumption of many security professionals is that clicking a malicious link is a lapse in judgment or temporary insanity on the part of the user. But given the above legitimate message that the user is required to read and act upon, is it unreasonable that they would click on a Dridex malspam using the same pitch? Would we as network defenders be shocked to see a phish that looked like this? And finally, given the absurdly high volume of email most end users deal with in an office environment, aren’t we really educating them to go ahead and click?
Please don’t do this
How do you stop phishing your own users? Before you hit send, make sure of the following:
- Use consistent text formatting, spacing, and justification.
- Don’t use third-party assets unless you know the user can display them in the same way you can.
- Identify yourself, and provide a backchannel to verify who you are outside of the email. Faceless entities engaged in unsolicited contact to spur the user with an urgent call to action is a textbook phishing pitch.
- Provide the full URL to links you want clicked. One of the most basic tricks in a phish is to hide or obfuscate an URL to discourage vetting by the user.
Malspam mitigation comes with many technical fixes: disabling office Macros, blocking unnecessary outbound traffic on a given user group’s profile, or blocking local execution of scripts, to name a few. But if the ultimate fix for phishing and malspam is the user who simply deletes the offending message, a simpler (and cheaper) fix is to stop flooding them with pseudophishes. Some additional time and forethought on user experience can create incentives leading to better security outcomes for everyone. When we send a clear, consistent message on security, we all stay safer.










