A new piece of mobile malware has been discovered in Google Play masquerading as multiple apps: an alarm clock app, a QR scanner app, a compass app, a photo editor app, an Internet speed test app, and a file explorer app. According to Google Play data, all were last updated between October and November 2017. These dates are likely when they were added to Google Play, based on their low version numbers (e.g. 1.0, 1.0.1).
We named this new malware variant Android/Trojan.AsiaHitGroup based on a URL found within the code of these malicious APKs.
For the sake of discussion as we analyze this malware, let’s concentrate on just one of its associated apps, since they all share the same behavior. We will focus on a malicious QR scanner app named Qr code generator – Qr scanner.
Surface analysis of Trojan AsiaHitGroup
AsiaHitGroup has several layers of maliciousness. It starts innocently enough with an icon created on the mobile device after install. Click on the icon, and it opens a functioning QR scanner, as promised.
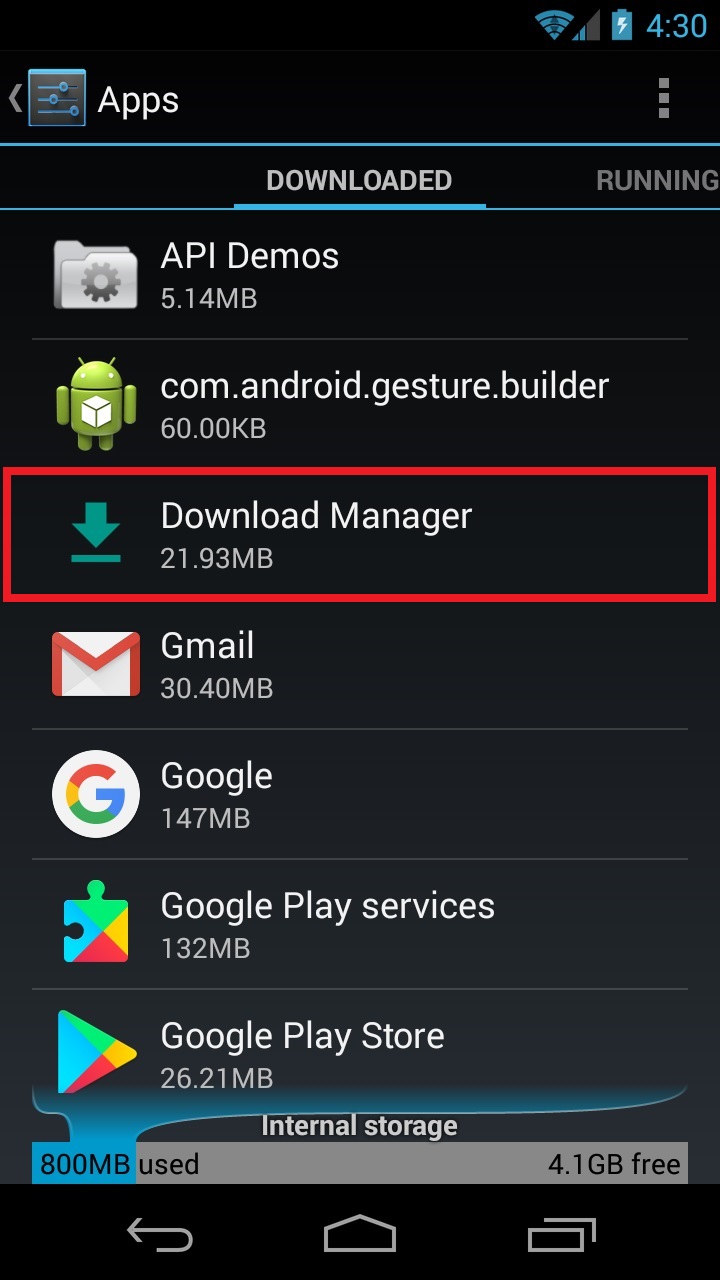
However, this QR scanner is short lived. You only get one chance to use the app, because after clicking out of it, the icon disappears! Out of frustration, you may immediately go to your apps list to uninstall this bizarre-behaving QR scanner, but good luck finding it. If you are looking under the Q’s for Qr coder generator or Qr scanner, it’s not there. It’s not even under the icon’s name, Barcode reader, which is shown briefly before vanishing. Instead, this deceiving app is called Download Manager in the app list. Unless you know all the apps on your mobile device exceptionally well, it’s near impossible to discover this app name.
Diving deeper into Trojan AsiaHitGroup
If the behaviors listed above weren’t enough to conclude this QR app is malicious, it gets worse. The first step performed by the malicious app in the background is checking the location of the mobile device. This is done by using the website ip-api.com which provides Geolocation using IP. If the location is in an area that satisfies rules within the code, then it proceeds to the next step. This next step is to download an APK by visiting a website that contains download instructions.Code from http://[hidden_domain]/api/custom/dynamic-fragment with instructions to download an APK
{">
Unfortunately during testing, the APK could not be downloaded via the malicious QR app—most likely due to my location. However, I was able to manually download the APK using the URL provided within the download instructions. The behavior of this downloaded APK was that of a Trojan SMS (which is why I subsequently named it Android/Trojan.SMS.AsiaHitGroup). Based on all the references to Asia within the code, my assumption is you must be in Asia for this malware to fully function.
Add some adware into the mix
Even if the malicious Trojan SMS fails to download, there is yet another layer to the malevolence. Hidden within the malicious QR app is another APK waiting to do its biding. However, this hidden APK is a less threatening, adware-pushing app.
The hidden adware app comes with an unusual service name: vn.solarjsc.fakeads.ShowAdsService. Within this service, there is reference to the same domain that was used to gain download instructions of the Trojan SMS. Although I was unable to verify, this domain may also contain the “fakeads” referenced in the service name. Regardless, rest assured we are detecting this hidden adware app as well as Android/Adware.AsiaHitGroup.
Google Play: not quite flawless
Even with the introduction of Google Play Protect, there appears to be no fail-proof way to stop malware from entering the Play store. This is where a second layer of protection is strongly recommended. By using a quality mobile anti-malware scanner, you can stay safe even when Google Play Protect fails. We (obviously) recommend Malwarebytes for Android. Stay safe out there!
Malicious APK samples: use at own risk
Android/Trojan.AsiaHitGroup
MD5: 178E6737A779A845B8F2BAF143FDEA15, Package Name: duy.van.dao.qrcode MD5: 7EEC1C26E60FEDE7644187B0082B6AC4, Package Name: com.varvet.barcodereader MD5: 7CEDA121F9D452E9A32B8088F50012B8, Package Name: com.maziao.alarm MD5: B481CE9D0B7295CDA33B15F9C7809B95, Package Name: com.magiaomatday.editimage MD5: 60A71632004EE431ABB28BF91C3A4982, Package Name: com.maziao.speedtest MD5: N/A, Package Name: com.ruzian.explorer
Android/Trojan.SMS.AsiaHitGroup
MD5: 3CC02E4FECEB488B084665E763968108, Package Name: duy.van.dao.dynamicduy
Android/Adware.AsiaHitGroup
MD5: 995D5DC873104B5E42B3C0AF805359DB, Package Name: com.offer.flashcall










