In the past, we used to do a blog series on exploit kits where we would periodically check in on the main players in the market. In March 2017, we wrote the Winter 2017 review, before exploit kit activity dropped down to a whisper. We’ve since discontinued our blog series, for lack of developments.
A year later, however, exploit kits are showing signs of life. An uptick in campaigns and the sharpshooter-like targeting of a single country make exploits once again worth writing about.
Overview
RIG EK still remains the most common exploit kit used by different actors in a diverse set of malvertising campaigns. We haven’t observed Terror EK since Fall 2017, but another older kit has made a comeback. And even though it remains largely unsophisticated, GrandSoft EK has maintained its activity.
While we aren’t seeing Sundown EK anymore, a spin-off named GreenFlash Sundown was the first (and only so far) to leverage a new Flash Player zero-day and distribute ransomware. Magnitude EK is the other exploit kit also consistently dropping its own Magniber ransomware.
Today’s exploit kits rely on Internet Explorer and Flash Player vulnerabilities for exploitation. We found it particularly interesting that many of those exploit kits are targeting South Korea specifically.
Coincidentally or not, both CVE-2016-0189 (IE) and CVE-2018-4878 (Flash) were both first used in targeted zero-day attacks against South Korea before they were added into EKs.
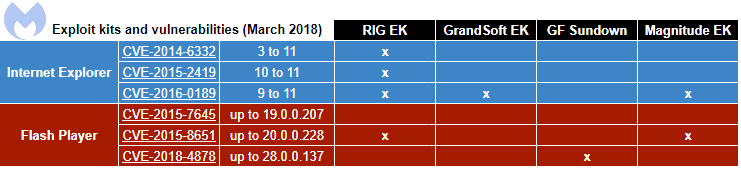
RIG-v EK
RIG EK is by far the most popular exploit kit these days, with many different distribution campaigns and, as a result, the most diverse payloads (banking Trojans, coin miners, and ransomware, to name a few).
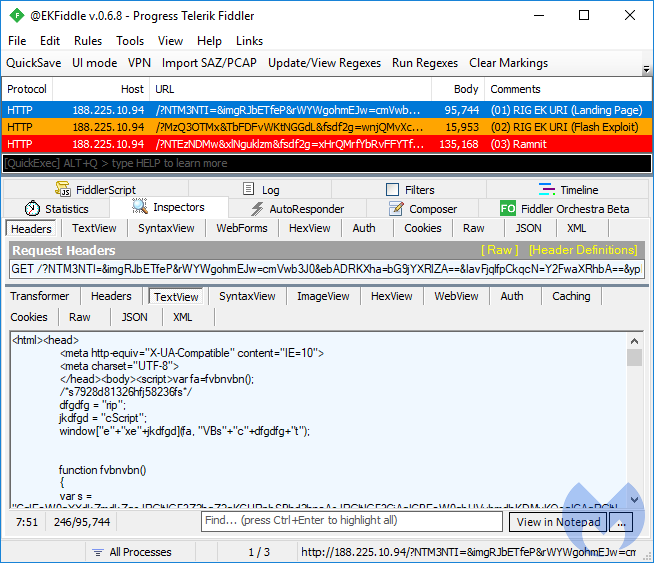
GrandSoft EK
GrandSoft is an older exploit kit that, for a strange reason, decided to make a comeback. Its code is simplistic and decipherable, and it uses rotating hostnames. GrandSoft was used to distribute the GandCrab ransomware in late January, but has also been observed dropping AZORult stealer, QuantLoader, and of course, miners.
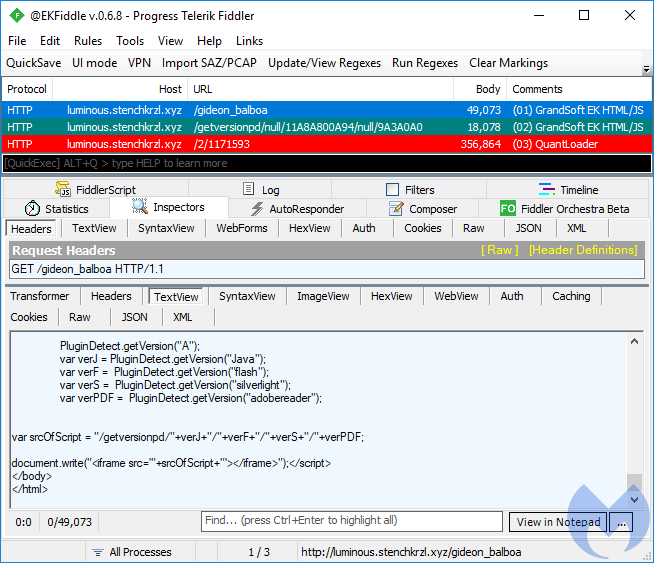
GreenFlash Sundown
GreenFlash Sundown is an interesting exploit kit that uses URI patterns that are almost impossible to match without causing false positives. It makes heavy use of the Flash Player to hide its redirections and malicious calls rather than relying on typical HTML/JS. Beyond this stealth feature, it is also the first exploit kit to integrate a newly-found Flash Player zero-day to target South Koreans with the Hermes ransomware.
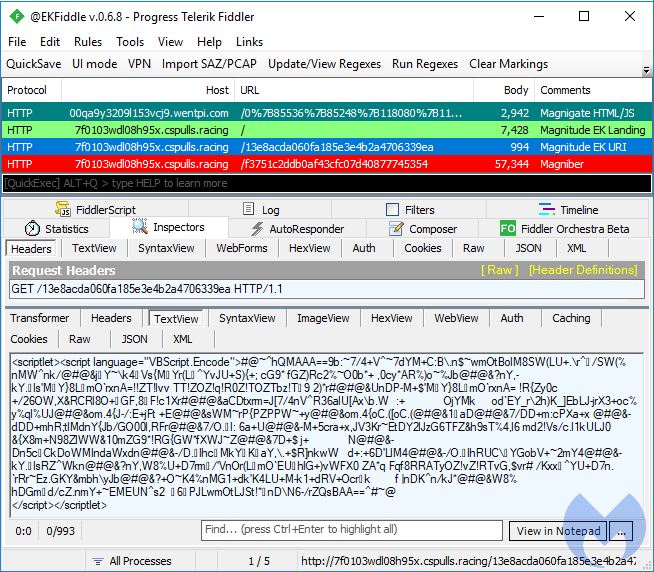
Magnitude EK
Magnitude is a long-standing exploit kit that for some time now has been exclusively focusing on South Korea. Contrary to GreenFlash Sundown, it has dropped all support for the Flash Player and only relies on Internet Explorer for exploitation. Magnitude comes with its very own payload, Magniber, a piece of ransomware that once again only targets South Korea.
Mitigation
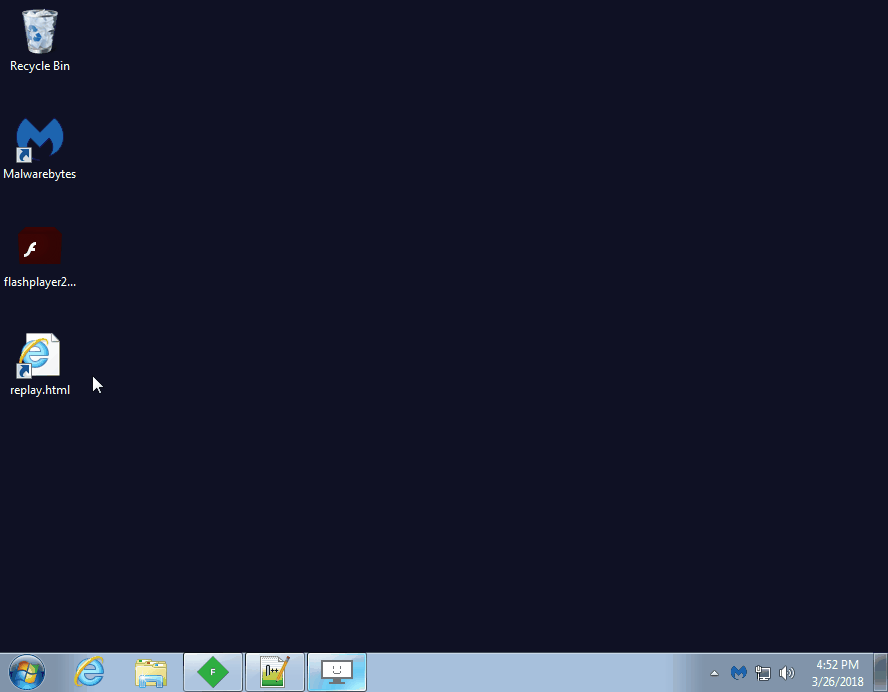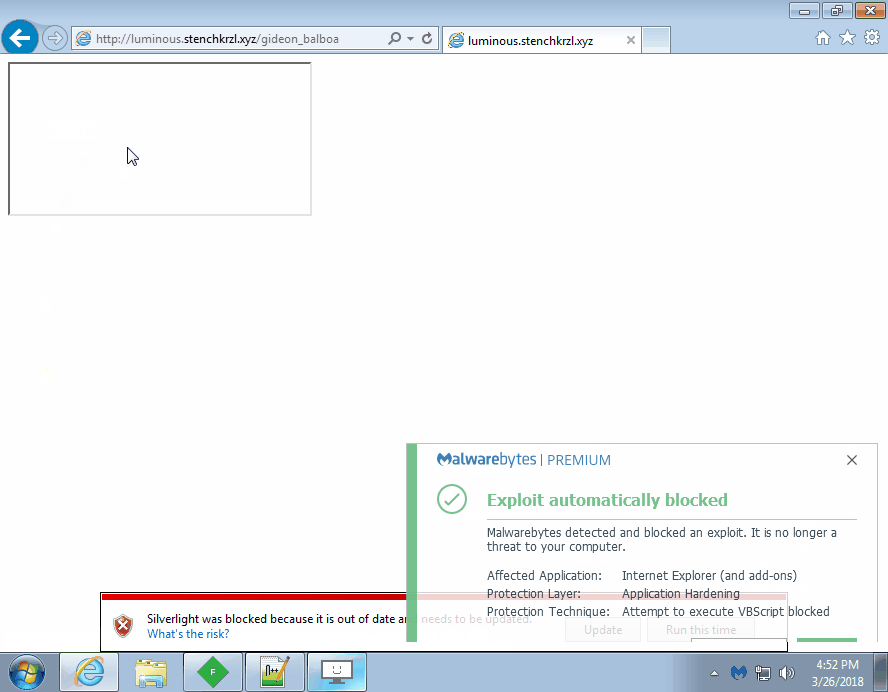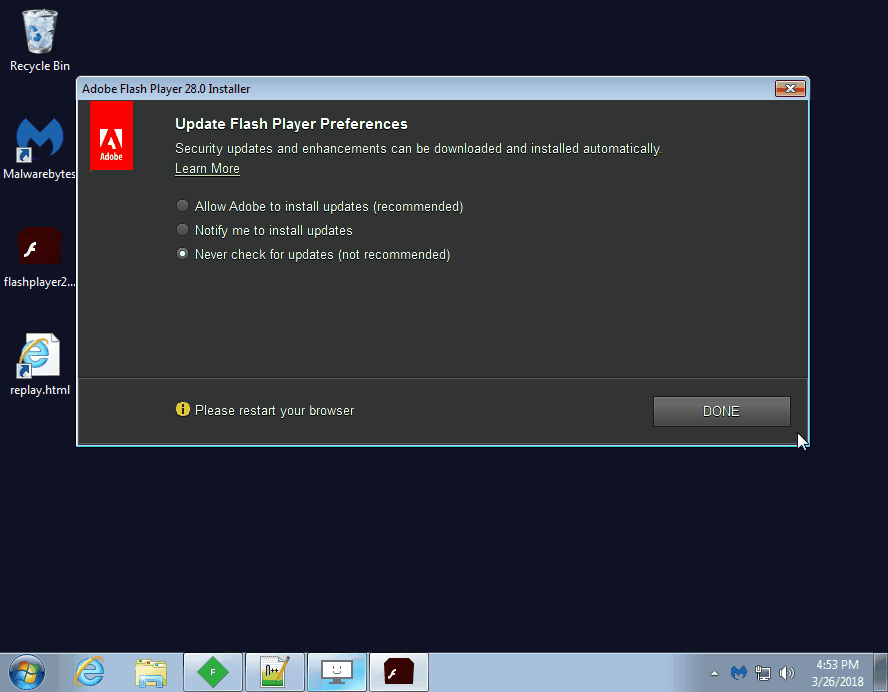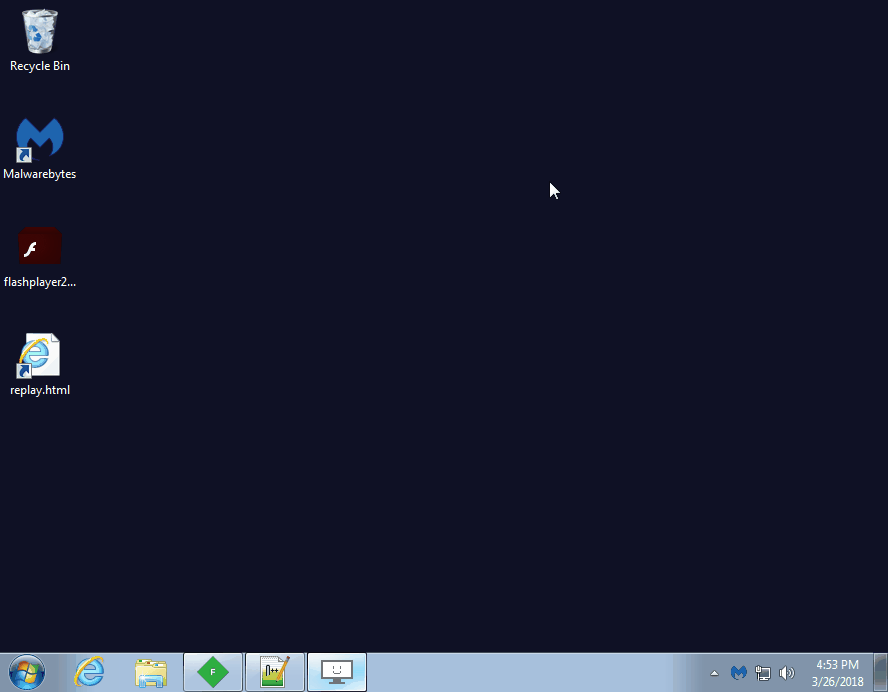
We ran all these exploit kits in our lab using Internet Explorer 10 and two different versions of the Flash Player. For GreenFlash Sundown, we updated our version of Flash to 28.0.0.137 to trigger the newest zero-day. Malwarebytes stopped all these exploit attempts before any payload had a chance to be dropped or executed.
Summary
While exploit kits are struggling to stay relevant in a browser market share dominated by Google Chrome and a rapid decline in Flash Player usage, we have noted that several different actors are still engaged in distribution via multiple malvertising chains. Some of these actors have taken over tools once used in broader campaigns to distribute their own payload and narrow down their targets to a single country.
Even though exploit kits have not evolved much in terms of firepower, the traffic distribution systems and gates leading to them remain active and diverse. For this reason, threat actors often mix traffic-based on user-agent information to divert victims toward exploit kits or social engineering–based attacks, if the former is not deemed to be a viable option.
Acknowledgment
Thanks to @nao_sec for additional information about GrandSoft EK.










