The days of ugly-looking phish pages hosted on something akin to a Geocities page are slowly receding into the distance. For quite some time now, phish attacks have made attempts to look fairly sophisticated and stand a decent chance of fooling anyone not keeping their guard up.
Today, we have a good example of this with a Netflix phish currently in circulation and (potentially) dropping into a mailbox near you. Netflix is a frequent target of all manner of scams, and is a popular go-to for phishers.
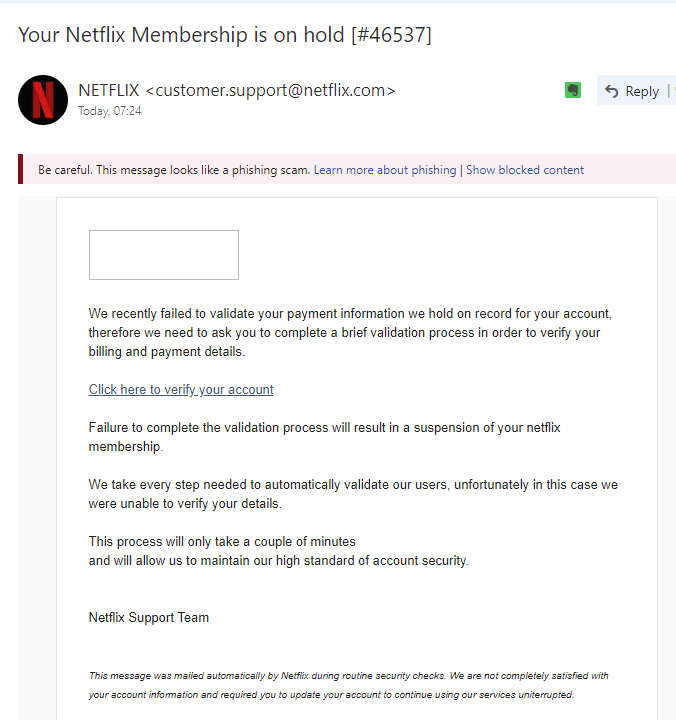
Here’s the email that kickstarts the process:
Your Netflix Membership is on hold [#46537]We recently failed to validate your payment information we hold on record for your account, therefore we need to ask you to complete a brief validation process in order to verify your billing and payment details.
Click here to verify your account
Failure to complete the validation process will result in a suspension of your netflix membership.
We take every step needed to automatically validate our users, unfortunately in this case we were unable to verify your details.
This process will only take a couple of minutes and will allow us to maintain our high standard of account security.Netflix Support Team
This message was mailed automatically by Netflix during routine security checks. We are not completely satisfied with your account information and required you to update your account to continue using our services uniterrupted.
Click to enlarge
Apart from the clunky typo in the small print, this is a fairly convincing email scam, combining someone who knows how to make an email not look terrible with the imminent threat of losing access. Having said that, you’ll notice the mail system above flagged it as suspicious anyway. This isn’t the case for all email clients, however, and one shouldn’t assume nothing slips through the cracks. The destination site, located at login(dot)netflix-activate(dot)com, appropriates a standard, no-frills Netflix login screen.
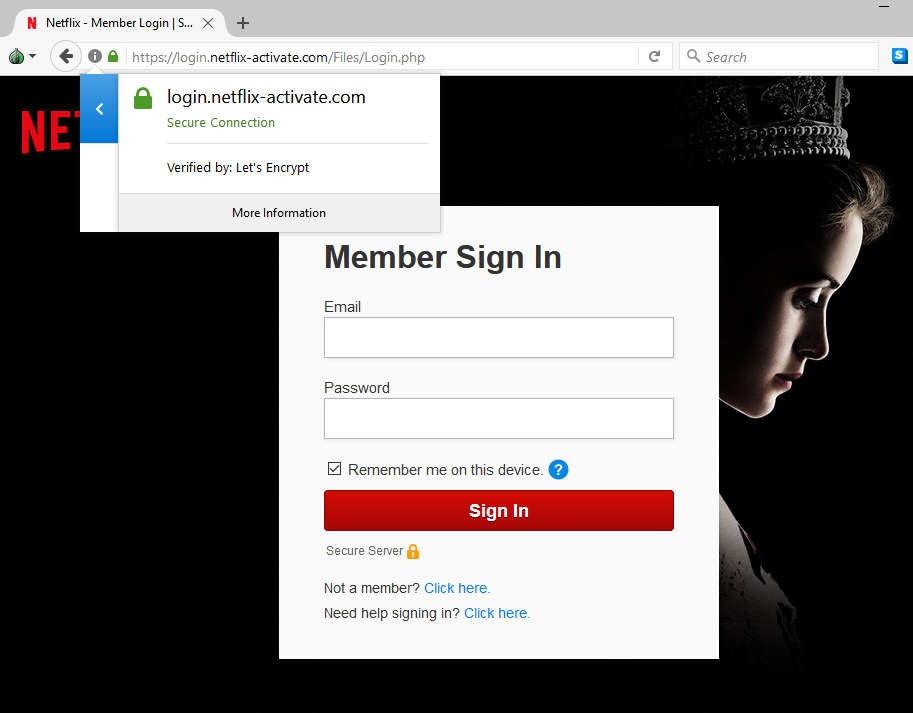
Click toeEnlarge
You’ll also notice the site makes use of HTTPS in an effort to look more convincing, via a free cert from Let’s Encrypt.
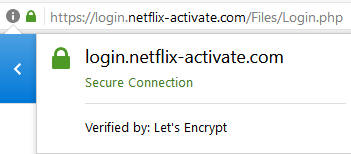
If the days of ugly phish pages are on the wane, so too are the days of advising people to look for HTTPS when working out if a site is trustworthy or not. For comparison, here’s what you see in the address bar for the real Netflix:
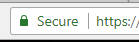
That’s really nothing you can base a “this is the real site” judgement on; all you can really do here is say that all communications on both sites are securely encrypted. But that doesn’t mean you’re securely communicating with the right people. You can, of course, click into the padlock area and see more information about the certificate issued, but for most people, that won’t help them make a decision one way or the other.
Many organisations make use of Extended Validation certificates, which display your name in the padlock area in return for additional auditing to make sure you’re who you claim to be. Visit Paypal’s website if you want to see an example of this. There is some criticism of these certs, but in general it’s a useful visual aid.
Anyway, onto the phish itself, which consists of a grab for personal information including name, address, phone number, and date of birth:
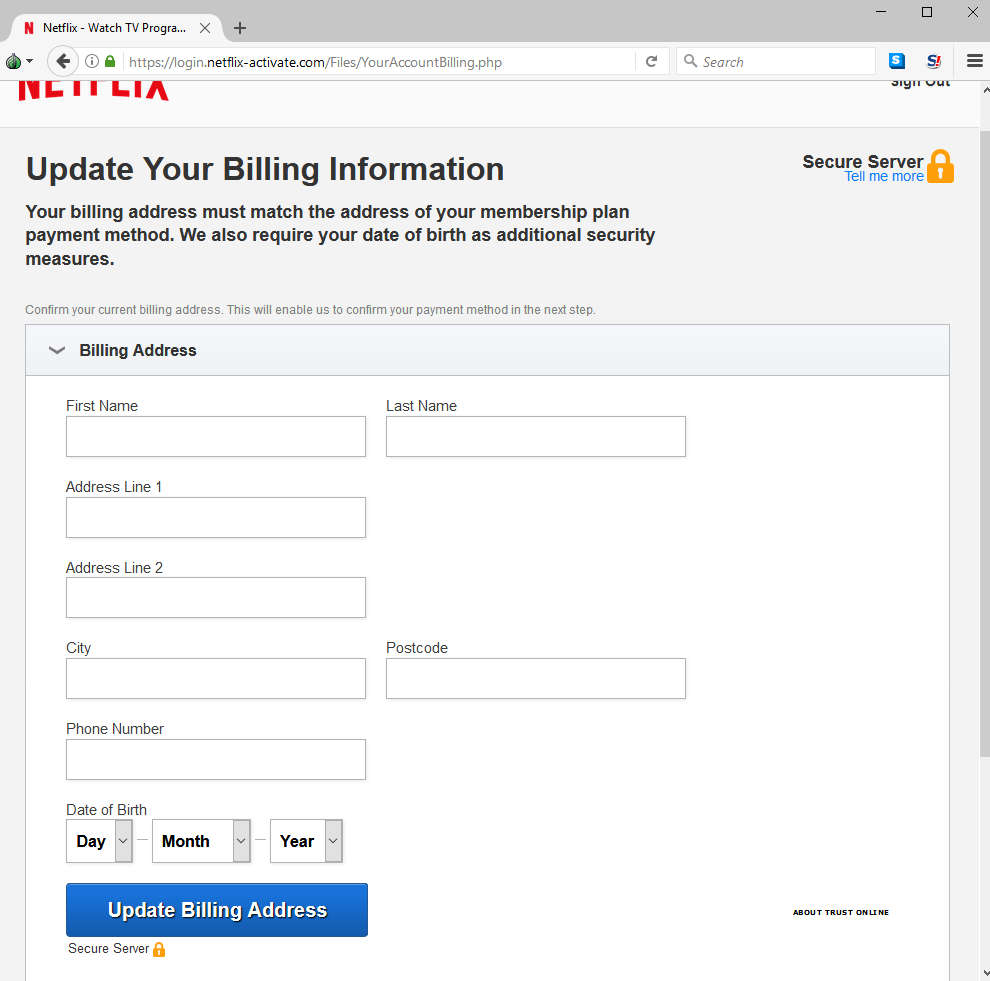
Click to enlarge
After that, they try and swipe payment information, asking for the name as written on the card, card number, expiry date, security code, and even a cheap grab at a security question answer for good measure.
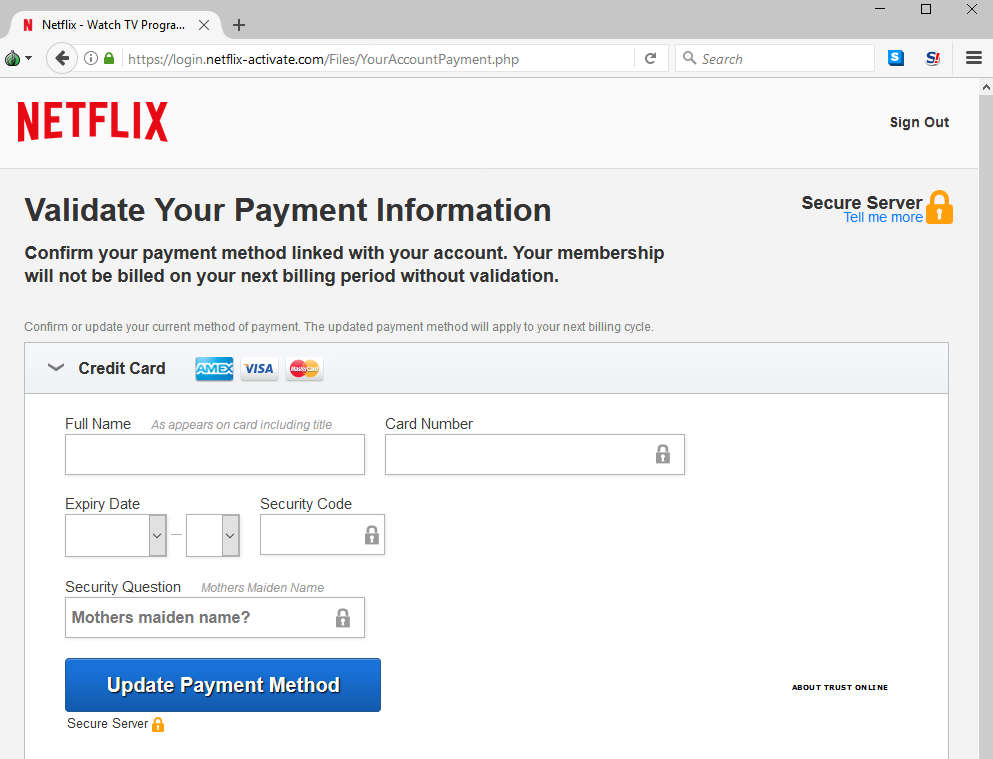
Click to enlarge
Once everything has been entered into the site, the scammer presents the victim with a splash page claiming everything is now up to date:
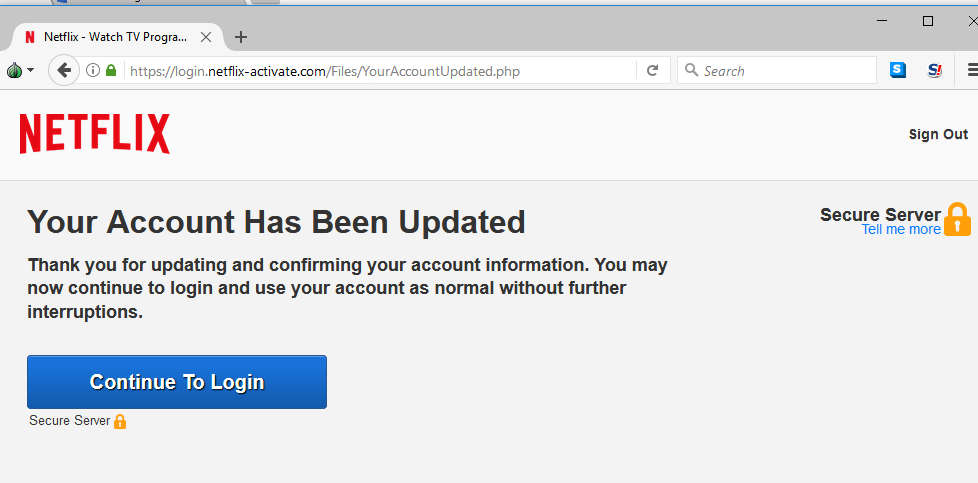
Click to enlarge
It reads as follows:
Your account has been updated.Thank you for updating and confirming your account information. You may now continue to login and use your account as normal without further interruptions.
After this, there’s nothing left for the scammer to do except gently coax the now phished website visitor to click the button and be directed to the real Netflix website. They’ll likely be blissfully unaware anything is untoward until the scammers try to make fraudulent transactions on their card.
These emails follow a similar format as the Apple phishes in February, and indeed quite a few others going around at the moment (also Apple-centric, so constant service-related vigilance is the order of the day). Phishing emails won’t be going away anytime soon, and the people behind them keep striving to make their fake-outs ever more believable. It’s up to us to do what we can, and consign their sneaky missives to the recycle bin. Your bank account will thank you for it.