I suppose we all get our share of spam. Some more than others. But how do we differentiate between simple commercial spam and the types of emails that want to get us in trouble?
The unsolicited commercial spam email is generally easy to recognize, report, and discard, but what about more dangerous types of spam? How can you determine if an email contains a malicious link or attachment, or is trying to scam you out of money or your personal information?
And if you do discover you have malicious emails in your inbox, what then? Is reporting as spam and deleting the email enough?
Knowing what you are up against helps you determine what to do with all that spam—whether it’s simply a nuisance or a landmine waiting to detonate.
Five red flags for spotting malicious emails
Before we jump into determining what to do with a malicious email, there are a few general tricks users should learn to spot red flags for malicious activity. They are as follows:
1. The sender address isn’t correct.
Check if this address matches the name of the sender and whether the domain of the company is correct. To see this, you have to make sure your email client displays the sender’s email address and not just their display name. Sometimes you need to train hawk eyes at the address, since spammers have some convincing tricks up their sleeve. For example:
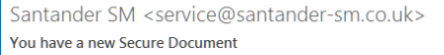
In this example sender’s address, the email domain does not match the actual bank’s domain, which is santander.co.uk.
2. The sender doesn’t seem to know the addressee.
Is the recipient name spelled out in the email, and are you being addressed as you would expect from the sender? Does the signature match how this sender would usually sign their mails to you? Your bank usually does not address you in generic ways like “Dear customer.” If the email is legit and clearly intended for you, then they will use your full name.
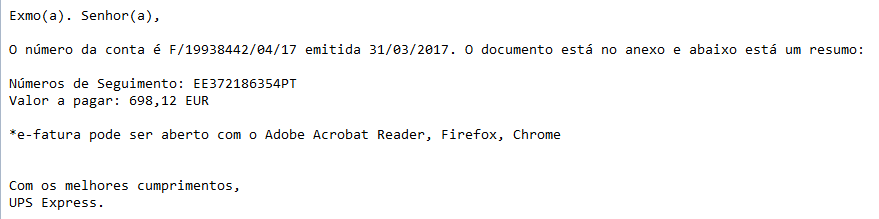
This one is not only in the wrong language, but it is addressed to no one in particular, and is not signed with an employee name you could contact for further information.
3. Embedded links have weird URLs.
Always hover first over the links in the email. Do not click immediately. Does the destination URL match the destination site you would expect? (Once again, train those eagle eyes.) Will it download a file? Are they using a link shortening service? When in doubt, if you have a shortcut to the site of the company sending you the email, use that method instead of clicking the link in the email.
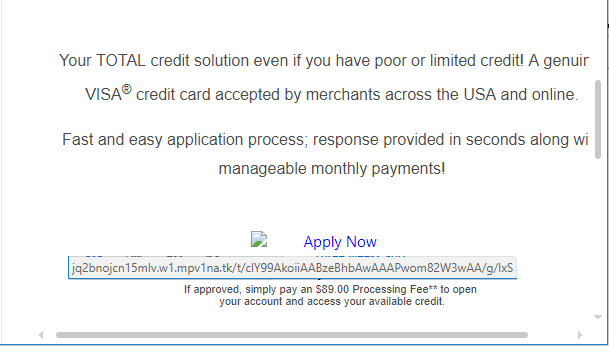
When I hover over “Apply Now,” does that link look like something VISA would use?
4. The language, spelling, and grammar are “off.”
Is the email full of spelling errors, or does it look like someone used an online translation service to translate the mail to your language?
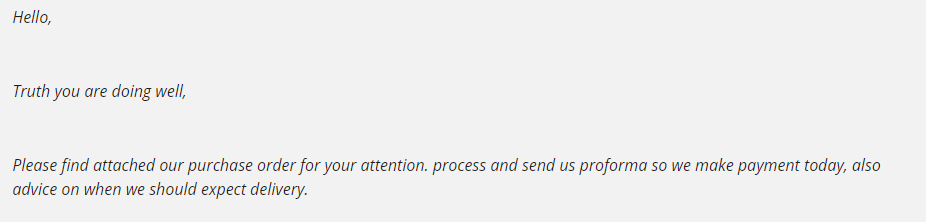
Does this look like it came from a native English speaker? In fact, it was a very intricate phishing attempt.
5. The content is bizarre or unbelievable.
If it is too good to be true, it probably isn’t true. People with lost relatives that leave you huge estates or suitcases full of dollars in some far-away country are not as common as these scammers would have us believe. You can recognize when email spam is trying to phish for money by its promises to deliver great gain in return for a small investment. For historical reasons, we call this type of spam “Nigerian prince” or “419” spam.

Part of a long and entertaining mail about how the FBI is investigating a Facebook promo where you won US$10,000,000.
So is it really malicious?
Please note that you need to weigh all the elements above if you want to rule them out as spam or malicious. Each of them is a red flag by itself—even if the other elements look legitimate. And, even if all of the above red flags have been cross-checked and determined as sound, that doesn’t rule out the possibility of the email still being malicious.
Sender addresses can be spoofed, signatures can be stolen or mimicked, domains can be typosquatted, accounts can be hacked, and the spelling and translation services among spammers are improving rapidly, as spammers have noticed that it improves their success rate. It’s also not always immediately clear from the content if the email is spam, scam, or bona fide truth. Some malspam authors have shown great creativity in coming up with believable stories to tell.
So when all else checks out but your gut tells you something is off, there are other edicts to keep in mind when determining whether an email could be misleading.
1. Companies just don’t do this.
Reputable banks do not send you unsolicited mails asking for credentials, they do not use link shortening services, and they will certainly not ask you to send your credit or debit card to them by (snail) mail. The IRS and Microsoft will not email you to tell you that you owe them money or that your computer has a virus. There are certain things that organizations just will not do—but threat actors like to fool users by seeming to come from a legitimate, scary company.
2. There are attachments.
First and foremost: do not, under any circumstances, open any attachments that you were not expecting. It’s as easy as that. If you receive an attachment without forewarning from a company or individual that you do not know, do not double-click on it. If it’s from a friend, acquaintance, or company that you do business with, it is necessary to check with the sender to see if it is safe to open the attachment.
3. There’s a call-to-action button.
Some dangerous spam emails do not come with malicious attachments but instead try to trick you into downloading a malicious file, courtesy of the call-to-action button. This button is simply a fancy embedded link that is meant to draw eyes and clicks. You can examine the call-to-action button in the same way you do links—by hovering over it. If you’re not sure, check with the sender and/or simply delete the email.
4. They are phishing for information.
Another type of dangerous spam is the type that phishes for information. This information does not necessarily have to concern you directly; it can be about the company you work for or someone you know well. Password credentials and credit card numbers aren’t the only data threat actors look to steal via malicious email. Always be cautious, always stay suspicious, until you can verify that the person requesting this information is who they say they are.
What to do with a suspected malicious email
The answer to this is quite simple: delete the email. You can ignore it and let it fester in your inbox or you can get rid of it and send it to trash, where it will be permanently dumped from your email client in a set amount of time. You may also want to report the email as spam before you delete—most email platforms have this functionality built in, and some are better than others are tracking and blocking these types of emails. Reporting the malicious email as spam will not hurt—if anything, it’s giving your email client important intel in the fight against malspam and can keep future similar emails coming to bother you again.
Finally, many banks and other financial companies have a special email address where you can send emails that you suspect to be phishing attempts. They will thank you if you are right about your suspicion. If you’re wrong and it is from them, they might consider changing their email practices to be less spammy.
Safe practices when receiving mail
If you want to be proactive against malicious emails, there are some tips and tools we recommend that will give you the opportunity to safely perform all the checks we have recommended earlier on. This includes changing some default settings in your email client (though yours may already have them in place by default.) Our recommendations are as follows:
- “Disable HTML” or “Read in plain text”: This lessens the chance of malicious scripts being executed as soon as you open the email. If you don’t want to disable HTML, then we would recommend closing the preview window. That will allow you to delete suspect emails from your inbox before giving them a chance to do any harm.
- Make sure you can see the full URL when you hover over a link in an email message. This is built into in most email clients by default. But if it’s not, we highly recommend enabling it.
- Make sure you can see the full email address of the sender when you first look at it. This is one of the main indicators that something might be “phishy.”
- If you have the option to use a spam filter, please use it. It will stop big waves of known spam. It does not make you completely safe, but it saves you a lot of work.
- We have said this before, but it’s really important: Please do not open any attachments that you weren’t expecting. The old misconception that only executable attachments can harm you is not true. Documents, PDFs, and other attachments are just as potentially dangerous.
If you are still unsure whether an email is malicious or just regular spam after checking all the points we stipulated, simply delete the email and go about your day.
If the email contains information you think could be important if legitimate, however, contact the sender in any other way besides using the “reply” option. For example, if it’s your bank, give them a call and ask if they really sent you something and whether it’s safe to open. Chances are, they didn’t—and they’ll be glad you reported the scoundrels for using their name.
Credits
Thanks to My Online Security for providing me with examples and screenshots. You can find his blog with many, many examples of phishing mails at myonlinesecurity.co.uk.











