Update (2019-03-21)
A proof of concept for CVE-2019-5786 was published by Exodus Intel. In our earlier post we exercised caution before claiming we would have blocked this zero-day, but we can now say with confidence that an older version of Malwarebytes (1.12.1.122) would have mitigated this attack:
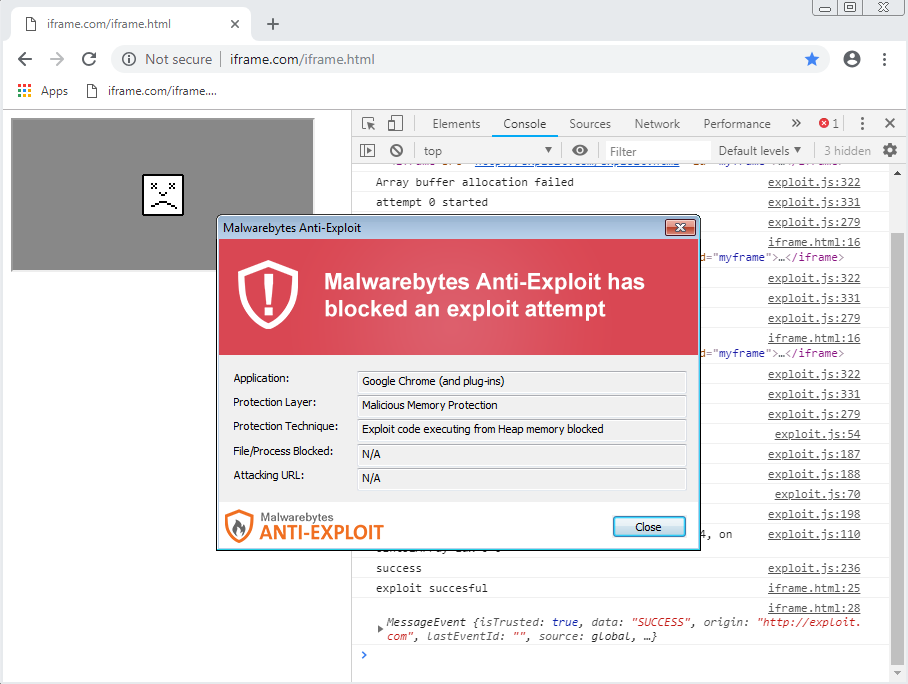
This shows the benefits for certain applications from being allowed to inject into Chrome, something that Google’s new policies have disabled.
—
It’s not often that we hear about a critical vulnerability in Google Chrome, and perhaps it’s even more rare when Google’s own engineers are urging users to patch.
There are several good reasons why you need to take this new Chrome zero-day (CVE-2019-5786) seriously. For starters, we are talking about a full exploitation that escapes the sandbox and leads to remote code execution. This in itself is not an easy feat, and is usually observed only sporadically, perhaps during a Pwn2Own competition. But this time, Google is saying that this vulnerability is actively being used in the wild.
According to Clément Lecigne, the person from Google’s Threat Analysis Group who discovered the attack, there is another zero-day that exists in Microsoft Windows (yet to be patched), suggesting the two could be chained up for even greater damage.
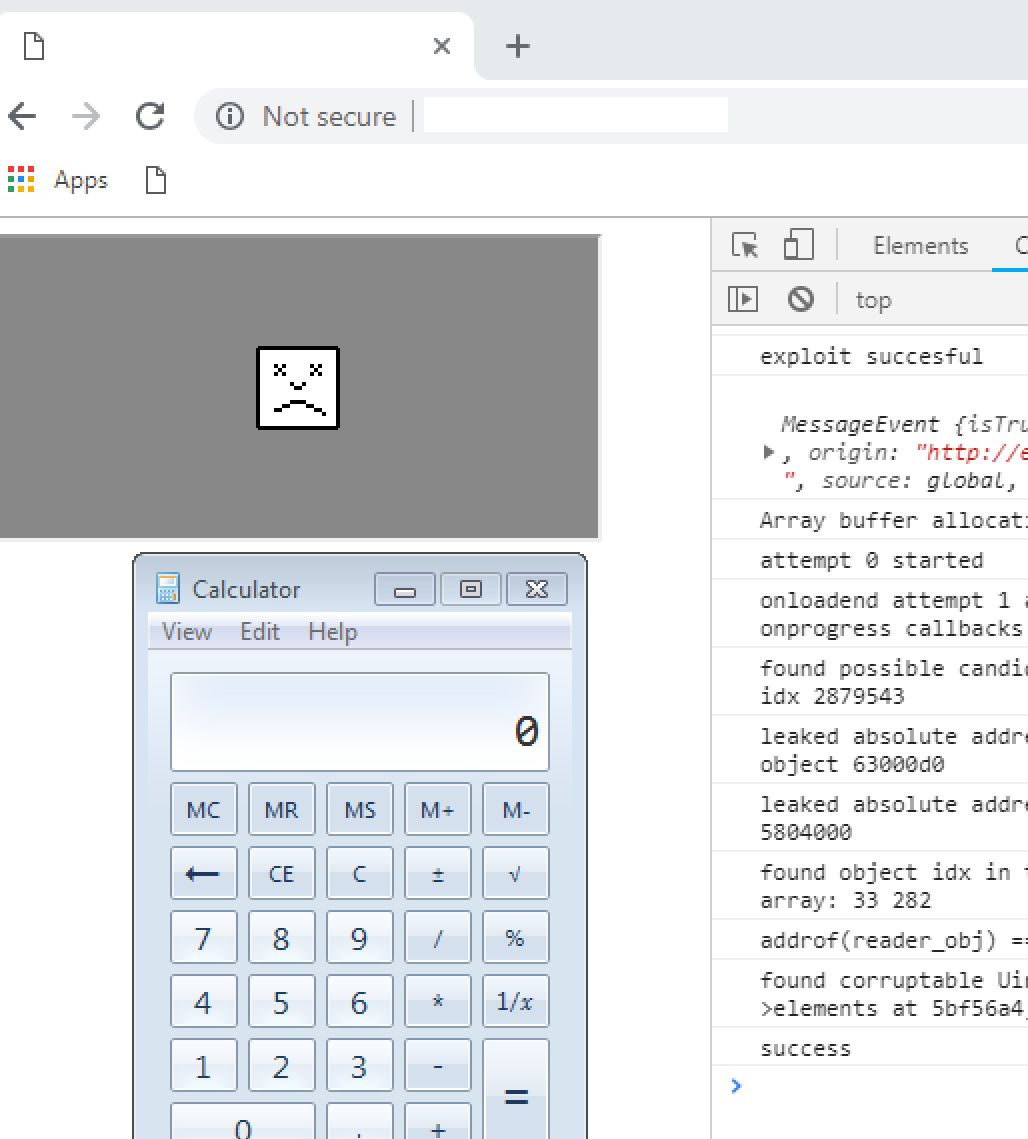
If you are running Google Chrome and its version is below 72.0.3626.121, your computer could be exploited without your knowledge. While it’s true that Chrome features an automatic update component, in order for the patch to be installed you must restart your browser.
This may not seem like a big deal but it is. Another Google engineer explains why this matters a lot, in comparison to past exploits:
https://twitter.com/justinschuh/status/1103763266445037568
Considering how many users keep Chrome and all their tabs opened for days or even weeks without ever restarting the browser, the security impact is real.
Some might see a bit of irony with this latest zero-day considering Google’s move to ban third-party software injections. Many security programs, including Malwarebytes, need to hook into processes, such as the browser and common Office applications, in order to detect and block exploits from happening. However, we cannot say for sure whether or not this could prevent the vulnerability from being exploited, since few details have been shared yet.
In the meantime, if you haven’t done so yet, you should update and relaunch Chrome; and don’t worry about your tabs, they will come right back.










