
Mitigation and take down
Malwarebytes’ browser extension was already blocking the various browlock pages heuristically.
We immediately reported the fraudulent ads to Google and Microsoft (Bing), as well as the decoy blogs to GoDaddy. The majority of their domains have been taken down already and their ad campaigns banned.
This tech support scam campaign cleverly targeted an older segment of the population by using paid search results for food recipes via online portals used by many Internet Service Providers.
There is no doubt scammers will continue to abuse ad platforms and hosting providers to carry out their business. However, industry cooperation for takedowns can set them back and save thousands of victims from being defrauded.
Indicators of compromise
Decoy blogs
alhotcake[.]com
bestrecipesus[.]com
cheforrecipes[.]com
chilly-recipesfood[.]com
cookwellrecipes[.]com
dezirerecipes[.]com
dinnerplusrecipes[.]com
dinnerrecipiesforu.com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
healthycookingidea[.]com
recipesstudios[.]com
a2zpcprotection[.]com
a2zcleanerpro[.]com
Regex to match browlock URIs on Azure
^http(s|)://(?!www)^.{2}[a-z]{2,7}/([cC]all-([nN]ow|Support)1|chx|macx|(Call-)?[mM]ac-[sS]upport)

And then, there are two new recipe sites that were both registered in June and, as with previous ones, they also use content copied from other places:

Mitigation and take down
Malwarebytes’ browser extension was already blocking the various browlock pages heuristically.

We immediately reported the fraudulent ads to Google and Microsoft (Bing), as well as the decoy blogs to GoDaddy. The majority of their domains have been taken down already and their ad campaigns banned.
This tech support scam campaign cleverly targeted an older segment of the population by using paid search results for food recipes via online portals used by many Internet Service Providers.
There is no doubt scammers will continue to abuse ad platforms and hosting providers to carry out their business. However, industry cooperation for takedowns can set them back and save thousands of victims from being defrauded.
Indicators of compromise
Decoy blogs
alhotcake[.]com
bestrecipesus[.]com
cheforrecipes[.]com
chilly-recipesfood[.]com
cookwellrecipes[.]com
dezirerecipes[.]com
dinnerplusrecipes[.]com
dinnerrecipiesforu.com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
healthycookingidea[.]com
recipesstudios[.]com
a2zpcprotection[.]com
a2zcleanerpro[.]com
Regex to match browlock URIs on Azure
^http(s|)://(?!www)^.{2}[a-z]{2,7}/([cC]all-([nN]ow|Support)1|chx|macx|(Call-)?[mM]ac-[sS]upport)
Their webste is hosted at 198.57.219.8, where we found two other interesting artifacts. The first one is a company named CoreTel that is also used by the scammers as a kind of business entity. It appears to be a rip off from another domain that pre-existed by several years and also hosted on the same IP adddress:

And then, there are two new recipe sites that were both registered in June and, as with previous ones, they also use content copied from other places:

Mitigation and take down
Malwarebytes’ browser extension was already blocking the various browlock pages heuristically.

We immediately reported the fraudulent ads to Google and Microsoft (Bing), as well as the decoy blogs to GoDaddy. The majority of their domains have been taken down already and their ad campaigns banned.
This tech support scam campaign cleverly targeted an older segment of the population by using paid search results for food recipes via online portals used by many Internet Service Providers.
There is no doubt scammers will continue to abuse ad platforms and hosting providers to carry out their business. However, industry cooperation for takedowns can set them back and save thousands of victims from being defrauded.
Indicators of compromise
Decoy blogs
alhotcake[.]com
bestrecipesus[.]com
cheforrecipes[.]com
chilly-recipesfood[.]com
cookwellrecipes[.]com
dezirerecipes[.]com
dinnerplusrecipes[.]com
dinnerrecipiesforu.com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
healthycookingidea[.]com
recipesstudios[.]com
a2zpcprotection[.]com
a2zcleanerpro[.]com
Regex to match browlock URIs on Azure
^http(s|)://(?!www)^.{2}[a-z]{2,7}/([cC]all-([nN]ow|Support)1|chx|macx|(Call-)?[mM]ac-[sS]upport)
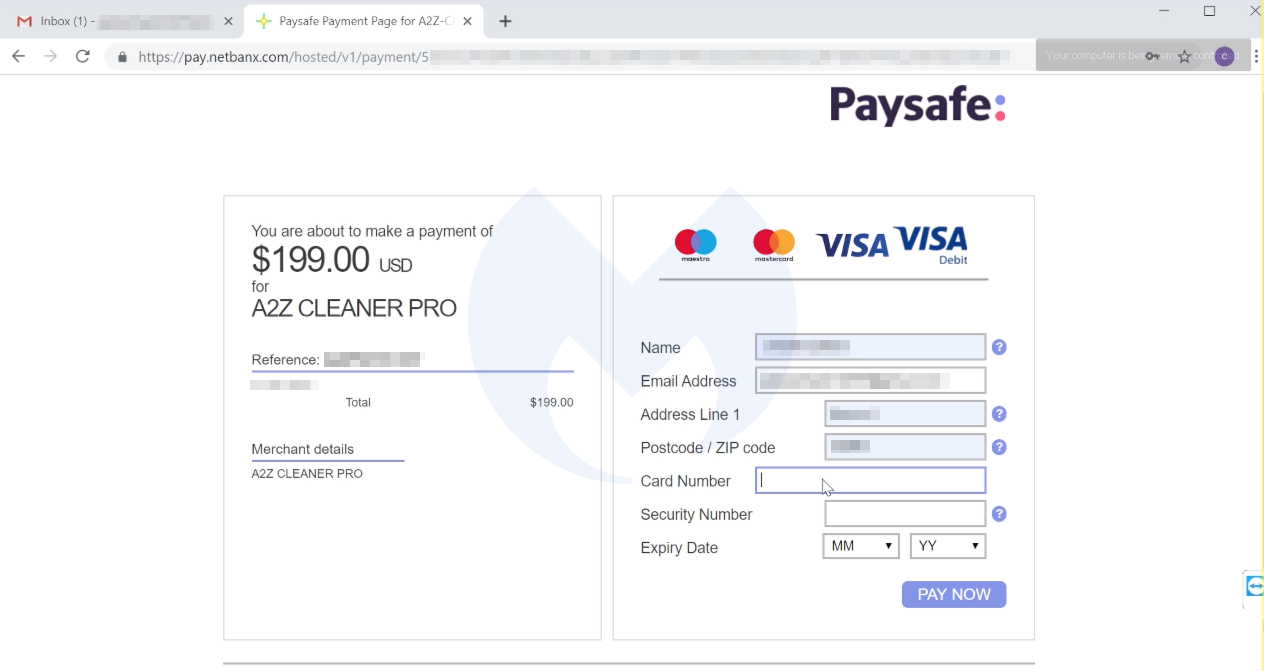
The company selling those services is A2Z Cleaner Pro (AKA Coretel Communications) and was previously identified by one victim in August 2018 in a blog comment on the FTC’s website.

Their webste is hosted at 198.57.219.8, where we found two other interesting artifacts. The first one is a company named CoreTel that is also used by the scammers as a kind of business entity. It appears to be a rip off from another domain that pre-existed by several years and also hosted on the same IP adddress:

And then, there are two new recipe sites that were both registered in June and, as with previous ones, they also use content copied from other places:

Mitigation and take down
Malwarebytes’ browser extension was already blocking the various browlock pages heuristically.

We immediately reported the fraudulent ads to Google and Microsoft (Bing), as well as the decoy blogs to GoDaddy. The majority of their domains have been taken down already and their ad campaigns banned.
This tech support scam campaign cleverly targeted an older segment of the population by using paid search results for food recipes via online portals used by many Internet Service Providers.
There is no doubt scammers will continue to abuse ad platforms and hosting providers to carry out their business. However, industry cooperation for takedowns can set them back and save thousands of victims from being defrauded.
Indicators of compromise
Decoy blogs
alhotcake[.]com
bestrecipesus[.]com
cheforrecipes[.]com
chilly-recipesfood[.]com
cookwellrecipes[.]com
dezirerecipes[.]com
dinnerplusrecipes[.]com
dinnerrecipiesforu.com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
healthycookingidea[.]com
recipesstudios[.]com
a2zpcprotection[.]com
a2zcleanerpro[.]com
Regex to match browlock URIs on Azure
^http(s|)://(?!www)^.{2}[a-z]{2,7}/([cC]all-([nN]ow|Support)1|chx|macx|(Call-)?[mM]ac-[sS]upport)
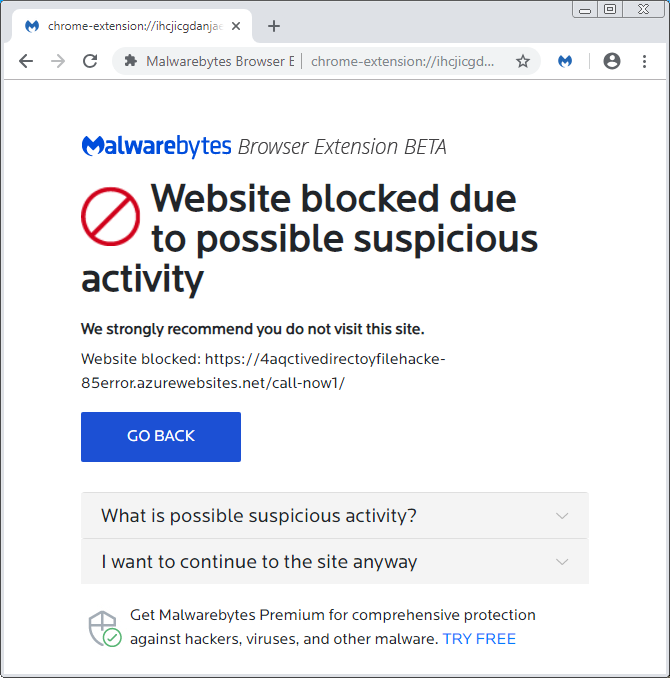
The scammers often register entire ranges of hostnames on Azure by iterating through numbers attached to random strings. While many of those pages are taken down quickly, new ones are constantly popping back up in order to keep the campaign running. Here are some URI patterns we observed:
10-server[.]azurewebsites[.]net/call-now1/
2securityxew-561error[.]azurewebsites[.]net/Call-Now1/
10serverloadingfailed-hgdfc777error[.]azurewebsites[.]net/chx/
11iohhwefuown[.]azurewebsites[.]net/Call-Support1/
11serversecurityjunkfile-65error[.]azurewebsites[.]net/Call-Mac-Support/
2serverdatacrash-de-12error[.]azurewebsites[.]net/macx/
2systemservertemporaryblockghjj-510error[.]azurewebsites[.]net/mac-support/
We believe the crooks may also be rotating the decoy site that performs the redirect in addition to the existing user filtering in order to evade detection from security scanners.
Finding the perpetrators
We do not condone interacting with scammers directly, but part of this investigation was about finding who was behind this campaign in order to take action and spare more victims.
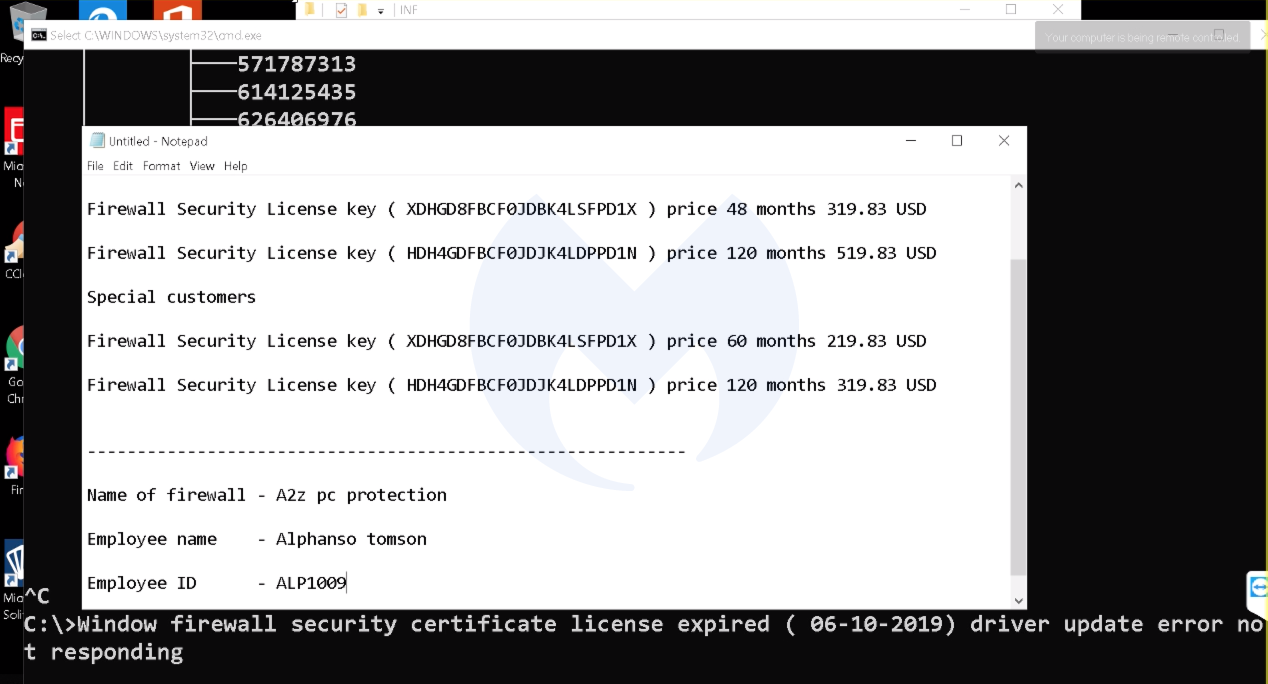
To continue on with deception, the rogue technicians lied to us about the state of our computer and made up imaginary threats. The goal was to sell expensive support packages that actually add little value.

The company selling those services is A2Z Cleaner Pro (AKA Coretel Communications) and was previously identified by one victim in August 2018 in a blog comment on the FTC’s website.

Their webste is hosted at 198.57.219.8, where we found two other interesting artifacts. The first one is a company named CoreTel that is also used by the scammers as a kind of business entity. It appears to be a rip off from another domain that pre-existed by several years and also hosted on the same IP adddress:

And then, there are two new recipe sites that were both registered in June and, as with previous ones, they also use content copied from other places:

Mitigation and take down
Malwarebytes’ browser extension was already blocking the various browlock pages heuristically.

We immediately reported the fraudulent ads to Google and Microsoft (Bing), as well as the decoy blogs to GoDaddy. The majority of their domains have been taken down already and their ad campaigns banned.
This tech support scam campaign cleverly targeted an older segment of the population by using paid search results for food recipes via online portals used by many Internet Service Providers.
There is no doubt scammers will continue to abuse ad platforms and hosting providers to carry out their business. However, industry cooperation for takedowns can set them back and save thousands of victims from being defrauded.
Indicators of compromise
Decoy blogs
alhotcake[.]com
bestrecipesus[.]com
cheforrecipes[.]com
chilly-recipesfood[.]com
cookwellrecipes[.]com
dezirerecipes[.]com
dinnerplusrecipes[.]com
dinnerrecipiesforu.com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
healthycookingidea[.]com
recipesstudios[.]com
a2zpcprotection[.]com
a2zcleanerpro[.]com
Regex to match browlock URIs on Azure
^http(s|)://(?!www)^.{2}[a-z]{2,7}/([cC]all-([nN]ow|Support)1|chx|macx|(Call-)?[mM]ac-[sS]upport)
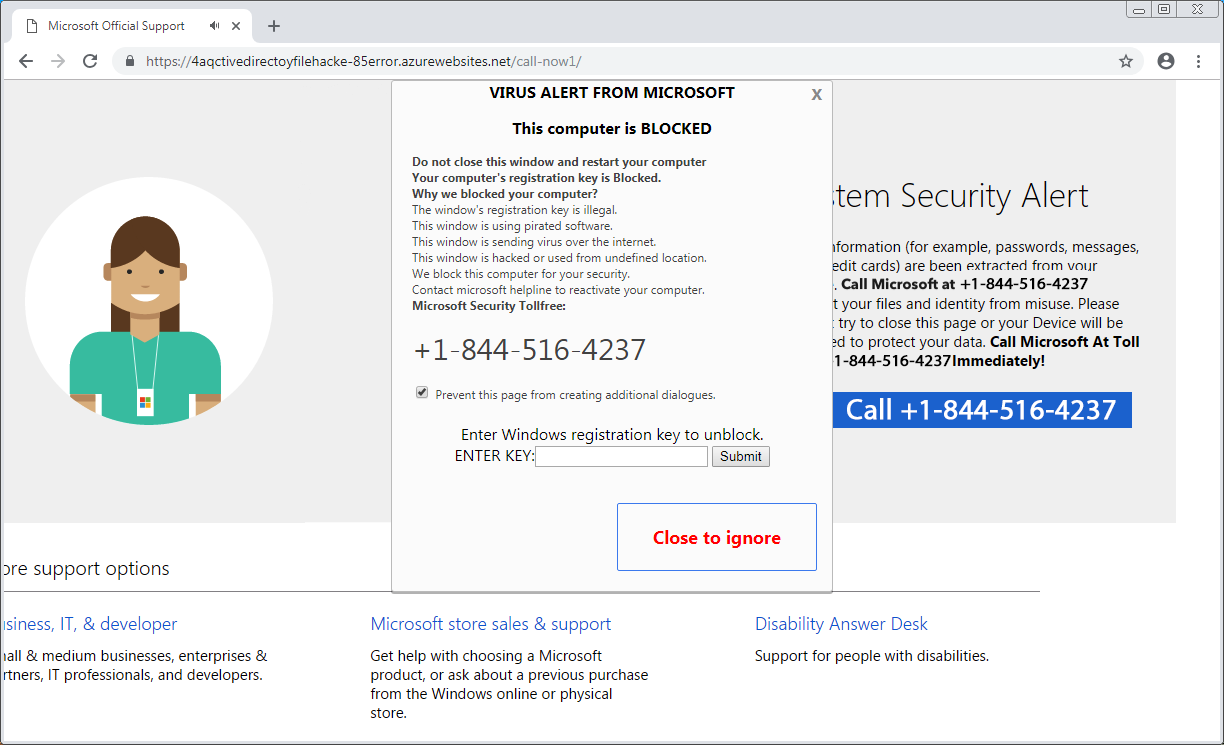
Browlock page
The fake warning page is fairly standard. It checks for the type of browser and operating system in order to display the appropriate template to Windows and Mac OS victims.

The scammers often register entire ranges of hostnames on Azure by iterating through numbers attached to random strings. While many of those pages are taken down quickly, new ones are constantly popping back up in order to keep the campaign running. Here are some URI patterns we observed:
10-server[.]azurewebsites[.]net/call-now1/
2securityxew-561error[.]azurewebsites[.]net/Call-Now1/
10serverloadingfailed-hgdfc777error[.]azurewebsites[.]net/chx/
11iohhwefuown[.]azurewebsites[.]net/Call-Support1/
11serversecurityjunkfile-65error[.]azurewebsites[.]net/Call-Mac-Support/
2serverdatacrash-de-12error[.]azurewebsites[.]net/macx/
2systemservertemporaryblockghjj-510error[.]azurewebsites[.]net/mac-support/
We believe the crooks may also be rotating the decoy site that performs the redirect in addition to the existing user filtering in order to evade detection from security scanners.
Finding the perpetrators
We do not condone interacting with scammers directly, but part of this investigation was about finding who was behind this campaign in order to take action and spare more victims.
To continue on with deception, the rogue technicians lied to us about the state of our computer and made up imaginary threats. The goal was to sell expensive support packages that actually add little value.

The company selling those services is A2Z Cleaner Pro (AKA Coretel Communications) and was previously identified by one victim in August 2018 in a blog comment on the FTC’s website.

Their webste is hosted at 198.57.219.8, where we found two other interesting artifacts. The first one is a company named CoreTel that is also used by the scammers as a kind of business entity. It appears to be a rip off from another domain that pre-existed by several years and also hosted on the same IP adddress:

And then, there are two new recipe sites that were both registered in June and, as with previous ones, they also use content copied from other places:

Mitigation and take down
Malwarebytes’ browser extension was already blocking the various browlock pages heuristically.

We immediately reported the fraudulent ads to Google and Microsoft (Bing), as well as the decoy blogs to GoDaddy. The majority of their domains have been taken down already and their ad campaigns banned.
This tech support scam campaign cleverly targeted an older segment of the population by using paid search results for food recipes via online portals used by many Internet Service Providers.
There is no doubt scammers will continue to abuse ad platforms and hosting providers to carry out their business. However, industry cooperation for takedowns can set them back and save thousands of victims from being defrauded.
Indicators of compromise
Decoy blogs
alhotcake[.]com
bestrecipesus[.]com
cheforrecipes[.]com
chilly-recipesfood[.]com
cookwellrecipes[.]com
dezirerecipes[.]com
dinnerplusrecipes[.]com
dinnerrecipiesforu.com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
healthycookingidea[.]com
recipesstudios[.]com
a2zpcprotection[.]com
a2zcleanerpro[.]com
Regex to match browlock URIs on Azure
^http(s|)://(?!www)^.{2}[a-z]{2,7}/([cC]all-([nN]ow|Support)1|chx|macx|(Call-)?[mM]ac-[sS]upport)
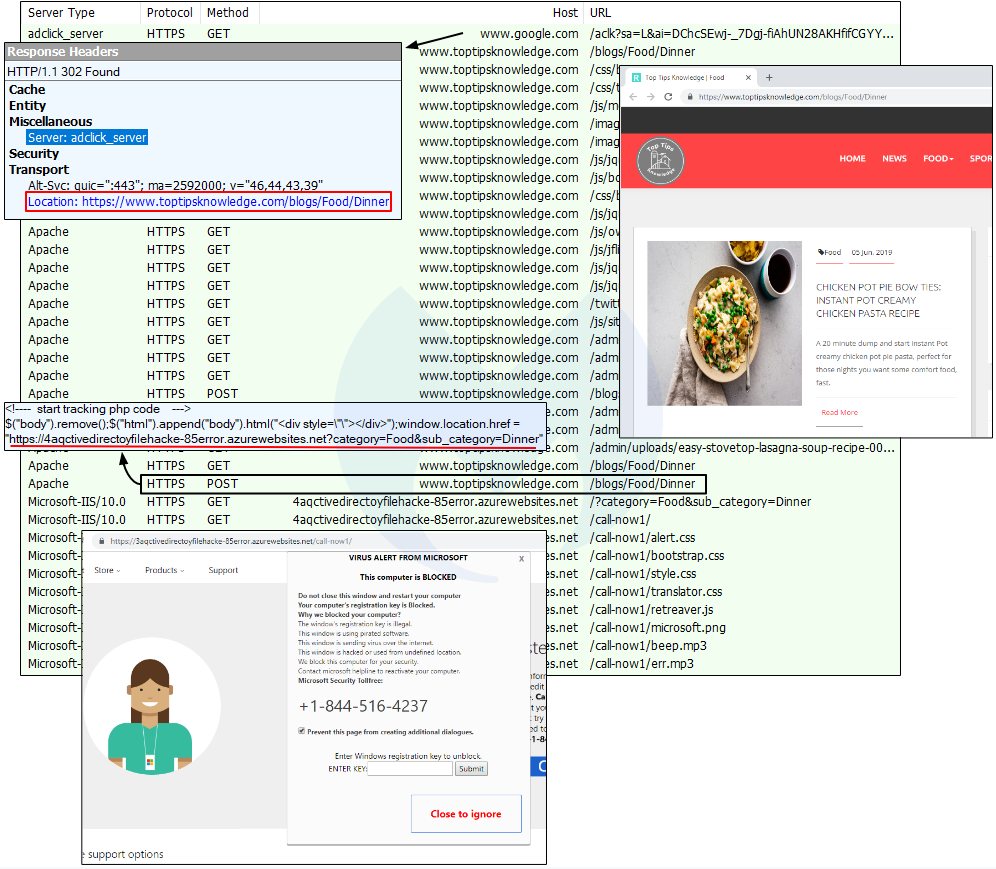
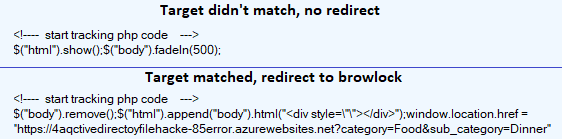
The blog’s URL is actually called three consecutive times, and the last one performs a POST request with the eventual conditional redirect to the browlock. In the screenshot below, you can see the difference between proper cloaking (no malicious behavior) and the redirect to a browlock page:

Browlock page
The fake warning page is fairly standard. It checks for the type of browser and operating system in order to display the appropriate template to Windows and Mac OS victims.

The scammers often register entire ranges of hostnames on Azure by iterating through numbers attached to random strings. While many of those pages are taken down quickly, new ones are constantly popping back up in order to keep the campaign running. Here are some URI patterns we observed:
10-server[.]azurewebsites[.]net/call-now1/
2securityxew-561error[.]azurewebsites[.]net/Call-Now1/
10serverloadingfailed-hgdfc777error[.]azurewebsites[.]net/chx/
11iohhwefuown[.]azurewebsites[.]net/Call-Support1/
11serversecurityjunkfile-65error[.]azurewebsites[.]net/Call-Mac-Support/
2serverdatacrash-de-12error[.]azurewebsites[.]net/macx/
2systemservertemporaryblockghjj-510error[.]azurewebsites[.]net/mac-support/
We believe the crooks may also be rotating the decoy site that performs the redirect in addition to the existing user filtering in order to evade detection from security scanners.
Finding the perpetrators
We do not condone interacting with scammers directly, but part of this investigation was about finding who was behind this campaign in order to take action and spare more victims.
To continue on with deception, the rogue technicians lied to us about the state of our computer and made up imaginary threats. The goal was to sell expensive support packages that actually add little value.

The company selling those services is A2Z Cleaner Pro (AKA Coretel Communications) and was previously identified by one victim in August 2018 in a blog comment on the FTC’s website.

Their webste is hosted at 198.57.219.8, where we found two other interesting artifacts. The first one is a company named CoreTel that is also used by the scammers as a kind of business entity. It appears to be a rip off from another domain that pre-existed by several years and also hosted on the same IP adddress:

And then, there are two new recipe sites that were both registered in June and, as with previous ones, they also use content copied from other places:

Mitigation and take down
Malwarebytes’ browser extension was already blocking the various browlock pages heuristically.

We immediately reported the fraudulent ads to Google and Microsoft (Bing), as well as the decoy blogs to GoDaddy. The majority of their domains have been taken down already and their ad campaigns banned.
This tech support scam campaign cleverly targeted an older segment of the population by using paid search results for food recipes via online portals used by many Internet Service Providers.
There is no doubt scammers will continue to abuse ad platforms and hosting providers to carry out their business. However, industry cooperation for takedowns can set them back and save thousands of victims from being defrauded.
Indicators of compromise
Decoy blogs
alhotcake[.]com
bestrecipesus[.]com
cheforrecipes[.]com
chilly-recipesfood[.]com
cookwellrecipes[.]com
dezirerecipes[.]com
dinnerplusrecipes[.]com
dinnerrecipiesforu.com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
healthycookingidea[.]com
recipesstudios[.]com
a2zpcprotection[.]com
a2zcleanerpro[.]com
Regex to match browlock URIs on Azure
^http(s|)://(?!www)^.{2}[a-z]{2,7}/([cC]all-([nN]ow|Support)1|chx|macx|(Call-)?[mM]ac-[sS]upport)
During our testing, visiting those sites directly did not create any malicious redirection, and they seemed to be absolutely benign. With only circumstantial evidence and without the so-called smoking gun, a case could not be made just yet.
Full infection chain
After some trial and error that included swapping various User-Agent strings and avoiding using commercial VPNs, we eventually were able to replay a full infection chain, from the original advert to the browser locker page.

The blog’s URL is actually called three consecutive times, and the last one performs a POST request with the eventual conditional redirect to the browlock. In the screenshot below, you can see the difference between proper cloaking (no malicious behavior) and the redirect to a browlock page:

Browlock page
The fake warning page is fairly standard. It checks for the type of browser and operating system in order to display the appropriate template to Windows and Mac OS victims.

The scammers often register entire ranges of hostnames on Azure by iterating through numbers attached to random strings. While many of those pages are taken down quickly, new ones are constantly popping back up in order to keep the campaign running. Here are some URI patterns we observed:
10-server[.]azurewebsites[.]net/call-now1/
2securityxew-561error[.]azurewebsites[.]net/Call-Now1/
10serverloadingfailed-hgdfc777error[.]azurewebsites[.]net/chx/
11iohhwefuown[.]azurewebsites[.]net/Call-Support1/
11serversecurityjunkfile-65error[.]azurewebsites[.]net/Call-Mac-Support/
2serverdatacrash-de-12error[.]azurewebsites[.]net/macx/
2systemservertemporaryblockghjj-510error[.]azurewebsites[.]net/mac-support/
We believe the crooks may also be rotating the decoy site that performs the redirect in addition to the existing user filtering in order to evade detection from security scanners.
Finding the perpetrators
We do not condone interacting with scammers directly, but part of this investigation was about finding who was behind this campaign in order to take action and spare more victims.
To continue on with deception, the rogue technicians lied to us about the state of our computer and made up imaginary threats. The goal was to sell expensive support packages that actually add little value.

The company selling those services is A2Z Cleaner Pro (AKA Coretel Communications) and was previously identified by one victim in August 2018 in a blog comment on the FTC’s website.

Their webste is hosted at 198.57.219.8, where we found two other interesting artifacts. The first one is a company named CoreTel that is also used by the scammers as a kind of business entity. It appears to be a rip off from another domain that pre-existed by several years and also hosted on the same IP adddress:

And then, there are two new recipe sites that were both registered in June and, as with previous ones, they also use content copied from other places:

Mitigation and take down
Malwarebytes’ browser extension was already blocking the various browlock pages heuristically.

We immediately reported the fraudulent ads to Google and Microsoft (Bing), as well as the decoy blogs to GoDaddy. The majority of their domains have been taken down already and their ad campaigns banned.
This tech support scam campaign cleverly targeted an older segment of the population by using paid search results for food recipes via online portals used by many Internet Service Providers.
There is no doubt scammers will continue to abuse ad platforms and hosting providers to carry out their business. However, industry cooperation for takedowns can set them back and save thousands of victims from being defrauded.
Indicators of compromise
Decoy blogs
alhotcake[.]com
bestrecipesus[.]com
cheforrecipes[.]com
chilly-recipesfood[.]com
cookwellrecipes[.]com
dezirerecipes[.]com
dinnerplusrecipes[.]com
dinnerrecipiesforu.com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
healthycookingidea[.]com
recipesstudios[.]com
a2zpcprotection[.]com
a2zcleanerpro[.]com
Regex to match browlock URIs on Azure
^http(s|)://(?!www)^.{2}[a-z]{2,7}/([cC]all-([nN]ow|Support)1|chx|macx|(Call-)?[mM]ac-[sS]upport)
However, upon closer inspection, we can see that those sites have basically taken content from various web developer sites offering paid or free HTML templates. “ 
During our testing, visiting those sites directly did not create any malicious redirection, and they seemed to be absolutely benign. With only circumstantial evidence and without the so-called smoking gun, a case could not be made just yet.
Full infection chain
After some trial and error that included swapping various User-Agent strings and avoiding using commercial VPNs, we eventually were able to replay a full infection chain, from the original advert to the browser locker page.

The blog’s URL is actually called three consecutive times, and the last one performs a POST request with the eventual conditional redirect to the browlock. In the screenshot below, you can see the difference between proper cloaking (no malicious behavior) and the redirect to a browlock page:

Browlock page
The fake warning page is fairly standard. It checks for the type of browser and operating system in order to display the appropriate template to Windows and Mac OS victims.

The scammers often register entire ranges of hostnames on Azure by iterating through numbers attached to random strings. While many of those pages are taken down quickly, new ones are constantly popping back up in order to keep the campaign running. Here are some URI patterns we observed:
10-server[.]azurewebsites[.]net/call-now1/
2securityxew-561error[.]azurewebsites[.]net/Call-Now1/
10serverloadingfailed-hgdfc777error[.]azurewebsites[.]net/chx/
11iohhwefuown[.]azurewebsites[.]net/Call-Support1/
11serversecurityjunkfile-65error[.]azurewebsites[.]net/Call-Mac-Support/
2serverdatacrash-de-12error[.]azurewebsites[.]net/macx/
2systemservertemporaryblockghjj-510error[.]azurewebsites[.]net/mac-support/
We believe the crooks may also be rotating the decoy site that performs the redirect in addition to the existing user filtering in order to evade detection from security scanners.
Finding the perpetrators
We do not condone interacting with scammers directly, but part of this investigation was about finding who was behind this campaign in order to take action and spare more victims.
To continue on with deception, the rogue technicians lied to us about the state of our computer and made up imaginary threats. The goal was to sell expensive support packages that actually add little value.

The company selling those services is A2Z Cleaner Pro (AKA Coretel Communications) and was previously identified by one victim in August 2018 in a blog comment on the FTC’s website.

Their webste is hosted at 198.57.219.8, where we found two other interesting artifacts. The first one is a company named CoreTel that is also used by the scammers as a kind of business entity. It appears to be a rip off from another domain that pre-existed by several years and also hosted on the same IP adddress:

And then, there are two new recipe sites that were both registered in June and, as with previous ones, they also use content copied from other places:

Mitigation and take down
Malwarebytes’ browser extension was already blocking the various browlock pages heuristically.

We immediately reported the fraudulent ads to Google and Microsoft (Bing), as well as the decoy blogs to GoDaddy. The majority of their domains have been taken down already and their ad campaigns banned.
This tech support scam campaign cleverly targeted an older segment of the population by using paid search results for food recipes via online portals used by many Internet Service Providers.
There is no doubt scammers will continue to abuse ad platforms and hosting providers to carry out their business. However, industry cooperation for takedowns can set them back and save thousands of victims from being defrauded.
Indicators of compromise
Decoy blogs
alhotcake[.]com
bestrecipesus[.]com
cheforrecipes[.]com
chilly-recipesfood[.]com
cookwellrecipes[.]com
dezirerecipes[.]com
dinnerplusrecipes[.]com
dinnerrecipiesforu.com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
healthycookingidea[.]com
recipesstudios[.]com
a2zpcprotection[.]com
a2zcleanerpro[.]com
Regex to match browlock URIs on Azure
^http(s|)://(?!www)^.{2}[a-z]{2,7}/([cC]all-([nN]ow|Support)1|chx|macx|(Call-)?[mM]ac-[sS]upport)
While those ads look typical and actually match our keyword search quite well, they actually redirect to websites created with malicious intent.
Decoy websites
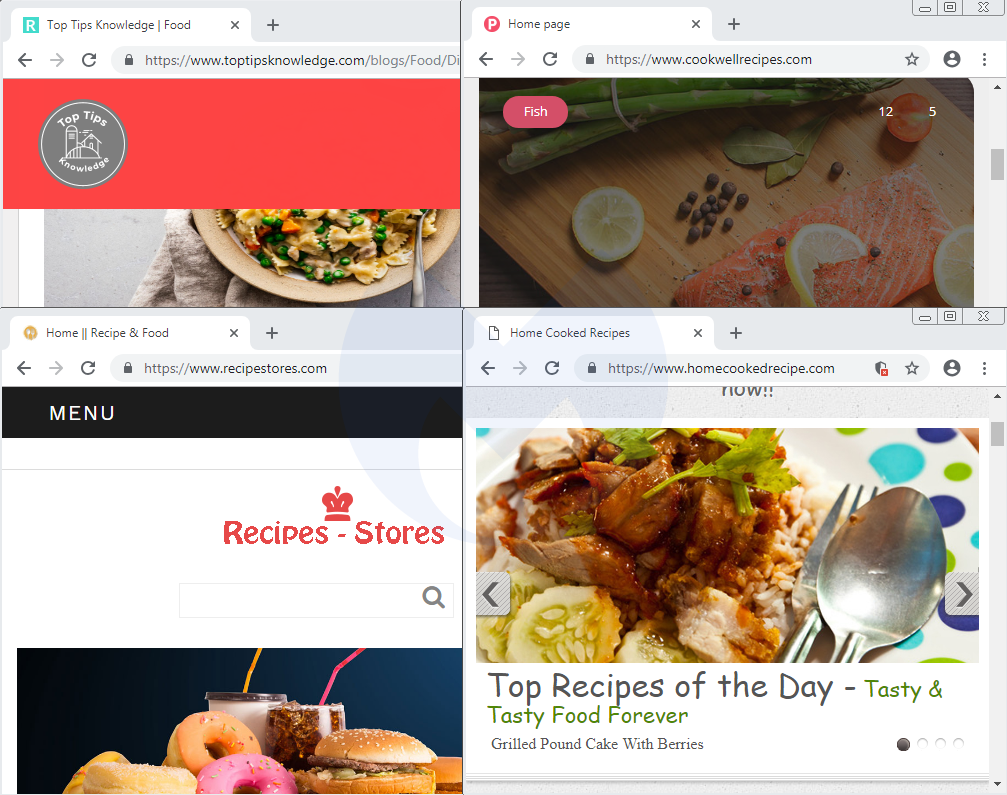
To support their scheme, the scammers have created a number of food-related blogs. The content appears to be genuine, and there are even some comments on many of the articles.

However, upon closer inspection, we can see that those sites have basically taken content from various web developer sites offering paid or free HTML templates. “ 
During our testing, visiting those sites directly did not create any malicious redirection, and they seemed to be absolutely benign. With only circumstantial evidence and without the so-called smoking gun, a case could not be made just yet.
Full infection chain
After some trial and error that included swapping various User-Agent strings and avoiding using commercial VPNs, we eventually were able to replay a full infection chain, from the original advert to the browser locker page.

The blog’s URL is actually called three consecutive times, and the last one performs a POST request with the eventual conditional redirect to the browlock. In the screenshot below, you can see the difference between proper cloaking (no malicious behavior) and the redirect to a browlock page:

Browlock page
The fake warning page is fairly standard. It checks for the type of browser and operating system in order to display the appropriate template to Windows and Mac OS victims.

The scammers often register entire ranges of hostnames on Azure by iterating through numbers attached to random strings. While many of those pages are taken down quickly, new ones are constantly popping back up in order to keep the campaign running. Here are some URI patterns we observed:
10-server[.]azurewebsites[.]net/call-now1/
2securityxew-561error[.]azurewebsites[.]net/Call-Now1/
10serverloadingfailed-hgdfc777error[.]azurewebsites[.]net/chx/
11iohhwefuown[.]azurewebsites[.]net/Call-Support1/
11serversecurityjunkfile-65error[.]azurewebsites[.]net/Call-Mac-Support/
2serverdatacrash-de-12error[.]azurewebsites[.]net/macx/
2systemservertemporaryblockghjj-510error[.]azurewebsites[.]net/mac-support/
We believe the crooks may also be rotating the decoy site that performs the redirect in addition to the existing user filtering in order to evade detection from security scanners.
Finding the perpetrators
We do not condone interacting with scammers directly, but part of this investigation was about finding who was behind this campaign in order to take action and spare more victims.
To continue on with deception, the rogue technicians lied to us about the state of our computer and made up imaginary threats. The goal was to sell expensive support packages that actually add little value.

The company selling those services is A2Z Cleaner Pro (AKA Coretel Communications) and was previously identified by one victim in August 2018 in a blog comment on the FTC’s website.

Their webste is hosted at 198.57.219.8, where we found two other interesting artifacts. The first one is a company named CoreTel that is also used by the scammers as a kind of business entity. It appears to be a rip off from another domain that pre-existed by several years and also hosted on the same IP adddress:

And then, there are two new recipe sites that were both registered in June and, as with previous ones, they also use content copied from other places:

Mitigation and take down
Malwarebytes’ browser extension was already blocking the various browlock pages heuristically.

We immediately reported the fraudulent ads to Google and Microsoft (Bing), as well as the decoy blogs to GoDaddy. The majority of their domains have been taken down already and their ad campaigns banned.
This tech support scam campaign cleverly targeted an older segment of the population by using paid search results for food recipes via online portals used by many Internet Service Providers.
There is no doubt scammers will continue to abuse ad platforms and hosting providers to carry out their business. However, industry cooperation for takedowns can set them back and save thousands of victims from being defrauded.
Indicators of compromise
Decoy blogs
alhotcake[.]com
bestrecipesus[.]com
cheforrecipes[.]com
chilly-recipesfood[.]com
cookwellrecipes[.]com
dezirerecipes[.]com
dinnerplusrecipes[.]com
dinnerrecipiesforu.com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
healthycookingidea[.]com
recipesstudios[.]com
a2zpcprotection[.]com
a2zcleanerpro[.]com
Regex to match browlock URIs on Azure
^http(s|)://(?!www)^.{2}[a-z]{2,7}/([cC]all-([nN]ow|Support)1|chx|macx|(Call-)?[mM]ac-[sS]upport)
We searched for various recipes on several different web portals (CenturyLink, Att.net, Yahoo! search and xfinity) and were able to easily find the ads bought by the scammers.
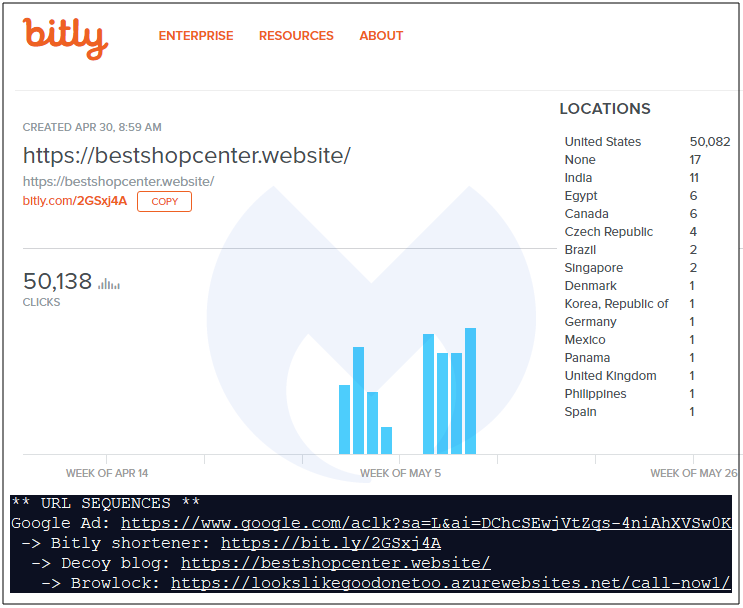
We do not have exact metrics on how many people clicked on those ads but we can infer that this campaign drew a significant amount of traffic based on two indicators: the first being our own telemetry and the second from a URL shortener used by one of the websites:

While those ads look typical and actually match our keyword search quite well, they actually redirect to websites created with malicious intent.
Decoy websites
To support their scheme, the scammers have created a number of food-related blogs. The content appears to be genuine, and there are even some comments on many of the articles.

However, upon closer inspection, we can see that those sites have basically taken content from various web developer sites offering paid or free HTML templates. “ 
During our testing, visiting those sites directly did not create any malicious redirection, and they seemed to be absolutely benign. With only circumstantial evidence and without the so-called smoking gun, a case could not be made just yet.
Full infection chain
After some trial and error that included swapping various User-Agent strings and avoiding using commercial VPNs, we eventually were able to replay a full infection chain, from the original advert to the browser locker page.

The blog’s URL is actually called three consecutive times, and the last one performs a POST request with the eventual conditional redirect to the browlock. In the screenshot below, you can see the difference between proper cloaking (no malicious behavior) and the redirect to a browlock page:

Browlock page
The fake warning page is fairly standard. It checks for the type of browser and operating system in order to display the appropriate template to Windows and Mac OS victims.

The scammers often register entire ranges of hostnames on Azure by iterating through numbers attached to random strings. While many of those pages are taken down quickly, new ones are constantly popping back up in order to keep the campaign running. Here are some URI patterns we observed:
10-server[.]azurewebsites[.]net/call-now1/
2securityxew-561error[.]azurewebsites[.]net/Call-Now1/
10serverloadingfailed-hgdfc777error[.]azurewebsites[.]net/chx/
11iohhwefuown[.]azurewebsites[.]net/Call-Support1/
11serversecurityjunkfile-65error[.]azurewebsites[.]net/Call-Mac-Support/
2serverdatacrash-de-12error[.]azurewebsites[.]net/macx/
2systemservertemporaryblockghjj-510error[.]azurewebsites[.]net/mac-support/
We believe the crooks may also be rotating the decoy site that performs the redirect in addition to the existing user filtering in order to evade detection from security scanners.
Finding the perpetrators
We do not condone interacting with scammers directly, but part of this investigation was about finding who was behind this campaign in order to take action and spare more victims.
To continue on with deception, the rogue technicians lied to us about the state of our computer and made up imaginary threats. The goal was to sell expensive support packages that actually add little value.

The company selling those services is A2Z Cleaner Pro (AKA Coretel Communications) and was previously identified by one victim in August 2018 in a blog comment on the FTC’s website.

Their webste is hosted at 198.57.219.8, where we found two other interesting artifacts. The first one is a company named CoreTel that is also used by the scammers as a kind of business entity. It appears to be a rip off from another domain that pre-existed by several years and also hosted on the same IP adddress:

And then, there are two new recipe sites that were both registered in June and, as with previous ones, they also use content copied from other places:

Mitigation and take down
Malwarebytes’ browser extension was already blocking the various browlock pages heuristically.

We immediately reported the fraudulent ads to Google and Microsoft (Bing), as well as the decoy blogs to GoDaddy. The majority of their domains have been taken down already and their ad campaigns banned.
This tech support scam campaign cleverly targeted an older segment of the population by using paid search results for food recipes via online portals used by many Internet Service Providers.
There is no doubt scammers will continue to abuse ad platforms and hosting providers to carry out their business. However, industry cooperation for takedowns can set them back and save thousands of victims from being defrauded.
Indicators of compromise
Decoy blogs
alhotcake[.]com
bestrecipesus[.]com
cheforrecipes[.]com
chilly-recipesfood[.]com
cookwellrecipes[.]com
dezirerecipes[.]com
dinnerplusrecipes[.]com
dinnerrecipiesforu.com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
healthycookingidea[.]com
recipesstudios[.]com
a2zpcprotection[.]com
a2zcleanerpro[.]com
Regex to match browlock URIs on Azure
^http(s|)://(?!www)^.{2}[a-z]{2,7}/([cC]all-([nN]ow|Support)1|chx|macx|(Call-)?[mM]ac-[sS]upport)
Leveraging paid search results
Tech support scams are typically distributed via malvertising campaigns. Cheap adult traffic is usually first on the list for many groups of scammers. Not only is it cost effective, but it also plays into the psychology of users believing they got infected after visiting a dodgy website.
Other times, we see scammers actively targeting brands by trying to impersonate them. The idea is to reel in victims looking for support with a particular product or service. However, in this particular campaign, the crooks are targeting folks looking up food recipes.
There are two types of results from a search engine results page (SERP):
- Organic search results that match the user’s search query based on relevance. The top listed sites are usually those that have the best Search Engine Optimization (SEO).
- Paid search results, which are basically ads relevant to the user’s query. They require a certain budget where not all keywords are equal in cost.
Because paid search results are typically displayed at the top (often blending in with organic search results), they tend to generate more clicks.

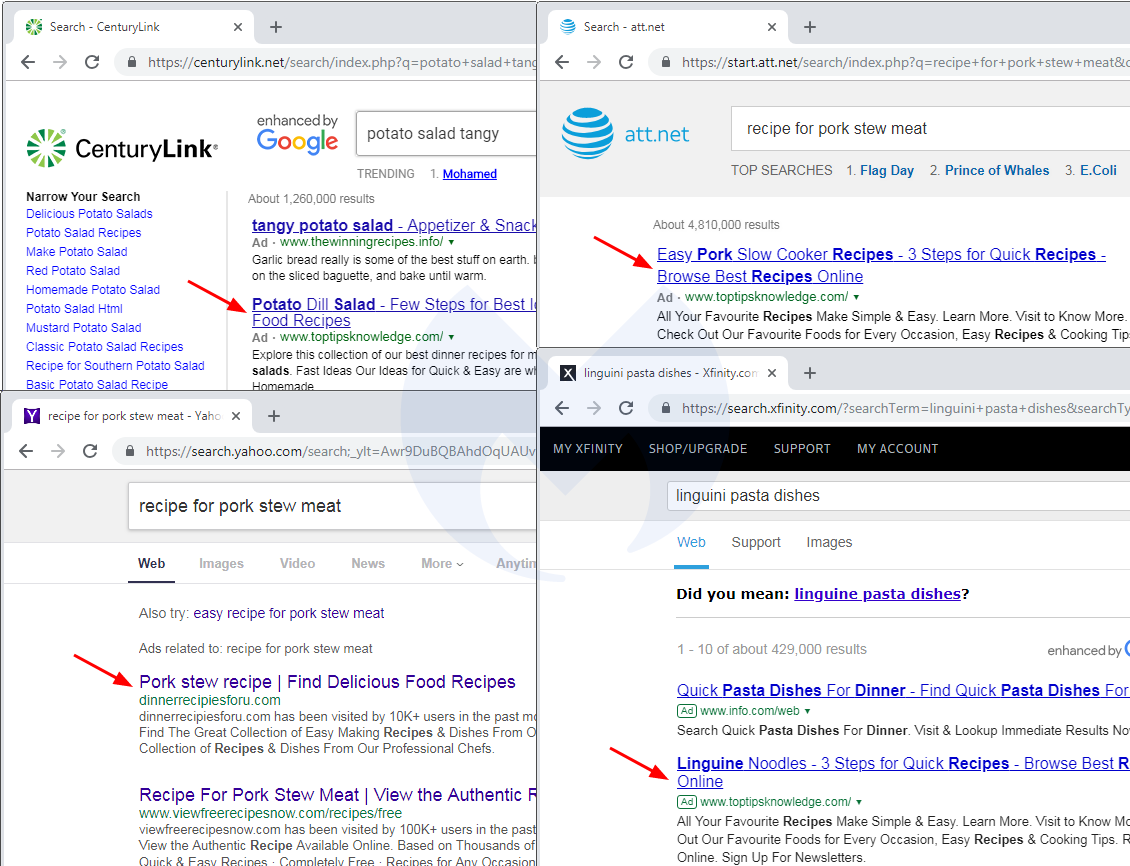
We searched for various recipes on several different web portals (CenturyLink, Att.net, Yahoo! search and xfinity) and were able to easily find the ads bought by the scammers.
We do not have exact metrics on how many people clicked on those ads but we can infer that this campaign drew a significant amount of traffic based on two indicators: the first being our own telemetry and the second from a URL shortener used by one of the websites:

While those ads look typical and actually match our keyword search quite well, they actually redirect to websites created with malicious intent.
Decoy websites
To support their scheme, the scammers have created a number of food-related blogs. The content appears to be genuine, and there are even some comments on many of the articles.

However, upon closer inspection, we can see that those sites have basically taken content from various web developer sites offering paid or free HTML templates. “ 
During our testing, visiting those sites directly did not create any malicious redirection, and they seemed to be absolutely benign. With only circumstantial evidence and without the so-called smoking gun, a case could not be made just yet.
Full infection chain
After some trial and error that included swapping various User-Agent strings and avoiding using commercial VPNs, we eventually were able to replay a full infection chain, from the original advert to the browser locker page.

The blog’s URL is actually called three consecutive times, and the last one performs a POST request with the eventual conditional redirect to the browlock. In the screenshot below, you can see the difference between proper cloaking (no malicious behavior) and the redirect to a browlock page:

Browlock page
The fake warning page is fairly standard. It checks for the type of browser and operating system in order to display the appropriate template to Windows and Mac OS victims.

The scammers often register entire ranges of hostnames on Azure by iterating through numbers attached to random strings. While many of those pages are taken down quickly, new ones are constantly popping back up in order to keep the campaign running. Here are some URI patterns we observed:
10-server[.]azurewebsites[.]net/call-now1/
2securityxew-561error[.]azurewebsites[.]net/Call-Now1/
10serverloadingfailed-hgdfc777error[.]azurewebsites[.]net/chx/
11iohhwefuown[.]azurewebsites[.]net/Call-Support1/
11serversecurityjunkfile-65error[.]azurewebsites[.]net/Call-Mac-Support/
2serverdatacrash-de-12error[.]azurewebsites[.]net/macx/
2systemservertemporaryblockghjj-510error[.]azurewebsites[.]net/mac-support/
We believe the crooks may also be rotating the decoy site that performs the redirect in addition to the existing user filtering in order to evade detection from security scanners.
Finding the perpetrators
We do not condone interacting with scammers directly, but part of this investigation was about finding who was behind this campaign in order to take action and spare more victims.
To continue on with deception, the rogue technicians lied to us about the state of our computer and made up imaginary threats. The goal was to sell expensive support packages that actually add little value.

The company selling those services is A2Z Cleaner Pro (AKA Coretel Communications) and was previously identified by one victim in August 2018 in a blog comment on the FTC’s website.

Their webste is hosted at 198.57.219.8, where we found two other interesting artifacts. The first one is a company named CoreTel that is also used by the scammers as a kind of business entity. It appears to be a rip off from another domain that pre-existed by several years and also hosted on the same IP adddress:

And then, there are two new recipe sites that were both registered in June and, as with previous ones, they also use content copied from other places:

Mitigation and take down
Malwarebytes’ browser extension was already blocking the various browlock pages heuristically.

We immediately reported the fraudulent ads to Google and Microsoft (Bing), as well as the decoy blogs to GoDaddy. The majority of their domains have been taken down already and their ad campaigns banned.
This tech support scam campaign cleverly targeted an older segment of the population by using paid search results for food recipes via online portals used by many Internet Service Providers.
There is no doubt scammers will continue to abuse ad platforms and hosting providers to carry out their business. However, industry cooperation for takedowns can set them back and save thousands of victims from being defrauded.
Indicators of compromise
Decoy blogs
alhotcake[.]com
bestrecipesus[.]com
cheforrecipes[.]com
chilly-recipesfood[.]com
cookwellrecipes[.]com
dezirerecipes[.]com
dinnerplusrecipes[.]com
dinnerrecipiesforu.com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
healthycookingidea[.]com
recipesstudios[.]com
a2zpcprotection[.]com
a2zcleanerpro[.]com
Regex to match browlock URIs on Azure
^http(s|)://(?!www)^.{2}[a-z]{2,7}/([cC]all-([nN]ow|Support)1|chx|macx|(Call-)?[mM]ac-[sS]upport)
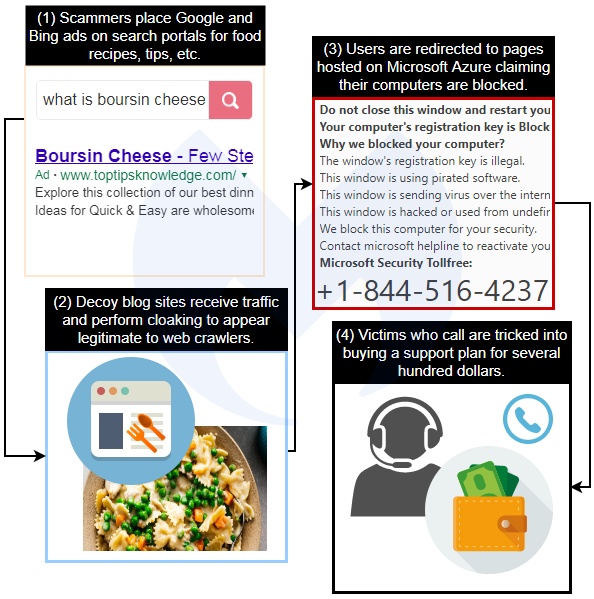
Tech support scammers are known for engaging in a game of whack-a-mole with defenders. Case in point, last month there were reports that crooks had invaded Microsoft Azure Cloud Services to host fake warning pages, also known as browser lockers. In this blog, we take a look at one of the top campaigns that is responsible for driving traffic to those Azure-hosted scareware pages.
We discovered that the scammers have been buying ads displayed on major Internet portals to target an older demographic. Indeed, they were using paid search results to drive traffic towards decoy blogs that would redirect victims to a browlock page.
This scheme has actually been going on for months and has intensified recently, all the while keeping the same modus operandi. Although not overly sophisticated, the threat actors behind it have been able to abuse major ad platforms and hosting providers for several months.

Leveraging paid search results
Tech support scams are typically distributed via malvertising campaigns. Cheap adult traffic is usually first on the list for many groups of scammers. Not only is it cost effective, but it also plays into the psychology of users believing they got infected after visiting a dodgy website.
Other times, we see scammers actively targeting brands by trying to impersonate them. The idea is to reel in victims looking for support with a particular product or service. However, in this particular campaign, the crooks are targeting folks looking up food recipes.
There are two types of results from a search engine results page (SERP):
- Organic search results that match the user’s search query based on relevance. The top listed sites are usually those that have the best Search Engine Optimization (SEO).
- Paid search results, which are basically ads relevant to the user’s query. They require a certain budget where not all keywords are equal in cost.
Because paid search results are typically displayed at the top (often blending in with organic search results), they tend to generate more clicks.

We searched for various recipes on several different web portals (CenturyLink, Att.net, Yahoo! search and xfinity) and were able to easily find the ads bought by the scammers.
We do not have exact metrics on how many people clicked on those ads but we can infer that this campaign drew a significant amount of traffic based on two indicators: the first being our own telemetry and the second from a URL shortener used by one of the websites:

While those ads look typical and actually match our keyword search quite well, they actually redirect to websites created with malicious intent.
Decoy websites
To support their scheme, the scammers have created a number of food-related blogs. The content appears to be genuine, and there are even some comments on many of the articles.

However, upon closer inspection, we can see that those sites have basically taken content from various web developer sites offering paid or free HTML templates. “ 
During our testing, visiting those sites directly did not create any malicious redirection, and they seemed to be absolutely benign. With only circumstantial evidence and without the so-called smoking gun, a case could not be made just yet.
Full infection chain
After some trial and error that included swapping various User-Agent strings and avoiding using commercial VPNs, we eventually were able to replay a full infection chain, from the original advert to the browser locker page.

The blog’s URL is actually called three consecutive times, and the last one performs a POST request with the eventual conditional redirect to the browlock. In the screenshot below, you can see the difference between proper cloaking (no malicious behavior) and the redirect to a browlock page:

Browlock page
The fake warning page is fairly standard. It checks for the type of browser and operating system in order to display the appropriate template to Windows and Mac OS victims.

The scammers often register entire ranges of hostnames on Azure by iterating through numbers attached to random strings. While many of those pages are taken down quickly, new ones are constantly popping back up in order to keep the campaign running. Here are some URI patterns we observed:
10-server[.]azurewebsites[.]net/call-now1/
2securityxew-561error[.]azurewebsites[.]net/Call-Now1/
10serverloadingfailed-hgdfc777error[.]azurewebsites[.]net/chx/
11iohhwefuown[.]azurewebsites[.]net/Call-Support1/
11serversecurityjunkfile-65error[.]azurewebsites[.]net/Call-Mac-Support/
2serverdatacrash-de-12error[.]azurewebsites[.]net/macx/
2systemservertemporaryblockghjj-510error[.]azurewebsites[.]net/mac-support/
We believe the crooks may also be rotating the decoy site that performs the redirect in addition to the existing user filtering in order to evade detection from security scanners.
Finding the perpetrators
We do not condone interacting with scammers directly, but part of this investigation was about finding who was behind this campaign in order to take action and spare more victims.
To continue on with deception, the rogue technicians lied to us about the state of our computer and made up imaginary threats. The goal was to sell expensive support packages that actually add little value.

The company selling those services is A2Z Cleaner Pro (AKA Coretel Communications) and was previously identified by one victim in August 2018 in a blog comment on the FTC’s website.

Their webste is hosted at 198.57.219.8, where we found two other interesting artifacts. The first one is a company named CoreTel that is also used by the scammers as a kind of business entity. It appears to be a rip off from another domain that pre-existed by several years and also hosted on the same IP adddress:

And then, there are two new recipe sites that were both registered in June and, as with previous ones, they also use content copied from other places:

Mitigation and take down
Malwarebytes’ browser extension was already blocking the various browlock pages heuristically.

We immediately reported the fraudulent ads to Google and Microsoft (Bing), as well as the decoy blogs to GoDaddy. The majority of their domains have been taken down already and their ad campaigns banned.
This tech support scam campaign cleverly targeted an older segment of the population by using paid search results for food recipes via online portals used by many Internet Service Providers.
There is no doubt scammers will continue to abuse ad platforms and hosting providers to carry out their business. However, industry cooperation for takedowns can set them back and save thousands of victims from being defrauded.
Indicators of compromise
Decoy blogs
alhotcake[.]com
bestrecipesus[.]com
cheforrecipes[.]com
chilly-recipesfood[.]com
cookwellrecipes[.]com
dezirerecipes[.]com
dinnerplusrecipes[.]com
dinnerrecipiesforu.com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
handmaderecipies[.]com
homecookedrecipe[.]com
hotandsweetrecipe[.]com
just-freshrecipes[.]com
lunch-recipesstore[.]com
mexirecipes[.]com
neelamrecipes[.]com
nidhikitchenrecipes[.]com
organicrecipesandfood[.]com
recipes4store[.]com
recipestores[.]com
royalwarerecipes[.]com
smokyrecipe[.]com
specialsweetrecipes[.]com
starcooking[.]club
starrecipies[.]com
sweethomemadefoods[.]com
tatesty-recipes[.]com
today4recipes[.]com
tophighrecipes[.]com
toptipsknowledge[.]com
totalspicyrecipes[.]com
vegfood-recipes[.]com
yammy-recipes[.]com
healthycookingidea[.]com
recipesstudios[.]com
a2zpcprotection[.]com
a2zcleanerpro[.]com
Regex to match browlock URIs on Azure
^http(s|)://(?!www)^.{2}[a-z]{2,7}/([cC]all-([nN]ow|Support)1|chx|macx|(Call-)?[mM]ac-[sS]upport)










