Search engines make money by showing users sponsored advertisements—a lot of money. This attracts attention, competition, and plenty who want a piece of the action without doing the actual work or considering the impact to those on the other end of the search bar. Because in the search business, even the crumbs are interesting.
In this post, we look at the ways in which shady advertisers, cybercriminals, and other vultures try to siphon off profits from the search engine business using sneaky tech tactics that ultimately harm users more than the search engines themselves.
How exactly do search engines make money?
Every time someone clicks on a sponsored advertisement, the requisite search engine earns money on a pay-per-click basis. They are paid by advertisers, who shell out for beneficial placement in the search results for keyword phrases of their choice.
As a result of the popularity of these search engines—Google in particular—US companies spend an estimated $80 billion on search engine optimization (SEO) alone. And the leading search engines are owned by some of the most valuable technology companies around.
Default search engine
Knowing this may make it easier to understand why browser hijackers are so keen on changing the default search engine on your favorite browser. They get a piece of the pie for referrals, and this entices them to use several methods to have your searches run through their hands. If a hijacker manages to change your default search engine to their own, they can profit from your searches.
But there are other profitable ways to interfere with your search results:
- Newtabs are browser hijackers that open a new tab with a site or page set by the hijacker. These pages usually contain a search bar. The goal is to get the user to enter his queries in that search form instead of searching from the address bar, which would still point to the default search engine.
- Startpage hijackers change the startpage of the affected browser for very much the same reasons as newtabs, just on different browsers.
- Searchpage hijackers are mostly browser extensions that can read and change the data on a number of websites. In these cases, the websites are the major search engines. Search hijackers come in a few major flavors:
- Redirects from major search engines are forced to a site owned by the hijacker. Sometimes the results will be displayed there, but sometimes you get sent back with only a referral added to your query. The referrals are what pays the hijackers.
- Sponsored results are added to the results retrieved by major search engines and sometimes presented as if you are using a whole new search engine. At other times the changes are so minimal you may never notice.
- Sponsored results are added to the results of major search engines and presented as if they were the original results.
- Redirected searches occur from a major search engine to another search engine. The hijacker feeds your query to another engine and adds its referral on the fly.
Each of the above methods are in use by major families of potentially unwanted programs (PUPs) and adware. While neither of these threat categories are considered malware, they inhibit users’ ability to view clean, original search results using the engine of their choice, ultimately interfering in their online experience.
More invasive methods of profiting from search results
Seeing the potential for profit windfall, PUPs and adware have found other, more invasive ways of making money from your searches—methods that interfere with the displayed results. These include:
- Search result changers that give paying sites a better position without disclosing that they are paid.
- SEO poisoning that artificially acquires a better page rank.
- Ad fraud, which dupes advertisers into believing they have displayed their advertisement on affected machines, while the user of such machine may not have noticed anything at all.
Page rank describes how high up in the search results your entry shows up. The higher the better is the general consensus, but you surely want to be on the first page. If people spot a search result likely to fulfill their quest for knowledge on the first page of results, they typically click on that link before even bothering to look at the other pages of results. Many are known to follow the first link beneath the sponsored results.
How do you achieve a good page rank? Search engines use many different algorithms to decide on the order in which to display results, but one of the main criteria is to have lots of incoming links to the webpage, with the understanding that links from reputable sites have heavier weight.
SEO poisoning is hard to do on the major search engines: They’ve seen every trick in the book and are vigilant about banning those tactics as fast as they can. So if you abuse the position of being marked as a reputable site, you might lose it a lot faster than you gained it. It will only render short-term effects, which works for those going for fast cash, but not for long-term business.
Fake privacy extensions
There are many ways to make changes to search engines and search results on a system affected with PUPs or adware, but the most popular method is to seduce victims into installing a browser extension that promises some kind of functionality.
It is typical to see search hijackers promising to guard your online privacy or act as an ad blocker, as both of those plugins require users to grant them permission to view or have control over a wide range of data and computer settings. Because of this, it is important users vet potential privacy extensions and ad blockers thoroughly before downloading.
Example hijackers
Let us show you some examples of the different search hijackers and the permissions they need to pull off their dirty work. I’ll use the permissions prompts for Chrome extensions only, but most of these hijackers also exist in the Firefox realm.
Example 1: Changing default search
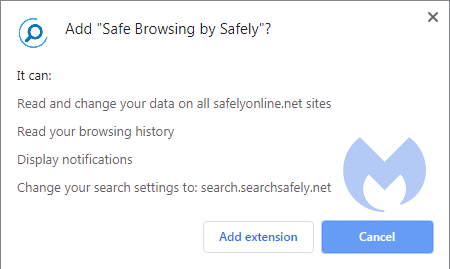
Your default search settings will be changed, which is a red flag. This type of extension usually promises you some functionality that explains the need for such a permission.
Example 2: Changing results
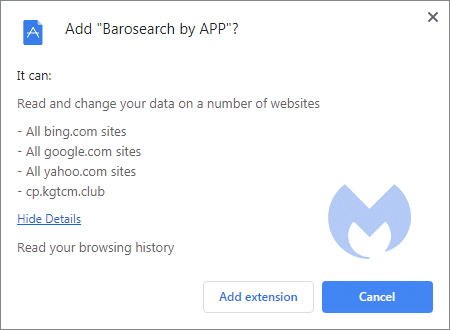
Changing your data in this case means they will alter the search results from the three major search engines: Bing, Google, and Yahoo. The fourth listing is for the origin of this extension.
Example 3: Adding a search bar on the new tab:
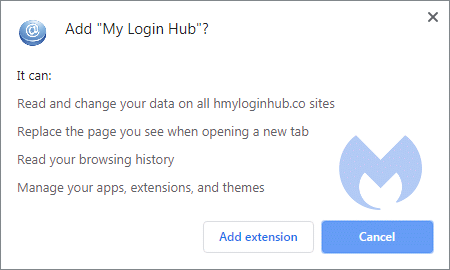
The page that gets displayed when you open a new tab will hold a search form that leads to the search site belonging to the extension.
Example 4: The kitchen sink
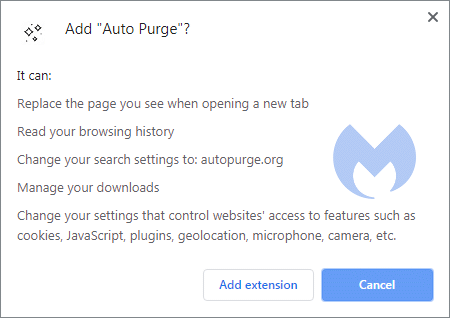
This extension changes the newtab and the default search; a multi-vector attack so to speak. It also requires other permissions, such as reading browsing history and managing downloads, that I would shy away from for privacy reasons.
Example 5: Adding sponsored results to your Google results:
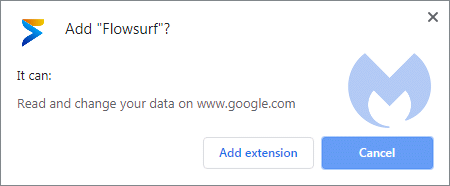
This one fetches the results from Google and then adds a tiny header and a bunch of sponsored results.

Search engine thieves are hard to find
We see a lot of complaints from people wondering what caused their search experience to change and how. Most of the time, it is because of an extension like the examples shown above. Many people don’t realize the extensions are the culprit because they were installed for a different reason, sometimes even from a reputable source or as part of a bundle—sometimes pretending not to install at all. But reading between the lines of the fine print in those permission requests—or just plain reading them at all—can give you insight into how your search engine and browser experience became tangled up in PUPs and adware.
We hope that this post (and a scan from a reputable antivirus program like Malwarebytes or Browser Guard) will help solve those problems in the future.
Stay safe, everyone!











