Google has released an update for its Chrome browser that includes 30 security fixes. The latest version of the stable channel is now Chrome 101.0.4951.41 for Windows, Mac and Linux. This version addresses vulnerabilities that an attacker could exploit to take control of an affected system.
Microsoft advises Edge users—which is essentially a Microsoft-badged version of Chrome—to update as well, since it shares many of these vulnerabilities.
Seven of the vulnerabilities are rated as “high.” Five of those vulnerabilities are “Use after free” flaws, which, thanks to a memory relocation issue, can allow hackers to pass arbitrary code to a program. Which is another way of saying that attackers can do unauthorized things on your computer just by getting you to go to a malicious web page coded to exploit these problems.
Use after free
Publicly disclosed computer security flaws are listed in the Common Vulnerabilities and Exposures (CVE) database. Its goal is to make it easier to share data across separate vulnerability capabilities (tools, databases, and services). The use after free vulnerabilities that are listed with a high severity are:
- CVE-2022-1477, a use-after-free vulnerability in the Vulkan graphics API.
- CVE-2022-1478, a use-after-free vulnerability in the SwiftShader 3D renderer.
- CVE-2022-1479, a use-after-free vulnerability in ANGLE a “graphics engine abstraction layer.”
- CVE-2022-1480, is a use-after-free vulnerability in Device API. A remote attacker can reportedly create a specially crafted web page, trick the victim into visiting it, trigger the use-after-free error and execute arbitrary code on the target system.
- CVE-2022-1481, is a use-after-free vulnerability in Sharing. This vulnerability can be reportedly be exploited by a remote non-authenticated attacker via the Internet, by luring the victim to a specially crafted web page.
Other high severity vulnerabilities
There are two other vulnerabilities listed as high severity issues:
- CVE-2022-1482, is described as an “Inappropriate implementation in WebGL” in Google Chrome. A remote attacker can create a specially crafted web page, trick the victim into visiting it and compromise their system.
- CVE-2022-1483, is a heap buffer overflow in WebGPU, a web API that exposes modern computer graphics capabilities for the Web. Heap is the name for a region of a process’ memory which is used to store dynamic variables. A buffer overflow is a type of software vulnerability that exists when an area of memory within a software application reaches its address boundary and writes into an adjacent memory region. In software exploit code, the two common areas that are targeted for overflows are the stack and the heap.
How to update
If you’re a Chrome user on Windows, Mac, or Linux, you should update to version 101.0.4951.41 as soon as possible.
The easiest way to update Chrome is to allow it to update automatically, which basically uses the same method as outlined below but does not require your attention. But you can end up blocking automatic updates if you never close the browser, or if something goes wrong, such as an extension stopping you from updating the browser.
So, it doesn’t hurt to check now and then. And now would be a good time, given the severity of the vulnerabilities listed.
My preferred method is to have Chrome open the page chrome://settings/helpwhich you can also find by clicking Settings > About Chrome.
If there is an update available, Chrome will notify you and start downloading it. Then all you have to do is relaunch the browser in order for the update to complete.
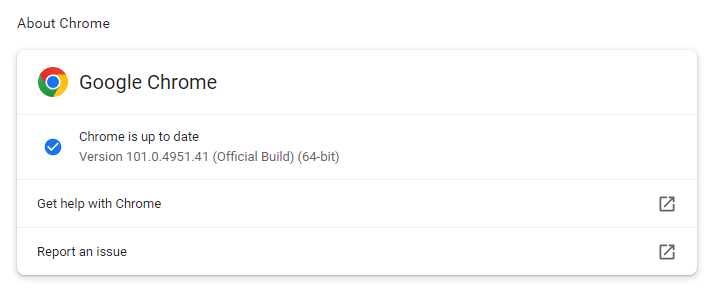
After the updates Chrome should be at version 101.0.4951.41 and Edge should be at version 101.0.1210.32.
Stay safe, everyone!











