In a blog by the Chrome security team we learned that the Chromium project is going to support the use of third-party Rust libraries from C++ in Chromium.
This is good news because Rust is a so-called memory-safe programming language. So using it in a widespread program like Chrome and the other members of the Chromium family means that almost everyone can benefit from this step forward.
Besides Google’s own Chrome browser, Microsoft Edge, Opera, and many other browsers are based on Chromium code. Reportedly, there are over 25 million lines of code in 36 programming languages in the Chromium browser codebase.
Rust
Rust is a community project and the product is a high-level, general-purpose programming language that enforces memory safety. Rust started in 2006 as a personal project by Mozilla Research employee Graydon Hoare as part of the development of the Servo browser engine. Then, in February 2021, the Servo team was disbanded and the Rust Foundation was announced by its five founding companies (AWS, Huawei, Google, Microsoft, and Mozilla).
Rust is designed to be memory safe, because poor memory management has been the root cause for way too many vulnerabilities, for way too long. Only a few months ago, the NSA urged a shift to memory safe programming languages.
Memory vulnerabilities
If you ever read our posts describing security vulnerabilities, you will see a lot of phrases like “buffer overflow”, “failure to release memory”, “use after free”, “memory corruption”, and “memory leak”. These are all memory management issues. And the best way to prevent memory management issues is to use a memory-safe language, which manages memory automatically instead of relying on a programmer to code things correctly.
In an earlier article about the effects of the introduction of memory safe languages in Android we showed a steady decline of memory safety vulnerabilities in Android. With the introduction of memory-safe languages like Kotlin, Java, and Rust in the development of the Android operating system, the contributions to the software that ties everything together in the background coded in C and C++ have gone down considerably.
Rule of two
Google’s goals for allowing the use of Rust libraries in Chromium are to provide a simpler and safer way to satisfy the rule of two, in order to speed up development and improve the security of Chrome.
The rule of two is demonstrated in the image below:
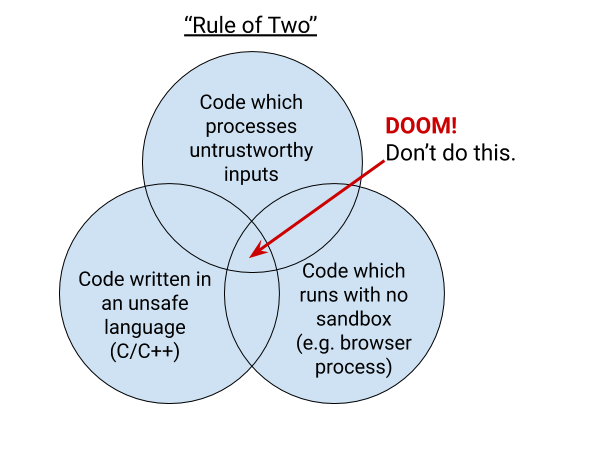
Image courtesy of Google
It says not to pick more than two of these possibly unsafe circumstances:
- untrustworthy inputs
- unsafe implementation language
- high privilege
By eliminating the “code written in an unsafe language” factor wherever you can, you lessen the need to run code in a sandbox. So, there is less code needed and less need for security reviews. This speeds up development while improving the security. Eliminating the untrustworthy input is almost impossible when you are working on a browser.
The Chrome browser runs as an OS-level account representing a person which is considered a high privilege. In Chrome, sandboxing is applied to attain privilege reduction, which means running the code in a process that has had some or many of its privileges revoked.
Libraries
Rust was set out to be the foundation for a secure browser and has already proven its use in a browser for Mozilla. But for now, Google will only support third-party libraries. Third-party libraries are written as standalone components, they don’t hold implicit knowledge about the implementation of Chromium.
For future developments, Google is investing in Crubit, an experiment in how to increase the fidelity of interop between C++ and Rust and express or encapsulate the requirements of each language to the other. Interop refers to two or more browsers behaving the same.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.











