Author’s Note: We at Malwarebytes continue to do our part in educating our product users and constant blog readers about day-to-day online threats and how they can avoid falling prey to them. “PUP Friday”, our latest attempt at getting users acquainted with files they may need to watch out for in the Wild Web, offers an in-depth look at some interesting and quite notable potentially unwanted programs (PUPs). Expect to see this type of content pushed out twice a month at the end of a work week.
In this episode we take a look at a hijacker that installs a new browser rather than hijacking an existing one. It even attempts to replace Chrome if that is already installed. To make sure that you will use your new browser, eFast makes itself the default browser and takes over some file-associations. File-associations are settings that determine which program will run when files with a certain extension are opened.
Hijacks
This one hijacks these file-associations:
- gif
- htm
- html
- jpeg
- jpg
- png
- shtml
- webp
- xht
- xhtml
The same is done for these URL-associations:
- ftp
- http
- https
- irc
- mailto
- mms
- news
- nntp
- sms
- smsto
- tel
- urn
- webcal
Taking over URL-associations means that every link for any of these protocols will be opened with eFast. If you want to have a look at the state of your own file type and protocol associations, these can be checked under “Control Panel” > “Programs” > “Default Programs” > “Set Associations”.
Looking there on an affected computer, selecting eFast in the list of programs will show you something like this:

Copy-cat
It also places a set of shortcuts to popular sites on your desktop which are all set to open with the eFast browser.
The installer for eFast also deletes all the shortcuts to Google Chrome on your taskbar and desktop, most likely hoping to confuse the user with their very similar icons. And not just the icons look alike. The newly installed browser feels and looks very much like Chrome, no doubt because they used the Chromium open source Projects to build this browser. It isn’t until you look in the settings that you spot the “about eFast” entry in the menu (or if you type “chrome://chrome” in the address bar).
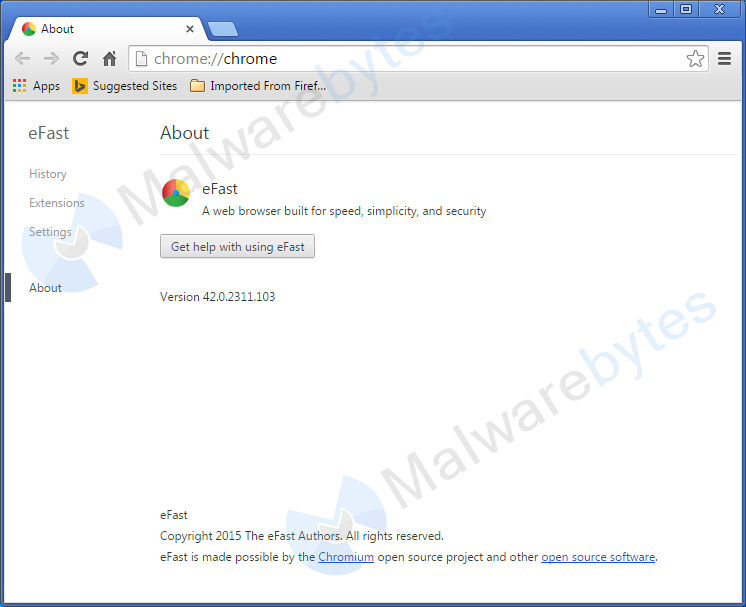
Given the similarity to Chrome it is very hard to tell why a user would choose this copy-cat over the real Chrome. Very likely not for the advertisements this hijacker shows them, especially seeing that they get nothing really worthwhile in return.
Privacy policy
Not only is it unclear what we have to gain by installing this browser, if eFast has put up a EULA or Privacy Policy somewhere, I was unable to find it. There is a privacy policy for ClaraLabs which might apply, but we can’t be sure about that since eFast isn’t mentioned there, just “the Software”.
More adware
Another point that raises some concerns about this install is that it dropped a file called predm.exe in the folder %Program Files%efas_en_110010107. Looking at the details for that file we see that it is misdated by a week earlier than the actual date of install and that the “File description” is “AA setup”.
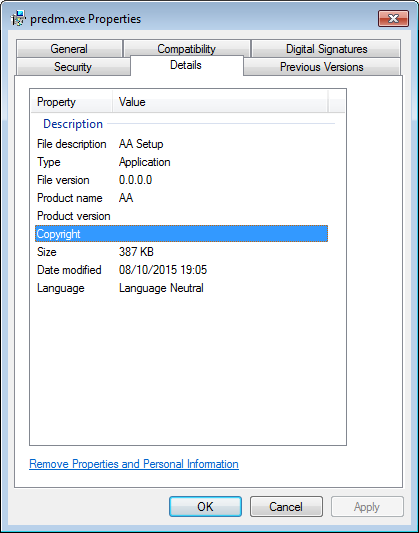
As it turns out this is another Eorezo/Tuto4PC variant according to these scanresults at Virustotal.
Detection and protection
Malwarebytes Anti-Malware detects and removes eFast as PUP.Optional.eFast, PUP.Optional.Clara and PUP.Optional.Tuto4PC. This only works if PUP detections are set to “Treat detections as malware”. You can change or check this under “Settings” > “Detection and Protection”. A removal guide for eFast can be found on our forums.
Resources
Pieter Arntz











