So far in this series, we have handed you some methods to recognize and remediate adware. We used this diagram as a guideline.
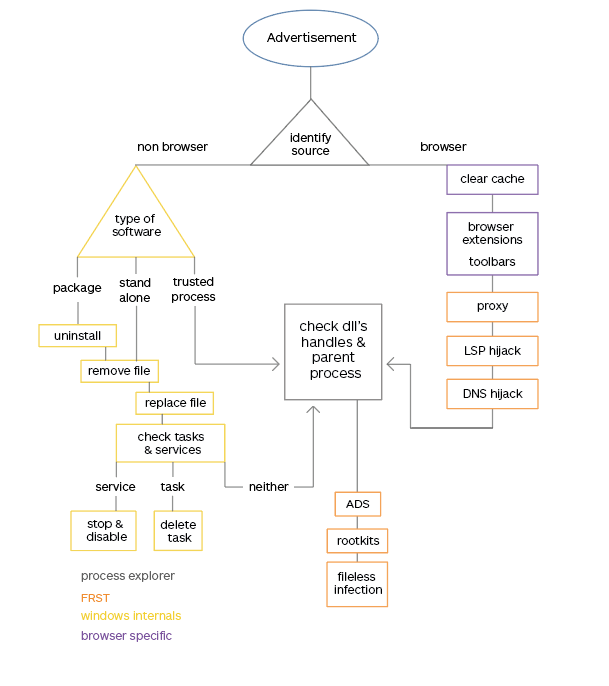
During this journey, we have touched upon several free tools that we used to get some insight on what type of infection we were dealing with and where the adware could be hiding. Our objective has been to give you an idea of how many different types of adware are around for Windows systems. Though most are classified as PUPs, you will also see the occasional Trojan or rootkit.
This, the final part of the series, will provide you with download-locations and a description of the tools. One word of warning: even though all the tools are free for personal use, that doesn’t make them less powerful. If you want to use these tools to remediate a problem, make sure you know what you are doing or have some kind of backup at hand, in case anything goes terribly wrong. If you want to learn more about removing malware, there are several online schools that offer free malware removal training.
The tools
Process Explorer (Microsoft/Sysinternals)
Site: https://technet.microsoft.com/en-us/sysinternals/processexplorer.aspx
We used Process Explorer to identify the process that belongs to a window and to identify parent/child processes and look at DLLs and handles. An introduction to Process Explorer and some more advanced information can be found on our blog.
Resource Monitor (Microsoft)
Built into Windows since Windows 7.
We explained how to use Resource Monitor to check which processes are connecting where.
FileASSASSIN (Malwarebytes)
Site: https://www.malwarebytes.com/fileassassin/
FileAssassin is a tool to delete any type of locked file.
Malwarebytes anti-rootkit BETA (Malwarebytes)
Site: https://www.malwarebytes.com/antirootkit/
Malwarebytes anti-rootkit BETA is the tool of choice when you are dealing with difficult to remove and even invisible infections.
FRST (Farbar)
Site: https://www.bleepingcomputer.com/download/farbar-recovery-scan-tool/
There is a 32-bit and 64-bit version. Make sure you download the correct one for your system.
The Farbar Recovery Scan Tool (FRST) is a very useful diagnostic tool. It can also be used as a manual remediation tool, but I want to focus on reading the scan output it produces and which sections to focus on when we are looking for adware. So unless you have cured the problem using Process Explorer, MBAM, MBAR or FileAssassin we are now going to have a look at FRST. FRST works equally well in normal or safe mode and when a machine has boot up problems it will even work in the Windows Recovery Environment.
The output of the FRST scans is nicely formatted in a way that makes it easy to check most of the problem areas that we have pointed out during the course of this series.
Browser sections
These are divided per installed browser and there is a general section.
==================== Internet (Whitelisted) ====================
This section contains information like DNS servers that are in use in the format:
TcpipParameters: [DhcpNameServer] {IP address 1} {IP address 2}
Tcpip..Interfaces{CLSID}: [DhcpNameServer] {IP address 1} {IP address 2}
Internet Explorer:
==================
This section has the add-ons for Internet Explorer listed in the format:
BHO: {name} -> {CLSID} -> {path + filename} [{date of install}] [{signed-by-company-name}]
It also list other items like Startpage, Searchscopes, Handlers, Toolbars, Filters and ActiveX objects
FireFox:
========
This section holds the extensions for Firefox in the format:
FF Extension: {name} – {folder to the extension} [{date of install}] [{signed-by-company-name}]
And the Plugins in these format types:
FF Plugin: @{company}/{name} -> {path + filename} [{date of install}] ({signed-by-company-name})
FF Plugin ProgramFiles/Appdata: {path + filename} [date of install}] ({signed-by-company-name})
It also list other information about Firefox like Homepage, Default search engine and the presence of user.js files.
Chrome:
=======
This section holds the extensions for each Chrome profile in these formats:
CHR Extension: ({name}) – {path to the extension folder} [{date of install}]
CHR HKLM...ChromeExtension: [{extension identifier string}] – [{update_url}]
It also lists information about the Homepage and policies that may be active.
Opera:
=======
This section holds the extensions for Opera in the format:
OPR Extension: ({name}) – {path to the extension folder} [{date of install}]
It also shows StartupUrls and StartMenuInternet where applicable.
Loaded modules
You can find some information about loaded modules in the section:
==================== Loaded Modules (Whitelisted) ==============
In the format:
{Date/time on system} – {Date/time created} - {filesize} {permissions} () {path to file}{filename + extension}
Note: it lists only unsigned files. Even if the files are signed by known malware publishers, they will not be listed.
Scheduled Tasks
Scheduled Tasks are flagged in the Addition log of FRST in the following format:
Task: {CLSID} - System32 or WindowsTasks{jobname} => {path to the file}{filename} [date] (signature)
Services
Services are reported along with their startup method and whether they are running or not.
R=RunningS=Stopped
U=Unknown
The startup type numbers are: 0=Boot
1=System
2=Auto
3=Demand
4=Disabled
5=Unknown
In the format:
{Letter}{number}{name of the service};{path to the file}{byte-size creation-date}{signed by}
LSP hijackers
As the order of the LSP layers is stored in the Winsock Service Provider you will find LSP entries listed in the Winsock section of a FRST log.
Example:
Winsock: Catalog5 000000000001\LibraryPath => restored successfully (%SystemRoot%system32NLAapi.dll)
The catalog numbers are important to keep in mind. Whenever you want to remove a Winsock:Catalog9 entry, it is recommended to use “netsh winsock reset”. This is to avoid the user ending up with a broken internet connection. You may have to repeat this after a reboot.
DNS hijackers and proxies
On the victim’s computer there are a few options for DNS hijacks:
- Alternative or altered hosts file. If the user has a non-standard hosts file FRST will report in Addition.txt: There are more than one entries detected in hosts”. This is not necessarily bad. Some security programs use the hosts file as a block-list.
- The DNS servers are listed in the “Other Areas” section. This also requires additional research as most DNS servers are legitimate.
- Proxies are listed in the “Internet” section of the FRST log.
Uninstall list
Programs that are listed in the list of installed Programs and Features can be found in the “Installed Programs” section of the Addition log including “hidden” entries.
ADS
Alternate Data Streams have a special section for themselves. Note that this section is white-listed, as are many others. The format looks like this:
AlternateDataStreams: {Path to the file}:{name of the stream} [number of bytes]
WMI
Hijackers using the Windows Management Instrumentation can be spotted in the Addition log. Example:
WMI_ActiveScriptEventConsumer_ASEC: < ===== ATTENTION
Conclusion
I really enjoyed sharing some of the knowledge that I gathered over the years and I’m also glad I now have it in a relatively organized fashion. I hope you, the readers have found it useful too. Or entertaining at least. Feel free to let us know in the comments.
Index
- Identify the process
- Clear browser caches
- Remove browser extensions
- Proxies
- Winsock hijackers
- DNS hijackers
- Type of software
- Uninstall
- Remove file
- Replace file
- Scheduled tasks
- Services
- DLL’s
- Handles
- Parent process
- ADS
- Rootkits
- Fileless infections
Part 7
- Tools to investigate with











