A variant of a remote code execution vulnerability with Internet Explorer’s scripting engine known as CVE-2018-8373 patched last August has been found in the wild. Looking at the IOCs posted by our colleagues at TrendMicro, we recognized the infrastructure serving this exploit. The same static domain has been active since at least early July, and is being redirected to from an adult website injected with a malicious script.
In the below traffic capture from August, we were served CVE-2018-8174, which is thought to be from the same author. It is interesting to note that this is not an exploit kit, but rather appears to be a single actor who implemented the available Proof of Concept to distribute his payload, the Quasar Remote Administration Tool (RAT).
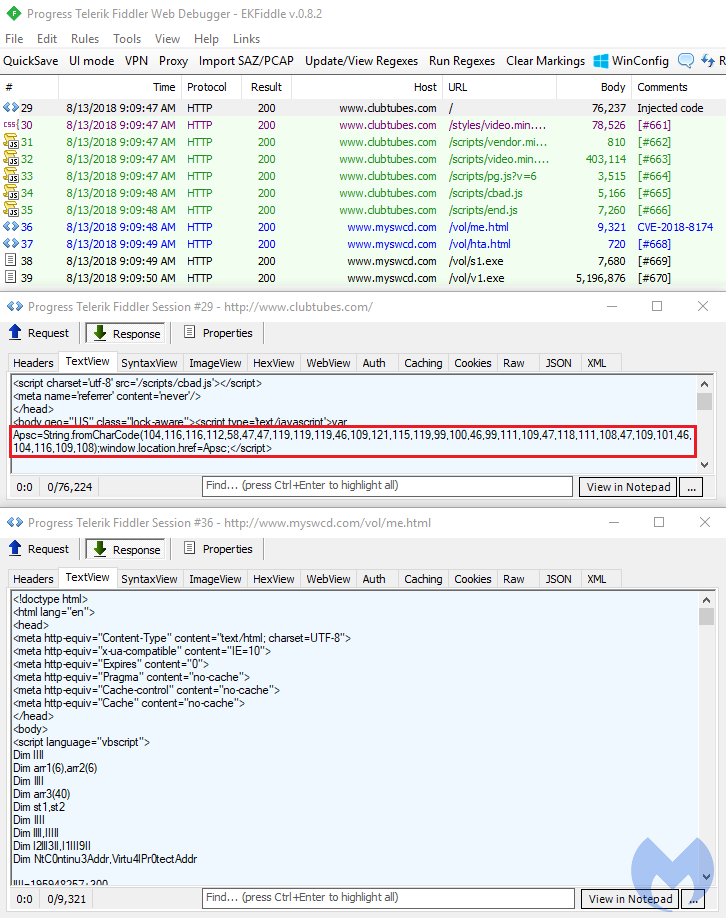
During our tests with this new variant of CVE-2018-8373, we found it to be quite unstable and failing to detonate its payload via Powershell invocation. However, a working CVE-2018-8174 was still serving the same payload we had captured back in August.
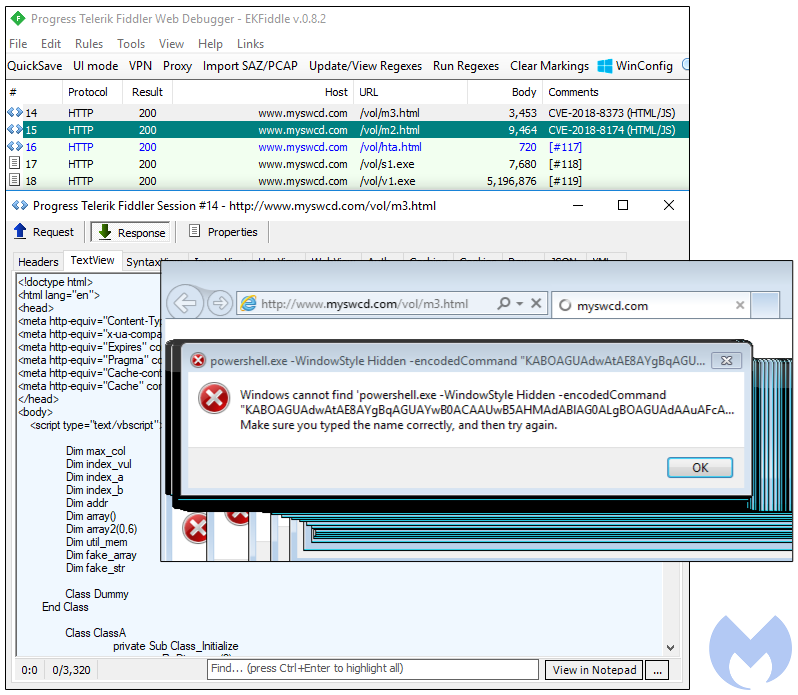
The source code for CVE-2018-8373 has been uploaded to many platforms already (PasteBin, VirusTotal), including to the AnyRun sandbox. That sample triggers the exploit and spawns PowerShell. In the following animation, we replayed this attack to show how our anti-exploit technology is able to mitigate this vulnerability at various levels.

We can expect that other treat actors will be looking at this code for possible implementation. However, unless it is improved, it is unlikely to be integrated into exploit kits, considering that its cousin, CVE-2018-8174, works flawlessly.
Indicators of compromise
Injected adult site
198.211.33[.]67 clubtubes[.]com
Exploit-serving domain
54.191.17[.]130 myswcd[.]com/vol/m3.html,CVE-2018-8373 myswcd[.]com/vol/m2.html,CVE-2018-8174 myswcd[.]com/vol/me.html,CVE-2018-8174
Payload
myswcd[.]com/vol/s1.exe,Loader myswcd[.]com/vol/v1.exe,Installer myswcd[.]com/vol/v2.exe,Quasar RAT 7EEF6EF8FED53B7C3BF61BA821F375A0A433EA4CB0185FD223780B729A9A5792 268909BC33F0F8C5312B51570016311E3676AF651A57DE38E42241DCC177B2D6 D9A967D0CAA8DB86FECA3AE469EF6797E81DFDAC4D8531658CB242A87C80CE05










