A phishing scam typically comes as an email purporting to be from your bank, Internet Service Provider, or any other online service.
It is crafted in such a way that it requires your immediate attention by clicking on a link and entering personal information (social security number, credit card details, etc.) into a fake webpage.
Cyber-crooks will normally host these phishing pages on compromised websites (without the owner’s knowledge), free web hosting , or as we saw more recently, on poorly secured home computers essentially acting as web servers for hire.
-
Microsoft Azure: cloud based apps and services
In this article, we will show how Microsoft’s very own cloud platform is being abused by cyber-criminals.
Microsoft Azure is a cloud computing platform formerly known as Windows Azure, developed and maintained by Microsoft.
It is “the public cloud platform for customers as well as for our own services Office 365, Dynamics CRM, Bing, OneDrive, Skype, and Xbox Live,” according to Microsoft.
The service offers multiple cloud-based features such as Virtual Machines, Big Data management, mobile apps and websites.
Although this is not the first case, cyber-crooks continue to use Azure’s web hosting service to house phishing websites, such as this one targeting Apple users:
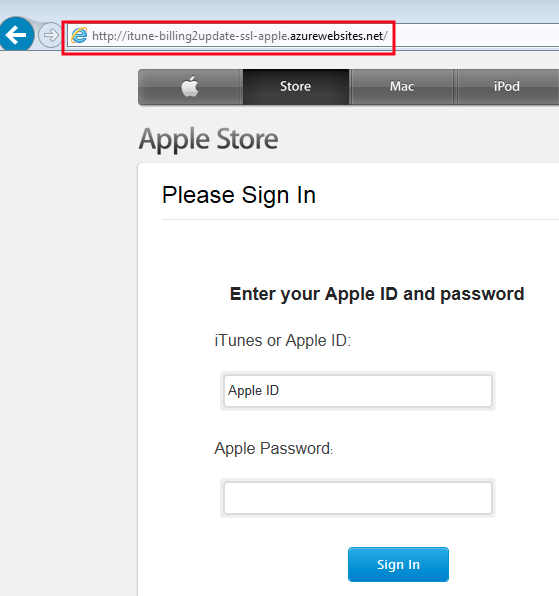
A phishing site targeting Apple users, hosted on Microsoft Azure
The phishing URL (http://itune-billing2update-ssl-apple . azurewebsites.net/) contains two parts:
- The subdomain (itune-billing2update-ssl-apple) which is picked by the user, so long as it’s available. Note the choice of keywords, and especially ‘ssl‘ which usually indicates that a site is using secure encryption (not the case here by the way).
- The main or root domain (azurewebsites.net) for Azure’s websites.
The following screenshots show the phishing scam in action. It is not simply after your user name and password but mostly after your personal and credit card details.
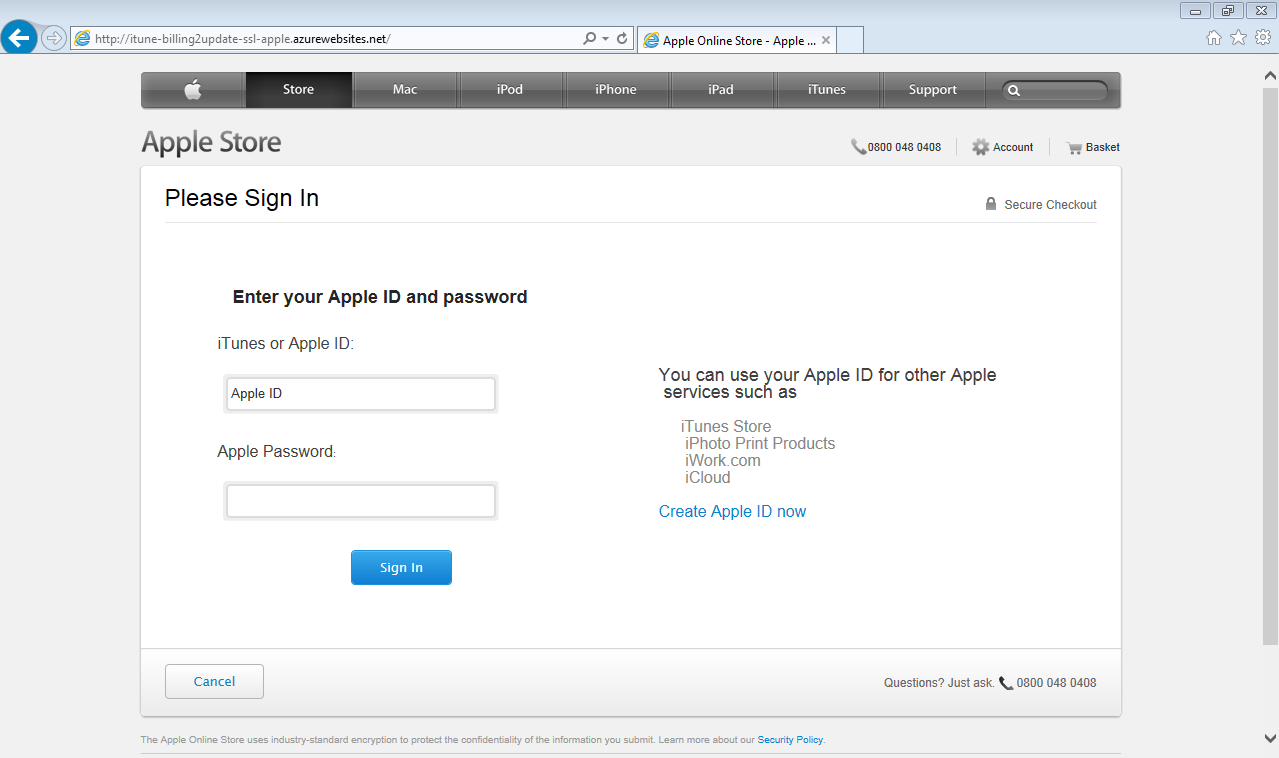
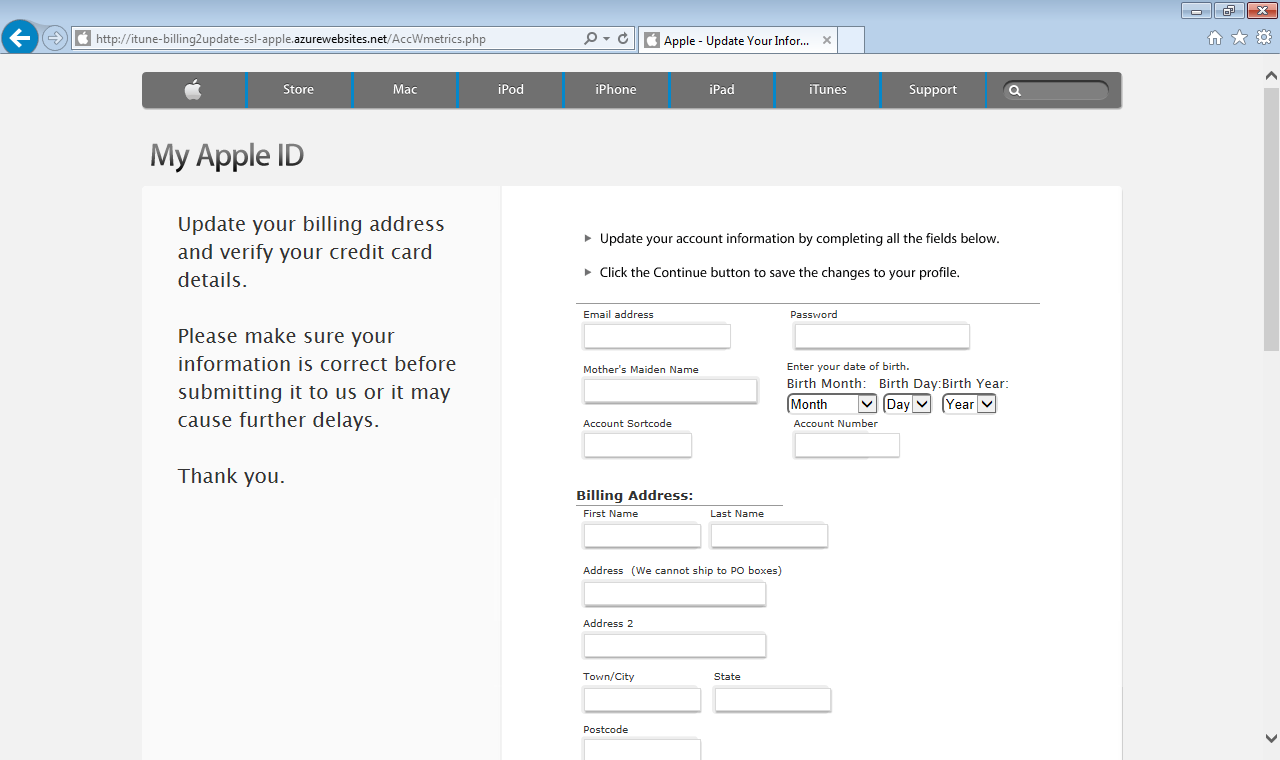
Step2: Collect personal information
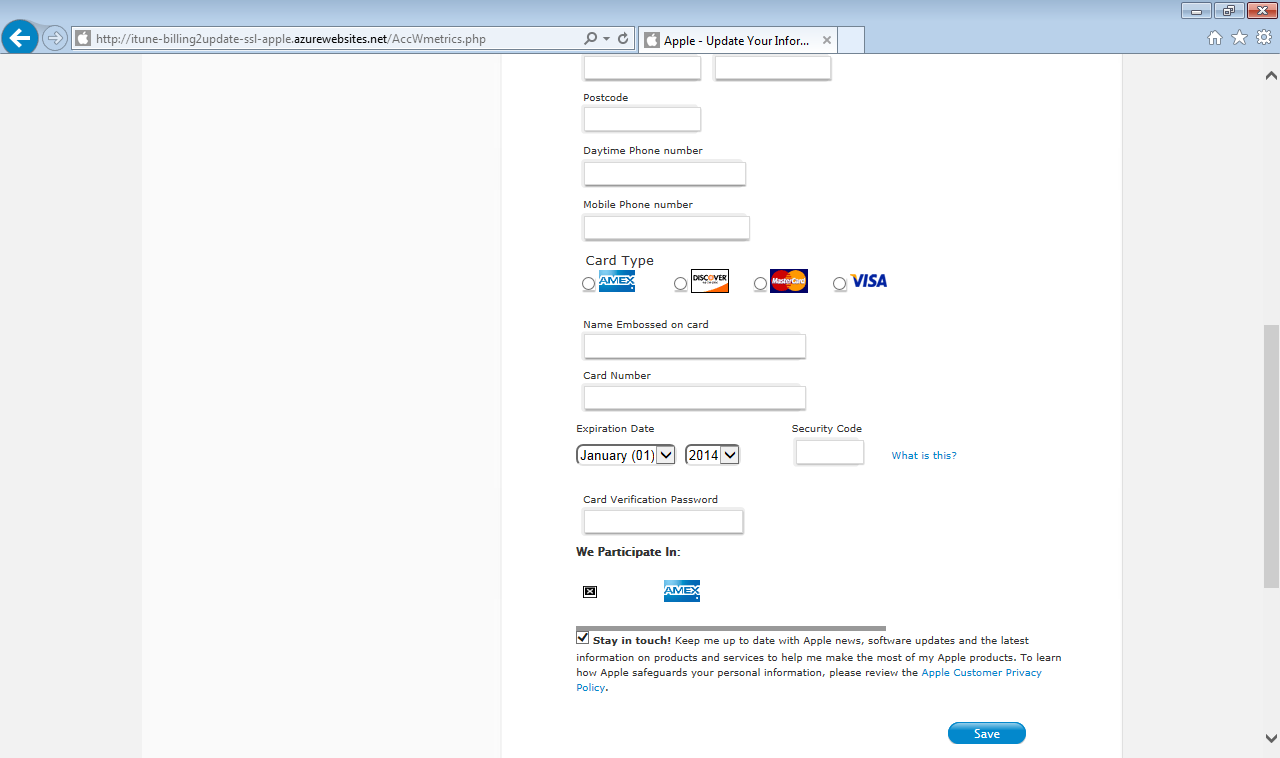
Step3: Harvest credit card details
-
Setting up a website on Azure is easy
There are only a few steps involved in getting a site up and running on Azure. You need to sign up for an account and there is even a free trial option.
Software architect Troy Hunt regularly talks about Azure on his blog and recently published “The world’s greatest Azure demo“, a recommended watch if you want to know more about the platform.
Once you are done with the account registration, you can move on to Azure’s main dashboard and create your first website.
-
Are the bad guys actually signing up for Azure?
Phishing pages on Azure are not something new. According to the website PhishTank, this has been an ongoing problem, with early cases such as this one in 2012 targeting a Brazilian bank’s customers.
This isn’t too surprising after all given that any platform that gains more publicity is also going to attract extra attention from cyber-criminals.
It has long been a problem for any provider of free online services (file storage, web hosting, blogging) to fend off spammers, and more generally, malicious actors.
A lot of efforts are put into making signing up and using these services relatively easy and user friendly. While it’s great for typical users, crooks are also taking advantage of it.
However, registering for Azure does require a genuine phone number and won’t work with an IP-based one (such as one from Google Hangouts or other free online provider). In addition, the prompt for a valid credit card does reduce the number of spammy or fraudulent sign-ups.
So there might actually be a more likely scenario to explain the presence of these phishing pages on Microsoft Azure. Bad guys may have stolen the credentials from legitimate users that were already registered.
In fact, stolen usernames and passwords are one of the main reasons why most websites get compromised. Certain types of malware will look for stored credentials within FTP clients, browsers or simply swipe them as you type them (keyloggers).
Unlike most compromised websites where the fraudulent pages are stored within a sub-directory, the bad guys actually create their own personalized URL on Azure to fit with the theme of the phish.
The following are a few examples taken from the PhishTank:
http://appleid . azurewebsites.net/ http://paypalscurity . azurewebsites.net/ http://www22online-americanexpress . azurewebsites.net/ http://www1bmo-com . azurewebsites.net/ https://bradesco-recadastramento . azurewebsites.net/ https://banque-accord-fr . azurewebsites.net/ http://verifiedbyvisa-sebse . azurewebsites.net/
-
Common sense goes a long way in spotting a scam
Phishing scams are getting more subtle every day and still making their way through our inboxes. The bad guys are exploring all avenues to house the matching phishing pages whether they be on hacked sites, personal computers acting as web servers or cloud based services.
As always, one way to quickly spot a fraudulent site is by looking at its URL. But that’s not enough unfortunately as certain pieces of malware are capable of spoofing what appears in the address bar.
You should be particularly cautious before clicking any link from an email and especially if it comes from your bank, Facebook, Gmail, etc.
Common sense also goes a long way with many of these scams. Why would your bank want to know your PIN number which you normally only ever type into an ATM or at a store?
If you have already been victim of a phishing scam or identity theft, you should report it to your bank, credit card company and local police immediately. This is a serious matter that needs to be dealt with swiftly.
Note: The Apple phishing website featured in this article was reported to Microsoft and just a few hours later the site was taken offline.
Additional resources:
- Email and web scams: how to protect yourself Microsoft
- Internet Explorer’s SmartScreen filter Microsoft
- Report a phish PhishTank
- Report a phish US-CERT










