Trojan.BrowserAssistant.PS
How to remove Browser Assistant Trojan Virus
Trojan.BrowserAssistant.PS is Malwarebytes’ detection name for a Trojan that injects javascript code in targeted browsers (Edge and Firefox). The BrowserAssistant installer is signed by Realistic Media Inc. and aimed at Windows systems.
Browser Assistant Symptoms
Users of affected systems may see this entry in their list of installed Programs and Features.
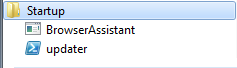
and these items in the Windows Startup folder:
Type and source of infection
Trojan.BrowserAssistant.PS is a Trojan that allows the threat actor to show advertisements in the affected browsers. Trojan.BrowserAssistant.PS is installed as part of bundlers.
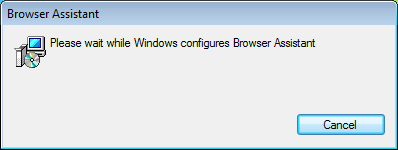
Browser Assistant Protection
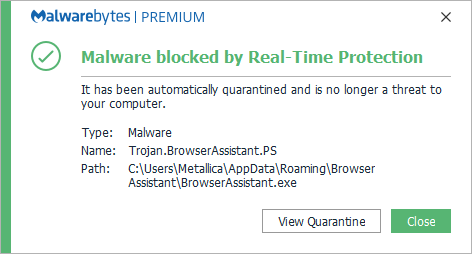
Malwarebytes blocks Trojan.BrowserAssistant.PS
Browser Assistant Detection and Removal
Malwarebytes can detect and remove Trojan.BrowserAssistant.PS without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Business remediation
How to remove Trojan.BrowserAssistant.PS with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.

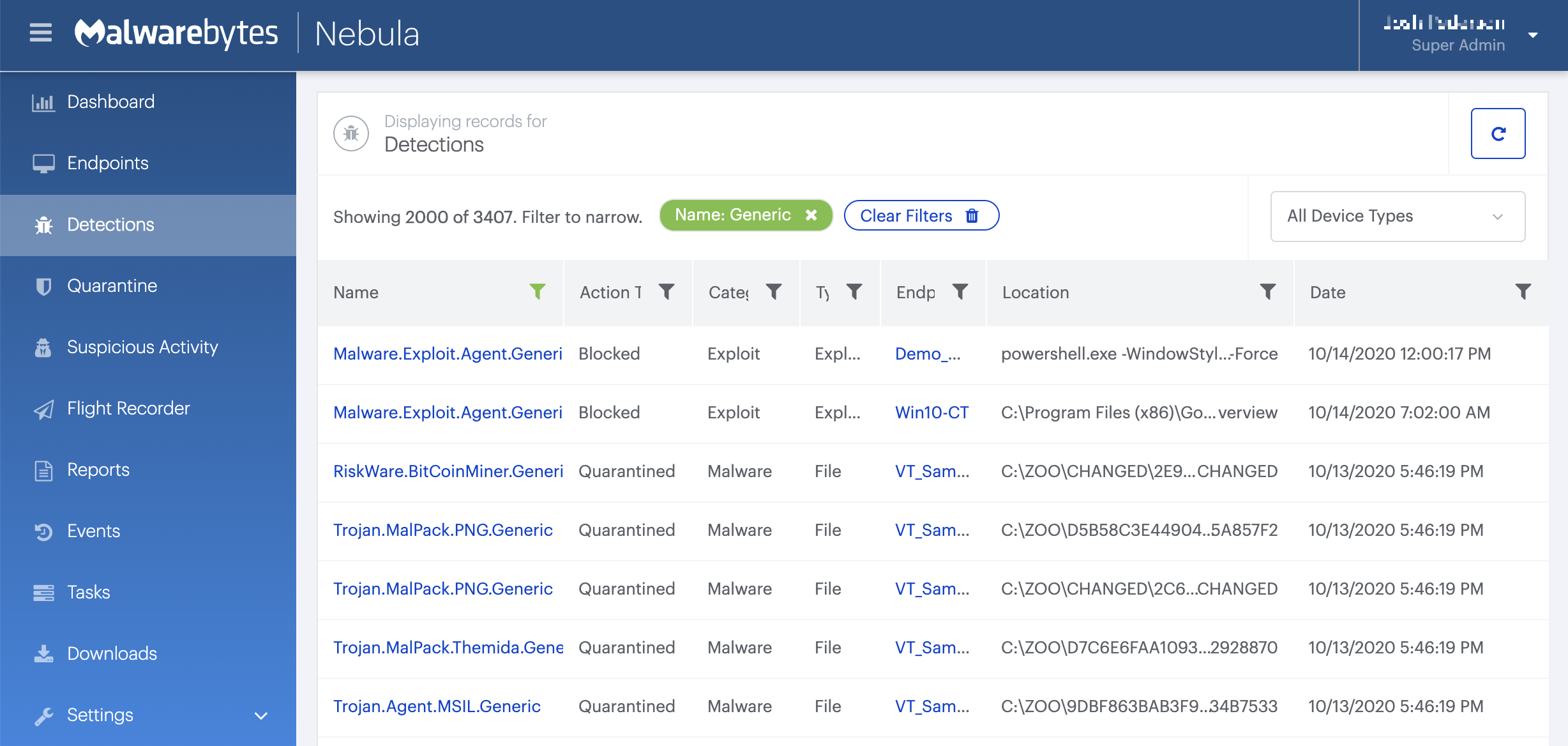
Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
On the Quarantine page you can see which threats were quarantined and restore them if necessary.
Malwarebytes removal log
A Malwarebytes log of removal will be huge but should contain these entries:
Malwarebytes www.malwarebytes.com
-Log Details- Scan Date: 7/25/19 Scan Time: 1:16 PM Log File: a687e548-aecd-11e9-ad51-00ffdcc6fdfc.json
-Software Information- Version: 3.7.1.2839 Components Version: 1.0.586 Update Package Version: 1.0.11712 License: Premium
-System Information- OS: Windows 7 Service Pack 1 CPU: x64 File System: NTFS User: {computername}\{username}
-Scan Summary- Scan Type: Threat Scan Scan Initiated By: Manual Result: Completed Objects Scanned: 237392 Threats Detected: 2255 Threats Quarantined: 2255 Time Elapsed: 48 min, 59 sec
-Scan Options- Memory: Enabled Startup: Enabled Filesystem: Enabled Archives: Enabled Rootkits: Enabled Heuristics: Enabled PUP: Detect PUM: Detect
-Scan Details- Process: 0 (No malicious items detected)
Module: 0 (No malicious items detected)
Registry Key: 1 Trojan.BrowserAssistant.Powershell, HKCU\SOFTWARE\REALISTIC MEDIA INC.\Browser Assistant, Quarantined, [3839], [661357],1.0.11712 Registry Value: 1 PUP.Optional.QXSearch, HKCU\SOFTWARE\GOOGLE\CHROME\PREFERENCEMACS\Default\extensions.settings|pidepfbnmnemhcencgnfhhfnfiebdgjk, Quarantined, [352], [676735],1.0.11712
Registry Data: 0 (No malicious items detected)
Data Stream: 0 (No malicious items detected)
Folder: 148 Trojan.BrowserAssistant.PS, C:\Users\{username}\AppData\Roaming\Browser Assistant\node_modules\@cliqz-oss\firefox-client\test, Quarantined, [3840], [710827],1.0.11712 Trojan.BrowserAssistant.PS, C:\Users\{username}\AppData\Roaming\Browser Assistant\extension\js, Quarantined, [3840], [710827],1.0.11712 Trojan.BrowserAssistant.PS, C:\Users\{username}\AppData\Roaming\Browser Assistant\node_modules, Quarantined, [3840], [710827],1.0.11712 Trojan.BrowserAssistant.PS, C:\Users\{username}\AppData\Roaming\Browser Assistant\WebDrivers, Quarantined, [3840], [710827],1.0.11712 Trojan.BrowserAssistant.PS, C:\Users\{username}\AppData\Roaming\Browser Assistant\extension, Quarantined, [3840], [710827],1.0.11712 Trojan.BrowserAssistant.PS, C:\Users\{username}\AppData\Roaming\Browser Assistant\edge\x86, Quarantined, [3840], [710827],1.0.11712 Trojan.BrowserAssistant.PS, C:\Users\{username}\AppData\Roaming\Browser Assistant\engine, Quarantined, [3840], [710827],1.0.11712 Trojan.BrowserAssistant.PS, C:\Users\{username}\AppData\Roaming\Browser Assistant\edge, Quarantined, [3840], [710827],1.0.11712 Trojan.BrowserAssistant.PS, C:\Users\{username}\AppData\Roaming\Browser Assistant\api, Quarantined, [3840], [710827],1.0.11712 Trojan.BrowserAssistant.PS, C:\USERS\{username}\APPDATA\ROAMING\BROWSER ASSISTANT, Quarantined, [3840], [710827],1.0.11712 Trojan.BrowserAssistant.Powershell, C:\USERS\{username}\APPDATA\ROAMING\MICROSOFT\WINDOWS\START MENU\PROGRAMS\STARTUP\UPDATER.LNK, Quarantined, [3839], [652810],1.0.11712
Physical Sector: 0 (No malicious items detected)
WMI: 0 (No malicious items detected)
(end)
Traces/IOCs
You may see these entries in FRST logs: Startup: C:\Users\{username}\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\BrowserAssistant.lnk [2019-07-25] ShortcutTarget: BrowserAssistant.lnk -> C:\Users\{username}\AppData\Roaming\Browser Assistant\BrowserAssistant.exe (Realistic Media Inc. -> ) Startup: C:\Users\{username}\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\updater.lnk [2019-07-25] ShortcutAndArgument: updater.lnk -> C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe => -noninteractive -ExecutionPolicy bypass -c “try{$w=”$env:APPDATA”+’\Browser Assistant\’;[Reflection.Assembly]::Load([System.IO.File]::ReadAllBytes($w+’Updater.dll’));$i=new-object u.U;$i.R()}catch{}” C:\Users\{username}\AppData\Roaming\Browser Assistant Browser Assistant (HKLM-x32\…\{367D5074-5E48-40AF-B009-7D3839DAE5E4}) (Version: 1.21.6922.27430 – Realistic Media Inc.)





