Backdoor.Qbot
Short bio
Backdoor.Qbot is Malwarebytes’ detection name for a large family of Backdoor Trojans that has been around in one form or another since 2009.
Type and source of infection
Backdoor.Qbot is mainly a banking Trojan and passwordstealer. It is worth noting that most varianst are VM-aware and some have polymorphic abilities. Backdoor.Qbot main source are exploit kits but they are also spread by infected email attachments.
Aftermath
- Data/information about the system may have been stolen
- User credentials may have been stolen
- Affected system may be susceptible to further attacks and/or infection due to a backdoor that was opened
Protection
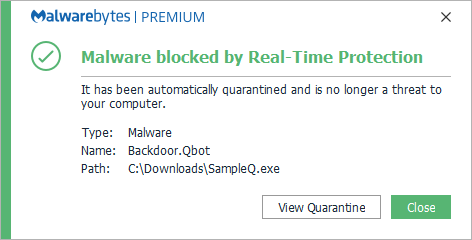
Malwarebytes block Backdoor.Qbot
Business remediation
How to remove Backdoor.Qbot with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.
Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
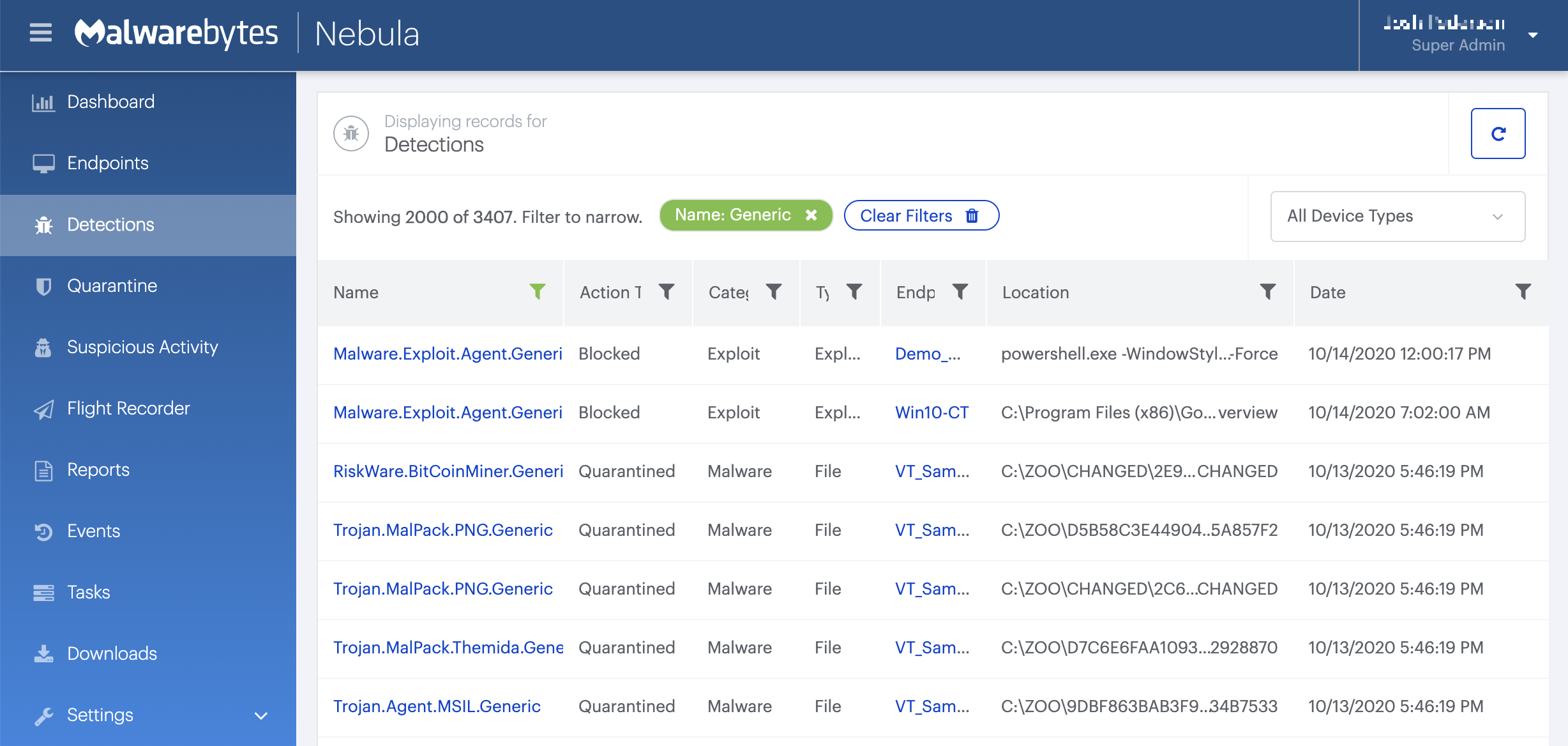
On the Quarantine page you can see which threats were quarantined and restore them if necessary.
Home remediation
Malwarebytes can detect and remove Backdoor.Qbot without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
IOCs
Backdoor.Qbot may install different files upon execution. It is usually installed in the folder %ALLUSERSPROFILE%, for example:
%ALLUSERSPROFILE% Microsoftoraene2 %ALLUSERSPROFILE% _qbothome_qbot.dll
but also
%APPDATA% microsoftjwkljxnwjwkljx.dll %APPDATA% roamingmicrosoftjwkljxnwjwkljxn.exe
Once installed, Backdoor.Qbot replaces existing registry data found in subkey “HKEY_LOCAL_MACHINEMicrosoftWindowsCurrentVersionRun” so that the malware runs at each Windows start. The malware prepends itself to a previously existing entry. For example, we have seen it create the following registry entry:
In subkey: HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun Sets value: “
enagk
Backdoor.Qbot attempts to connect to a remote server to receive command instructions from a threat actor. Commands may include any of the following actions:
Install additional files Execute processes Download updates Log keystrokes Steal passwords from MSN, Internet Explorer, and Outlook Get system information Monitor several Web sites, some of which are related to banks and other financial institutions Steal cookies and certificates Downloads other malware
Backdoor.Qbot may connect to remote sites to download updates or additional malware, which are then installed in the computer.
Some of the domains it is known to connect to are:
nt11.co.in nt002.cn





