Exploit kit (EK) activity continues to surprise us as the weather cools, the leaves change, and we move into the fall of 2018. Indeed, shortly after our summer review, a new exploit kit was discovered, and while no new vulnerabilities were added to the current EKs, several malvertising chains are still going strong.
Smoke Loader, Ramnit, and AZORult are some of the most common payloads we’ve observed in the last few months—particularly in Japan and Canada. The geo-targeted exploit kits such as Magnitude EK continue to predominantly affect South Korea and Taiwan.
Another interesting trend as of late is a decrease in cryptomining payloads and an increase in ransomware drops instead, mostly via the Fallout and RIG EKs.
Fall 2018 EK overview
- Fallout EK
- RIG EK
- GrandSoft EK
- Magnitude EK
- Underminer EK
Internet Explorer’s CVE-2018-8174 and Flash’s CVE-2018-4878 continue to be the most relied upon vulnerabilities.
Fallout EK
Fallout EK, discovered by team nao_sec, is the newest exploit kit which takes its name and URI patterns from the defunct Nuclear EK. Fallout EK has diverse campaigns that are not limited to a particular geographic location and therefore could be seen as a direct rival to RIG EK. Due to its constantly changing and complex URI paths, Fallout EK stands out from its counterparts.
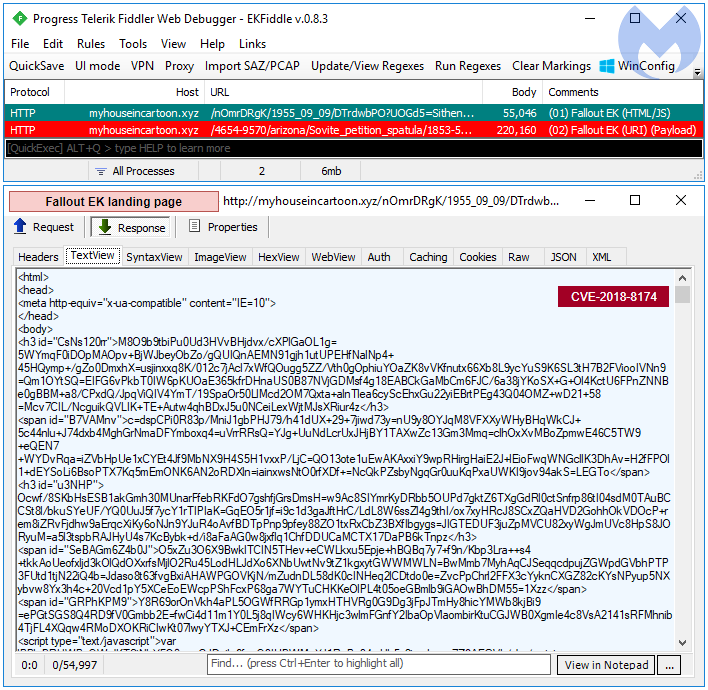
The payload in this sequence is GandCrab ransomware.
229BD13628C1AE3E84A9C7860617B836ACCDE4D932D2A2DC9DB64E78C211DA41
RIG EK
Not much has changed with RIG EK in recent times, but since the arrival of its new competitor, Fallout EK, our telemetry shows its usage has slowly declined in the past quarter.
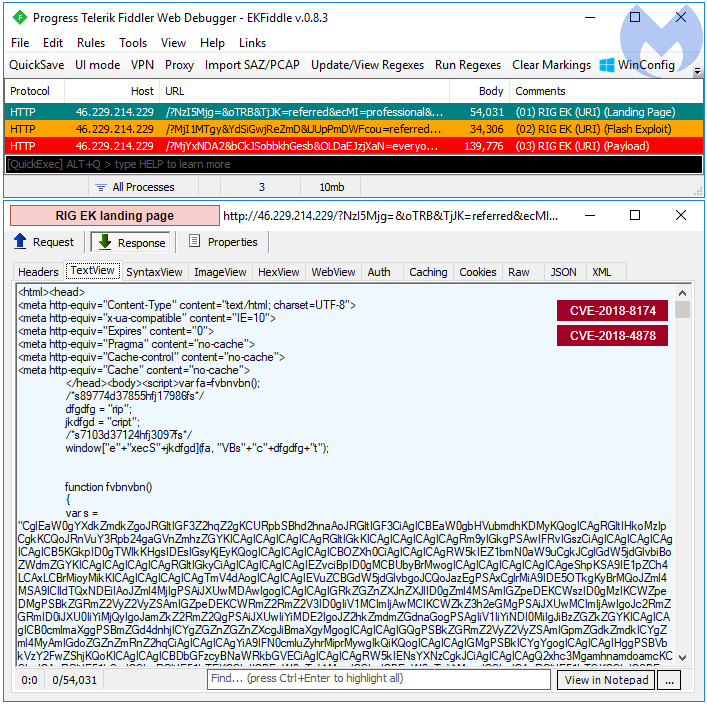
The payload in this sequence is Kraken ransomware.
2F5DEC0A8E1DA5F23B818D48EFB0B9B7065023D67C617A78CD8B14808A79C0DC
GrandSoft EK
GrandSoft EK is a little less common than the other EKs that we track. Some of its delivery chains include compromised websites acting as an intermediary gate. Thanks to team nao_sec for sharing some recent traffic.
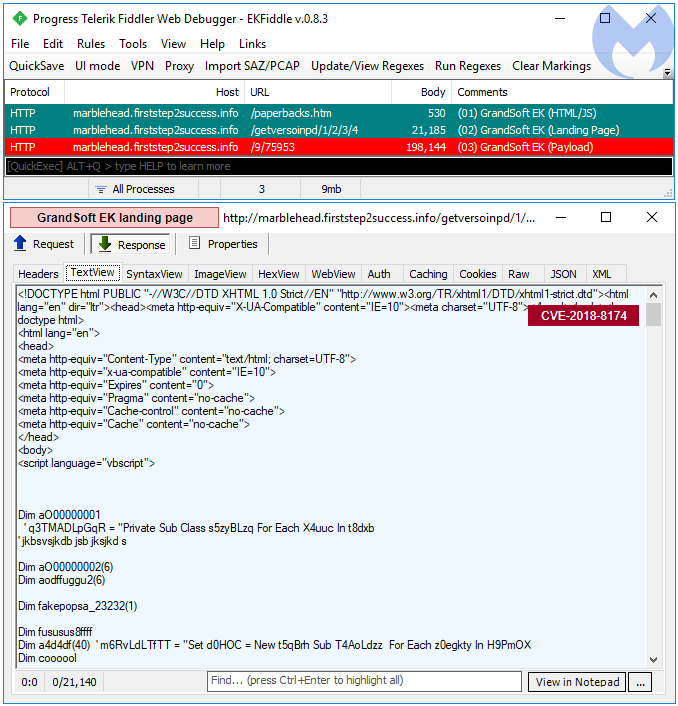
The payload in this sequence is the Ramnit banker.
6FDA89FBB9FD66EE929665E376077E07C1BD2AF2D91C63148A7F5E818E4D27B2
Magnitude EK
Magnitude EK continues to faithfully deliver its own brand of ransomware to targeted countries, such as South Korea. and Taiwan. It is one of the rare exploit kits that uses a truly fileless payload, which makes its extraction to disk a challenge.
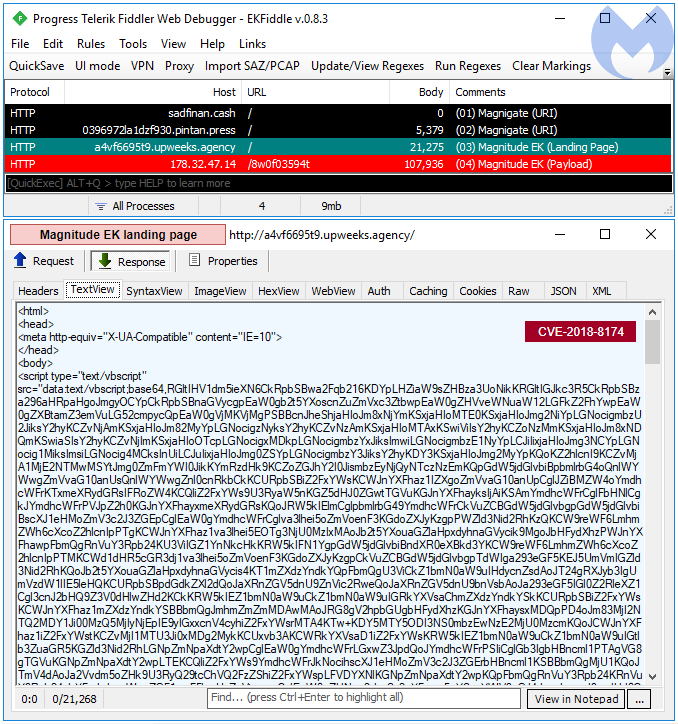
The payload in this sequence is Magniber ransomware (extracted with @hasherezade‘s hollows_hunter).
F229AE5F68C72E678D4D706CE84ABFCCC983A299E39BEBCD990AECE7E3F97D71
Underminer EK
We spotted Underminer EK a few times during the past quarter. This exploit kit is unique because its payload delivery, a bootkit, is vastly different from any other EK.
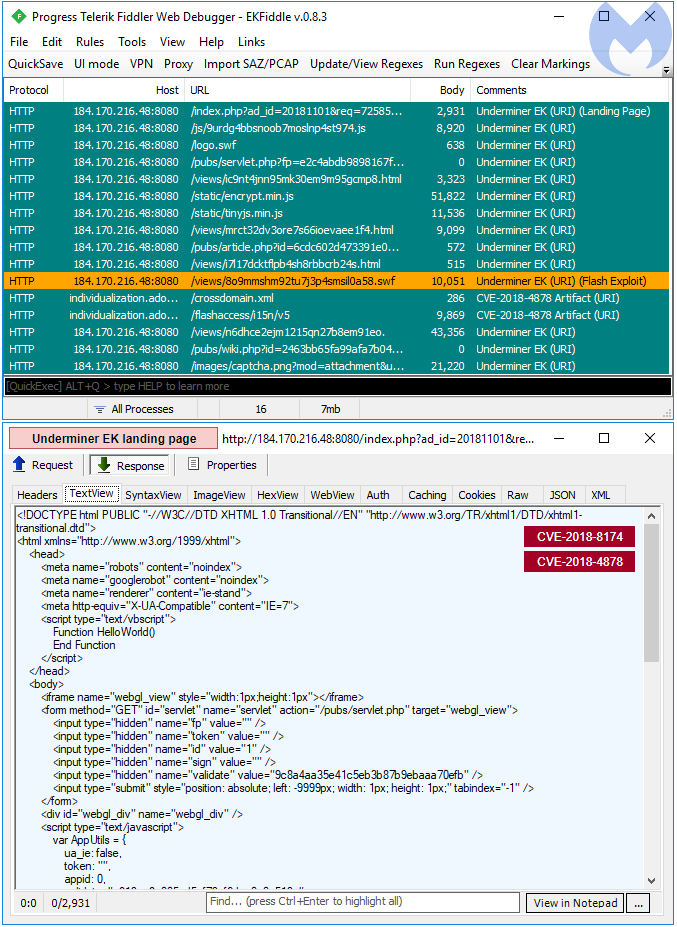
The payload in this sequence is a bootkit infector.
Mitigation
As always, it is important to keep systems up-to-date and reduce the attack surface whenever possible. The current vulnerabilities used by the above exploit kits have already been patched by their respective vendors.
Malwarebytes’ application hardening protection layer blocks these EKs before they even get a chance to drop their payloads.
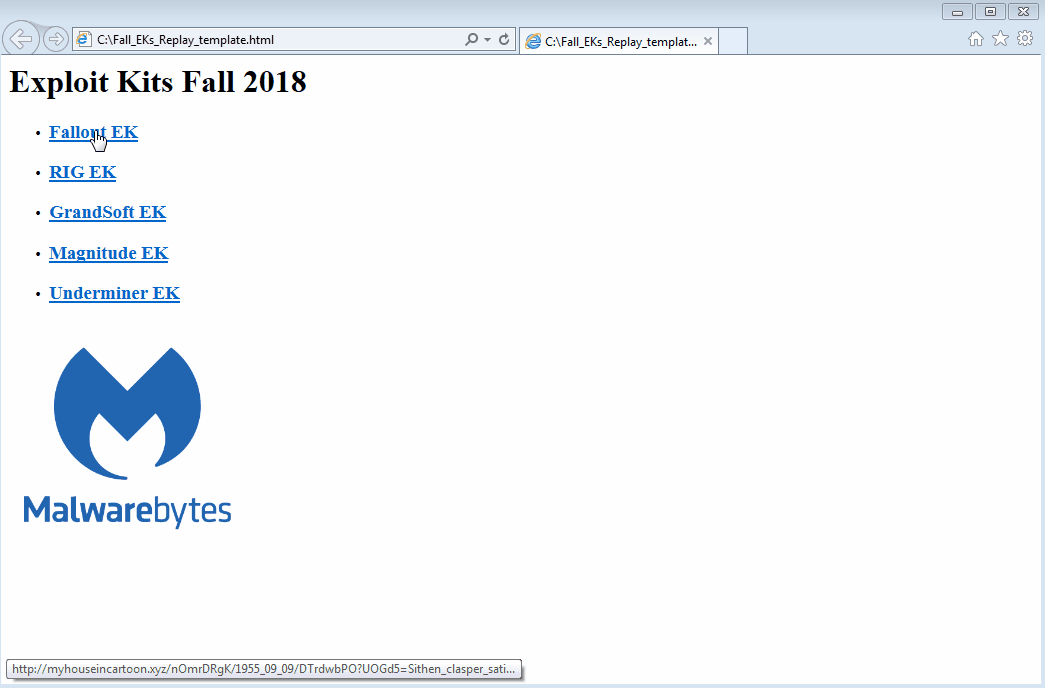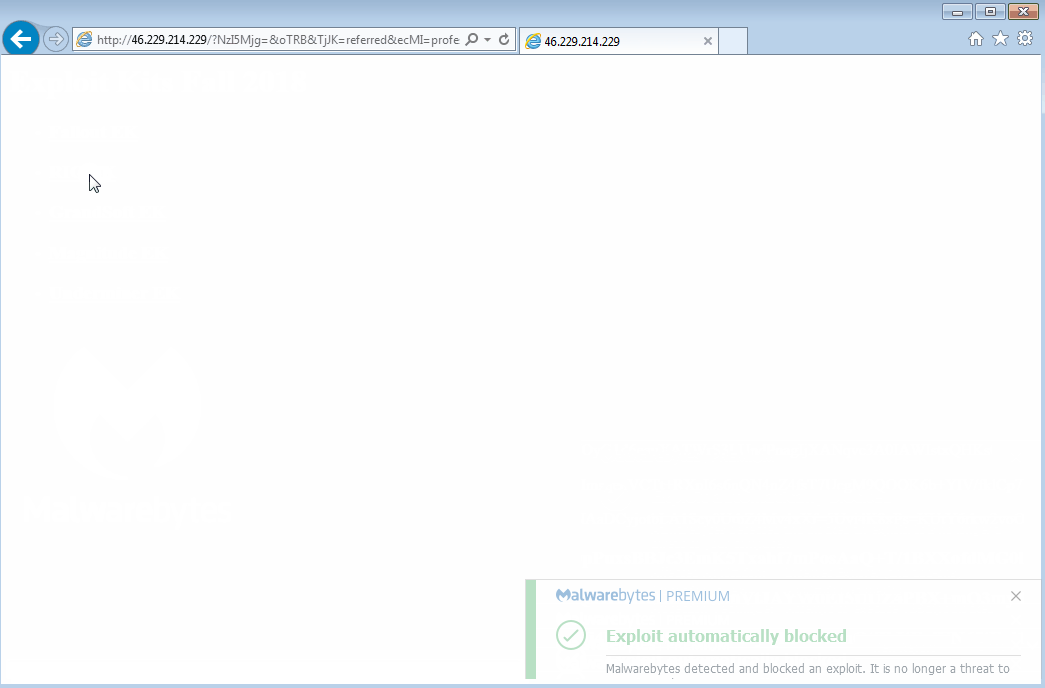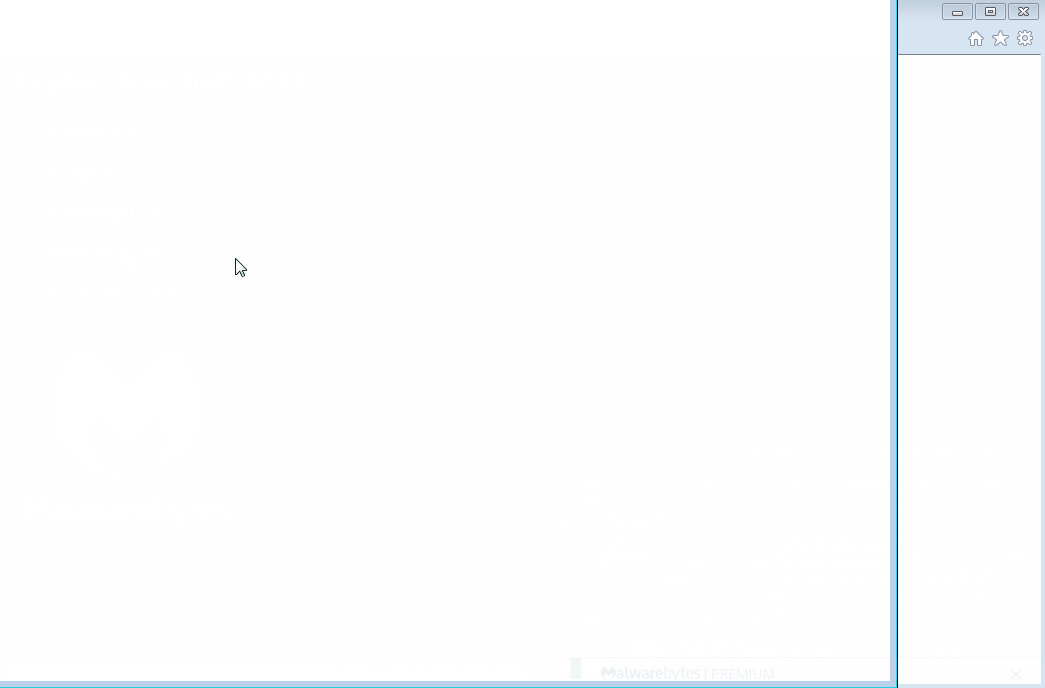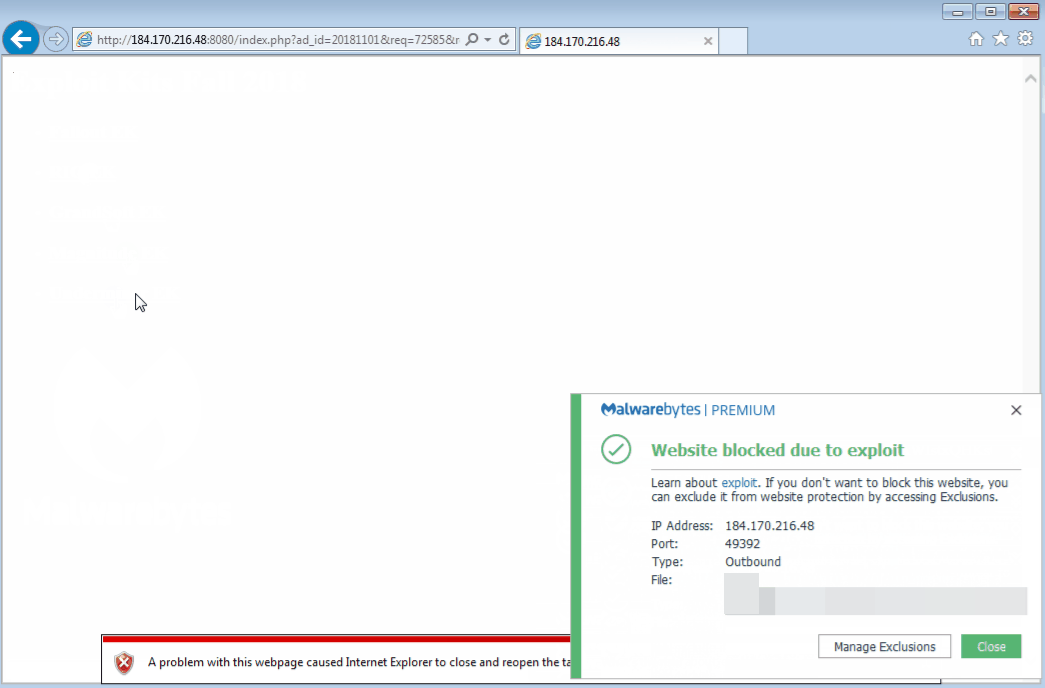
Extended shelf life
The recent addition of Fallout EK has given exploit kits yet another extension on their otherwise limited shelf life by tapping into existing and new malvertising campaigns with a wider geographic focus.
As 2019 comes closer, Internet Explorer is still offering opportunities for newer exploits yet to be weaponized, but we could see other browsers such as Edge gain some attention as well.










