In the past few weeks we’ve talked about the Neutrino and Magnitude exploit kits. This time, we take a look at RIG EK and in particular at various distribution channels and payloads.
Like most exploit kits, RIG relies on compromised sites and malvertising as its source of traffic but is one of the less sophisticated EKs due to its use of older exploits. For instance, its Flash exploit (CVE-2015-8651) was patched in late December 2015 whereas other EKs are using a more recent Flash exploit from May 2016 (CVE-2016-4117).
Despite a less potent engine, RIG EK still generates a fair amount of traffic via several malware campaigns. The redirection mechanism from compromised site or malvertising to RIG EK is either done server side (302 redirects) or client side (iframe, JavaScript).
Different malware campaigns may represent different customers of the exploit kit (which can explain the various malware payloads), or the same individual diversifying his operations for redundancy purposes. One surprise with the samples we collected below is the absence of ransomware, a payload that is usually very prevalent with other exploit kits. Instead, we see bots and stealers that are thoroughly packed and obfuscated.
Campaigns overview:
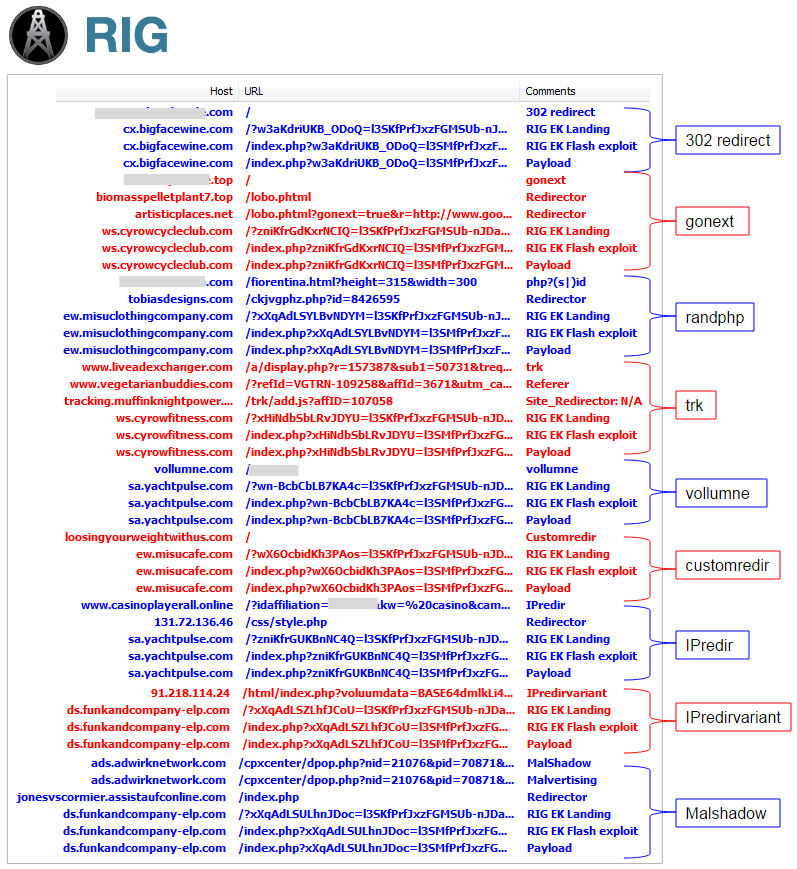
The naming convention here is very basic as we picked some string or pattern that was unique for each campaign and used it as a label to differentiate it from others. As a note, there are probably additional variants, and other gates we have not documented here.
302 redirect
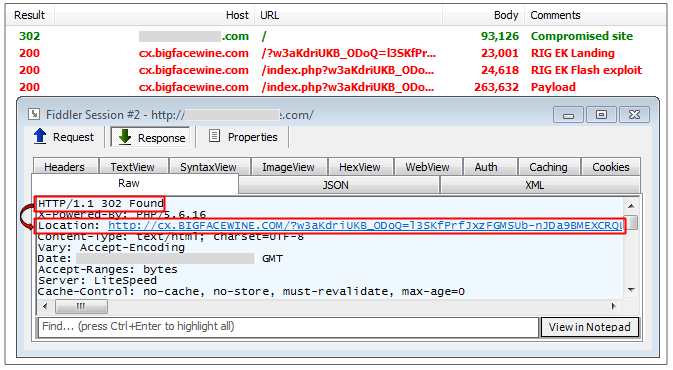
The 302 redirect path, as its name indicates it, uses server side 302 redirection to RIG EK’s landing page. For the most part, these are hacked sites that still load their content and perform the redirect.
Payload:
- 0289ab23c01b2ccb9f347035b5fca1bf8a607bc511dfbe52df8881c6482a4723
- Neurevt Bot (Betabot)
- Unpacked: malwr
- Neurevt info
gonext
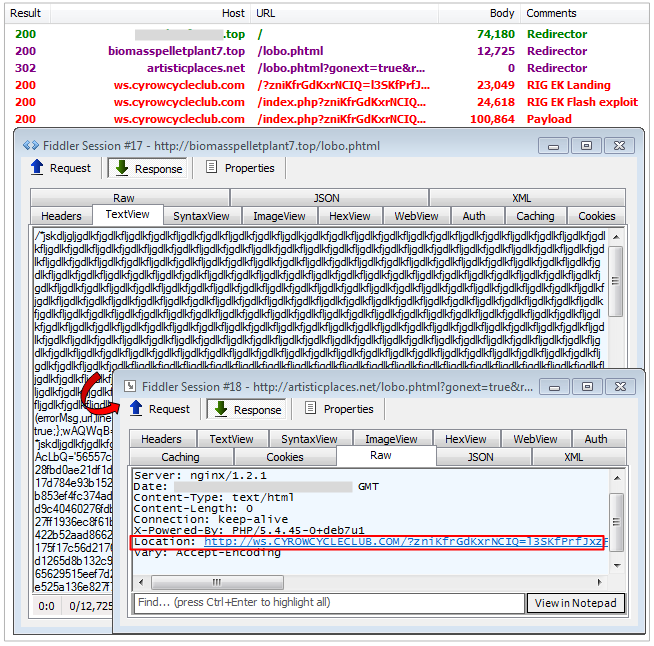
This is one of the most active campaigns easily recognizable by the use of redirectors from certain TLDs, such as .top, and HTML files largely obfuscated with naming patterns such as lobo.phtml. The ultimate redirect to RIG relies on a 302, from a fairly static domain name (i.e. artisticplaces.net).
Payload:
- c5184a30a88c234d3031c7661e0383114b54078448d62ae6fb51a4455863d4b5
- Dofoil (Smoke Loader)
- Unpacked: malwr
- Smoke Loader info
- C&C: prince-of-persia24.ru
- Downloads: payload (IRC bot, C&C: med-global-fox.com)
randphp
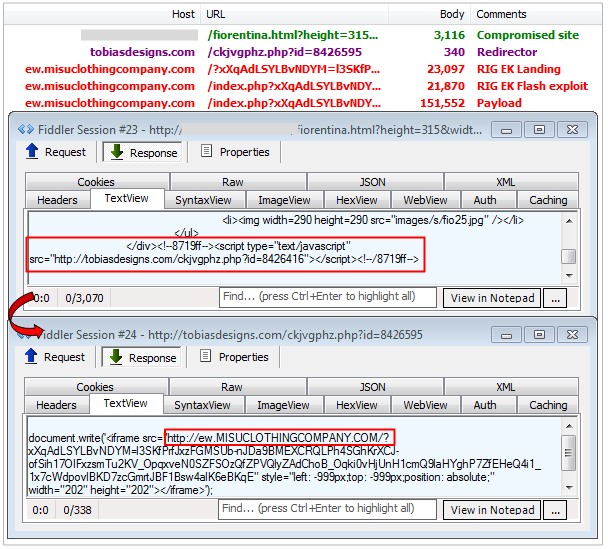
This distribution path is also very popular and leverages compromised sites injected with JavaScript that redirects to an intermediary site using a randomly named php file that contains an iframe to RIG EK.
Payload:
- 1a3e2f940db24ff23c40adfd45d053036bad7372699c904c1ef0aaae81b24c5d
- Packed with VB packer, crashes
trk
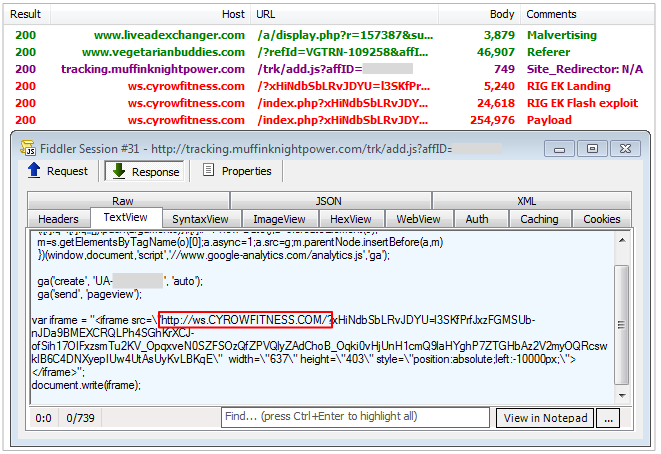
This campaign is based on malvertising that uses a two level redirection: a spammy/dummy site and a tracker which logs stats via a Google Analytics account and redirects to RIG EK via iframe.
Payload:
- 09f7926969f1dd11b828e2a3537c923646389140b2dba64c0b623b58099f3b64
- Gootkit
- Unpacked: malwr
vollumne
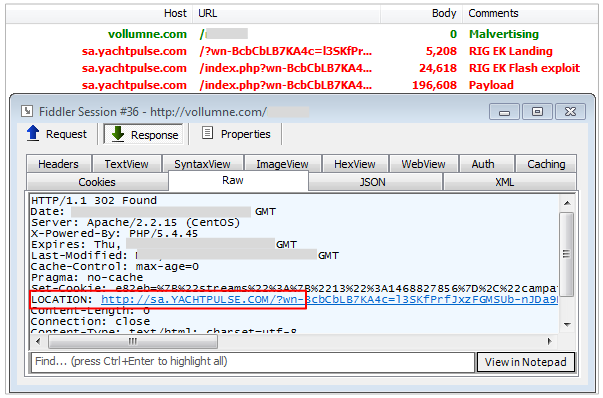
This is yet another malvertising based campaign that funnels all traffic via vollumne.com, a domain registered to gianafyn410@yahoo.com (Russia). It uses a simple 302 redirect (server side) mechanism to RIG EK.
Payload:
- fe128f8bc1be6a0076dd78133ae69029374e25b2662aaafdeb846af1bc60b617
- Packed with VB packer, crashes
Custom redirector
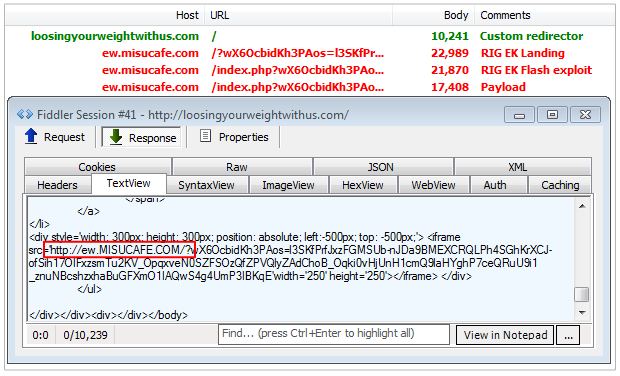
This attack path appears to use hacked or bogus domains stuffed with other content (porn, viagra, other ads). It may also be linked via malvertising and the redirection mechanism to RIG EK happens thanks to an iframe tag injected at the bottom of the home page.
Payload:
- bb863da684e0b4a1940f0150a560745b6907c14ff295d93f73e5075adb28f3ea
- Backdoor – turns off Windows Security Center
- Automated analysis: malwr
IPredir
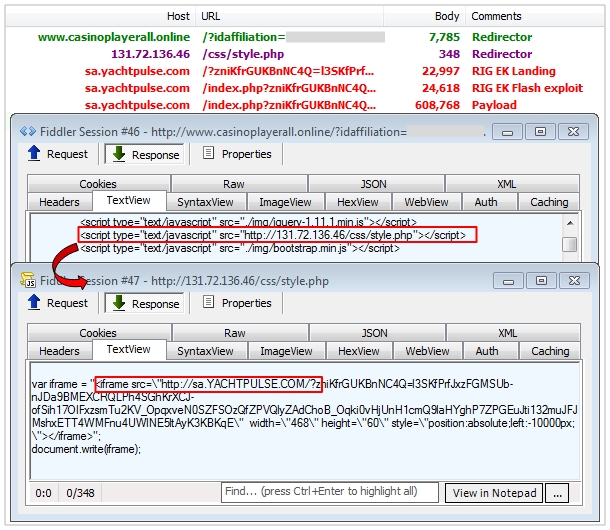
This is another easily recognizable attack with a custom redirector (i.e. casinoplayerall.online) and a redirect to a hardcoded IP address (i.e. 131.72.136.46) performing the final redirection to RIG EK.
Payload:
- f21a7b90a83c482948206060d6637dffafc97ef319c9d7fa82f07cd9e8a7ec56
- Gootkit
- Unpacked: (intermediate payload) -> dropper_dll_service.dll
IPredirvariant
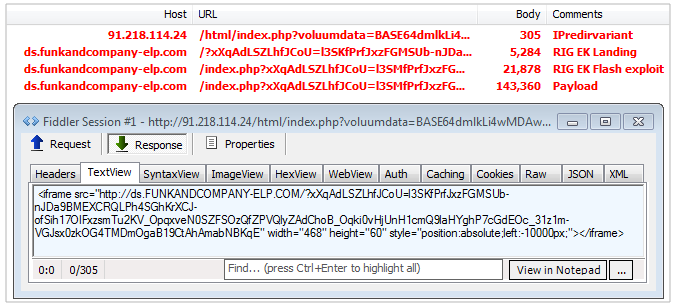
More recently we started seeing this redirect mechanism. These campaigns are malvertising driven, and lead to a harcoded IP address owned by threat actors.
Payload:
- a1985dd74238996ab137b21f1856a5787ce07c8cd09744a260aaf1310d4a8944
- Packed with VB packer, crashes
Malshadow
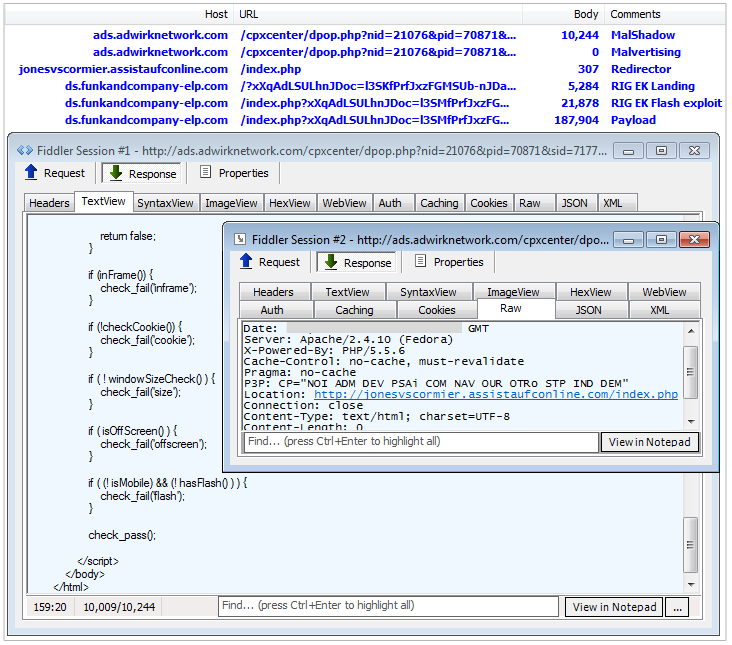
Malvertising based attack path with the use of domain shadowing as the redirector to RIG EK.
Payload:
- b91dd7571f191224ea8802bb9c9d153857b4f5d48eb72b811620268e8c954a00
- Gootkit
- Unpacked: dropper_dll_service.dll
Conclusion
The demise of Nuclear EK and the mysterious disappearance of Angler EK, by far two of the more sophisticated exploit kits to date, has lead to a new playing field where even smaller actors get increased exposure. Neutrino took the first spot and is used for high profile attacks via malvertising and a number of popular gates via hacked sites.
We continue to see RIG EK in malvertising attacks with low quality traffic and the tried and tested hacked sites distribution path, which all in all is very similar to Magnitude EK, except for the latter having an advantage with a better Flash exploit.
Malwarebytes Anti-Exploit customers continue to be protected against the RIG exploit kit.
Special thanks to @hasherezade for help with payload analysis!
IOCs:
Payloads (SHA256 dump)
gonext
- artisticplaces[.]net/lobo.phtml?gonext=true&r=
- biomasspelletplant2[.]xyz/lobo.html
- biomasspelletplant3[.]xyz/lobo.html
- biomasspelletplant4[.]xyz/lobo.html
- biomasspelletplant5[.]xyz/lobo.html
- biomasspelletplant6[.]xyz/lobo.html
- biomasspelletplant7[.]top/lobo.html
- biomasspelletplant[.]xyz/lobo.html
- 24x7apple[.]com/sp1.phtml?gonext=
- affordableaffairsbyyoli[.]com/spm.phtml?gonext=
- analyticsonjs[.]com/analytics.phtml?gonext=
- balkanlight[.]com/bro.phtml?gonext=
- blockmycalls[.]com/sm.phtml?gonext=
- buzzinarea[.]com/immo.phtml?gonext=
- capemadefieldguide.org/dan.phtml?gonext=
- capemadefieldguide.org/ram.phtml?gonext=
- clothes2017.club/oly.phtml?gonext=
- cookingschoolonline.us/bro.phtml?gonext=
- dadadeo[.]com/jes.phtml?gonext=
- easyastrologyoraclecards[.]com/bruno.phtml?gonext=
- ebldf[.]com/bruno.phtml?gonext=
- enkorepartners[.]com/bruno.phtml?gonext=
- gstatistics[.]com/stat.phtml?gonext=
- henrymountjoy[.]com/sm.phtml?gonext=
- littlebungas[.]com/myst.phtml?gonext=
- mikeandangelina[.]com/myst.phtml?gonext=
- molodinoska[.]com/bro.phtml?gonext=
- monmariemakeupartist[.]com/sp1.phtml?gonext=
- monsterbungas[.]com/myst2.phtml?gonext=
- religiousapproaches[.]com/ch.phtml?gonext=
- religiouslandscape[.]com/ch2.phtml?gonext=
- siliconvalleydreams[.]com/oly.phtml?gonext=
- snovels[.]com/myst.phtml?gonext=
- svdreams[.]com/oly.phtml?gonext=
- tequilabuch[.]com/bro.phtml?gonext=
- thebookoneducation[.]com/bro.phtml?gonext=
- thebookoneducation[.]com/laze2.phtml?gonext=
- thebookoneducation[.]com/laze.phtml?gonext=
- thebookoneducation[.]com/may.phtml?gonext=
- thecasinobank[.]com/buggy.phtml?gonext=
- wordpresscache.org/bro.phtml?gonext=
- wordpresscache.org/youshynec.phtml?gonext=
- youthadvocatecoaching[.]com/shi.phtml?gonext=
- 103rdcomposite[.]net/forums/db/g3hbzckj.php?id=8548176
- az.mediancard[.]com/8xrvwbkd.php?id=8141864
- bitina[.]com/wqjkt8m2.php?id=12866788
- e-bannerstand[.]com/nycy2z8t.php?id=11726031
- ekitab[.]net/7thwcbvz.php?id=11741674
- fh380968.bget[.]ru/templates/stets1/hhwbwny9.php
- filosofia.top/j6fn3dfl.php?id=8294815
- forum.wloclawek[.]pl/dmzxkcbr.php?id=14338552
- gaptaquara[.]com.br/gkxpdffh.php?id=8231629
- gv-pk[.]com/bfnmvvlw.php?id=7912878
- illirico18[.]it/v98vrpz6.php?id=8247670
- jobroom.nichost[.]ru/zpgrkljm.php?id=10810290
- kromespb[.]ru/_VTI_CNF/rpwbr3gt.php?id=8519025
- louisiana-indonesia[.]com/qc8nf2nc.php?id=8324784
- multiporn[.]us/milfs/rzhxpbr8.php?id=1266474
- ocenem1.nichost[.]ru/ndpvy6rk.php?id=10810290
- russianbiker.de/4hyrb3fk.php?id=8062768
- shop.universalauto[.]ru/x6m2byg8.php?id=8295668
- tobiasdesigns[.]com/ckjvgphz.php?id=8426416
- ugasac[.]com/webapp/sigemave/3cdnvtkn.php?id=8186035
- waterjet-cutter[.]com/lc6jxqkv.php?id=15783431
- www.bma[.]com.ua/vk63ntzy.php?id=2259041
- www.hima-haven[.]com/rmbwj7ld.php?id=8118993
- www.nspiredsigns[.]com/pfmj94vq.php?id=15876656
- www.rospravo[.]ru/k67cpfnn.php?id=8673574
- 131.72.136.46/css/style.php
- 185.86.77.27/css/style.php
- 84.200.84.230/css/style.php
- 91.218.114.24/html/index.php?voluumdata
- ads.adwirknetwork.com










