Ransom.Troldesh
Short bio
Ransom.Troldesh is Malwarebytes’ detection name for a type of ransomware that is also known as Shade. It is thought to be of Russian origin and has been around since 2014.
Symptoms
Ransom.Troldesh adds different extensions to the encrypted files, depending on the version of the ransomware. The most well-known extensions are:
- .xbtl
- .cbtl
- .no_more_ransom
- .better_call_saul
When the ransomware has finished encrypting files it will show a ransom note similar to this one:
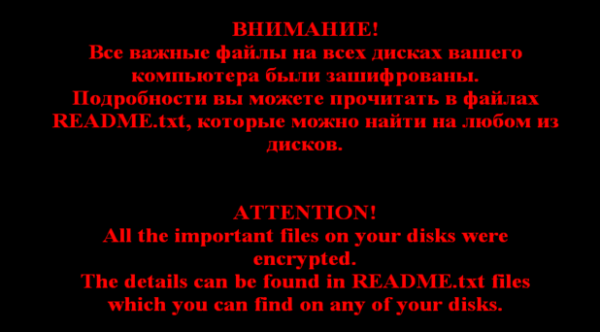
The README.txt files are dropped in many folders on the affected system. Most likely in every folder that has an encrypted file in it.
Type and source of infection
Ransom.Troldesh is ransomware. Ransomware is a type of malware that prevents users from accessing their system or personal files and demands ransom payment in order to regain access. Ransom.Troldesh is spread by malspam, typically in the form of attached .zip files. This ransomware sometimes uses a CMS on a compromised site to host downloads.
Aftermath
Ransom.Troldesh uses a strong encryption, so sometimes there is no way to regain your encrypted files for free, but there are free decryption tools available for some of the Troldesh variants. Check NoMoreRansom.org for your options.
Protection
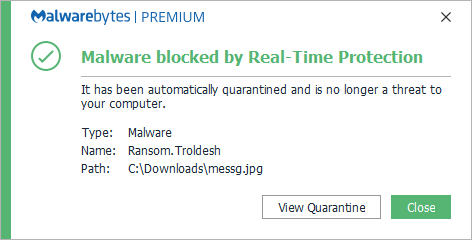
Malwarebytes protects users from Ransom.Troldesh by using real-time protection.
Home remediation
Malwarebytes can detect and remove Ransom.Troldesh without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Take note, however, that removing this ransomware does not decrypt your files. You can only get your files back from backups you made before the infection happened.
Business remediation
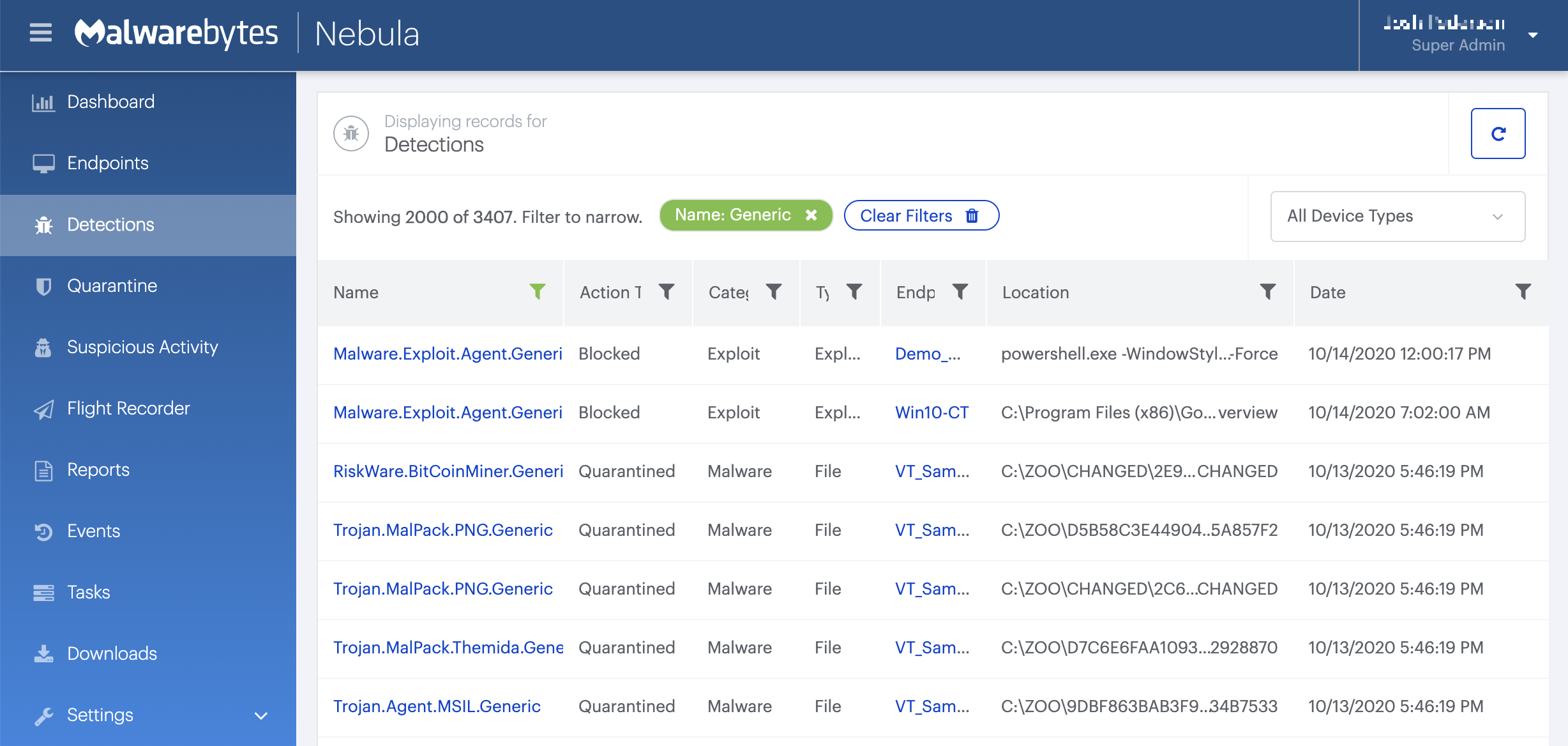
How to remove Ransom.Troldesh with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.

Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
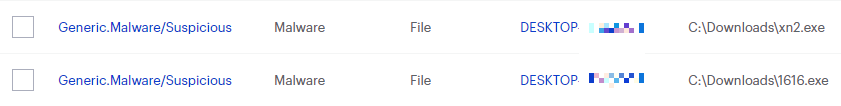
On the Quarantine page you can see which threats were quarantined and restore them if necessary.
IOCs
Extensions of encrypted files
- .xtbl
- .ytbl
- .cbtl
- .no_more_ransom
- .better_call_saul
- .breaking_bad
- .heisenberg
- .da_vinci_code
- .magic_software_syndicate
- .windows10
- .crypted000007
- .crypted000078
Contacts: Novikov.Vavila@gmail.com Selenadymond@gmail.com RobertaMacDonald1994@gmail.com IPs TCP 154.35.32.5 443 outgoing Bitcoin: 1Q1FJJyFdLwPt5yyZAQ8kfxfeWq8eoD25E Domain : cryptsen7fo43rr6.onion





