Sodinokibi.Ransom.Encrypt.DDS
Short bio
Sodinokibi.Ransom.Encrypt.DDS is Malwarebytes’ detection name for a ransomware variant that targets Windows systems as detected by Malwarebytes’ Katana engine.
The detection names are produced by Malwarebytes 4 and Malwarebytes business products. These generic malware detections are due to our new automated signature system called BytesTotal and specifically the DDS engine that are based on Machine Learning technology with 100% autonomous learning which don’t require any human interaction to correctly identify malware. These techniques are part of Malwarebytes’ Katana engine and were developed for automated mass detection of wide ranges of malware and adware.
Type and source of infection
This detection was based on the resemblance with Ransom.Sodinokibi. The version that surfaced a few months after the REvil infrastrcuture was taken down adds a random extension name to affected files and creates a ransom note—both as text and HTML files—identical to old Sodinokibi versions.
Protection
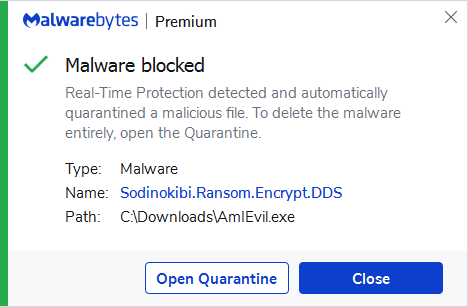
Malwarebytes blocks Sodinokibi.Ransom.Encrypt.DDS
Home remediation
Malwarebytes can detect and remove Sodinokibi.Ransom.Encrypt.DDS without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get startedbutton.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Business remediation
How to remove Sodinokibi.Ransom.Encrypt.DDS with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.

Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
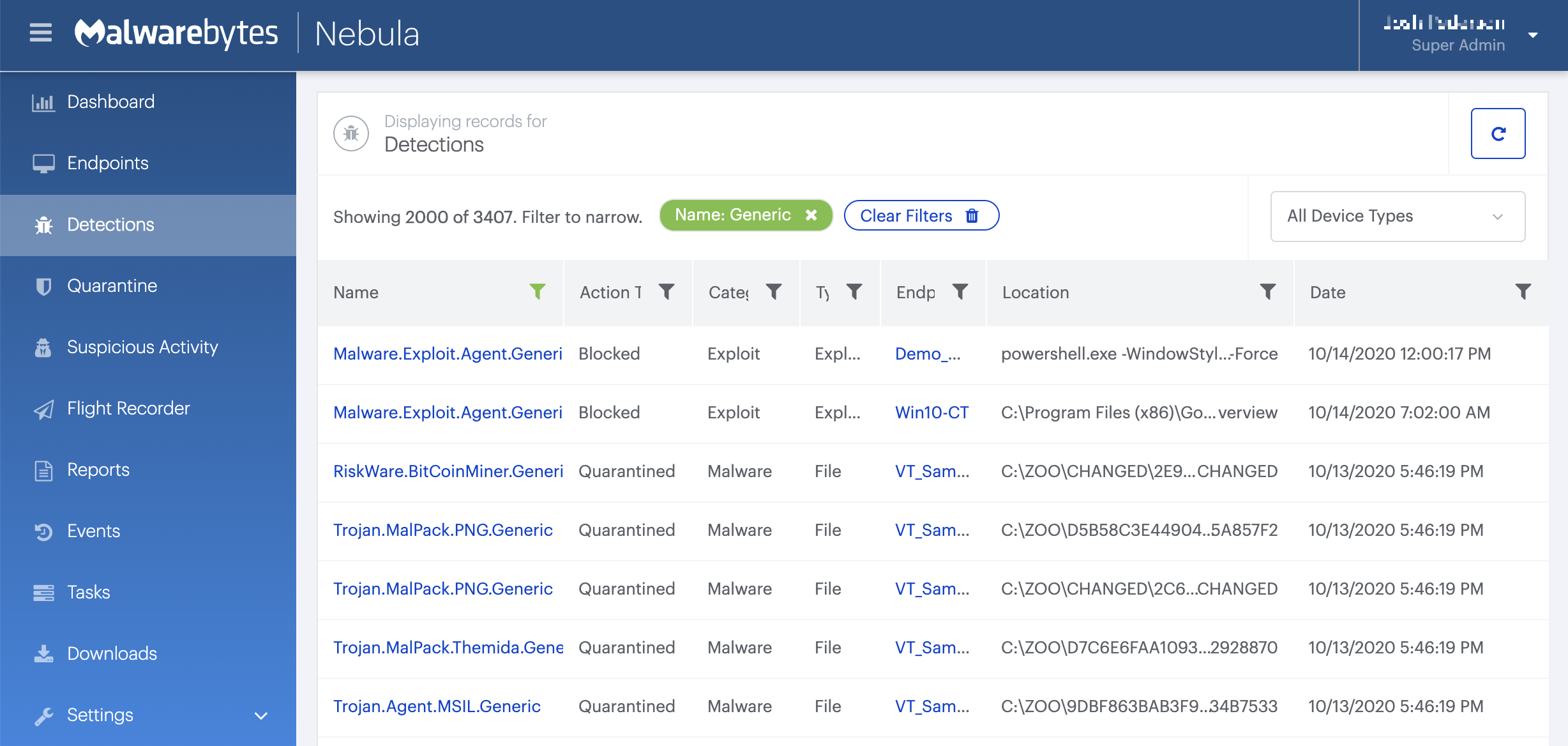
On the Quarantine page you can see which threats were quarantined and restore them if necessary.





