Trojan.TrickBot.Generic
Short bio
Trojan.TrickBot.Generic is Malwarebytes’ detection name for the generic detections of a family of banking Trojan targeting Windows machines.
Developed in 2016, TrickBot is one of the more recent banking Trojans, with many of its original features inspired by Dyreza (another banking Trojan). Besides targeting a wide array of international banks via its webinjects, Trickbot can also steal from Bitcoin wallets.
Some of its other capabilities include harvesting emails and credentials using the Mimikatz tool. Its authors also show an ability for constant new features and developments.
Trojan.TrickBot comes in modules accompanied by a configuration file. Each module has a specific task like gaining persistence, propagation, stealing credentials, encryption, and so on. The C&Cs are set up on hacked wireless routers.
Symptoms
The endpoint user will not notice any symptoms of a Trickbot infection. However, a network admin will likely see changes in traffic or attempts to reach out to blacklisted IPs and domains, as the malware will communicate with Trickbot’s command and control infrastructure to exfiltrate data and receive tasks.
Some variants of Trojan.TrickBot.Generic gain persistence by creating a Scheduled Task.
Type and source of infection
Trojan.TrickBot.Generic focuses on stealing banking information. TrickBot typically spreads via malicious spam campaigns. Other methods of propagation include infected attachments and embedded URLs. Trojan.TrickBot.Generic is also seen as a secondary infection dropped by Trojan.Emotet.
Aftermath
Due to the way Trickbot spreada through a company’s network, any infected machine on the network may re-infect machines that have been previously cleaned when they rejoin the network. Therefore, IT teams need to isolate, patch, and remediate each infected system one-by-one. This can be a long and painstaking process.
Protection
Malwarebytes can also protect users from Trojan.TrickBot.Generic with our real-time protection.
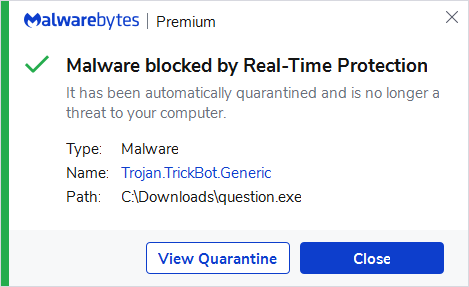
Malwarebytes blocks Trojan.TrickBot.Generic
Home remediation
Malwarebytes can detect and remove Trojan.TrickBot.Generic without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Business remediation
Malwarebytes can detect and remove Trojan.TrickBot on business endpoints without further user interaction. But to be effective on networked machines, you must first follow these steps:
- Identify the infected machine(s).
- Disconnect the infected machines from the network.
- Patch for EternalBlue.
- Disable Administrative Shares.
- Remove the Trickbot Trojan.
- Change account credentials.
Identifying the infected machines
If you have unprotected endpoints/machines, you can run Farbar Recovery Scan Tool (FRST) to look for possible Indicators of Compromise (IOC). Besides verifying an infection, FRST can also be used to verify removal before bringing an endpoint/machine back into the network.
Disabling Administrative Shares
Windows server shares by default install hidden share folders specifically for administrative access to other machines. The Admin$ shares are used by Trickbot once it has brute forced the local administrator password. A file share sever has an IPC$ share that Trickbot queries to get a list of all endpoints that connect to it. These AdminIP shares are normally protected via UAC, however, Windows will allow the local administrator through with no prompt.
The most recent Trickbot variants use C$ with the Admin credentials to move around and re-infect all the other endpoints.
Repeated re-infections are an indication the worm was able to guess or brute force the administrator password successfully. Please change all local and domain administrator passwords.
It is recommended to disable these Admin$ shares via the registry, as discussed here. If you do not see this registry key, it can be added manually and set up to be disabled.
To remove the Trickbot Trojan using Malwarebytes business products, follow the instructions below.
How to remove Trojan.TrickBot with Malwarebytes Endpoint Protection
- Go to the Malwarebytes Cloud console.
- To allow you to invoke a scan while the machine is off the network, go to Settings > Policies > your policy > General.
- Under Endpoint Interface Options, turn ON:
- Show Malwarebytes icon in notification area
- Allow users to run a Threat Scan (all threats will be quarantined automatically)
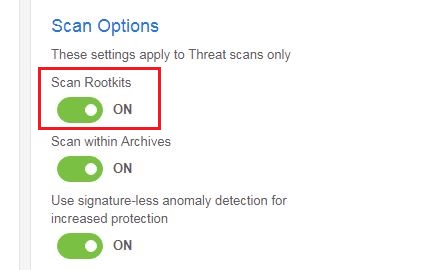
- Temporarily enable Anti-Rootkit scanning for all invoked threat scans. Go to Settings > Policies > your policy > Endpoint Protection > Scan Options
- Set Scan Rootkits to ON.
- Once the endpoint has been updated with the latest policy changes:
If you have infected machines that are not registered endpoints in Malwarebytes Endpoint Protection, you can remove Trickbot with our Breach Remediation tool (Malwarebytes Incident Response).