During our malware investigations, we are often learning about new techniques or ways the bad guys try to bypass us. But sometimes, we also experience cultural differences or discover some new things about people or countries.
Today is such a case, with a bit of a geography lesson brought to us by the Nuclear exploit kit, which takes us to Croatia.
Our journey starts with “Slobodna Dalmacija” (“Free Dalmatia” in English), a popular Croatian newspaper that was founded in 1943.
Dalmatia is one of four Croatian regions, the others being Croatia proper, Slavonia, and Istria.
According to Wikipedia, “the first issue of Slobodna Dalmacija was published on June 17, 1943 by Tito’s Partisans in a cave on Mosor, a mountain near Split, which was occupied by the Italian army during that time. The paper was later published in various locations until Split was liberated on October 26 1944.”
Since then, the newspaper has grown in popularity and has an online version, as most newspapers do these days.
slobodnadalmacija.hr (do not visit unless you are in a Virtual Machine) is a very popular website, ranking at #21 in Croatia, with an estimated 3.2 M visits a month according to SimilarWeb.
Considering the 2011 census counted a little over 4 M inhabitants in Croatia, this site’s traffic is quite high.
This brings us to our main topic, the fact that the ad server running on this site has been compromised and is redirecting visitors to the Nuclear exploit kit.
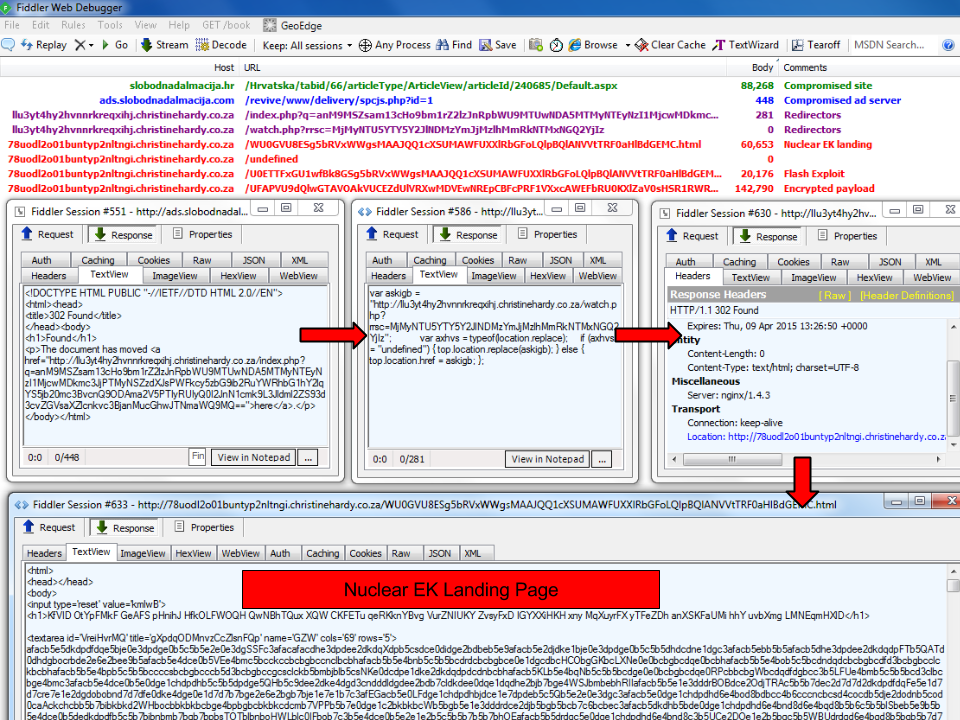
The main culprit is the newspaper’s own ad server which appeared to have been hacked:
hxxp://ads.slobodnadalmacija.com/revive/www/delivery/spcjs.php?id=1
This is slightly different from the regular malvertising attacks we see where malicious code is loaded from a third-party.
In this case, the server itself has been compromised and it’s a more tricky situation because it will require a full forensics investigation into the “how, when, where, etc…”
Malwarebytes Anti-Exploit users are already protected against this attack:

The malware that would have been downloaded from this attack is detected as “Trojan.Glupteba” by Malwarebytes Anti-Malware.
Glupteba via the Nuclear EK is the mark of the Windigo gang (thanks to ‘you know who you are’ for linking the two). Infected computers become part of a large botnet and their main task is to send spam.
Upon execution, the payload connects to 87.107.133.83, an IP address in Iran which is most likely its command and control server.
We have notified the owners of the Croatian website via email in their own tongue (thanks Stefán!) and hope they are able to restore the site to a clean state shortly.