Evolve is a new co-op game which involves four people running after a big monster and firing laser beams until it decides to fall over (that’s the TL;DR version).
It’s been whipping up hype for some time now, and with the recent release of the game on February 11 malware was always going to follow close behind.
The game is designed to pitch four human players versus one human-controlled monster, and cheats which claim to offer an edge to the solo monster player are always going to be the kind of bait which lures a hasty Kraken to their doom.
Sure enough, there’s a link going around on Twitter which takes advantage of related hashtags and has 274 Retweets at time of writing [Update – Tweet has now been deleted]
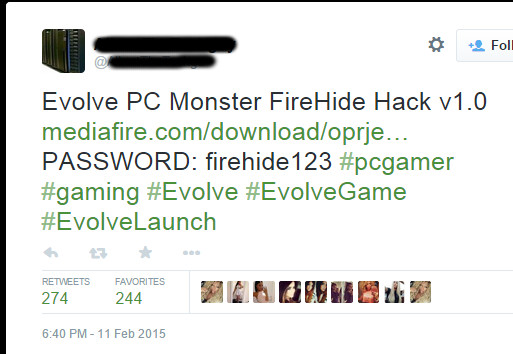
The supposed cheat file is called
Evolve PC Monster FireHide Hack v1.0
and promises a boost for anybody not doing very well controlling the monsters. The Readme which comes with the executable explains what the deal is:
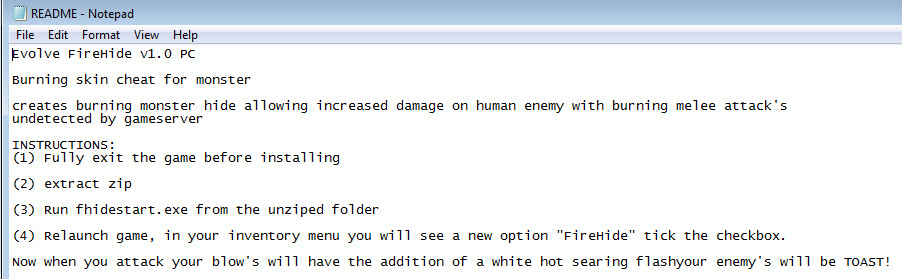
Burning skin cheat for monstercreates burning monster hide allowing increased damage on human enemy with burning melee attack's
undetected by gameserver
INSTRUCTIONS:
(1) Fully exit the game before installing
(2) extract zip
(3) Run fhidestart.exe from the unziped folder
(4) Relaunch game, in your inventory menu you will see a new option "FireHide" tick the checkbox.
Now when you attack your blow's will have the addition of a white hot searing flash your enemy's will be TOAST!
The “cheat” file – called Firehide.exe and weighing in at 987.5KB – is not what it appears to be. Running the executable results in a number of events on the target PC which are consistent with keyloggers created by the Predator Pain builder [Trend Micro PDF]. Similarities include the following:
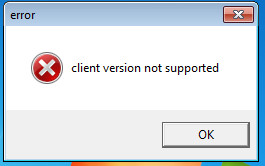
1) A supposed error message upon running the file. Predator Pain allows Malware authors to whip up error messages of their choosing:
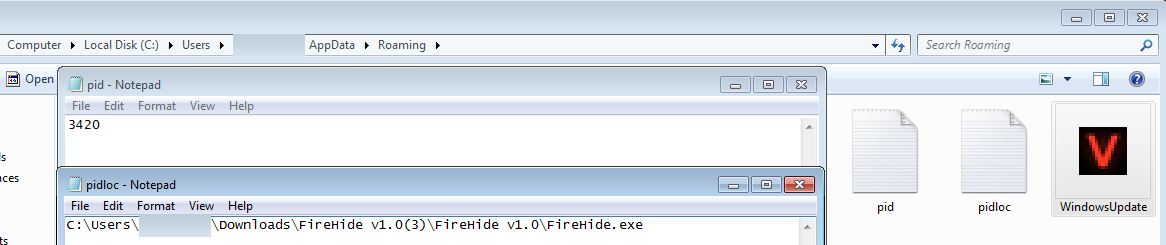
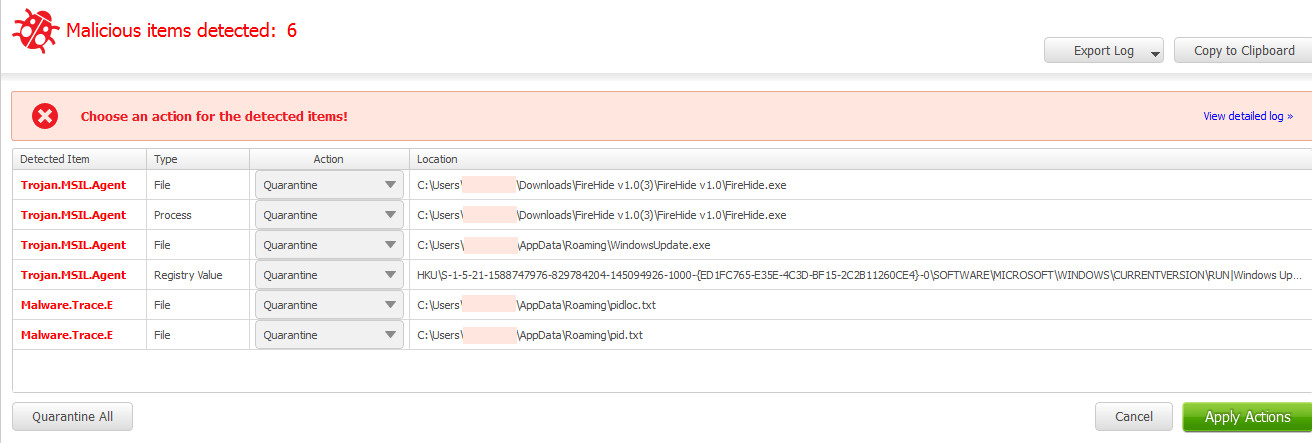
2) The executable copies itself into
C:Users[username]AppDataRoaming
along with pid.txt and pidloc.txt, which list the path and ID of the Keylogger. Note that the file is designed to run at startup, meaning a reboot of the OS won’t fix anything. This is another feature of Predator Pain files.
You can see an overview of what can happen in a typical Predator Pain related infection over at Stop Malvertising, and we’ve also seen mention of the above file sending home data via email (though we didn’t witness this taking place during testing). Depending on the aim of the Malware author, these files can be configured to spread by USB, P2P, steal browser data, take screenshots, capture keystrokes and send it all back to base via Email, FTP or PHP. As you can see, it’s a very versatile tool and gives the creator lots of ways to go about compromising a PC.
One would assume the target here is gaming credentials given the theme of the executable, but selecting which specific logins you want to go after is as simple as ticking checkboxes in the builder so the sky is potentially the limit.
VirusTotal scores are currently flagged at 30 / 57, and users of Malwarebytes Anti-Malware will find we detect FireHide.exe as Trojan.MSIL.Agent.
It’s only natural that gamers would look for an edge – nobody wants to face off against four other people without a method to even the odds – but this isn’t the way to do it, and will have you tranquilized and shipped off to a Malware Lab quicker than you can blink all twelve of your drool-coated night vision peepers.
Good hunting…
Christopher Boyd










