We detected a malvertising attack on popular dating site PlentyOfFish (POF) which draws over 3 million daily users.
The attack chain uses the Google URL shortener goo.gl as intermediary to load the Nuclear exploit kit. While we see this mechanism quite frequently within our telemetry, it is particularly difficult to reproduce it in a lab environment.
- www.pof.com
- mediaservices-d.openxenterprise.com
- newimageschool.com/adframe/banners/serv.php?uid={redacted}
- ad.360yield.com
- frexw.co.uk
- gp-[a-z].info
- goo.gl/zSQxk4
- ducumsacfire.caseyscollectables.com
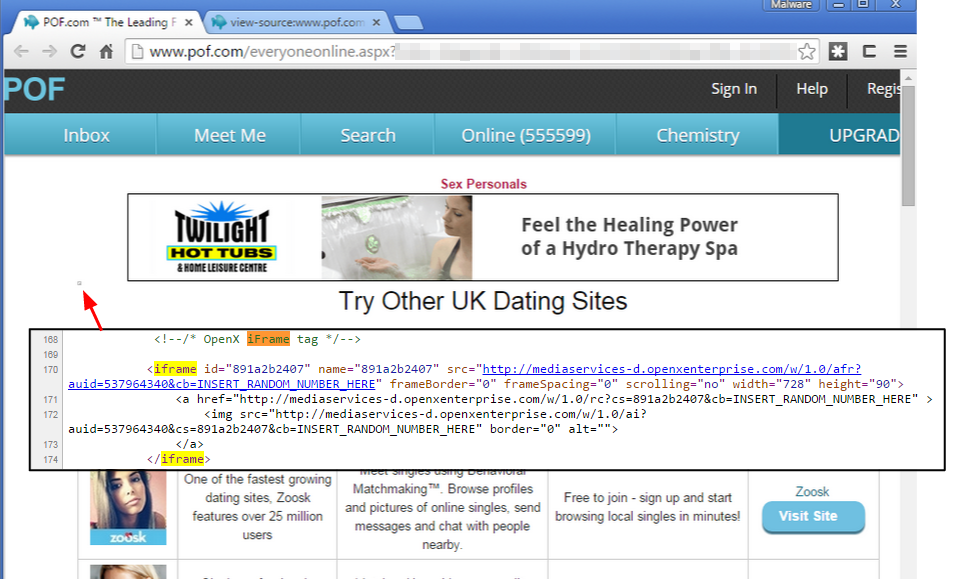
The ad network involved in the malvertising campaign (ad.360yield.com) was familiar and it turns out that we had observed it in a rare attack captured by our honeypots just one day prior.
As you can see in the picture below, the redirection chain goes through multiple hoops before reach its final destination, the exploit kit landing page.
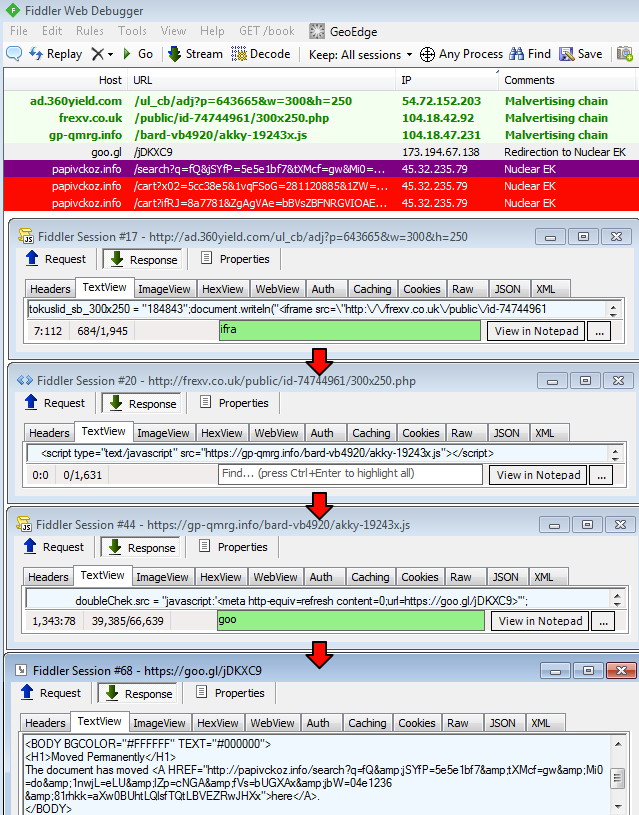
The sample collected in this particular instance was the Tinba banking Trojan. Given that the time frame of both attacks and that the ad network involved is the same, chances are high that pof[dot]com dropped that Trojan as well.
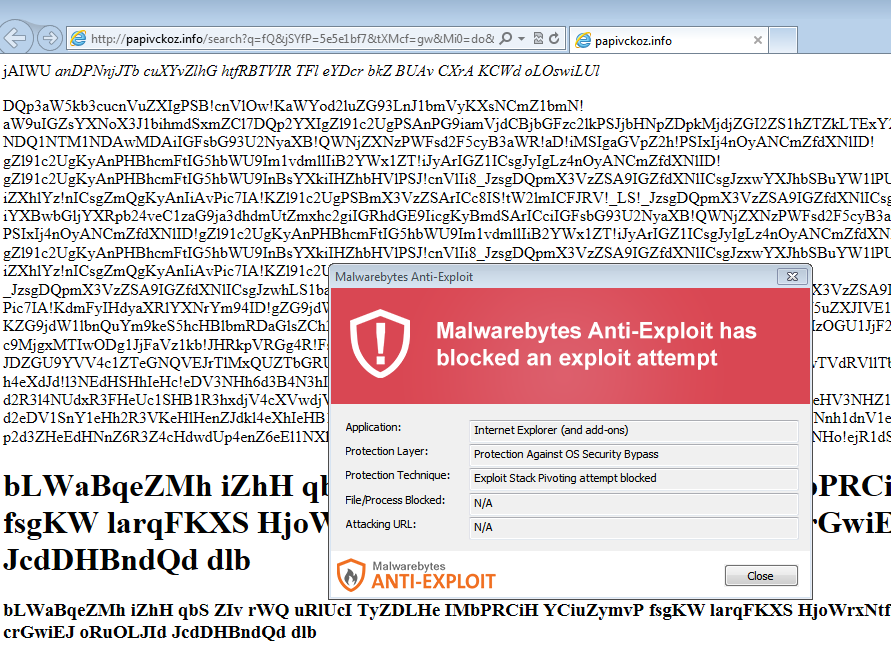
Malwarebytes Anti-Exploit users were protected against this attack.
We have contacted PlentyOfFish to make them aware of this issue and will update this post if we hear back.










