Dear Readers,
We regret to inform you that over the weekend, Malwarebytes was under direct, targeted attack from a new type of malware of unknown origin. The malware was shutting down systems left and right at our headquarters. We were able to cut off its spread through our network and obtain a sample of it from the infected systems before their hard drives were completely erased. It took our lead analysts over 10 hours to obtain a small amount of information that they could and we decided it was important to share it with you.First of all, the malware appears to have been completely destructive in nature, it was able to infect every type of operating system with every current security patch. Once infected, it mapped out a method of exit to another uninfected system then copied and executed itself on the new system. Finally, it began completely erasing everything on the system by writing over data with the hex characters 53:4b:59:4e:45:54 until nothing remained of the original data.
Further analysis of the attack has lead researchers to assume the attack was indeed targeted. In fact, the first files overwritten by the malware were identified as files and folders concerning the development of Malwarebytes Anti-Malware 2.0. It was discovered that the malware was able to search specifically for these files and destroy them before anything else. This information leads us to believe that the attack was to prevent the development and launch of our most powerful tool yet.
Our users have nothing to worry about however, as our team was able to secure all essential systems and keep the flow of updates coming to you. In addition, 10 minutes after obtaining the malware, Malwarebytes Anti-Malware is able to protect against it and any other similar malware.
As far as who was behind the attack, analysts are still baffled due to the unique and custom programming language it appears to be written in (being converted into C++ by an onboard translation tool and executed in real time). We are currently in the process of investigating the original entry point of the attack. However, some are saying it came from an e-mail received by our newest developer: J.Connor. One thing is for sure though, the file had been heavily modified due to the file properties claiming the malware was originally compiled on April 1, 2023.
Sincerely,
The Malwarebytes Staff
April Fools…. =P
The above story was obviously a hoax and I hope you got a good laugh out of it. On a serious note though, while April Fool’s day can be a great time to pull a silly prank on your friends or family, it is also synonymous with malware attacks. We are going to look at the historical association between April Fools and the spread of malware and help you enjoy the fun pranks but avoid the malicious ones.
Historical Evidence
Dorf Malware
The Dorf Trojan was one of the biggest online threats in 2007 and in 2008, the people behind the Trojan decided to take advantage of April Fools Day, to spread a new variant of their malware. As reported by Sophos, the attackers sent out massive amounts of e-mails with various subject lines all concerning April Fools. The e-mails varied in their content but all included a link to a webpage that downloaded Dorf malware onto the users system.

Special thanks to Sophos
Although Dorf is no longer an issue for modern malware fighters, other families of malware might be spread using the same method this year or the next, be sure to keep an eye out for any fishy (or Phishy) e-mails you get over the next few days.
Conficker
Conficker was a very terrifying malware for its time, most likely developed by a team of authors to completely infect an operating system at its very core; it held secret functionality that was aimed to be launched on April 1, 2009. Of course, when that date came and went and nothing happened, it was apparent that the joke was that there was no payload.
Special thanks to Sophos
While not spread on April Fools, the association nonetheless exists between malicious software and this jokester’s holiday. Sophos wrote about conficker and its April 1st association as well, offering the suggestion that something could have happened around the date rather than on it and what exactly Conficker was meant to do.
Social Networking Sites
As traditional e-mail phishing, fake ads and chat room bots are not enough to spread April Fools malware, many cyber-criminals have expanded to the social networking sector since its massive boom over the last few years. This kind of attack might come from a chain-status update that advertises a funny video or a link to some tragic story about a person who took an prank too far. Cyber criminals don’t hold back when it comes to pulling on the heart strings to get you to click on a link.
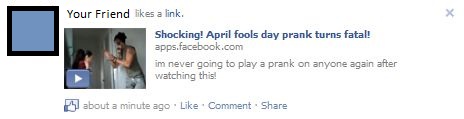
Special thanks to Lauren Mikov
In a blog post from 2011, Lauren Mikov wrote about the dangers of social networking scammers on April fool’s day and describes some methods on how you can remove malicious Facebook apps if you happen to fall victim to one of their scams.
Precautions
If you have been doing computer security right, then you have nothing to worry about. The attacks will not come on any venue that you aren’t already familiar with. You won’t open a letter and suddenly be infected with malware and you won’t turn on the TV and have malware downloaded into your phone.
However, if you haven’t been following the guidelines we post on this blog nearly every week, then you might be in trouble. To keep yourself safe from online threats, especially on April Fools:
- Do not open any suspicious e-mails, even if they are from a friend or family member. Call them first and ask about the e-mail before opening it and especially CLICKING on any link included.
- Do not fall for a funny link on Facebook, be it video or otherwise. If you want to see if the video is legit, check out Youtube and type in the title posted on the link in Facebook, then you could watch the video and know you are safe.
- Just go ahead and disable Java from your browser, along with Flash. The year 2013 has not been the best for browser security and this is mainly due to the increase in exploits being discovered for applications like Java. So at least for the next week, completely disable Java and Flash.
- Attacks might not come from a source that you can click on, even navigating to web sites can be dangerous with all the exploit kits out there, so be careful where you surf, try to stay on legit web sites that you trust.
- Keep your antivirus and anti-malware definitions up-to-date. Keep in mind that you can easily update Malwarebytes Anti-Malware automatically without it ever bothering you to click to update and stay protected constantly from all the new threats by configuring your scheduler to the settings below.
Conclusion
If this blog post made you a little scared or upset, I do apologize for that. However, keep in mind that while my example of an April fool’s joke was obviously silly, cyber criminals will not easily give away the true intent of their messages and will do anything they can to get you to download that malware or give up that password. Please follow the guidelines we put out for today and the rest of your life. Thanks for reading and stay safe!
—————————————————————————————————————————–
Adam Kujawa is a computer scientist with over eight years’ experience in reverse engineering and malware analysis. He has worked at a number of United States federal and defense agencies, helping these organizations reverse engineer malware and develop defense and mitigation techniques. Adam has also previously taught malware analysis and reverse engineering to personnel in both the government and private sectors. He is currently the Malware Intelligence Lead for the Malwarebytes Corporation. Follow him on Twitter @Kujman5000











