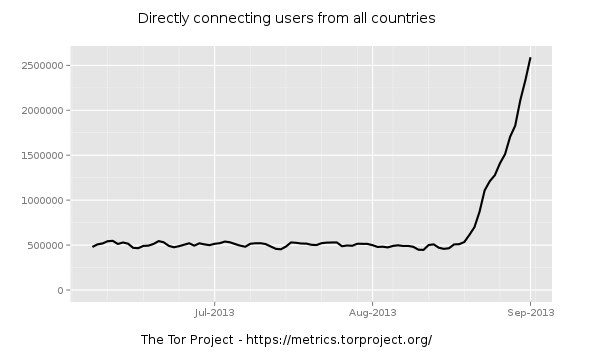
You might have already heard that last month’s traffic within the Tor network saw a significant increase. Over 1.2 million users during the month of August to be exact–that’s more than twice the amount of average traffic going through their network.
Tor, sometimes referred to as the “onion-routing” network, exists as a volunteer effort to conceal the identity of its users.
Conversely, Tor has also been used by criminals to peddle wares and offer illegal services.
A handful of explanations can explain this traffic surge: more users seeking privacy after disclosures of government surveillance on internet traffic, the Syrian civil war, and the release of ‘The Pirate Browser’ on August 10.
There doesn’t seem to be any sign of decline since the August takeoff. In fact, the numbers keep rising every day, and the Tor network is having difficulty handling it all.
“The tremendous influx of new clients that started mid-August is stretching the current Tor network and software to its limits,” their weekly news report stated yesterday.
It seems highly unlikely that this traffic surge would be caused by a sudden influx of privacy-seeking users, or even a civil war.
Many security experts have suggested the presence of a Tor botnet, which appears more believable than alternative theories.
Over at Fox-IT, researchers have analyzed a botnet that suggests that very notion. This botnet, called “SBC” by its operators, recently switched to Tor as its communications channel.
In their blog, Fox-IT explains how an already massive botnet making the switch to the Tor network could easily explain the traffic increase.
Image: Fox-IT blog
When you consider a botnet that’s compromised thousands of computers worldwide making a change in its traffic channel, the traffic metrics from Tor seem to make a lot more sense.
However, it’s not absolutely certain yet that the SBC botnet is the cause.
We’ll keep you updated with any developments on this story. In the meantime, you can read the full blog from Fox-IT here.
_______________________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell









