Security company Curesec disclosed a vulnerability that disables the lock screen in Android 4.3 Jelly Bean. Android 4.3 is Google’s most widely distributed version of their mobile operating system — about 54.5 percent of Android users are on Jelly Bean.
Android has a few options when it comes to locking your device: PIN, pattern, or facial recognition. The security hole lies in the Java class that handles which lock type is used.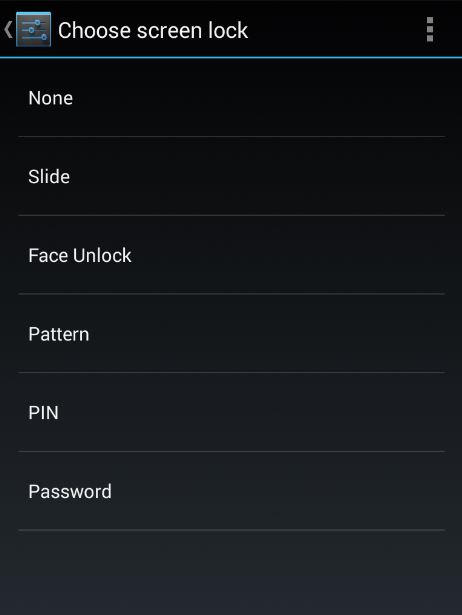
When a user changes the lock type, they are required to enter the lock/PIN of the previous one, if a malicious app were to target this vulnerability it could bypass this check altogether.
The Curesec’s blog discloses the bug, includes some proof of concepts (PoC) and code examples. One such PoC is an Android app that allows you to remove locks in one click or set on timer.
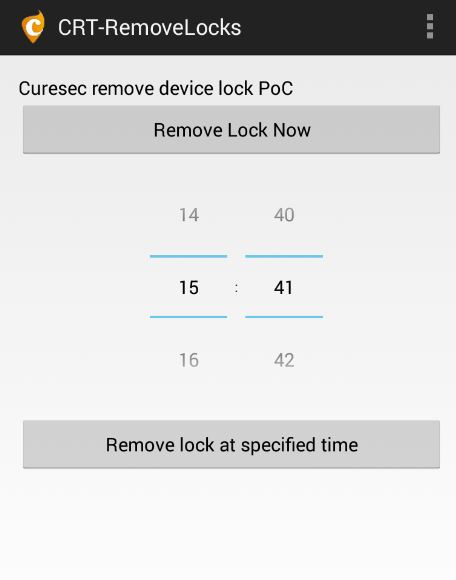
Curesec attempted to contact Google about this bug, but Google became unresponsive to their queries which led Curesec to publicly disclose.
The company said are also checking if vulnerability exists in other version of Android.
This is just another example of the lock screen challenges mobile device and operating system developers are running into. It seems every iteration has a new vulnerability introduced or an existing one uncovered.
This isn’t isolated to Android, iOS has had their share of screen lock issues.
Although there are some ways of bypassing the lock screen on your mobile device, we here at Malwarebytes still encourages using a security lock as a first line of defense.










