It’s quite common for malware to take code from the Windows API and use it for a malicious purpose.
For example, VirtualAlloc is a function from kernel32.dll, and its intended purpose is to allocate new virtual memory within the calling process. However, nearly every piece of malware today will use this function (or another memory allocation function) to create memory used for housing decrypted malicious code.
A less obvious case where seemingly “good” code being misused is in conjunction with malicious callback functions.
Callback functions are used as a parameter for other functions, and are referenced at the signaling of some event. For example, sometimes malware will create timers, and when these timers “time-out”, a Timer callback function (TimerProc) will be executed.
Callback functions can be useful in malware because they can be subtly inserted into legitimate functions. A recent example where this code misuse occurred was analyzing a Zeus Trojan, which had a very long WinMain function.

This code in this function is “bloated” to slow down analysis, hence the large graph. A lot of times when seeing this, the interesting stuff starts to happen at the end of the function, usually where a call or jump occurs to a CPU register. However, with this sample it appears there is a call to EnumDisplayMonitors at the end of WinMain, which specifies callback function as the third parameter.
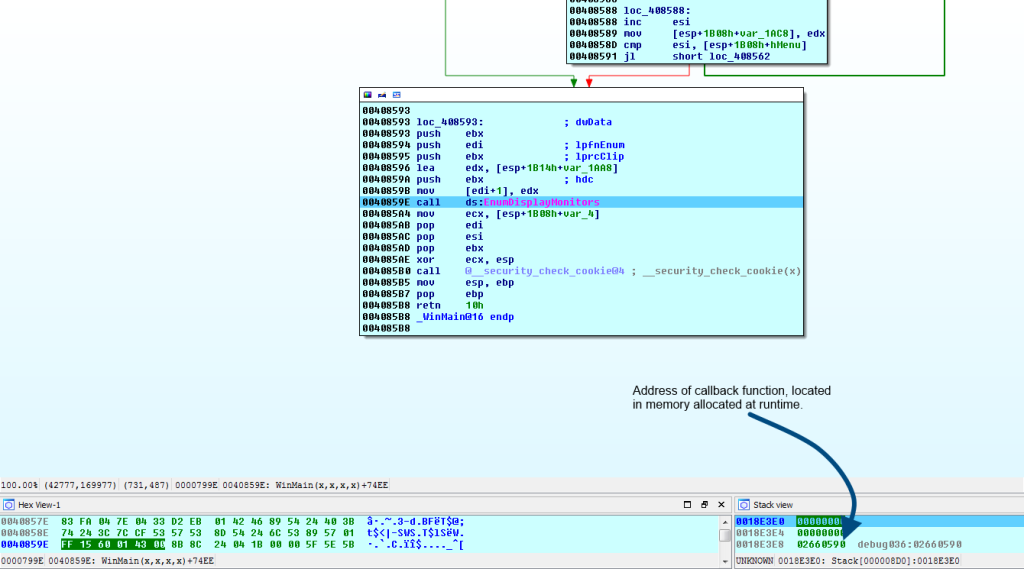
(click to enlarge)
When we start executing that code for the callback function, we can see the real work beginning as the malware starts retrieving handles to required libraries.
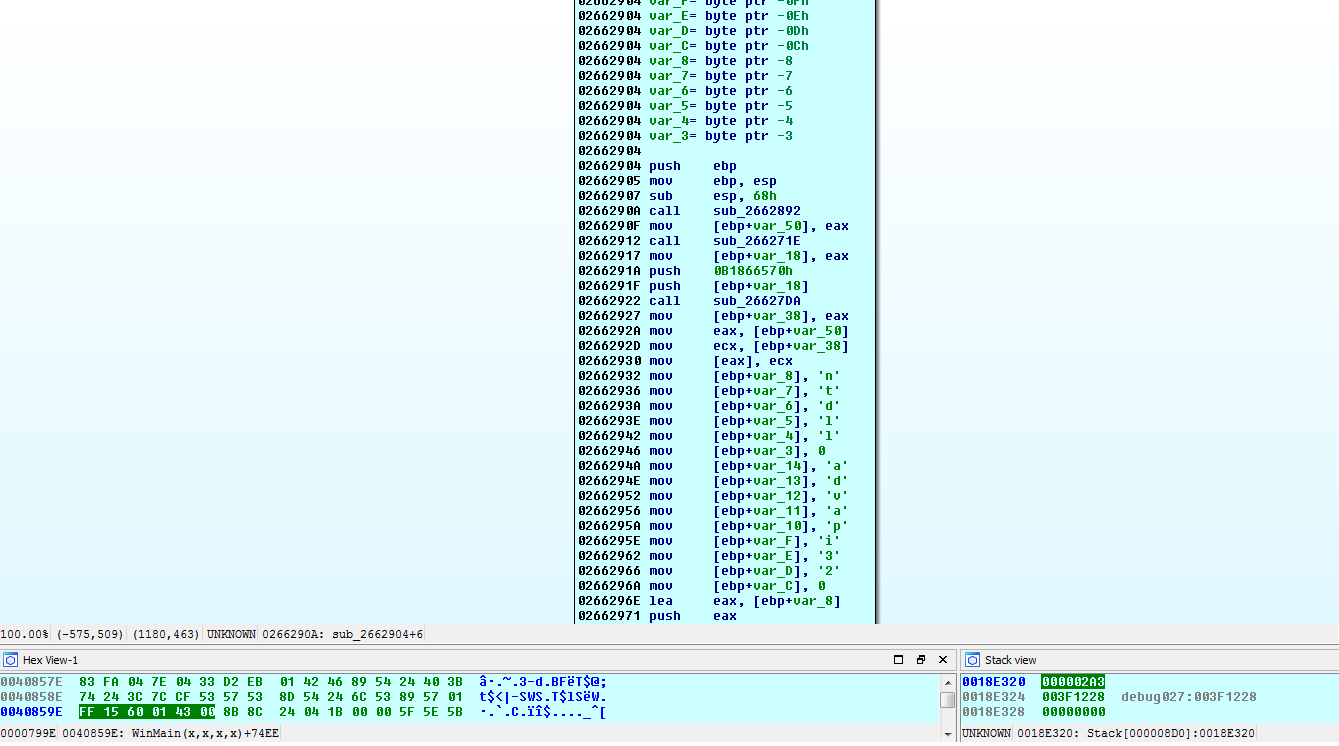
Had I stepped over the call to EnumDisplayMonitors, the callback function would have already executed. From this point, we can continue to analyze the malware and observe its behavior.
For any questions, please post in the comments below.
_________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and malware analysis. Twitter: @joshcannell










