Some folks worry when they get a malicious e-mail, Facebook update or Tweet from some untrusted account with a suspicious link attached to it, I get excited!
Yesterday, I was doing my rounds on Social Media when I came across a tweet directed at me from an account I was unfamiliar with, informing me that the US Government was working on taking down Bitcoin and included a shortened link for more information.
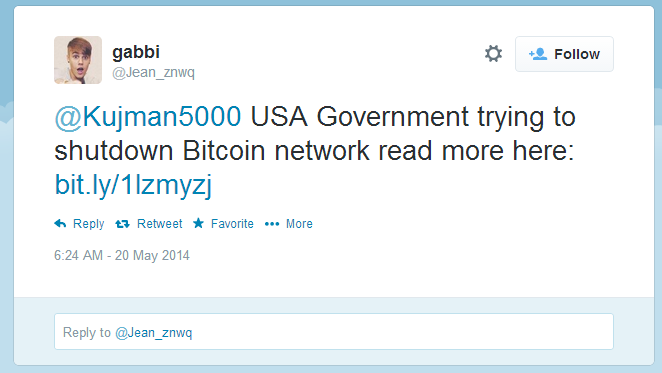
A quick search for the text on Twitter revealed that the spread of this thing was pretty large:
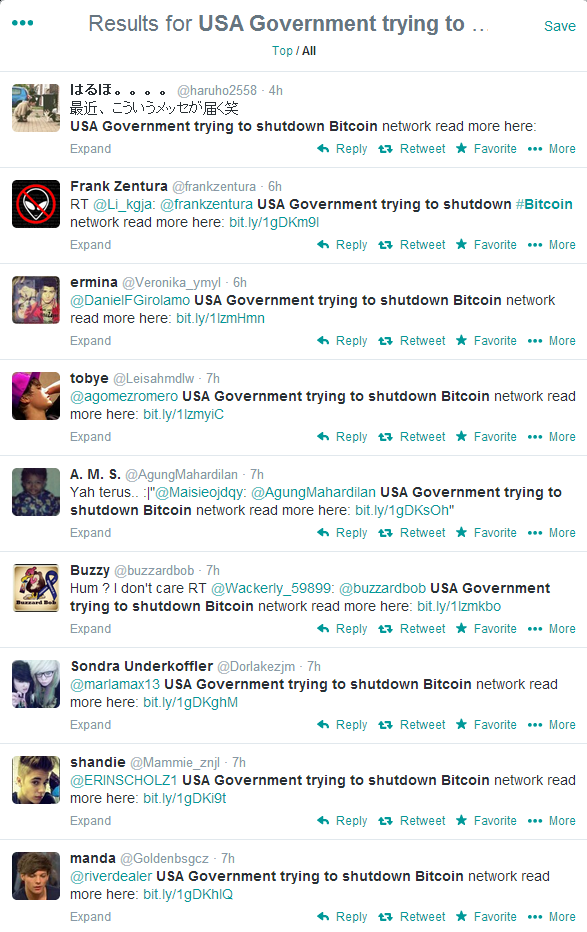
The majority of the accounts pushing these things are clearly fake, using gathered Twitter handles to launch the barrage of malicious spam at the Twitterverse.
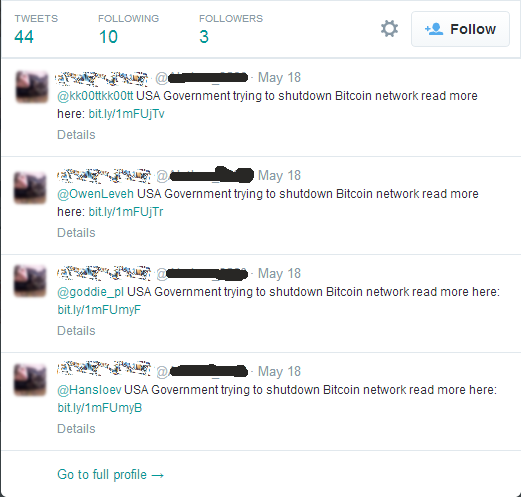
However, the most worry some part is that some legitimate accounts are retweeting the spam without actually reading into what it is, or maybe their account has been compromised. In this instance, one user had over 500 followers and tweeted nothing more than a shortened URL that looked like it might be coming from Linkedin:
So now that we know these links are everywhere, where do they go? Well it turns out that they navigate the user to a “video” for the Wall Street Journal, that is to discuss the USA trying to shut down Bitcoin:
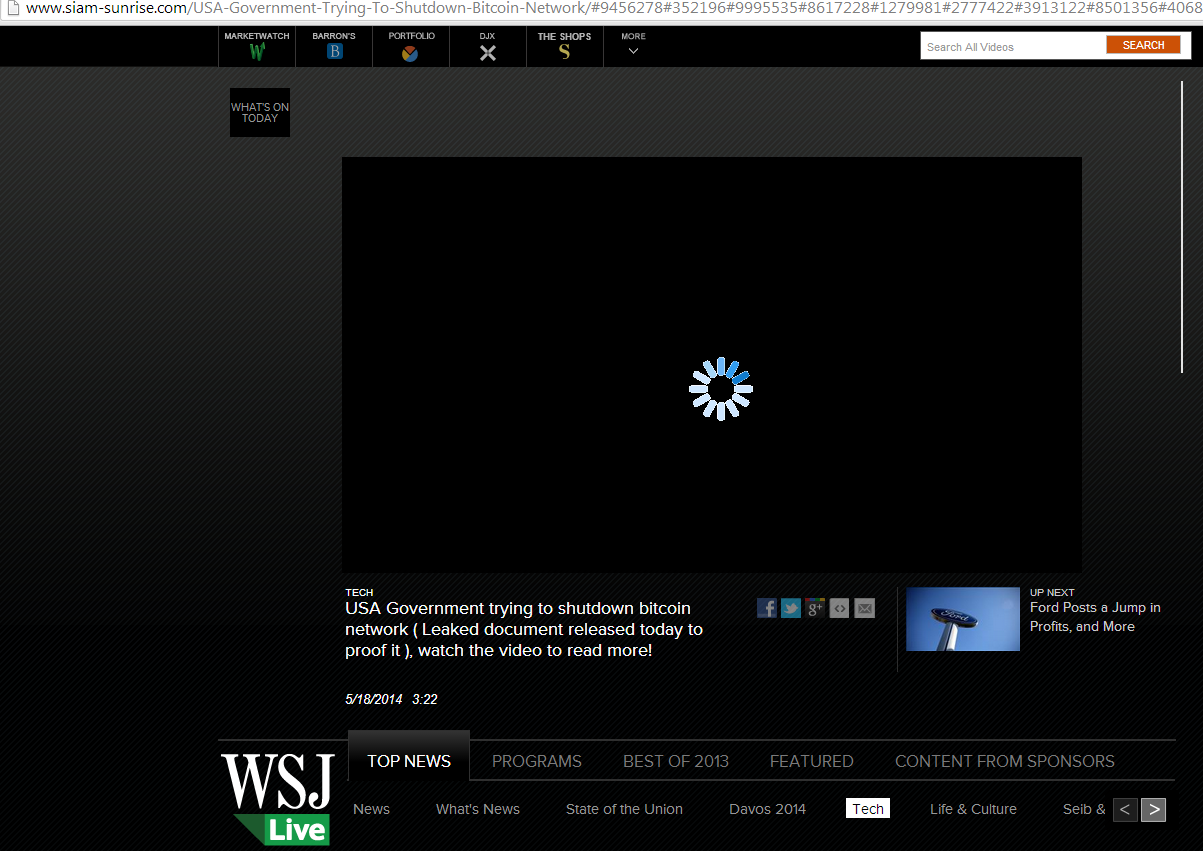
However, quickly checking out the URL reveals that you are actually located at “siam-sunrise.com” a website for a business in Thailand, although actually visiting the source domain leads to nothing more than a black screen. Clearly the site was compromised and we are working on getting it taken down in the mean time.
The video looks like it’s loading but shortly after a pop-up to install Adobe Flash Player will appear:

Clicking the “Install” button will offer the user the option to download the flash player files, when accepting they are provided with a RAR file that includes four files:
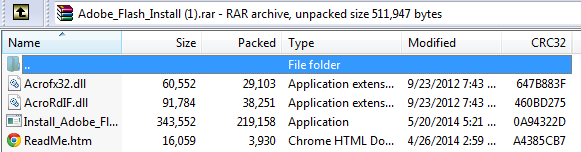
The two DLLs and ReadMe.htm file all appear legitimate, however the Install_Adobe_Flash_Player.exe (third one down) is not so harmless. Upon launching it, the file itself is relocated to the systems Temp folder and made hidden.
I haven’t done too much analysis into this malware, however according to similar files scanned on VirusTotal, it is likely to be a remote access Trojan, possibly related to the Darkcomet RAT.
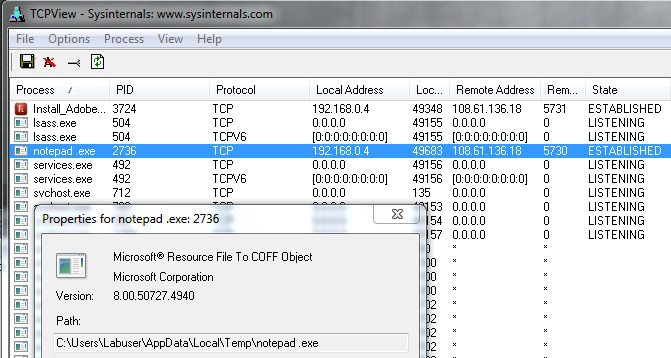
According to my own dynamic analysis, the malware creates an establish connection with a remote server and drops additional malware, such as the “notepad.exe” that is found in the Temp folder and beaconing out to the same remote server as the initial Install file.
The initial analysis definitely supports the RAT theory however further investigation needs to be done in order to be sure and identify which RAT is actually being run.
If you do come across this kind of tweet or something similar, please don’t click the link and report the tweet to Twitter as Spam, they have already been able to shut down numerous accounts because of my poking around so a group effort can really nip this threat in the bud.
If you did click the link and downloaded anything, be sure to run your favorite antivirus and/or Malwarebytes Anti-Malware, we detect this threat as Adware.Agent.
Thanks for reading and safe surfing!











