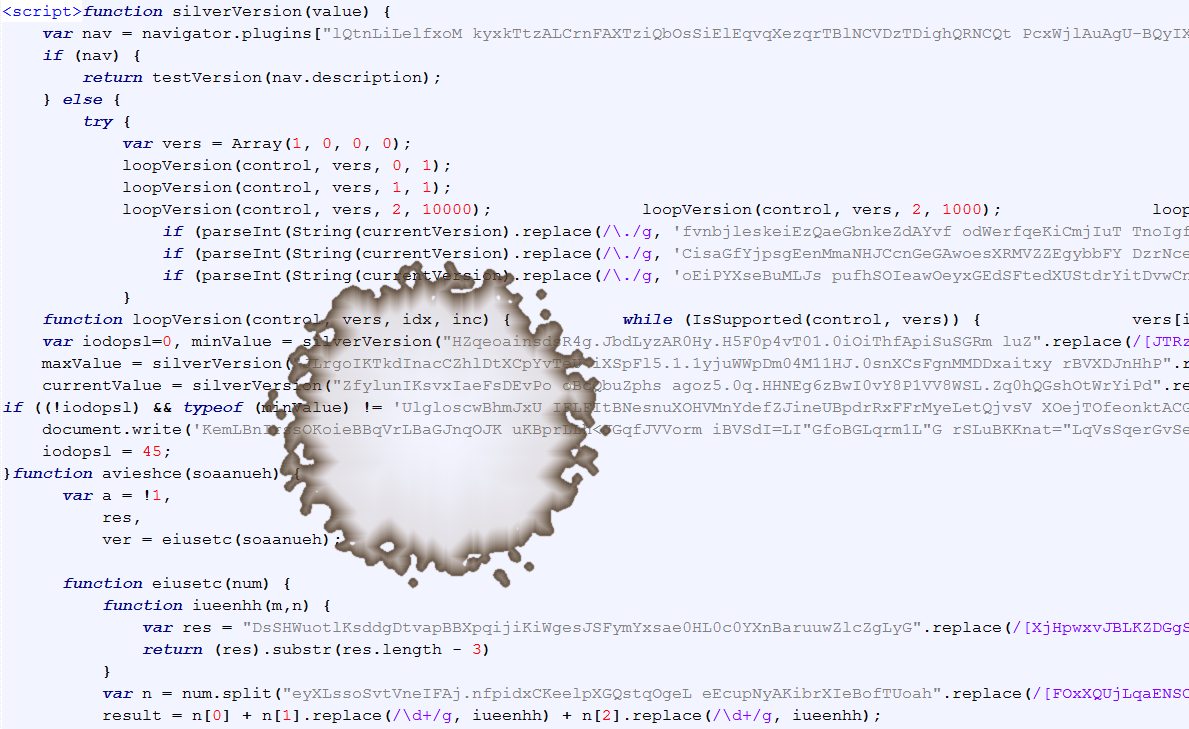
Every now and again we come across new URL patterns when investigating traffic captures. In some cases, they are variations of existing redirectors or exploit kits which play the cat-and-mouse game with security researchers, other times they are the indication of a new threat.
But what makes something ‘new’, and how can you be sure that it is indeed something truly novel? Unless you have tracked the drive-by / exploit kit scene from day one or been able to map it out down to the tiniest details, this is not something easy.
There are a few reasons for this. For one, the landscape is vast and ever-changing, bringing an overwhelming amount of information that needs to be dissected and categorized.
Secondly, much of what we see is what the bad guys are showing us, which essentially means client-side traffic.
What about the back-end structure, the actual actors in this ecosystem?
Thankfully we do get the chance to look at it thanks to the relentless work of dedicated researchers such as @kafeine. But sometimes, there are still some things that are left unclear or may confuse some of us (including the author of this article).
When a security researcher stumbles upon something he does not recognize, he often calls it ‘unknown’ for the lack of information needed to give it a proper name.
This post will dig into such a case that has been floating around for some time now and may finally get a chance to have enough exposure to be categorized.
The ‘Unknown’ Exploit Kit
A couple of weeks ago, we observed a new traffic pattern (new to us) that first caught our attention for a couple of reasons:
- The payload’s size did not match that of any URL from the capture
- The URL patterns were new
Before diving into the exploit kit itself, let’s first take a look at how we got there.
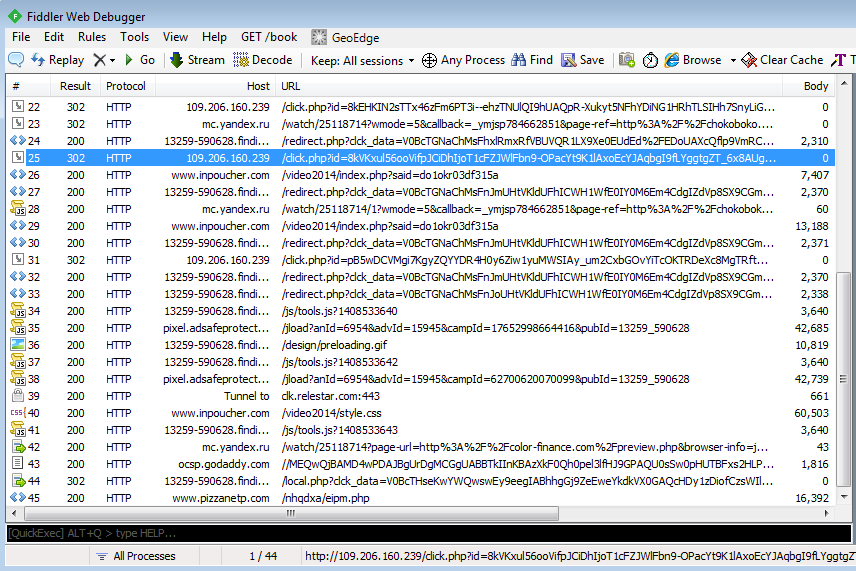
Redirection chain
Raw traffic:
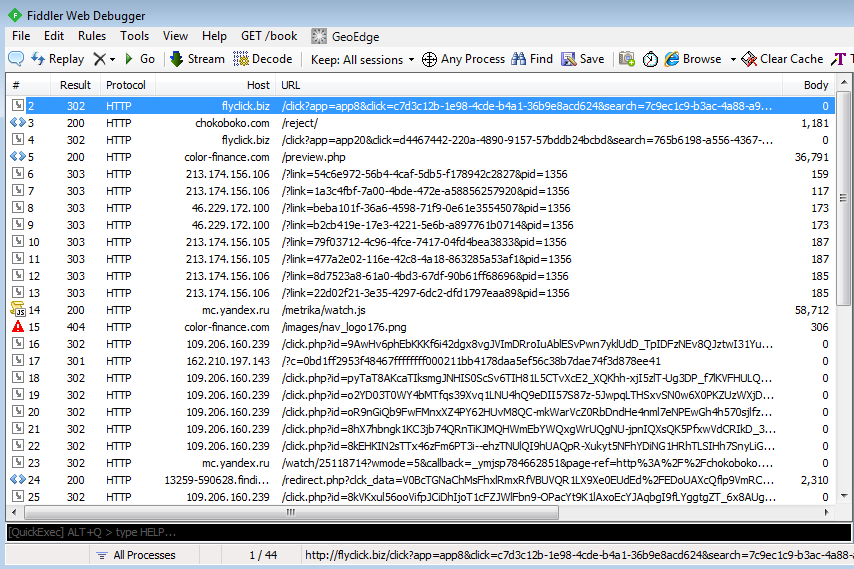
Traffic highlights:
hxxp://flyclick.biz/click?app=app8&click=c7d3c12b-1e98-4cde-b4a1-36b9e8acd624&search=7c9ec1c9-b3ac-4a88-a99f-c95bb7c07d02&feed=18418
HTTP/1.1 302 Found Server: nginx Date: Wed, 20 Aug 2014 11:19:58 GMT Connection: keep-alive Location: http://chokoboko.com/reject/ Content-Length: 0
hxxp://chokoboko.com/reject/
//document.write("http://flyclick.biz/click?app=app20&click=d4467442-220a-4890-9157-57bddb24bcbd&search=765b6198-a556-4367-9633-8adb52afcf8e&feed=18398");hxxp://flyclick.biz/click?app=app20&click=d4467442-220a-4890-9157-57bddb24bcbd&search=765b6198-a556-4367-9633-8adb52afcf8e&feed=18398
HTTP/1.1 302 Found Server: nginx Date: Wed, 20 Aug 2014 11:20:01 GMT Connection: keep-alive Location: http://color-finance.com/preview.php Content-Length: 0
hxxp://color-finance.com/preview.php