We recently encountered certain phish pages targeting the United Services Automobile Association (USAA), a Fortune 500 financial company that offers banking, investing, and insurance to US Military soldiers and their families.
Here is what the fake page looks like:
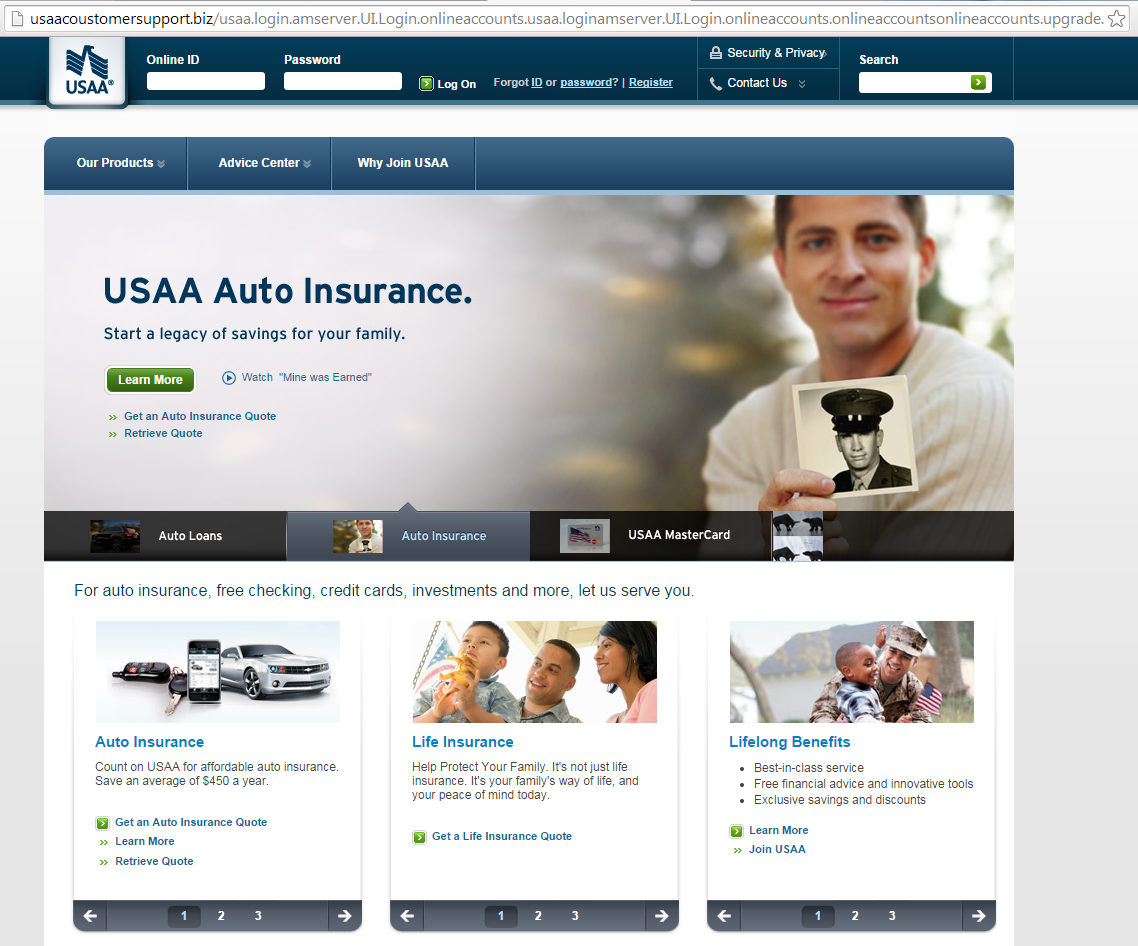
click to enlarge
It’s highly likely that the URL came from a phishing email; unfortunately, we were not able to get our hands on a sample of it.
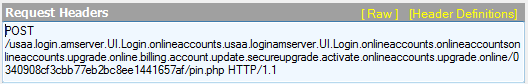
Harvested data from whatever one puts under “Online ID” and “Password” are posted back to pin.php, according to the Fiddler finding below:
Users are then led to this page:
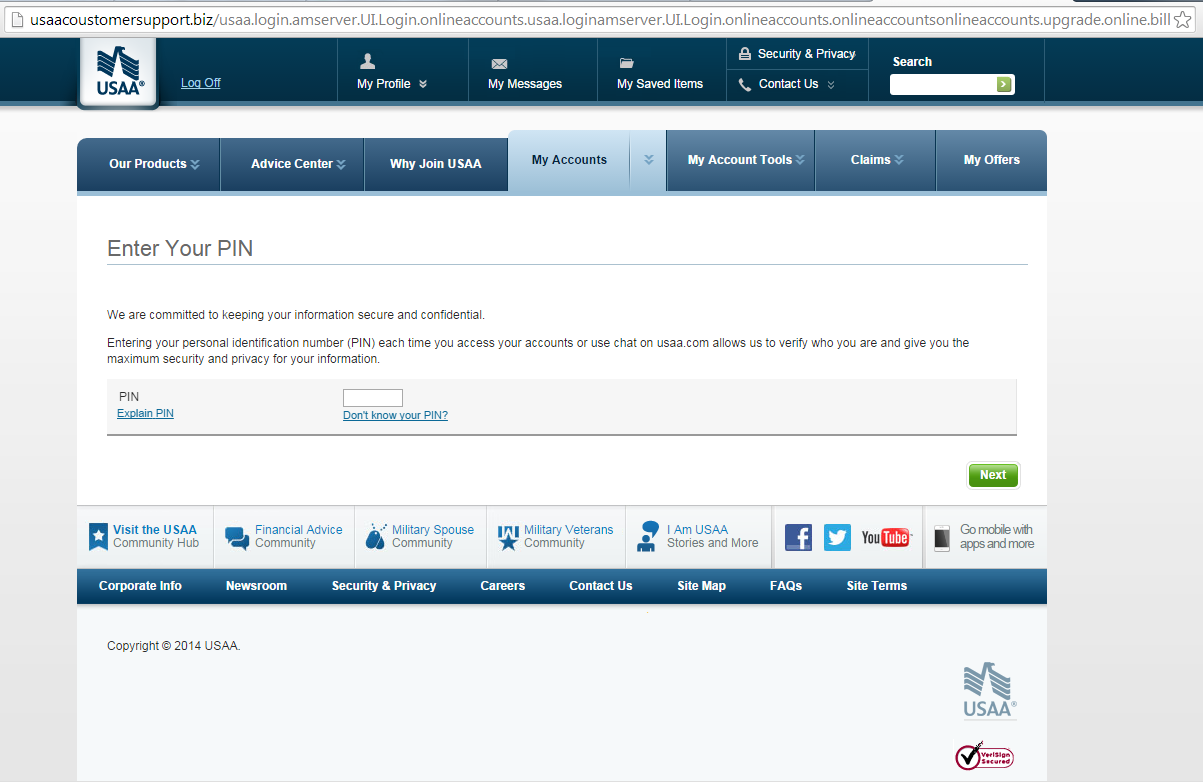
click to enlarge
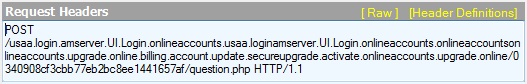
The PIN provided on this page gets posted back to question.php.
Clicking the “Next” button opens this page wherein users can supply their secret questions and their respective answers:
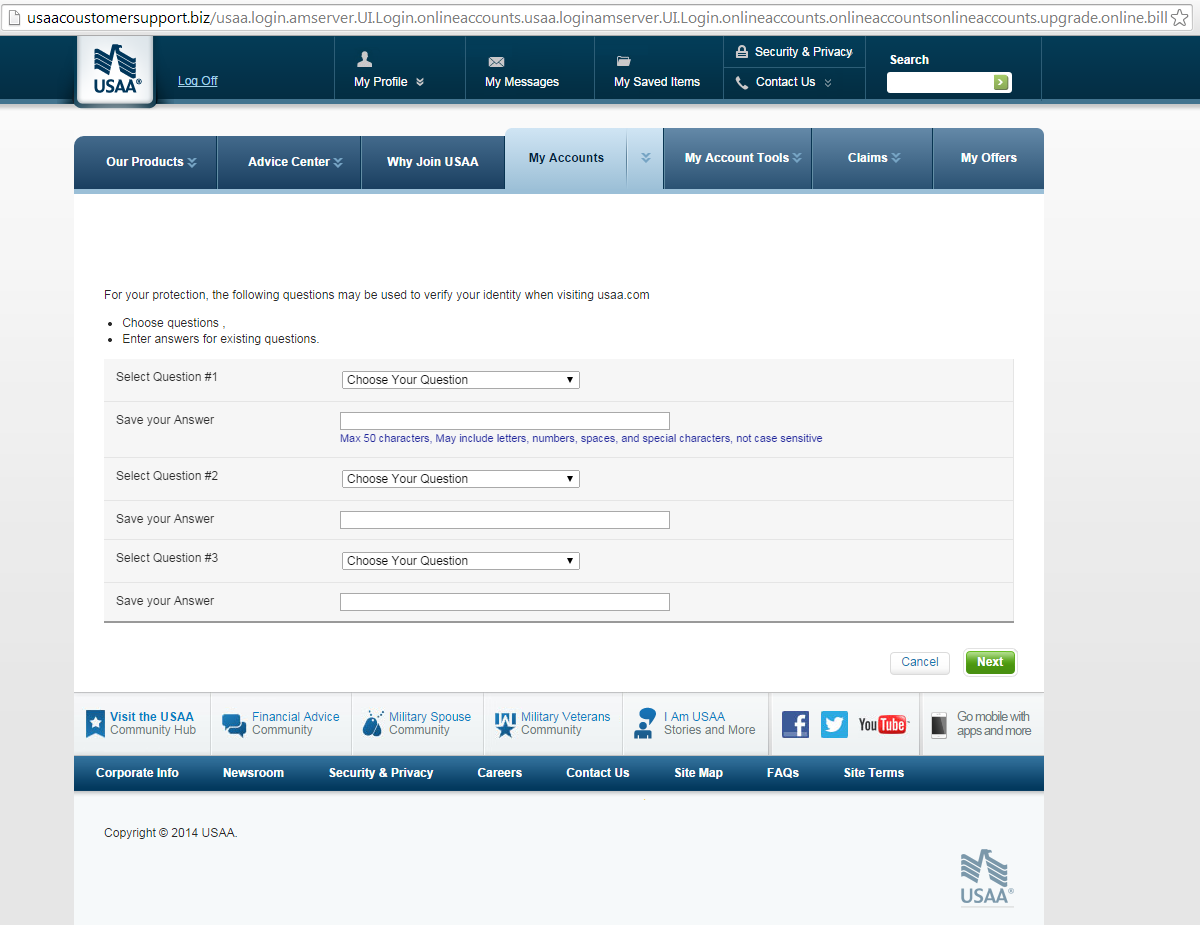
click to enlarge
Data are posted to contact.php.
Clicking “Next” opens the last page, which asks for more information that needs “updating”, including full name and date of birth:
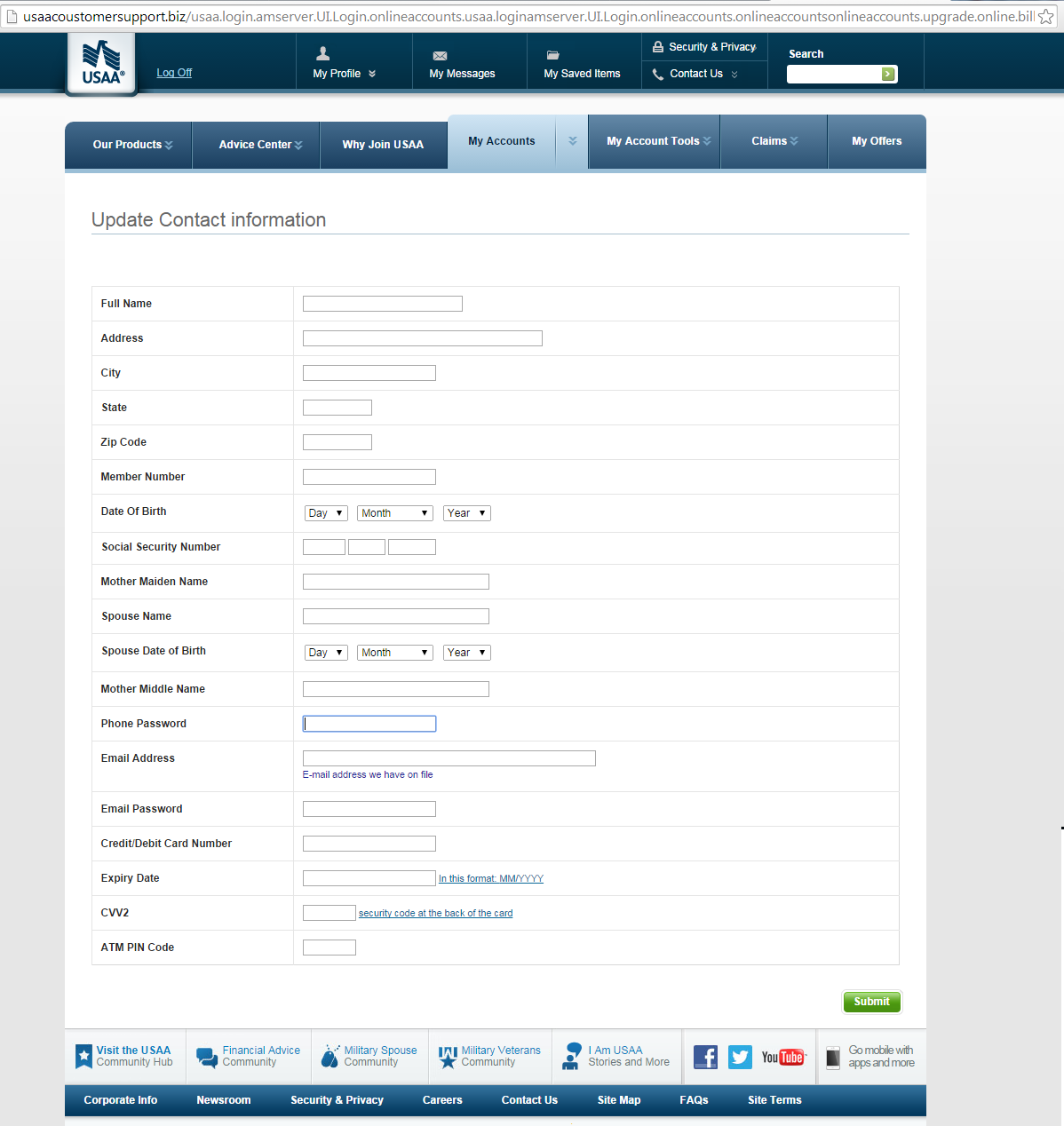
click to enlarge
Details entered here are then posted back to action.php.
Users are then shown the door by redirecting them to the legitimate USAA page one sees when they log out (screenshot below).
click to enlarge
Thankfully, Google Chrome already blocks the aforementioned .biz domain.
With a little more digging, we found that the email associated with the domain usaacoustomersupport(dot)biz is also tied to the following domains, which we’ve already confirmed are inaccessible:
- usaafdscewvrevre(dot)net
- usaafewcrvrvrvr(dot)net
- usaasasadsadsad(dot)net
We’ve also observed the following URL also tied to the same email address:
click to enlarge
We’ve also seen other USAA phish pages in circulation such as this example on Phishtank, which appears to have been hosted on a hacked website and has since been taken down (Note: This is unrelated to the pages covered in this blog entry).
USAA phishing scams are seen in the wild, but they’re not particularly common. Our friend, Kimberly, at StopMalvertising wrote a piece similar to this phishing campaign she found in February of this year. Several months later, Oklahoma-based news outlet, KJRH, has reported a similar occurrence.
In case you receive emails claiming to be from USAA, please note that they do not send out emails to their clients, or to anyone for that matter, asking for their information.
Here is a short list of tips to help you steer clear of USAA phishing attempts:
- Remain aware of phishing cases involving USAA. It’s also good to have their contact details handy in the event of fraud or account compromise.
- The legitimate USAA website, www.usaa.com, is a verified domain. As such, look for the green box beside its URL on the browser address bar. This site also uses SSL encryption, which means that it uses the https protocol, making it safe to access even over public networks.
- Ensure that the anti-phishing feature of your Internet browser is enabled. Do this for your antivirus software as well.
Jovi Umawing (Thanks to Chris for the assist)










