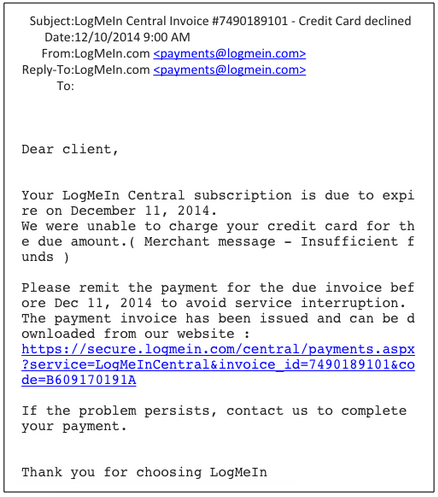
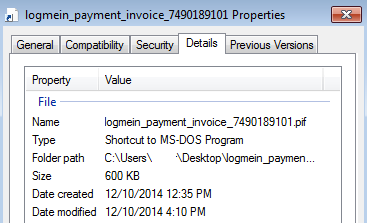
Today we received a phishing email pretending to come from LogMeIn, the popular remote administration tool. It uses a classic scare tactic “We were unable to charge your credit card for the due amount.( Merchant message – Insufficient funds )” to trick the user into opening up a fake invoice:
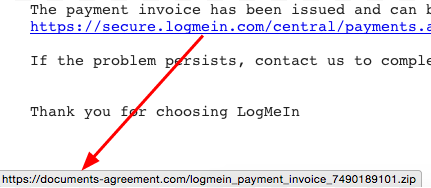
Of course the URL pasted in the message is using a simple trick to link to something else. You can see it by simply moving your mouse over the URL, to see its actual destination:
What struck our interest here was the fact that this link was https based. It was indeed a secure connection (details provided by SSleuth Firefox extension; thanks @JP):
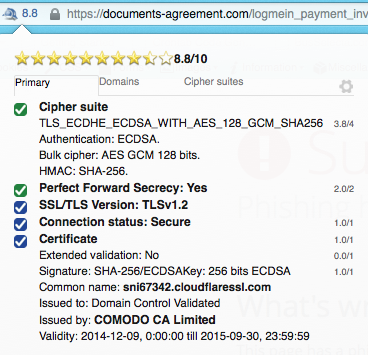
with a valid certificate:
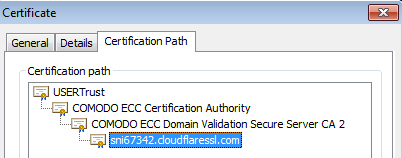
The original certificate was issued to sni67342.cloudflaressl.com (CloudFlare).
SNI stands for Server Name Indication (hostname information) which according to Wikipedia “allows a server to present multiple certificates on the same IP address and TCP port number and hence allows multiple secure (HTTPS) websites (or any other Service over TLS) to be served off the same IP address without requiring all those sites to use the same certificate.“
On September 29, CloudFlare, a CDN and DNS provider amongst other things, announced Universal SSL, a feature available to all its paid and free customers.
It is not the first time cyber-criminals are abusing CloudFlare, and this case is not entirely surprising. By giving a false sense of security (the HTTPS padlock), users are more inclined to follow through and download the malicious file.
Malwarebytes Anti-Malware detects this file as Trojan.Crypt.NKN.
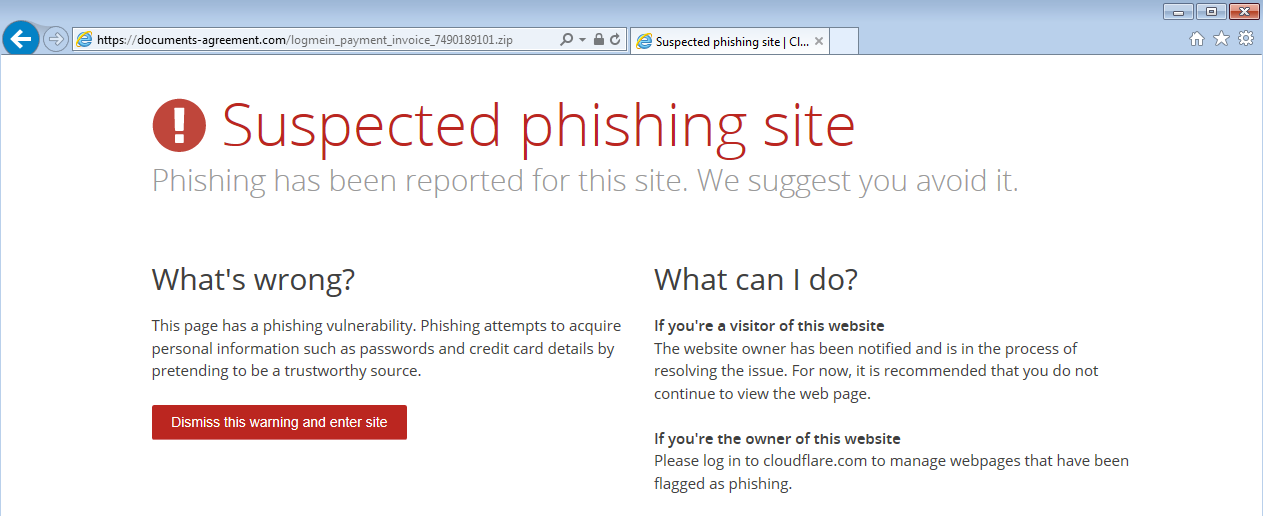
Thankfully, CloudFlare is issuing a warning that the URL is a ‘Suspected phishing site’:
In some regard SSL certifications may become like digitally signed files, where while they do add a level of trust one should still exercise caution and not blindly assume everything is fine.
It might be difficult to keep up with each and every new site that wants to abuse the system (cat-and-mouse game), although in this case the domain name, registrant and registrar details are quite suspicious:
Domain name: documents-agreement.com Registry Domain ID: 1869159429_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.bizcn.com Registrar URL: http://www.bizcn.com Updated Date: 2014-07-31T17:17:52Z Creation Date: 2014-07-31T17:17:53Z Registrar Registration Expiration Date: 2015-07-31T17:17:53Z Registrar: Bizcn.com,Inc. Registrar IANA ID: 471 Registrar Abuse Contact Email: abuse@bizcn.com Registrar Abuse Contact Phone: +86.5922577888 Reseller: Cnobin Technology HK Limited Domain Status: clientDeleteProhibited Domain Status: clientTransferProhibited Registrant Name: Wuxi Yilian LLC Registrant Organization: Wuxi Yilian LLC Registrant Street: No.1001 Anling Road Registrant City: Xiamen Registrant State/Province: Fujian Registrant Postal Code: 361008 Registrant Country: cnBut these are the kind of things that may be obvious to a security researcher but not necessarily to a machine.
We can certainly expect cyber criminals to start using SSL more and more given that it is freely available and not extremely difficult to put in place.
Another standard known as Extended Validation Certificate SSL (EV SSL) requires additional validation than plain SSL, but again, this does not make things simple for the end user. If regular SSL is deemed weak, then we have a bit of a problem.
If you are interested in reading more about SSL, you should check out a recent blog post by one of our security analysts about SSL personas.
Note: We have reported this URL to CloudFlare and hope they can revoke the SSL certificate and shutdown the site.










