These days it is getting harder and harder to download a program from its official source, in its original format, without additional pieces of software bundled to it.
Companies specializing in so-called ‘download assistants’ or ‘download managers’ claim that they:
- Provide a value added service to users by suggesting additional programs tailored to the users’ needs.
- Offer a way for software manufacturers to monetize their free applications.
Let’s have a look for ourselves by checking an installer for the Adobe Flash Player. The details are as follows:
Name: adobe_flash_setup.exe Size: 809.0 KB MD5: d549def7dd9006954839a187304e3835 imphash: 884310b1928934402ea6fec1dbd3cf5e
Out of the box
The first thing we noticed was that the program behaves differently whether it is launched on a real physical machine or a Virtual Machine, as described in the diagram below:
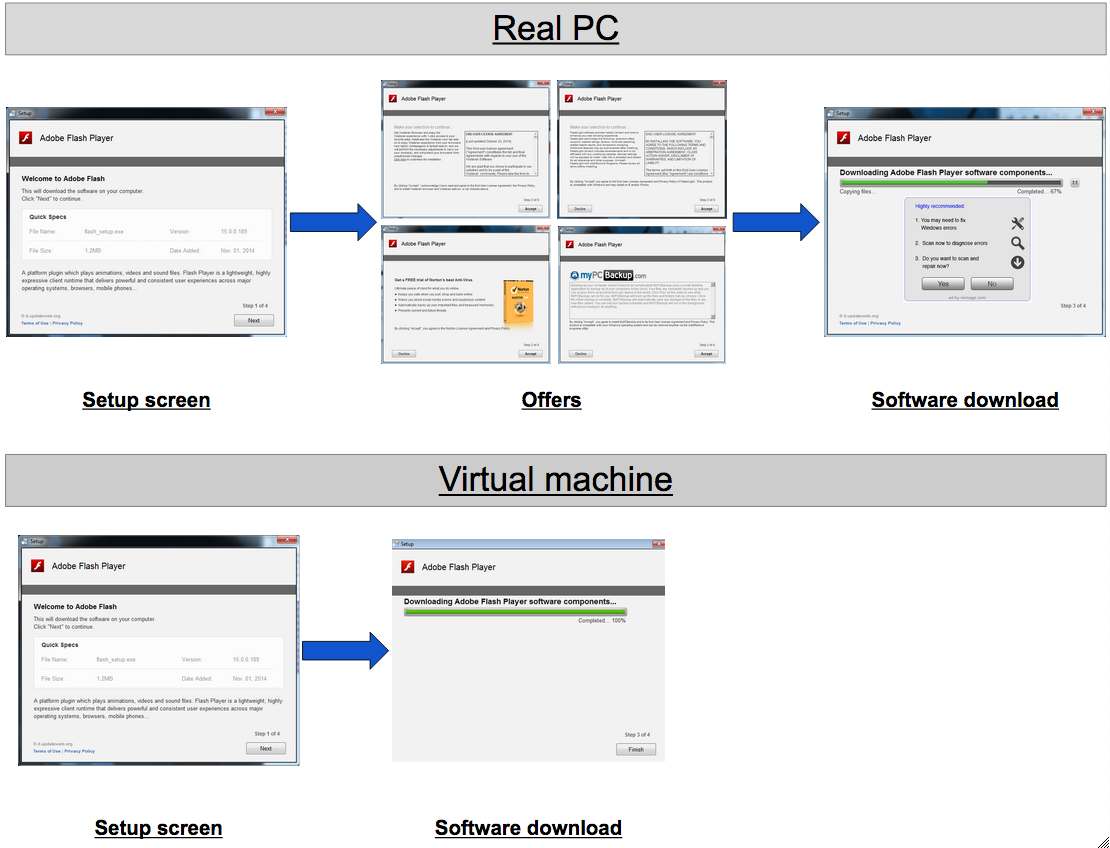
In a VM such as VirtualBox, the installer skips all the bundled offers and goes straight for the Flash Player.
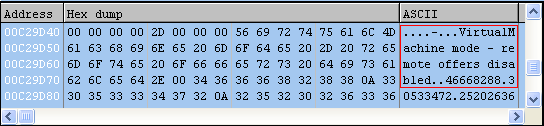
By reverse engineering the installer, we can confirm the detection of Virtual Machines: “VirtualMachine mode – remote offers disabled”
There might be a few reasons for this:
- To avoid unnecessary impressions and installs on ‘fake’ systems that would skew metrics.
- To appear as a ‘clean’ installer when installed on automated sandboxes or by hand from security researchers.
Anti-vm behavior does not necessarily mean that the application is malicious, but it is something that many malware authors use.
Time stamp
The program was compiled with a date of June 19th 1992, long before PUPs even existed:
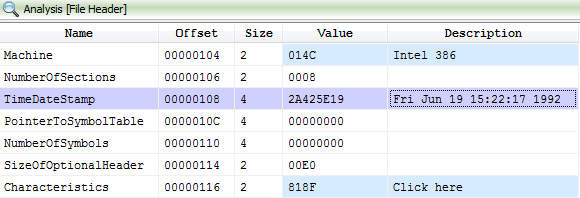
By using an older time stamp, the program looks less suspicious and it is a technique that we observe with certain malware samples.
[Edit] @Hexacorn commented that this is actually a bug with the Delphi programming language.
Digital footprint
The file was digitally signed by Fried Cookie Ltd. A digital certificate is a trust of authenticity but can be abused and certainly can be used to ‘boost’ a program’s credibility.
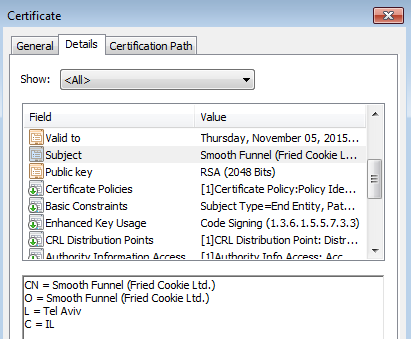
The certificate details show that said company is located in Tel Aviv, Israel and a VirusTotal scan hints at a connection with InstallCore, a “digital content delivery platform”.
The link between the two companies can be established from this blog statement:
In early 2013, Fried Cookie proudly announced a formal partnership with installCore. We are now both under the ironSource umbrella of products.
The offers
The first offer cannot be opted out from, you must accept it in order to keep going:
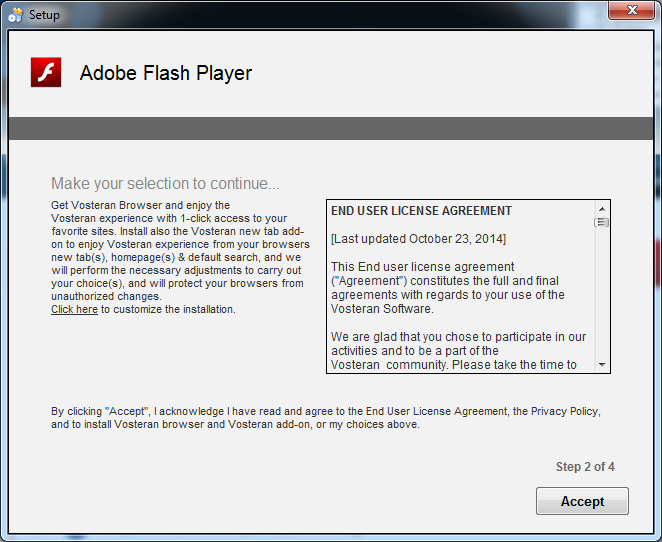
This mandatory offer installs the Vosteran Browser, a Chromium-based browser created by Fried Cookie Ltd.
Most searches to download the Vosteran Browser on its own return results for how to remove it instead:
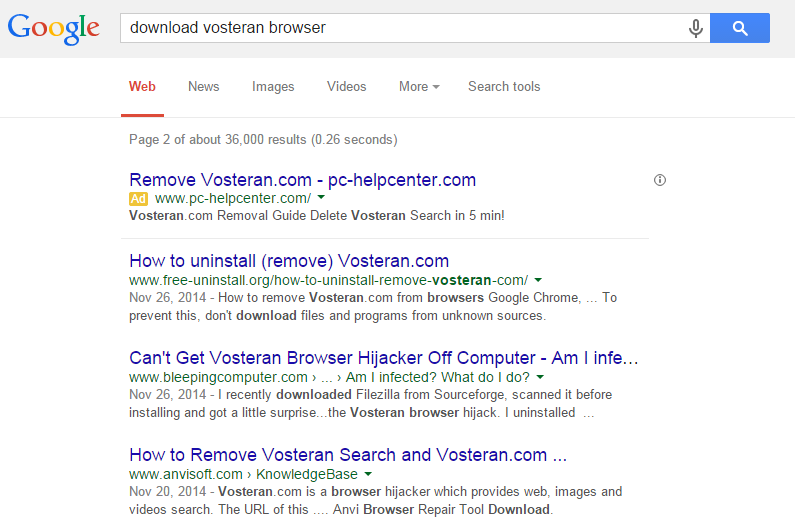
Finally, Vosteran’s privacy policy states that:
We may also use a third party tracking service that uses cookies (analytics) to track aggregate non-Personal Identifiable Information regarding our Software and/or Services. Please note that We have no control over third parties privacy policies.
This essentially means that Vosteran Search cannot be held liable for abuses committed by third parties.
There are also various other offers bundled in this installer, courtesy of “distributer” called Entarion Ltd., with an “address” conveniently located in Cyprus, well-known as a safe haven for offshore companies.
d.updateweb.org softwareportals@gmail.com Stratigou Spyrou Stathopoulou, 14B, 3066, Limassol, Cyprus
Note that the domain is using Privacy Protect to hide the registrant’s details. However, a search on the Gmail address shows that there is another domain seemingly belonging to an individual in St Petersburg, Russia.
It doesn’t take too long to find several reports of unwanted pop-ups aggressively pushing bogus registry cleaners many of which are funneled through securedshopgate.com a well hidden portal with an SSL certificate tied to an address in Cyprus, once again:
Installing the Flash Player from this installer is not an easy task due to the large number of promoted software:
[youtube=http://youtu.be/yeBYDG2EXjI&rel=0]
It could be argued that this particular example is not the norm and that most download managers do explicitly let the user choose or decline additional pieces of software that have been vetted as legitimate.
However, opposite examples do exist as well and do cause a lot of headaches and large amounts of money spent on programs whose effectiveness can be questioned.
To quickly remove any trace from these Potentially Unwanted Programs (PUPs), you can download and run Malwarebytes Anti-Malware:
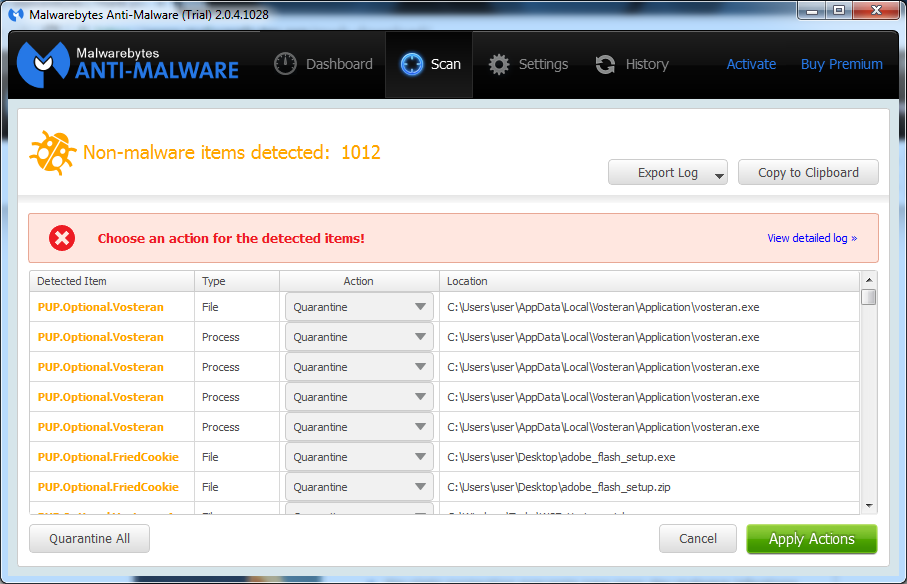
Malwarebytes’ criteria for listing a program as a PUP can be viewed here. The lists is pretty thorough and will most likely continue to evolve as PUP makers diversify their operations.
Consumers should be able to make educated choices rather than being mislead down a path that they didn’t intend to take.
Unfortunately, because software bundles are such an attractive business model from a financial standpoint, the line between legitimate and fraudulent gets crossed too many times.
Special thanks to Adrian Gill, Joshua Cannell and JP Taggart for additional research assistance.