Playing games online with your friends can lead to frustration where teamwork and coordination are concerned – if you’re not paired off with the 12-year-old holding his controller upside-down, you’re likely howling into the void due to your built-in comms tools (or even ones provided by gaming platforms) breaking at inopportune moments.
As a result, there are plenty of alternate services available for gamers to try out and Razer Comms is one such voice chat service for PC Gamers. They offer up two downloads on their homepage, for both Windows and mobile devices. I don’t believe we’ve seen gaming voice comms services used as bait for malware attacks before, so the following riff on the Steam Community URL came as a bit of a surprise once we saw the content:
steamccommynity(dot)com
Instead of the usual fake Steam community pages touting fake in-game items with links to phishing pages, we saw a rip of the Razer Comms website instead:

The site functions in a similar fashion to the real thing, along with linking to the (legit) mobile app on the Google Play store. Clicking the Windows download button, however, will serve potential victims a bogus file instead of the actual Razer Comms executable:
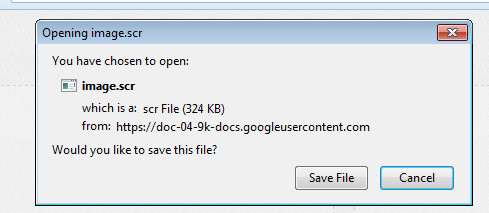
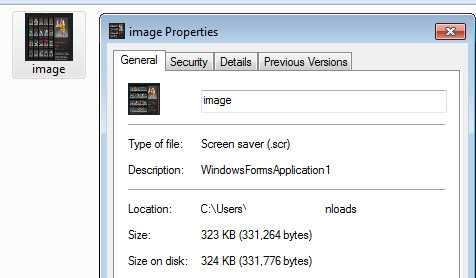
The file is an .scr which should be familiar to readers of this blog – they’re very common in fake in-game trading scams [1], [2]. Users of Malwarebytes Anti-Malware will find we detect this file as Spyware.OnlineGames, though the .scr doesn’t appear to be firing on all cylinders at time of writing with errors galore should you try and run it.
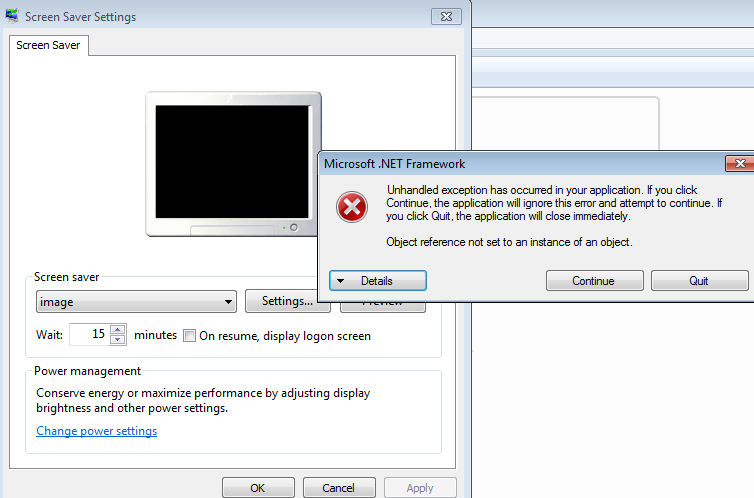
The file is rather erratic, occasionally popping a screensaver box after executing – but always firing a .NET framework error message, which needs to be on the system for the .scr to run in the first place. We didn’t see any data being stolen during testing – most likely due to the errors – but that doesn’t mean a more reliable file won’t replace it at some point down the line.
In the code of the .scr file, we saw a couple of pieces of data worth noting. First up, some bits and pieces of code which can also be found in a similar file associated with password theft on VirusTotal (we detect that one too, as – you guessed it – Spyware.OnlineGames). Secondly, a reference to a URL which leads to some interesting places – a login page for something called “Steam Fishing [sic] Tools”.
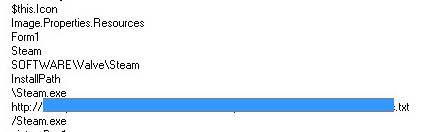
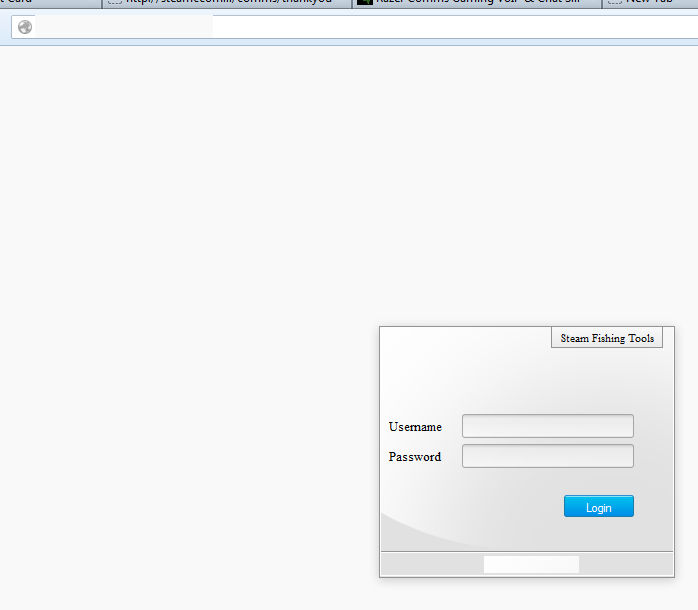
Other pages on their website were non functional, but one link took us to a Russian gaming portal with multiple threads on hacking related topics. Here’s a small shot of a thread advertising the services of the people behind the above setup, with an image file explaining the services instead of the more usual approach (writing stuff):

The information is text on a screenshot, so you can’t just run it through google translate because we’re effectively looking at someone hitting PrtSc at some text. What you can do, is use the handwriting feature in Google translate and draw the individual letters instead – Google Translate takes your “A for Effort, D for Accuracy” scribbles and bashes them into translated words. Please note that this is an incredibly long-winded way to go about it, even if you do get to watch this…
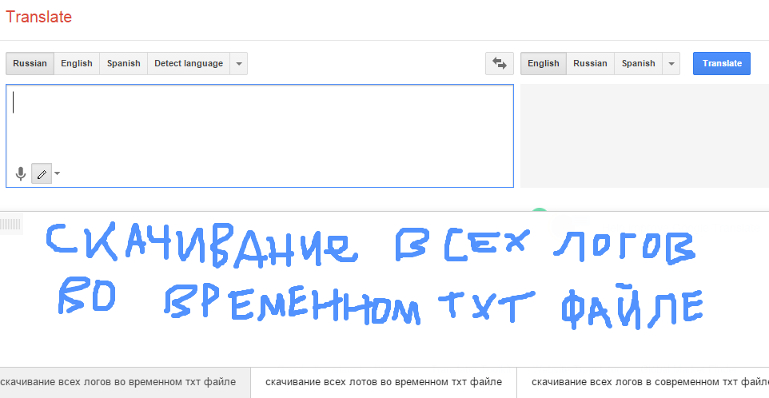
…become this:
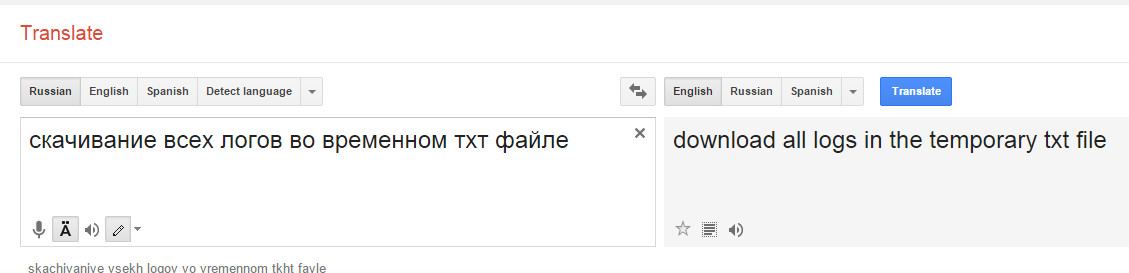
In addition to “downloading all logs in the temp txt file”, the rest of the advertisement for their service mentions “issuing additional accounts for the spammer”, “fake geolocation”, “selection of languages”, “ban protection” in relation to using Google Chrome and the potential for “Kriptovat virus”.
They want just over 1,000 WMR per week for their services, or a slightly cheaper fee of 3,500 for a month. WMR appears to be a form of secure online payment, though I’m not familiar with it at all and hesitate to give an equivalent total to the kind of real world money you’d hide under the bed. At any rate, your online gaming accounts have never tasted so sweet to those with an eye for making money in ways they probably shouldn’t be.
The most attractive way in for scammers where Steam accounts are concerned is trading. You should give the official Steam trading policy a read, and check out this huge list of trading tips to help you avoid being caught out by scammers.
In most cases that we see, the name of the game is luring the victim outside of the trade system window. If you’re being sent links to “previews” of items in Steam chat by strangers who started messaging you ten minutes ago? You may be on your way to a bad day. Whether we’re dealing with links to executables, so-called pictures of in-game items which turn out to be .scr files, login pages asking you for credentials and / or uploads of your SSFN, you should do your very best to avoid them all.
Christopher Boyd (Thanks to Steven for additional information)