In January, The Guardian published a piece on Facebook‘s noteworthy success with its user-generated videos along with their growing shareability and viewability within the network. The numbers were actually quite impressive. It was only a matter of time for those with ill intent to notice.
Indeed, as more and more users are creating, sharing, and viewing videos on Facebook now more than ever, we can also expect online criminals to jump in on the bandwagon and attempt to get some of the attention, too.
Dear Reader, if you see an interesting post on your feed carrying a link to a supposed video that, once visited looks similar to the screenshot below, know that you’re no longer on Facebook but on an imitation page located at http://storage[dot]googleapis[dot]com/yvideos/video2[dot]html:
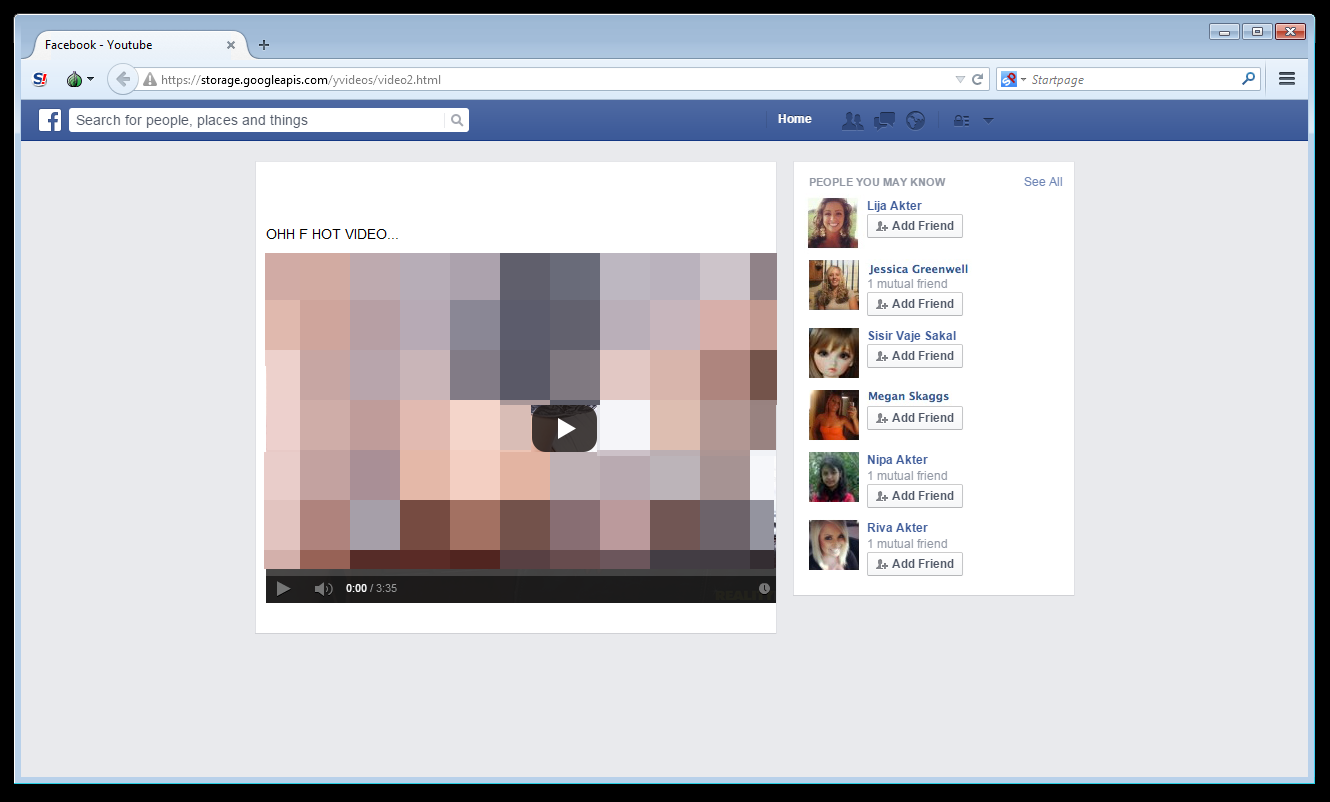
click to enlarge
The individual or group behind this scam has abused Google’s free online file storage service to house the HTML page that has mimicked Facebook’s interface. This method has been a long-time practice of phishers who use free such services like Dropbox and Google Drive in their campaigns.
Once you hit the Play button, an error message appears on top, saying that Flash Player is required to view the video. A file named youtube.scr is downloaded instead.
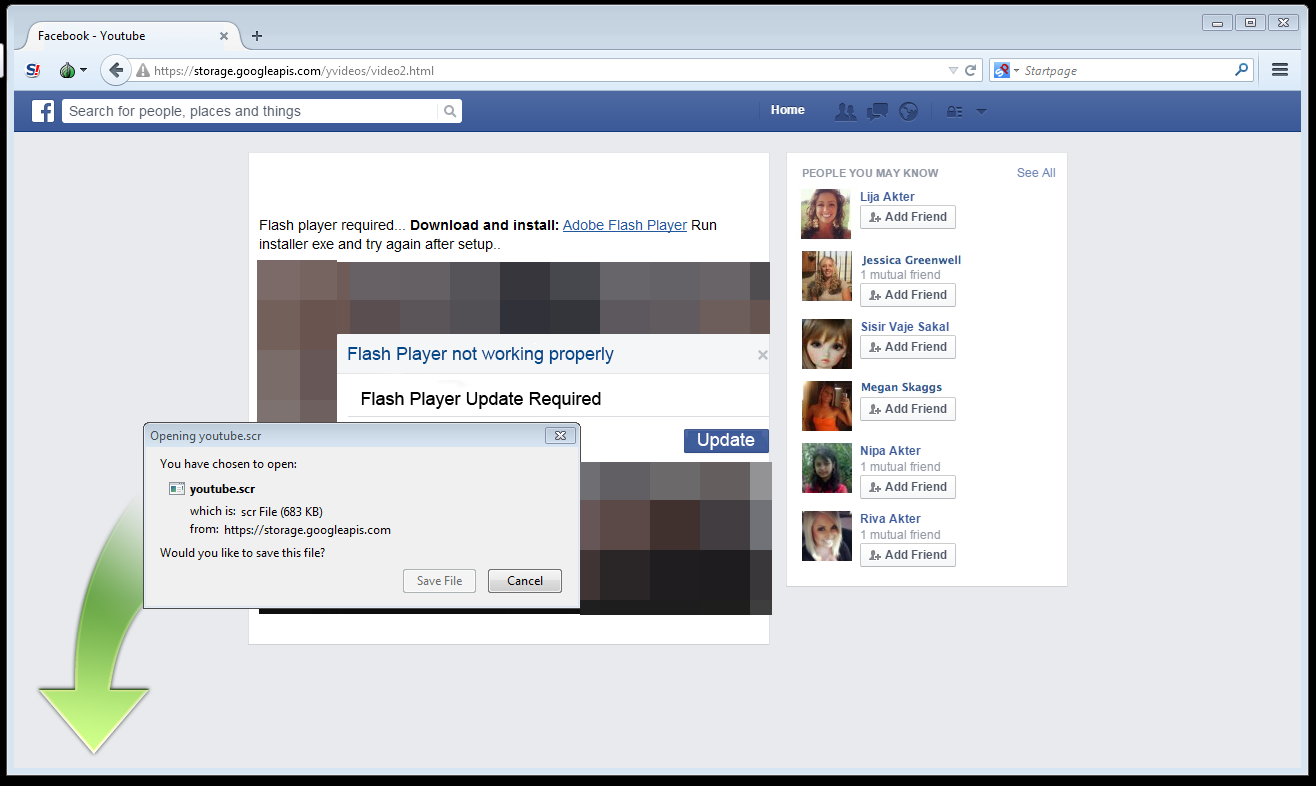
click to enlarge
Flash player required... Download and Install: Adobe Flash Player Run installer exe and try again after setup..

This file lacks the sophistication to detect virtual environments, so one can easily test it against any free, online sandbox—in this case, I used this one from Payload Security—to see how badly it behaves on a system once executed.
Malwarebytes Anti-Malware (MBAM) detects youtube.scr as Trojan.Ransom.AHK.
Jovi Umawing










