It is a well-known fact that malware authors try really hard to avoid security researchers and their analysis tools. For instance, many binaries have anti VM features and will behave differently if they detect that they are running in a non genuine environment.
Exploit kits also perform similar tricks despite some limitations since they are browser based. Kafeine documented VM and network tools checks in a post showing how CVE-2013-7331, a vulnerability in Internet Explorer allows file system enumeration. According to Kafeine:
The Microsoft.XMLDOM ActiveX control in Microsoft Windows 8.1 and earlier allows remote attackers to determine the existence of local pathnames, UNC share pathnames, intranet hostnames, and intranet IP addresses by examining error codes, as demonstrated by a res:// URL, and exploited in the wild in February 2014.
We first spotted this vulnerability used in trying to detect the presence of our own software, Malwarebytes Anti-Exploit, in a limited custom exploit kit a couple of months ago (hat tip to @dsanchezlavado):
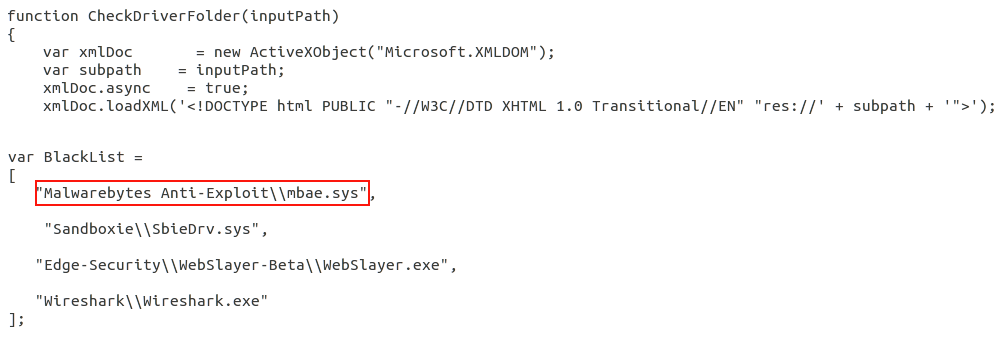
But now, as discovered by Kafeine, the latest version of Angler EK, one of the most popular and sophisticated exploit kits, also checks to see if either Malwarebytes Anti-Malware or Anti-Exploit are installed on the target system.
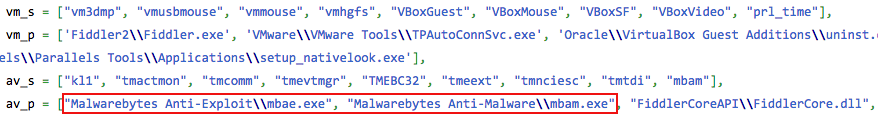
If Malwarebytes software is installed, then the exploit kit will silently exit and not even attempt to launch further exploits or malware.
We can almost imagine cyber criminals complaining about how their brand new creations, fresh out of the binary factory, are already being detected by our software. Even when they think they will catch everyone by surprise with a zero-day, we are already blocking it.
The combination of Malwarebytes Anti-Exploit and Anti-Malware is extremely effective at stopping both drive-by download and social engineering attacks. It’s nice however, when independent sources, albeit malware authors, confirm it.
The rationale behind not delivering the payloads to anyone running Malwarebytes software is motivated by a lack of return on investment. Knowing that they won’t be able to exploit those machines, cyber criminals would rather avoid wasting their ammo and also not generate unnecessary attention.
Just because exploit authors are choosing to avoid us doesn’t mean that we will avoid them. We are keeping a close eye on their activities and making sure that whatever they are cooking is still being blocked by our software.
In the meantime, this gives anyone not yet running Malwarebytes software another reason to go ahead and install our Malwarebytes Anti-Malware and Anti-Exploit on their computers.










