Security firm Fox-IT has identified a large malvertising campaign that began affecting Dutch users on June 11.
In their blog post, they say that several major news sites were loading the bogus advertisement that ultimately lead to the Angler exploit kit.
Looking at our telemetry we also noticed this attack, and in particular on Dutch news site Telegraaf[.]nl via an advert from otsmarketing.com, which according to Fox-IT is more than a suspicious ad network.
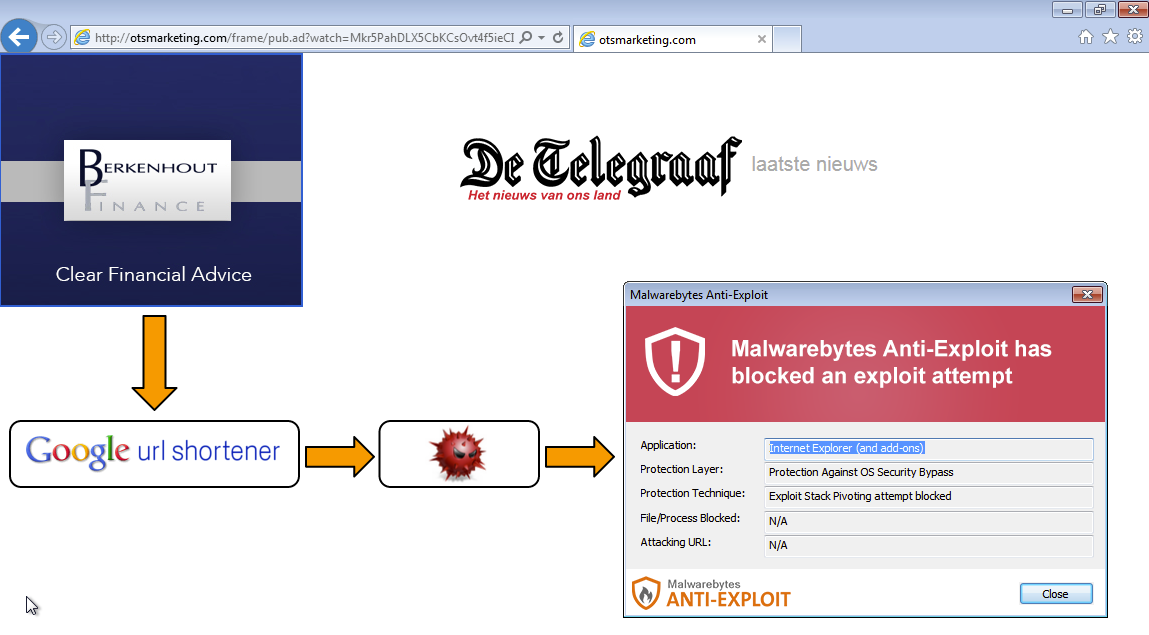
The ad silently loaded a Google shortened URL used to redirect to the exploit kit:
goo.gl//qeGEz9
uvjetovati1-huipputekij.cherokeealternativeenergy.com/five.disco?four=uPPu3w&jspage=0Ak&one=aWvlR&six=&cppbin=CerYZ-2&aspface=2aW&pycharm=hSoE49QHrfjrDqTcLwwJG-3E
Malwarebytes Anti-Exploit users were already protected from this exploit which employed a memory stack pivoting attack using the VirtualAllocEx API.
This latest malvertising case illustrates the efficacy of leveraging ad networks to selectively infect end users while also demonstrating that there is a clear problem with identifying rogue advertisers.
As stated by Fox-IT, the company responsible for the malvertising was not “loaded via advertisements until Thursday last week, the first day we’ve seen this malvertising campaign in action.”
This leaves some serious questions about the additional scrutiny in place for new advertisers and how it made it through security checks.